
Selecting a managed IT support company is crucial for businesses aiming to thrive in today’s competitive landscape. Enhanced operational efficiency, improved cybersecurity, and significant cost savings are just a few of the compelling advantages that come with this choice. In an era where cybersecurity threats are rampant, organizations must prioritize their IT strategies to safeguard their assets and data.
Managed IT services streamline operations by providing specialized expertise that allows businesses to focus on their core activities. This not only alleviates the burden of managing IT complexities but also ensures compliance with industry regulations. How can organizations effectively navigate these challenges without the right support? The answer lies in partnering with a managed IT provider that understands the unique needs of your business.
Moreover, the cost savings associated with managed IT services cannot be overlooked. By outsourcing IT support, companies can reduce overhead costs while gaining access to cutting-edge technology and resources. This strategic move enables organizations to allocate their budgets more effectively, driving growth and innovation.
In conclusion, the decision to choose a managed IT support company is not just about technology; it’s about empowering your business to operate at its best. By leveraging specialized expertise and focusing on core activities, organizations can navigate the complexities of the digital landscape with confidence. Don’t let IT challenges hold you back—consider the benefits of managed IT services today.
In a world where digital threats are more prevalent than ever, businesses must recognize the critical need for robust IT support to protect their operations. The transition to managed IT services not only bolsters security but also enhances efficiency, enabling organizations to concentrate on their core missions. But with a plethora of options available, what truly distinguishes a managed IT support company? How can it reshape a business's operational landscape? This article explores ten compelling reasons why partnering with a managed IT support provider is not merely a strategic choice but an essential necessity for any forward-thinking organization.
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. As cyber threats evolve, healthcare organizations face unique challenges that demand robust IT solutions tailored to their specific needs. Cyber Solutions Inc. distinguishes itself as a managed IT support company by offering a comprehensive range of services designed to meet the diverse requirements of industries like healthcare, finance, manufacturing, and government.
This holistic approach integrates advanced cybersecurity solutions, including:
By implementing these measures, businesses can concentrate on their core operations without the complexities of IT management. With the managed IT support company sector projected to grow at a remarkable compound annual growth rate of 14.1%, reaching a market size of USD 731.08 billion by 2030, the reliance on specialized IT support is becoming increasingly critical. This growth underscores the necessity for organizations to enhance operational efficiency and security, particularly in meeting compliance requirements unique to their sectors.
A managed IT support company not only boosts growth but also enhances security. Companies utilizing these resources report quicker growth, improved security, and reduced downtime compared to those managing IT internally. Organizations that adopt managed solutions can expect significant improvements in their cybersecurity posture, enabling them to navigate the ever-changing digital threat landscape with confidence. Industry leaders emphasize that incorporating AI and machine learning into managed offerings will further enhance delivery speed and efficiency, allowing digital firms to proactively monitor their assets and identify vulnerabilities before they can be exploited.
Moreover, holistic IT solutions are essential for streamlining operations and ensuring compliance with industry regulations, which is particularly vital in sectors like healthcare and finance. Tech Systems Inc. provides extensive managed security support, including:
This ensures that enterprises are prepared for any potential threats. As the demand for adaptable, scalable IT offerings continues to rise, Tech Services Inc. remains committed to empowering organizations with customized services that foster growth and resilience in an increasingly complex digital landscape.
In today's fast-paced business environment, having 24/7 help desk support is not just a luxury—it's a necessity. Cyber Solutions ensures that technical issues are addressed promptly, regardless of the hour. This ongoing accessibility is crucial for enhancing employee productivity; research indicates that companies with round-the-clock IT support experience significant improvements in operational efficiency. By utilizing continuous support, businesses report a marked reduction in downtime, which directly correlates with increased employee output and morale.
Moreover, a dedicated support team available at all times fosters a culture of reliability and trust within the organization. Employees can focus on their primary responsibilities without the worry of unresolved technical issues. Our comprehensive 24/7 network monitoring and alert services proactively detect anomalies and potential vulnerabilities, allowing for swift action to prevent downtime or breaches. This includes tailored access controls and restrictions, ensuring that only authorized users have access to sensitive information.
As companies navigate the complexities of 2025, the importance of continuous IT support becomes even more pronounced. Many organizations recognize that a managed IT support company is a vital component of their operational strategy. For instance, companies like Linktree and Biteable have successfully implemented 24/7 support models, resulting in enhanced customer satisfaction and loyalty. These examples showcase the tangible benefits of investing in a managed IT support company for continuous IT support. Are you ready to elevate your business operations and ensure your team can work without interruptions?
