
Understanding the cost of IT is crucial for C-suite leaders. With the rapid evolution of technology, grasping the various cost components—such as hardware, software, personnel, and cybersecurity investments—has never been more important. This knowledge not only aids in effective budgeting but also highlights the financial benefits of IT investments.
By adopting a strategic approach to IT expenditures, organizations can enhance operational efficiency, mitigate risks, and drive competitive advantage. Consider the implications: how can a well-structured IT budget transform your organization’s performance? The answer lies in recognizing that every dollar spent on IT can yield significant returns when managed wisely.
Moreover, the article outlines strategies that empower leaders to evaluate their IT investments critically. By focusing on the right components and understanding their impact, C-suite executives can make informed decisions that align with their organizational goals. This proactive stance is essential in today’s competitive landscape, where technology plays a pivotal role in success.
In conclusion, a comprehensive understanding of IT costs is not just beneficial; it’s imperative for leaders aiming to navigate the complexities of modern business. Embrace this knowledge to unlock the full potential of your IT investments.
Understanding the complexities of IT costs is crucial for C-suite leaders navigating today’s intricate business landscape. With organizations grappling with rising cybersecurity threats and the swift pace of technological advancement, the financial implications of IT expenditures have never been more significant. This article explores the essential components of IT costs, providing insights into effective budgeting strategies that not only enhance operational efficiency but also create a competitive edge.
How can executives ensure their IT investments deliver maximum returns while protecting their organizations from emerging risks?
In today’s digital landscape, comprehending the cost of it is crucial for effective budgeting and operational efficiency. Cybersecurity, in particular, stands out as a pressing concern for healthcare organizations. With cyber threats escalating, CFOs must navigate a complex environment where every dollar spent can significantly impact their organization’s resilience and compliance.
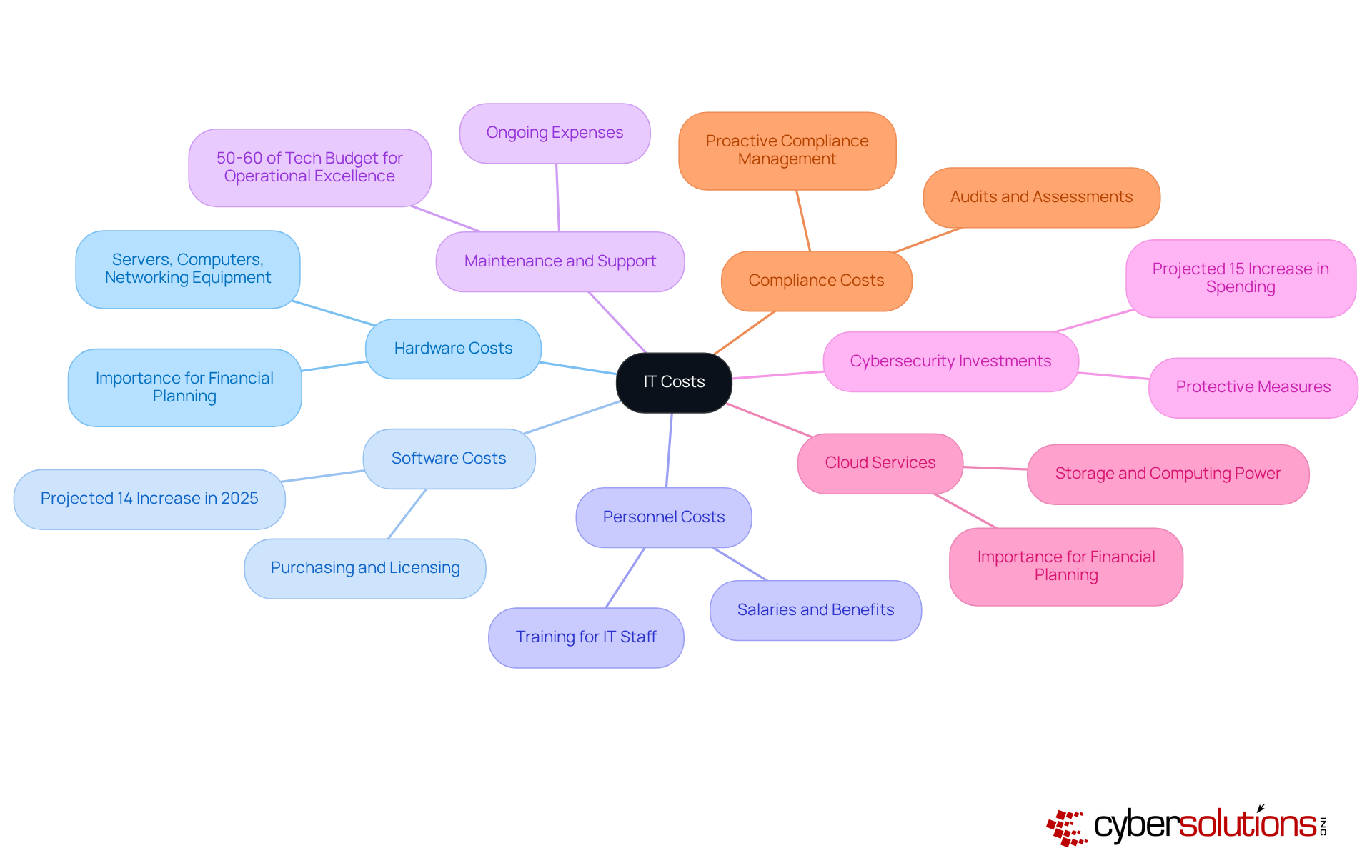
Hardware Costs: This includes servers, computers, networking equipment, and other essential devices for IT operations. As organizations increasingly rely on advanced hardware, grasping the cost of it is vital for sound financial planning.
