
In the realm of cybersecurity, understanding the distinct roles of vulnerability scanning and penetration testing is paramount. Vulnerability scanning serves as a crucial first step, identifying known weaknesses within systems. However, it is penetration testing that takes this a step further, simulating real-world attacks to exploit these vulnerabilities. This comprehensive approach is essential for organizations aiming to fortify their security posture against evolving threats.
The necessity of employing both methods in tandem cannot be overstated. Vulnerability scanning alone may leave organizations exposed, as it only reveals existing vulnerabilities without assessing the potential impact of an exploit. On the other hand, penetration testing not only uncovers these weaknesses but also provides invaluable insights into how they can be exploited, thereby informing strategic defenses.
Ultimately, the distinction between these two methodologies highlights a critical aspect of cybersecurity: the need for a multifaceted approach to effectively manage and mitigate cyber risks. Organizations must recognize that a robust cybersecurity strategy involves both identifying vulnerabilities and understanding their implications through simulated attacks. By integrating both vulnerability scanning and penetration testing, organizations can enhance their defenses and better protect their assets.
In an era where cyber threats are becoming increasingly sophisticated, organizations face the daunting challenge of safeguarding their digital assets. Understanding the nuances between vulnerability scanning and penetration testing is essential for developing a robust cybersecurity strategy. This article explores ten key insights that reveal how these two critical components work in tandem to not only identify potential weaknesses but also simulate real-world attacks. By providing organizations with a comprehensive approach to risk management, we pose a crucial question:
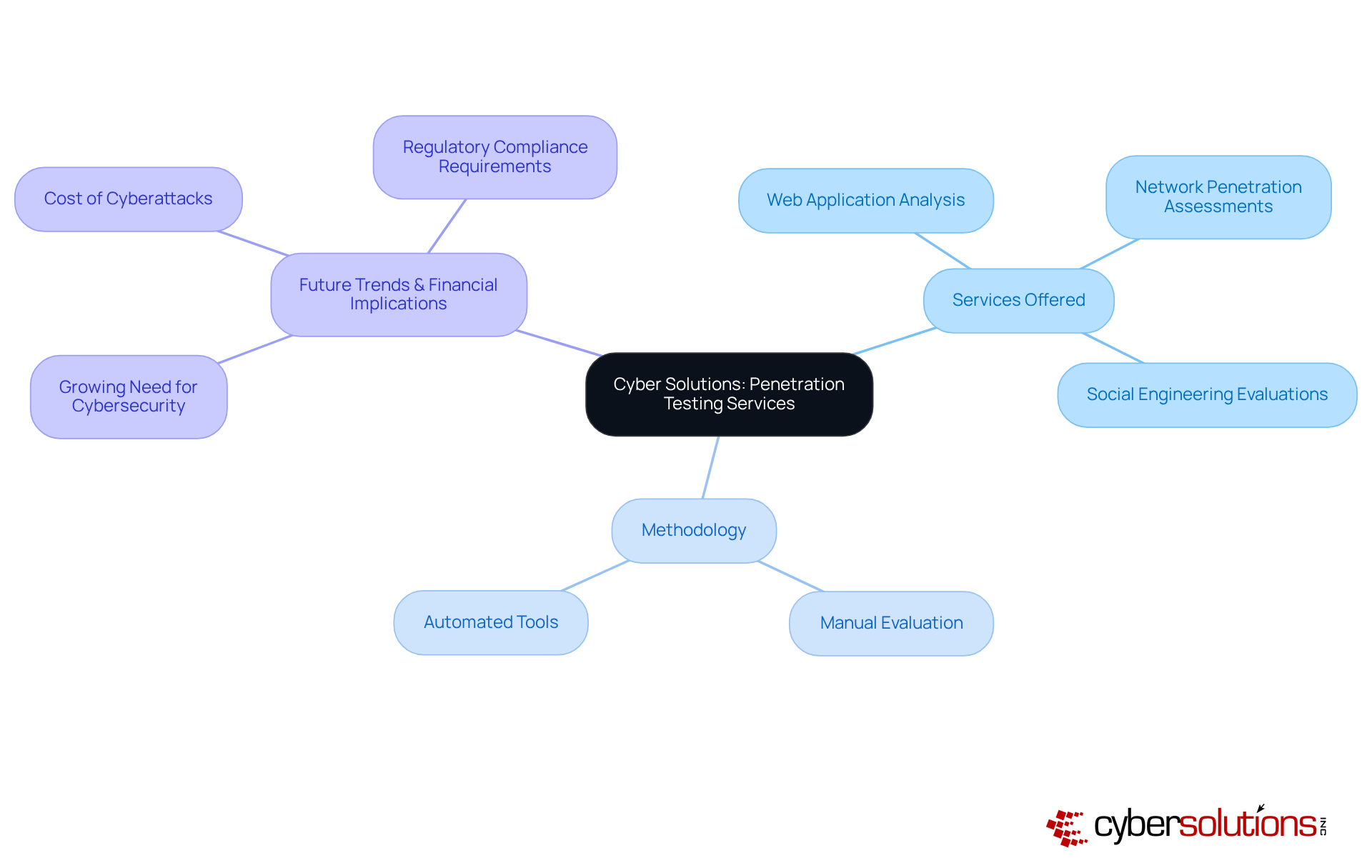
In today's digital landscape, the importance of robust cybersecurity cannot be overstated. Cyber Solutions Inc. offers an extensive range of penetration evaluation services designed to reveal and exploit weaknesses within a company's IT framework. Their methodology combines both manual evaluation and automated tools, ensuring comprehensive coverage across various areas, including:
This customized approach meets the specific requirements of various sectors, enabling entities to not only identify weaknesses but also evaluate the potential financial consequences of these vulnerabilities.