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, particularly for enterprises engaged in federal contracts. Cybernetic Services employs a range of sophisticated tactics designed to shield organizations from the ever-evolving threats that permeate the digital realm. Central to this strategy is the deployment of advanced threat detection systems, which have been shown to dramatically reduce the time it takes to identify and respond to incidents. For example, organizations utilizing these systems can detect breaches an average of 108 days faster than those relying on traditional methods, significantly cutting costs associated with prolonged exposure, given that the average duration of a breach is 258 days.
Moreover, Cyber Solutions places a strong emphasis on the necessity of robust incident response protocols. These protocols are vital for compliance with stringent cybersecurity standards that protect Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). By ensuring that entities can swiftly address security incidents, these protocols minimize potential damage and maintain operational continuity. Regular vulnerability assessments further strengthen defenses by identifying and mitigating risks before they can be exploited.
By prioritizing these cybersecurity measures—such as a layered approach that includes endpoint isolation, malware removal, and user training—organizations not only protect sensitive data but also ensure compliance with mandatory regulations. This commitment to security not only fosters customer trust but also enhances the company's reputation in the marketplace, positioning them as a reliable partner in an increasingly regulated environment. Notably, 32% of organizations express concern over reputational damage and negative feedback following a cyberattack, underscoring the critical importance of maintaining strong cybersecurity measures.
In today’s digital landscape, robust backup and disaster recovery services are not just optional; they are essential for maintaining data integrity and ensuring business continuity. Cyber Solutions offers automated backup solutions that empower businesses to protect their critical data against loss and swiftly restore operations after disruptions. Regular testing of recovery processes is integral to this strategy, enhancing the reliability of recovery efforts and minimizing downtime.
Consider this: 96% of businesses with a solid backup and recovery strategy can effectively resist ransomware attacks. This statistic underscores the importance of immediate action and specialized expertise. Furthermore, companies that implement comprehensive disaster recovery plans experience a remarkable 96% success rate in resuming operations after data loss incidents. Alarmingly, 43% of businesses without recovery plans fail after catastrophic data loss, highlighting the critical need for such strategies.
As Karyn DiMassa, Managing Director, emphasizes, "Having the right processes and procedures in place will significantly enhance your entity’s ability to recover and continue operations." This layered strategy not only enables entities to sustain their competitive advantage but also showcases a dedication to operational resilience and stakeholder trust.
To ensure your entity is prepared, consider implementing a checklist to evaluate your current backup solutions and recovery strategies. This proactive approach is directly informed by insights gained from our rapid incident response case study, ensuring you are equipped to face any challenge head-on.
Co-managed IT assistance from a managed IT support company like Tech Services is crucial for organizations looking to bolster their internal IT capabilities through strategic partnerships with seasoned professionals. This collaborative model empowers businesses to delegate routine tasks, allowing their teams to focus on high-impact initiatives that drive growth and innovation. By tapping into external expertise, a managed IT support company can significantly enhance IT efficiency, achieve substantial cost savings, and ensure that internal teams receive the support they need to meet their objectives.
Industry leaders emphasize that such partnerships not only lighten the load on internal staff but also cultivate a culture of innovation and resilience. For instance, organizations that adopt co-managed IT often report improved operational performance and reduced downtime, as they gain access to specialized skills without the overhead of hiring full-time personnel. This approach is especially advantageous in today’s fast-paced digital landscape, where the demand for agile and responsive IT solutions is more critical than ever.
In today’s healthcare landscape, cybersecurity is not just a necessity; it’s a critical component of operational integrity. Cyber Solutions offers Compliance as a Service (CaaS), a strategic approach that empowers organizations to adeptly navigate the complex regulatory environments of HIPAA, PCI-DSS, and GDPR. By outsourcing compliance management to seasoned experts, businesses can ensure they meet essential requirements without the strain of maintaining extensive in-house resources. This strategy not only reduces the risk of costly penalties but also significantly boosts operational efficiency by streamlining compliance processes.
Consider this: data indicates that 38% of businesses are now outsourcing some or all of their compliance functions. This trend reflects a growing recognition of the benefits that CaaS brings. Organizations leveraging CaaS report faster compliance timelines and reduced administrative burdens, allowing them to focus on core business activities. As compliance frameworks evolve, the ability to adapt quickly becomes crucial. CaaS providers offer automated monitoring and reporting, ensuring that organizations remain aligned with changing regulations.
Experts agree that navigating these regulatory frameworks demands a proactive stance. Andrew Jacobs, Chief Compliance Officer at Avangrid, emphasizes the need for a shift in compliance training towards cultivating an ethical culture, which is vital for long-term success. By partnering with a CaaS provider, organizations gain access to cutting-edge technologies and expertise, positioning themselves to excel in an increasingly regulated environment.