Software Costs: These expenses cover purchasing, licensing, and maintaining software applications, such as operating systems and productivity tools. Notably, software spending is projected to rise by 14% in 2025, reaching approximately $1.23 trillion, reflecting a strategic shift towards scalable digital solutions.
Personnel Costs: Salaries, benefits, and training for IT staff often represent a significant portion of the IT budget. Investing in skilled personnel is essential for sustaining operational excellence and fostering innovation.
Maintenance and Support: Ongoing expenses for sustaining hardware and software, including help desk assistance and system updates, are critical for ensuring smooth operations. Companies should allocate 50-60% of their tech budget to operational excellence, which encompasses the cost of it for maintenance.
Cybersecurity Investments: With the rise of cyber threats, organizations must allocate funds for protective measures, including firewalls, antivirus software, and incident response services. Application allowlisting is a key component of these investments, proactively preventing unauthorized software from executing and reducing vulnerabilities. Gartner predicts a 15% increase in cybersecurity spending, with global expenditures projected to reach $212 billion, underscoring the necessity of robust cybersecurity measures.
Cloud Services: Expenses related to cloud computing solutions, including storage, computing power, and software as a service (SaaS) subscriptions, are becoming increasingly significant. As companies shift to cloud-based solutions, understanding the cost of it is essential for efficient financial planning.
Compliance Costs: Investments required to meet regulatory requirements can include audits, assessments, and compliance software. As regulations evolve, organizations must remain proactive regarding compliance expenses to avoid potential fines and operational disruptions.
By thoroughly understanding these components, C-suite leaders can allocate resources more effectively and identify opportunities for cost reductions, ultimately enhancing their organization’s financial health and operational efficiency. Moreover, implementing a rapid incident response strategy, such as a 24-hour on-site support team, can significantly mitigate the impact of cyber threats, ensuring continuity and resilience in operations.
To effectively budget for IT, consider these essential strategies:
Align IT Budget with Business Goals: It's crucial that the IT budget supports the overall strategic objectives of your organization. This alignment not only prioritizes spending on initiatives that drive business value but also enhances operational efficiency and competitive advantage.
Implement Zero-Based Budgeting (ZBB): Adopting a zero-based approach for each budgeting cycle requires justification for every expense, rather than relying on historical spending patterns. This method can reveal unnecessary expenses and promote efficiency, with organizations reporting potential decreases in operating expenditures by 10 to 30% through ZBB practices.
Prioritize Cybersecurity Investments: Given the rising threat landscape, allocating a significant portion of the budget to cybersecurity measures is imperative. This proactive allocation not only safeguards your organization but also reduces the potential cost of it associated with substantial data breaches.
Utilize Cloud Solutions Wisely: It's important to carefully evaluate cloud service providers to select solutions that offer both scalability and consider the cost of it. Regularly reviewing cloud usage is essential to eliminate waste and optimize spending, especially since 81% of companies exceeded their cloud budgets in 2024 due to inaccurate needs assessments.
Involve Stakeholders in the Budgeting Process: Engaging various departments in the budgeting process ensures that IT expenditures align with the needs of the entire organization. This collaboration fosters informed decision-making and better resource allocation, ultimately aligning IT expenditures with broader business objectives.

IT costs play a pivotal role in shaping business operations and strategic direction across several key areas:
Operational Efficiency: Strategic IT investments streamline processes, minimize downtime, and boost productivity. Transitioning to advanced software solutions can accelerate project timelines and enhance employee satisfaction, ultimately leading to a more engaged workforce.
Competitive Advantage: Organizations that allocate resources effectively toward technology can secure a competitive edge. By utilizing cutting-edge tools and systems, they significantly improve customer experiences and operational capabilities, positioning themselves ahead of competitors.