As we look ahead to 2025, the average expense of penetration evaluation services is anticipated to mirror the growing need for strong cybersecurity strategies. Numerous entities are acknowledging that proactive assessments are crucial for upholding compliance and protecting sensitive information. The evolving nature of cyber threats highlights the necessity for regular vulnerability scanning vs penetration testing, as both serve as critical components of a proactive cybersecurity strategy, enabling businesses to fortify their defenses and protect customer trust.
By investing in these services, entities position themselves to effectively reduce risks and improve their overall protection stance. Proactive measures today can safeguard against potential threats tomorrow, ensuring that organizations remain resilient in the face of increasing cyber challenges.
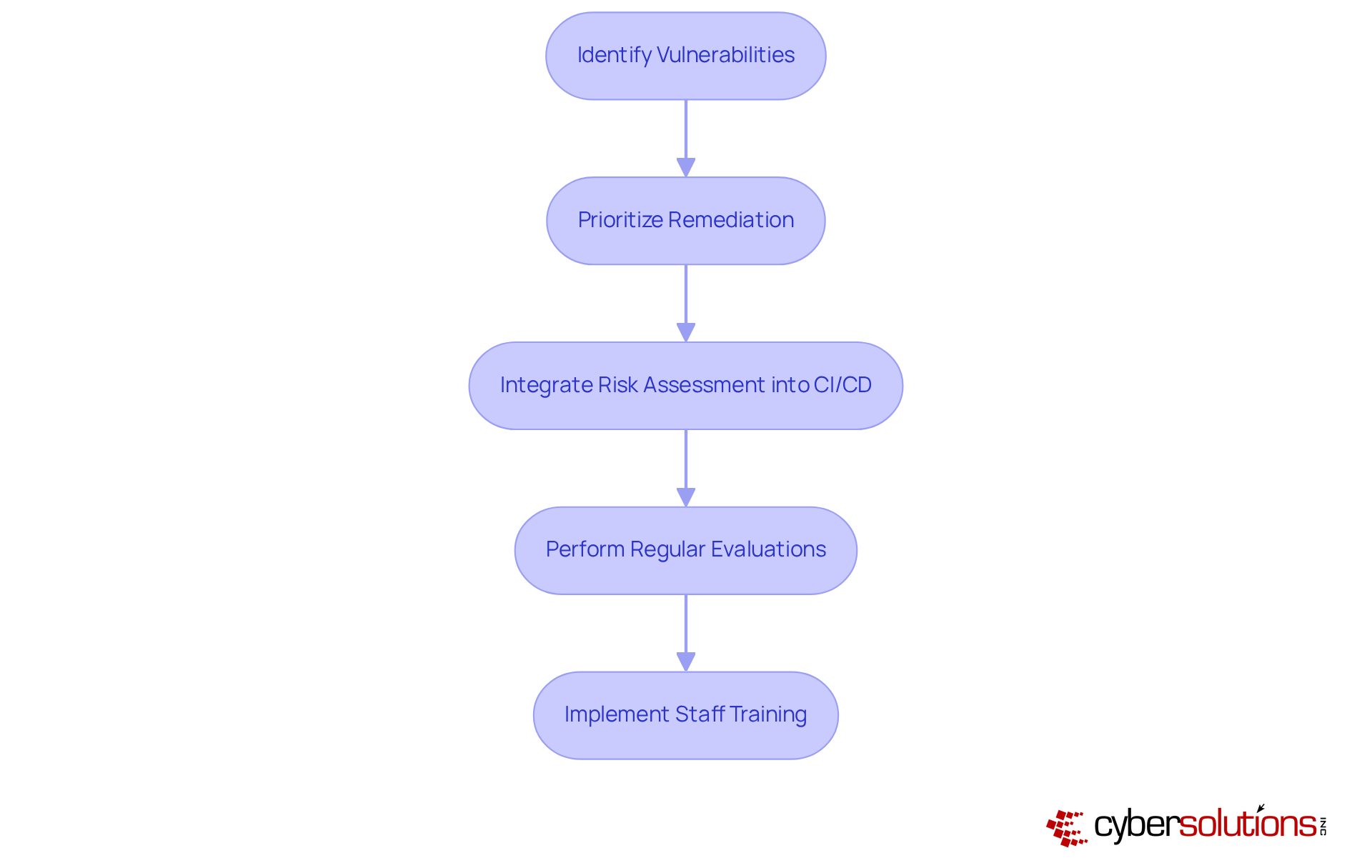
Vulnerability scanning vs penetration testing highlights the automated process crucial for detecting known weaknesses within a company's systems, networks, and applications. In the current landscape of cybersecurity threats, understanding vulnerability scanning vs penetration testing is essential for establishing a comprehensive list of potential vulnerabilities, enabling organizations to prioritize their remediation efforts efficiently. Regular evaluations are essential to maintain a robust protective stance against increasingly sophisticated cyberattacks.
By consistently performing vulnerability scanning vs penetration testing as part of their security assessments, companies can adopt a proactive strategy to cybersecurity, addressing weaknesses before they can be exploited by attackers. Current best practices emphasize the