In today’s digital landscape, the importance of cybersecurity cannot be overstated. Organizations face an ever-evolving array of threats that can compromise sensitive data and disrupt operations. Cyber Solutions stands at the forefront of this battle, offering advanced threat detection solutions that leverage cutting-edge technology to identify potential security risks before they escalate.
By continuously monitoring network activity and employing sophisticated analytics, businesses gain invaluable insights into their security posture. This proactive approach not only enhances security but also minimizes the potential impact of cyber incidents. It ensures compliance with cybersecurity standards that are essential for protecting sensitive federal data and maintaining eligibility for government contracts.
Our extensive offerings include:
These are critical components for securing your organization. Moreover, our commitment to employee training on cybersecurity hygiene fortifies your defenses, aligning seamlessly with our Zero Trust approach to security. Have you considered how well your team can recognize suspicious emails? Case studies illustrate the effectiveness of our network hardening strategies and the vital role of training in fostering a robust cybersecurity posture.
In a world where cyber threats are increasingly sophisticated, Cyber Solutions empowers organizations to stay ahead of the curve. Let us help you safeguard your assets and ensure your organization is prepared to face the challenges of tomorrow.
In today’s healthcare landscape, the importance of cybersecurity cannot be overstated. Cyber Solutions offers a robust incident response service designed to minimize damage and ensure swift recovery from cybersecurity incidents. Their comprehensive strategy encompasses:
This enables organizations to resume normal operations quickly. A well-defined incident response strategy is essential; entities with such plans experience an average breach lifecycle of just 189 days, significantly shorter than the 258 days faced by those without. This structured methodology not only mitigates the impact of security breaches but also protects valuable assets.
The company emphasizes customized remediation strategies that address compliance gaps through:
Detailed documentation, including security policies, procedures, and evidence such as incident logs and audit trails, is meticulously prepared to demonstrate compliance during audits, particularly for HIPAA standards. Timely recovery is crucial; companies that regularly test their incident response plans can reduce breach costs by an average of $1.49 million. Furthermore, organizations investing in AI-driven security automation can significantly cut response times, saving an average of $2.22 million per breach. These strategies highlight the necessity of preparedness and proactive measures in an ever-evolving threat landscape.
Real-world examples underscore the effectiveness of rapid recovery. For instance, during a recent ransomware attack, Cyber Solutions’ swift incident response team was on-site within 24 hours, enabling a healthcare provider to restore 4,500 endpoints and enhance their security measures. Organizations that engage in monthly security training can reduce the likelihood of breaches by 60%, while those implementing clear communication protocols during incidents can prevent 21% more secondary breaches caused by mismanaged responses. By prioritizing incident response readiness and regulatory compliance, businesses can build technical resilience and minimize damage during cybersecurity incidents.
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in healthcare. Regular vulnerability evaluations are crucial for systematically identifying potential weaknesses within an entity's IT infrastructure. This thorough assessment of systems and applications allows businesses to prioritize remediation efforts effectively, significantly enhancing their security posture.
Proactive vulnerability assessments not only help prevent data breaches—consider that 60% of breaches stem from unpatched vulnerabilities—but also ensure compliance with industry standards and regulations. As organizations face an increasing array of vulnerabilities, the need for ongoing evaluation becomes essential. By adopting this approach, companies can safeguard sensitive data, including Controlled Unclassified Information (CUI) and Federal Contract Information (FCI), while maintaining eligibility for lucrative government contracts.
Furthermore, integrating Compliance as a Service (CaaS) solutions can enhance this process by providing comprehensive support, including:
This proactive stance reinforces a commitment to operational excellence and regulatory adherence.
In conclusion, the evolving cybersecurity threats demand a robust response. Organizations must not only recognize the risks but also take decisive action to protect their assets and ensure compliance. Are you ready to elevate your cybersecurity strategy?