Risk Management: Allocating budget for cybersecurity and compliance is essential in mitigating risks related to data breaches and regulatory penalties. This proactive approach safeguards the entity’s reputation and protects its financial stability, highlighting the cost of it as evidenced by companies that have successfully navigated compliance challenges through robust IT frameworks.
Scalability: Investments in scalable IT solutions enable businesses to expand without incurring a proportional cost of it. This adaptability is crucial for addressing changing market conditions and customer needs, allowing businesses to maintain agility in a competitive environment.
Innovation Enablement: A well-structured IT budget fosters innovation by providing the necessary resources for research and development. This funding enables organizations to explore new technologies and business models, driving growth and enhancing their market position. Organizations that prioritize innovation in their IT expenditures frequently experience significant returns, with many indicating favorable effects on efficiency and revenue growth.
In summary, a strategic approach to IT expenditure not only enhances operational efficiency but also drives competitive advantage, mitigates risks, supports scalability, and enables innovation. This makes it a critical component of modern business strategy.

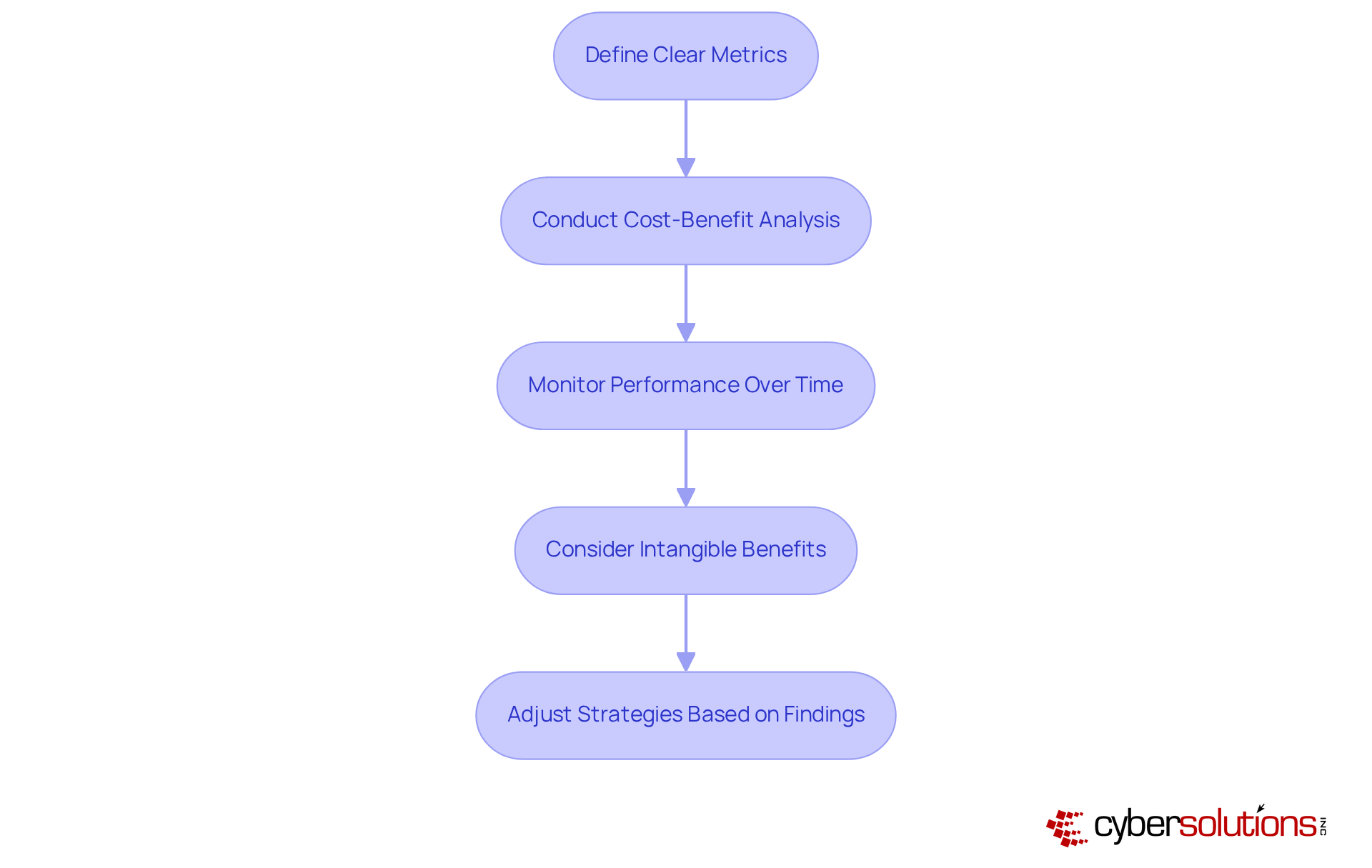
To effectively evaluate the ROI of IT investments, it’s crucial to follow these steps:
Define Clear Metrics: Establish specific, measurable objectives for each IT allocation. Metrics may encompass elevated revenue, decreased expenses, or enhanced customer satisfaction. Did you know that nearly 73% of executives cite the inability to define metrics as a major challenge in assessing technology expenditures? Furthermore, 64% of executives rely on enhanced operational efficiency as the primary measure for evaluating ROI. This highlights the necessity for clarity in your approach.