integration of risk assessment into the continuous integration and continuous deployment (CI/CD) pipeline, ensuring that security is a fundamental aspect of the development process. This integration not only streamlines the identification of weaknesses but also facilitates quicker remediation, significantly reducing the window of exposure.
Organizations across various sectors, including healthcare and finance, have reported significant enhancements in their protection frameworks through regular risk assessments. This proactive approach is vital in today's threat landscape, where cyberattacks are both frequent and sophisticated. Cyber Solutions Inc. exemplifies this methodology by implementing network hardening strategies that effectively close potential attack vectors and enhance protective configurations. Moreover, staff training focused on recognizing suspicious emails and maintaining proper cybersecurity hygiene further fortifies defenses against emerging threats.
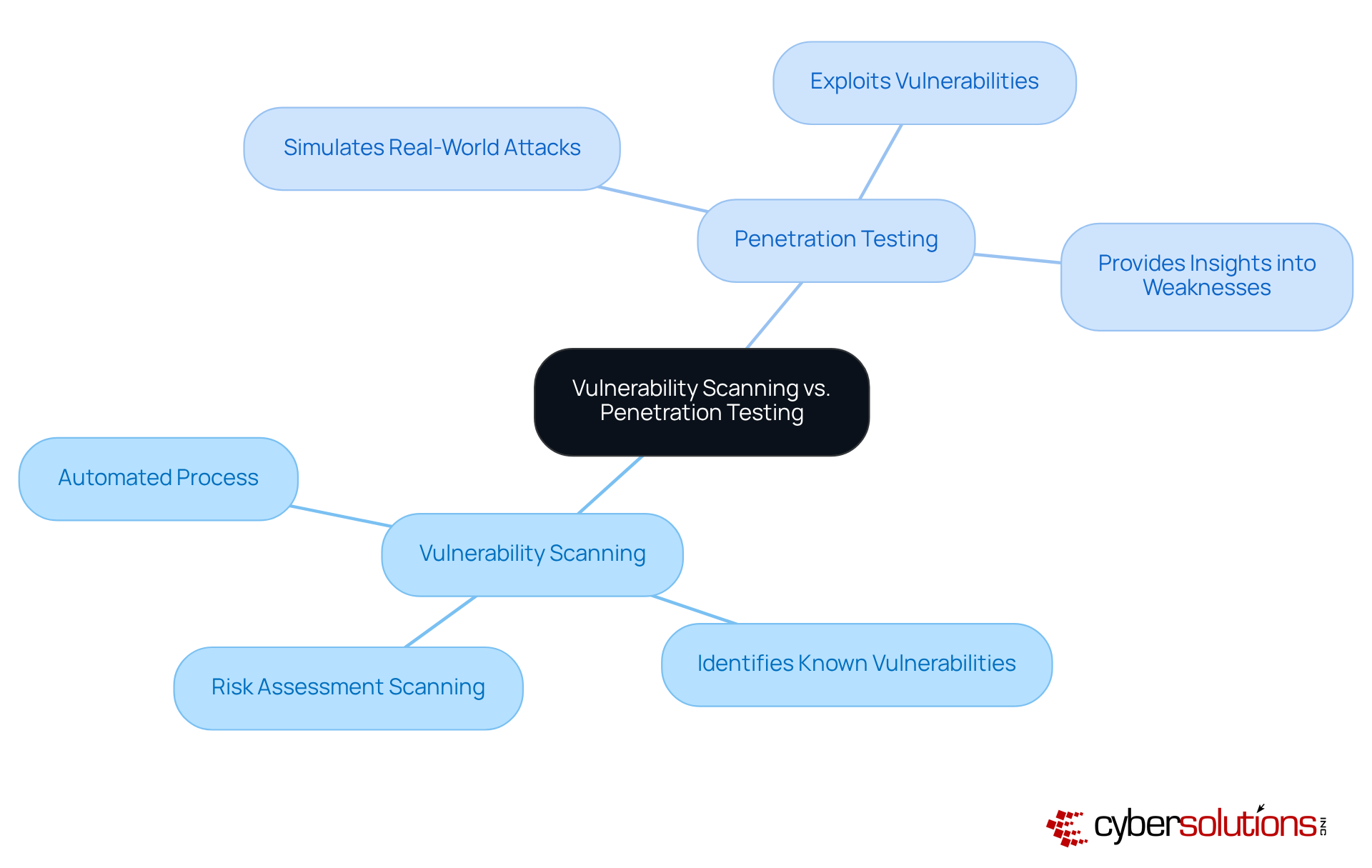
While both vulnerability scanning vs penetration testing aim to enhance security, they serve distinct purposes that are critical to understand.
Understanding the difference in vulnerability scanning vs penetration testing is essential for organizations as they formulate their cybersecurity strategies.
When considering vulnerability scanning vs penetration testing, vulnerability scanning is essential for organizations aiming to fortify their cybersecurity measures. It offers numerous benefits, including:
In today’s rapidly evolving threat landscape, understanding the difference between vulnerability scanning vs penetration testing is crucial, as vulnerability scanning is not merely an option; it is a necessity for maintaining robust cybersecurity.

Penetration testing is an essential component of a robust cybersecurity strategy, providing several key advantages that organizations cannot afford to overlook:
Statistics show that a significant proportion of enterprises perform penetration assessments each year, highlighting its significance in proactive cybersecurity strategies. Practical instances demonstrate how companies have effectively employed penetration testing to strengthen their incident response strategies, ultimately resulting in better outcomes and decreased risk exposure.

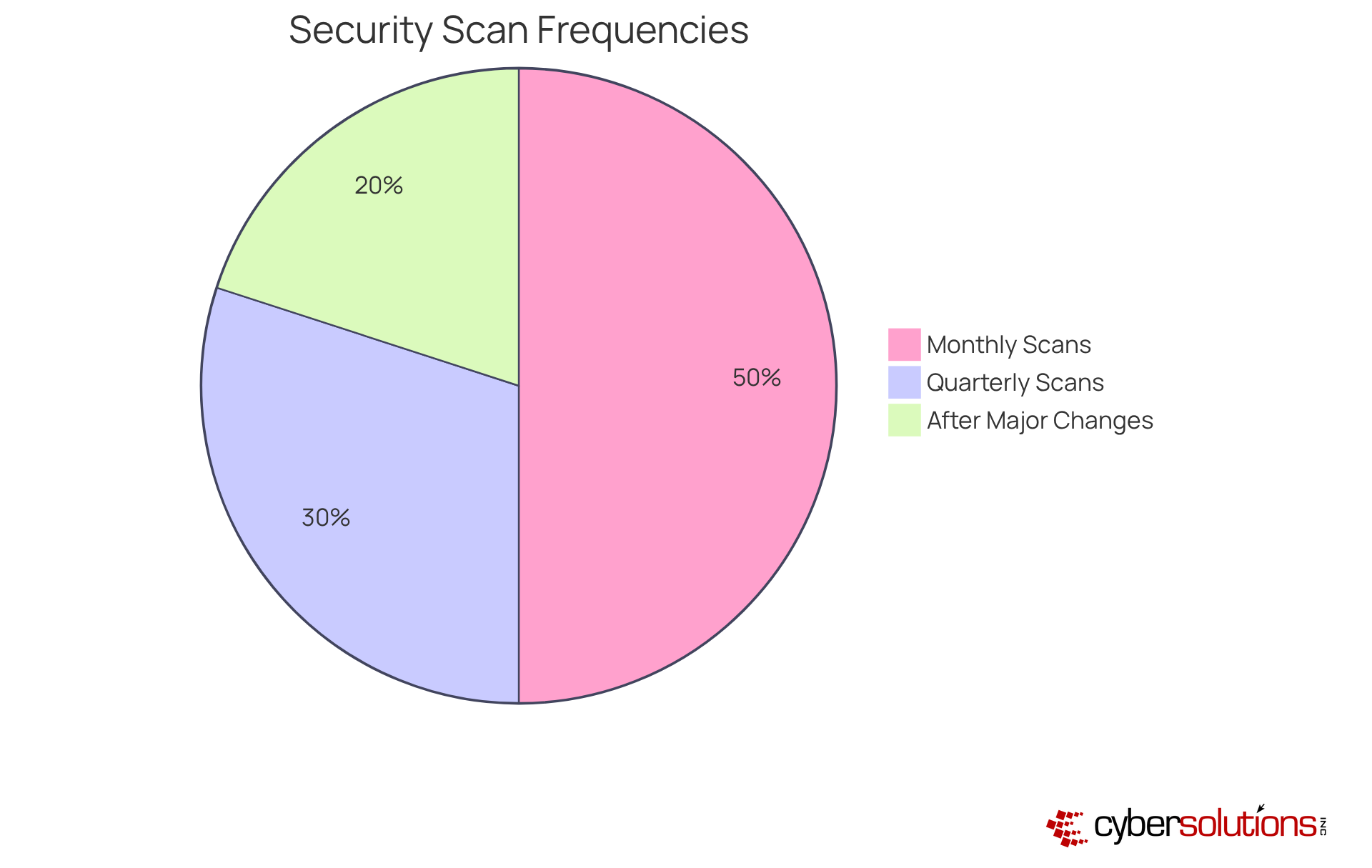
The frequency of security assessments is critical, influenced by factors such as the entity's size, sector, and risk appetite. Best practices in cybersecurity underscore the necessity of regular evaluations to safeguard organizational assets.
Monthly Scans: For most organizations, conducting scans at least once a month is essential to maintain a current view of their security posture. Routine security assessments enhance proactive strategies, such as application allowlisting, which prevents unauthorized software from running and minimizes the attack surface.
Quarterly Scans: Organizations operating in lower-risk environments may choose to conduct scans quarterly; however, this decision should be reassessed regularly. Implementing application allowlisting can significantly bolster protection by ensuring that only authorized applications are in operation, thereby reducing potential risks.
After Major Changes: Significant alterations to the IT environment—such as new software deployments or system upgrades—should trigger an immediate security scan to identify new risks. This practice is crucial, especially alongside application allowlisting, which helps maintain compliance with standards like HIPAA, PCI-DSS, and GDPR by enforcing strict control over software usage.
When considering vulnerability scanning vs penetration testing, it's clear that penetration testing is essential to fortify cybersecurity defenses, especially in the face of evolving threats. To ensure maximum effectiveness, organizations should perform penetration testing at strategic intervals:
Annually: It is imperative for most organizations to conduct a comprehensive penetration test at least once a year. This regular evaluation of vulnerability scanning vs penetration testing helps identify weaknesses that may have developed over time, ensuring robust defenses against shifting threats.
After Major Changes: Significant alterations to the IT infrastructure, such as the introduction of new applications or system upgrades, necessitate immediate penetration testing. These changes can introduce new vulnerabilities, and timely evaluations through vulnerability scanning vs penetration testing are crucial for identifying and mitigating risks before they can be exploited.
Before Compliance Audits: Organizations preparing for compliance audits must prioritize penetration testing. Conducting these tests not only ensures adherence to regulatory requirements but also demonstrates due diligence in maintaining a secure environment. Notably, a significant percentage of companies perform penetration tests specifically to meet compliance mandates, highlighting the critical nature of this practice in regulated industries.
By adhering to these strategic intervals, organizations can enhance their defensive posture and better protect themselves against the increasing frequency of cyberattacks.