Conduct Cost-Benefit Analysis: Compare the total costs of the IT expenditure against the expected benefits over time, taking into account the cost of it. This analysis should encompass both direct financial returns and indirect benefits, such as enhanced employee productivity, while also considering the cost of it. For instance, a recent study revealed that organizations investing in data management and architecture reported an impressive 83% ROI, showcasing the potential financial benefits from strategic IT expenditures.
Monitor Performance Over Time: Regularly evaluate the effectiveness of IT expenditures against the defined metrics. Ongoing assessment helps identify areas for enhancement and ensures that resources align with business objectives. Organizations that adopt a portfolio perspective of their technology resources are better equipped to assess their impact on overall goals.
Consider Intangible Benefits: While financial metrics are crucial, it’s equally important to account for intangible benefits such as improved brand reputation, customer loyalty, and employee engagement. These factors can significantly influence long-term success and are often overlooked in traditional ROI calculations.
Adjust Strategies Based on Findings: Utilize insights gained from ROI evaluations to inform future budgeting and funding decisions. This iterative process allows organizations to continually optimize their IT spending for maximum impact, ensuring that technology investments effectively contribute to business growth.
Understanding the multifaceted nature of IT costs is crucial for C-suite leaders who want to optimize their organizations' financial health and operational efficiency. By dissecting the various components—hardware, software, personnel, maintenance, cybersecurity, cloud services, and compliance—executives can make informed decisions that align IT expenditures with broader business objectives, ultimately driving strategic growth.
Effective budgeting strategies can significantly enhance resource allocation. Consider:
These approaches not only streamline costs but also ensure that IT investments bolster operational efficiency, competitive advantage, risk management, scalability, and innovation. Isn’t it clear that strategic IT investments are pivotal in shaping business success?
In light of the evolving landscape of IT expenses, organizations must adopt a proactive approach to budgeting and resource management. By continuously assessing the ROI of IT investments and adjusting strategies based on performance metrics, executives can ensure that their technology expenditures contribute meaningfully to business objectives. Emphasizing the importance of strategic IT cost management not only secures immediate operational benefits but also positions organizations for long-term success in an increasingly competitive market.
Ultimately, the question remains: Are you ready to take charge of your IT costs and drive your organization toward sustained growth?
What are the key components of IT costs?
The key components of IT costs include hardware costs, software costs, personnel costs, maintenance and support, cybersecurity investments, cloud services, and compliance costs.
What do hardware costs encompass?
Hardware costs encompass expenses for servers, computers, networking equipment, and other essential devices necessary for IT operations.
How are software costs defined?
Software costs include expenses for purchasing, licensing, and maintaining software applications such as operating systems and productivity tools.
What is the projected trend for software spending?
Software spending is projected to rise by 14% in 2025, reaching approximately $1.23 trillion, reflecting a strategic shift towards scalable digital solutions.
Why are personnel costs significant in the IT budget?
Personnel costs, which include salaries, benefits, and training for IT staff, represent a significant portion of the IT budget as investing in skilled personnel is essential for operational excellence and innovation.
What should organizations allocate for maintenance and support?
Organizations should allocate 50-60% of their tech budget to operational excellence, which includes ongoing expenses for maintaining hardware and software, help desk assistance, and system updates.
Why are cybersecurity investments important?
Cybersecurity investments are crucial due to the rise of cyber threats, requiring organizations to allocate funds for protective measures such as firewalls, antivirus software, and incident response services.
What is the expected increase in global cybersecurity spending?
Gartner predicts a 15% increase in cybersecurity spending, with global expenditures projected to reach $212 billion.
What are cloud service expenses?
Cloud service expenses include costs related to cloud computing solutions, such as storage, computing power, and software as a service (SaaS) subscriptions.
What are compliance costs?
Compliance costs are investments required to meet regulatory requirements, which can include audits, assessments, and compliance software.
How can understanding IT costs benefit organizations?
By understanding IT costs, C-suite leaders can allocate resources effectively, identify opportunities for cost reductions, and enhance their organization’s financial health and operational efficiency.
What strategy can help mitigate the impact of cyber threats?
Implementing a rapid incident response strategy, such as a 24-hour on-site support team, can significantly mitigate the impact of cyber threats and ensure continuity in operations.