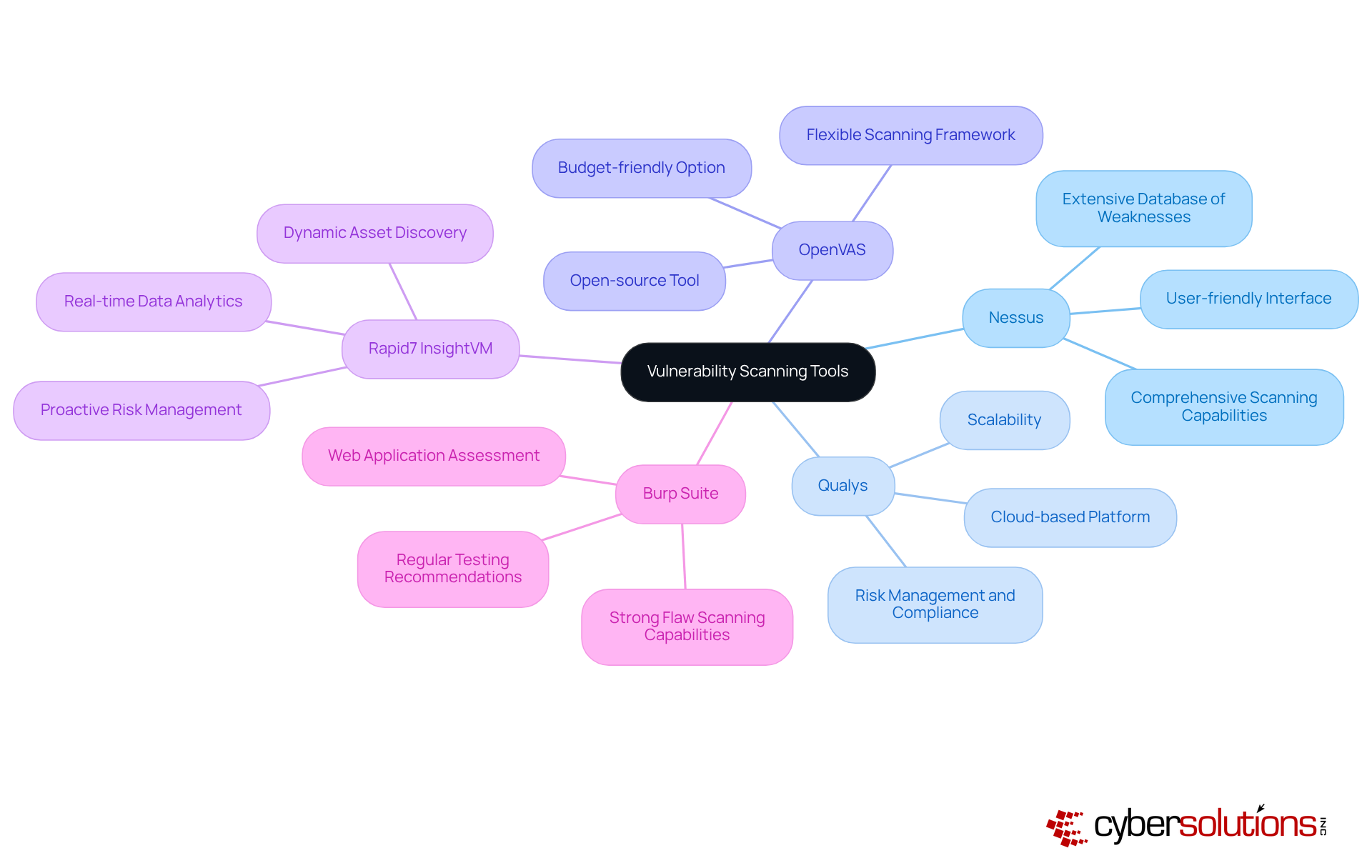
In today's digital landscape, understanding the importance of vulnerability scanning vs penetration testing cannot be overstated. Several tools stand out for their ability to address diverse organizational needs:
Nessus: Renowned for its comprehensive scanning capabilities, Nessus provides a user-friendly interface that simplifies the vulnerability management process. Organizations employing Nessus report high satisfaction levels, particularly due to its extensive database of weaknesses and ease of integration into existing protective frameworks. With nearly [30,000 weaknesses discovered each year](https://thehackernews.com/search/label/vulnerability scanner), tools like Nessus are essential for timely detection and resolution.
Qualys: This cloud-based platform excels in risk management and compliance solutions, enabling entities to continuously monitor their security stance. Qualys is preferred for its scalability and strong reporting capabilities, which assist companies in maintaining compliance with regulatory standards. Cybersecurity specialists assert that regular use of Qualys can greatly enhance a company's ability to manage vulnerabilities efficiently.
OpenVAS: As an open-source tool, OpenVAS offers a flexible and powerful scanning framework. It is especially attractive to businesses seeking budget-friendly options without sacrificing functionality, making it a favored choice among SMEs. Regular utilization of OpenVAS can help organizations stay ahead of potential threats.
Rapid7 InsightVM: This tool combines weakness management with real-time data analytics, enabling proactive risk management. Organizations utilizing InsightVM benefit from its dynamic asset discovery and prioritization features, which enhance their overall protection strategy. The proactive approach facilitated by InsightVM is crucial, particularly given that cyberattacks on small and midsized companies can cost an average of $200,000 per incident.
Burp Suite: Focused on web application assessment, Burp Suite offers strong flaw scanning capabilities. Its ability to detect weaknesses in web applications makes it an essential tool for organizations prioritizing application security. Experts recommend regular testing with Burp Suite to ensure web applications remain secure against evolving threats.
Recent advancements in security scanning tools emphasize the significance of understanding vulnerability scanning vs penetration testing for effectively mitigating risks. Entities that integrate these tools into a comprehensive cybersecurity plan are better positioned to identify weaknesses and react proactively, ultimately minimizing their exposure to cyber threats. Incorporating security scanning into a broader cybersecurity framework enhances asset management, patch management, and incident response capabilities.
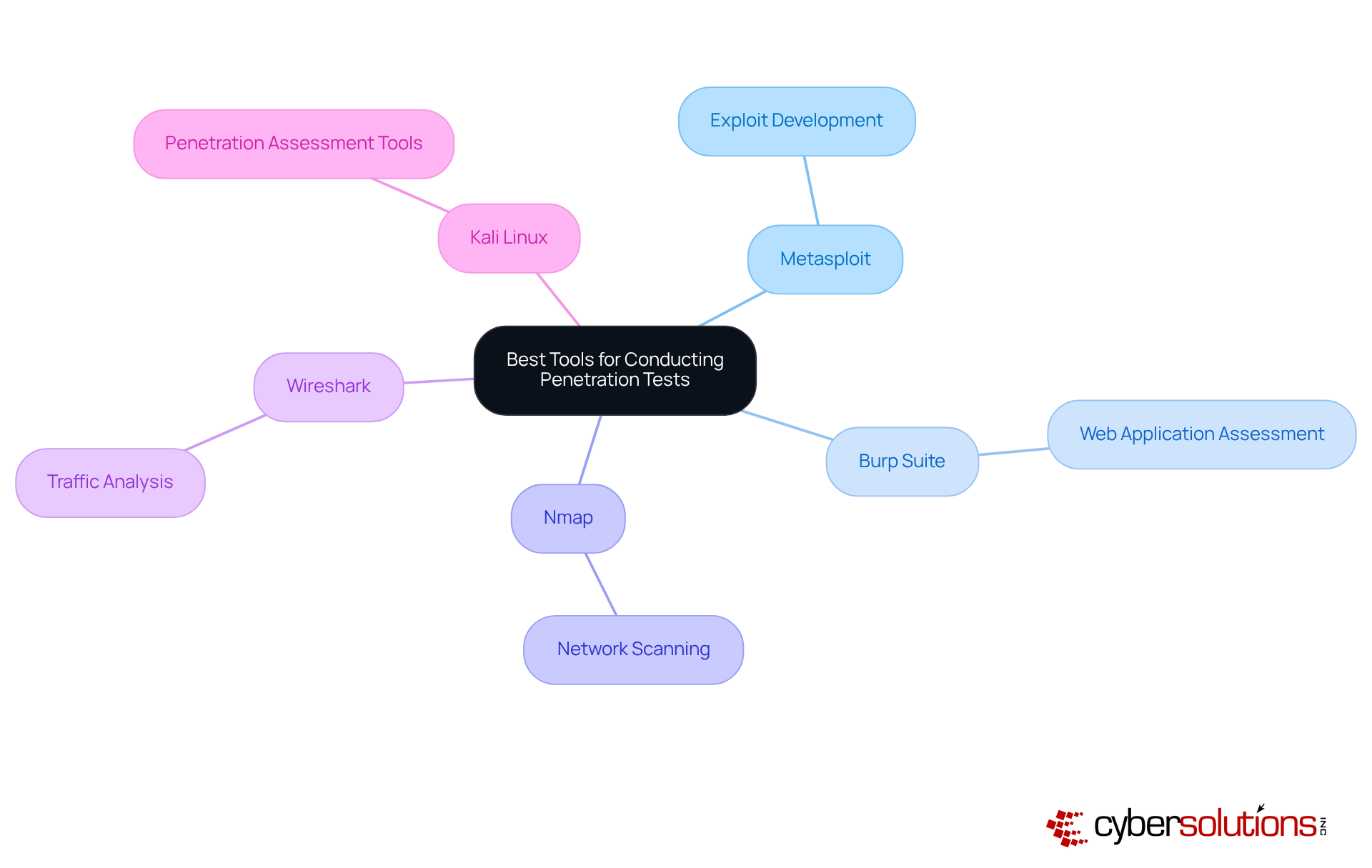
In today’s cybersecurity landscape, understanding vulnerability scanning vs penetration testing is crucial, as effective penetration testing requires the right tools to simulate attacks and identify vulnerabilities. Here are some essential tools:
Utilizing these tools effectively can significantly enhance an organization’s security posture against evolving threats.
In today's digital age, the importance of cybersecurity in healthcare cannot be overstated. Combining risk assessment scans and penetration evaluations establishes a thorough protective approach that tackles both recognized and unrecognized weaknesses. Regular vulnerability scanning vs penetration testing helps entities identify and address known weaknesses, while penetration testing uncovers how these vulnerabilities might be exploited in real-world situations. This combined approach strengthens overall security and aligns with compliance requirements, such as HIPAA and PCI-DSS.
Moreover, by leveraging Cyber Solutions' Compliance as a Service (CaaS) and incident response capabilities, organizations can streamline their compliance efforts and enhance threat detection. This ensures they are well-prepared to manage and mitigate potential cyber threats effectively. In an environment where the stakes are high, the integration of these services not only fortifies defenses but also instills confidence in stakeholders regarding the organization's commitment to safeguarding sensitive information.

In today's digital landscape, the significance of cybersecurity cannot be overstated, particularly for organizations dedicated to protecting their assets. Understanding the distinction between vulnerability scanning and penetration testing is essential for establishing robust defenses against cyber threats. Vulnerability scanning identifies known weaknesses, while penetration testing simulates real-world attacks to exploit these vulnerabilities. This dual approach empowers organizations to discover potential risks and comprehend their implications in a practical context.
Key insights throughout this discussion highlight the necessity of regular assessments and the integration of both methodologies into an organization's cybersecurity strategy. From proactive risk management and compliance assurance to enhanced incident response, each method offers unique benefits that collectively contribute to a stronger security posture. Tools such as Nessus, Qualys, and Metasploit are crucial for effectively implementing these strategies, ensuring organizations remain vigilant in the face of evolving threats.
Ultimately, integrating vulnerability scanning and penetration testing transcends best practice; it is a necessity for organizations committed to safeguarding sensitive information and maintaining customer trust. As cyber threats grow in sophistication and frequency, embracing a comprehensive cybersecurity strategy that includes both methodologies empowers organizations to proactively address vulnerabilities, enhance defenses, and cultivate a culture of security awareness. Taking decisive action now can significantly mitigate risks and prepare businesses for the challenges of tomorrow.
What services does Cyber Solutions Inc. offer for penetration testing?
Cyber Solutions Inc. offers a range of penetration evaluation services, including web application analysis, network penetration assessments, and social engineering evaluations.
How does Cyber Solutions Inc. approach penetration testing?
Their methodology combines both manual evaluation and automated tools to ensure comprehensive coverage across various areas of a company's IT framework.
Why is penetration testing important for organizations?
Penetration testing helps organizations identify weaknesses in their IT systems and evaluate the potential financial consequences of these vulnerabilities, which is crucial for maintaining compliance and protecting sensitive information.
What is the difference between vulnerability scanning and penetration testing?
Vulnerability scanning is an automated process that identifies known vulnerabilities without exploiting them, while penetration testing simulates real-world attacks to exploit these vulnerabilities and provide insights into how they could be leveraged by malicious actors.
Why should organizations perform regular vulnerability scans and penetration tests?
Regular evaluations are essential for maintaining a robust protective stance against sophisticated cyberattacks, allowing organizations to address weaknesses before they can be exploited.
How can integrating risk assessment into the CI/CD pipeline benefit organizations?
Integrating risk assessment into the CI/CD pipeline ensures that security is a fundamental aspect of the development process, streamlining the identification of weaknesses and facilitating quicker remediation, thus reducing exposure time.
What sectors benefit from regular risk assessments?
Organizations in various sectors, including healthcare and finance, have reported significant enhancements in their protection frameworks through regular risk assessments.
What additional measures can organizations take to strengthen their cybersecurity defenses?
Organizations can implement network hardening strategies, conduct staff training to recognize suspicious emails, and maintain proper cybersecurity hygiene to fortify their defenses against emerging threats.