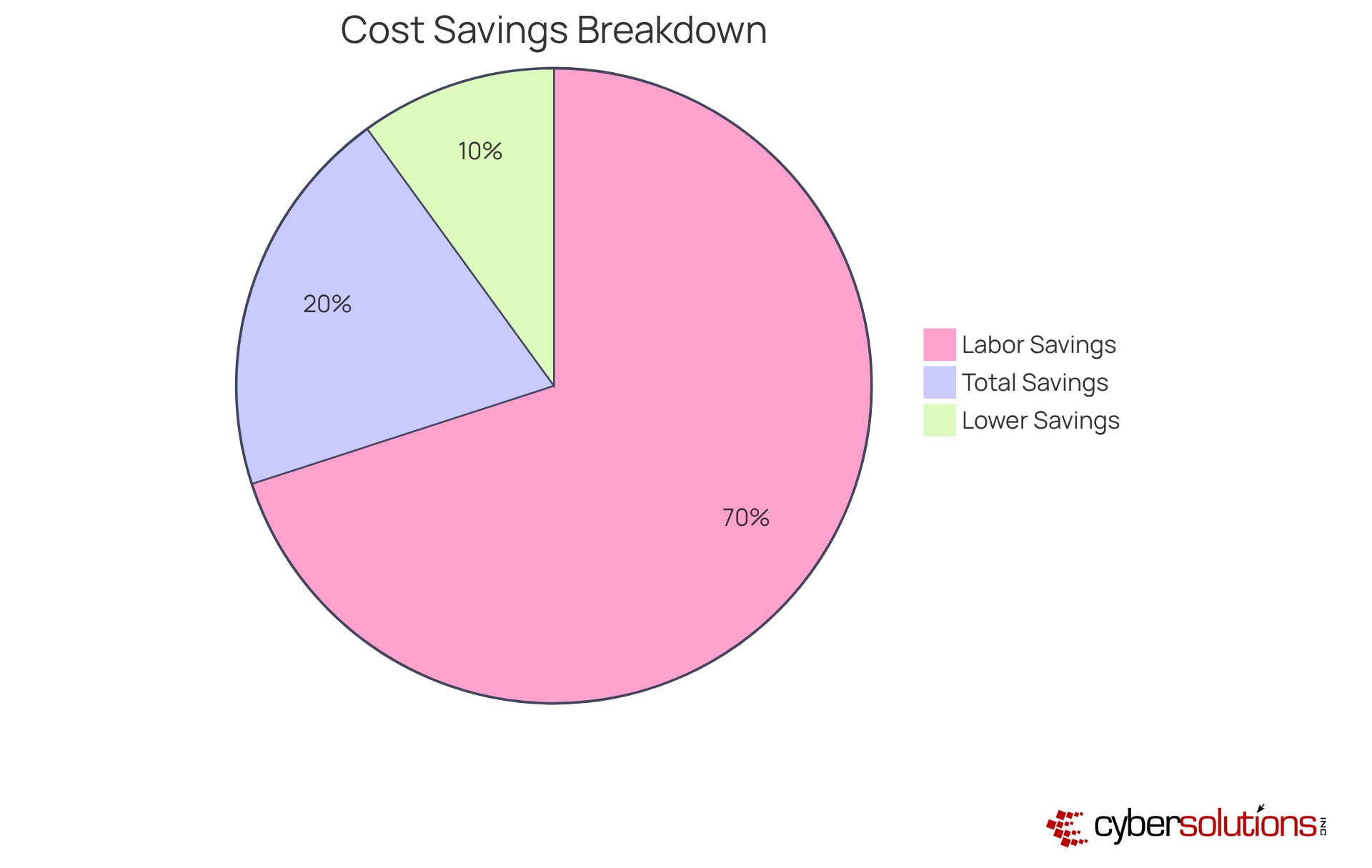
Investing in a managed IT support company such as Cyber Solutions is not just a smart move; it can lead to significant cost savings and a remarkable return on investment (ROI). By outsourcing IT functions, companies can reduce labor expenses by about 70%, translating to nearly $1 million in savings over three years. This strategic approach minimizes downtime and grants access to specialized expertise without the hassle of hiring full-time staff. For example, a non-profit legal membership organization achieved a 70% reduction in monthly operational costs through a cloud-first strategy, showcasing the tangible benefits of outsourcing.
Moreover, companies that utilize a managed IT support company can focus on their core strengths, driving growth and profitability. A Deloitte survey found that more than half of respondents experienced lower-than-expected cost savings from outsourcing, highlighting the critical need to choose the right partner. However, those who engage effectively with managed solution providers (MSPs) often see a marked improvement in quality and operational efficiency. Firms that conduct regular ROI evaluations can better align their outsourcing agreements with strategic objectives, ensuring they not only meet financial metrics but also enhance overall service delivery.
Cyber Solutions simplifies budgeting with a flat-rate pricing model that removes unexpected IT expenses and surprises. This pricing structure encompasses everything from email licenses to advanced cybersecurity, offering peace of mind in one comprehensive package. The flat-rate model not only aids in budgeting but also boosts operational efficiency by allowing businesses to accurately predict their IT costs, facilitating better resource allocation and planning. As Tom Mulvaney, Managing Director at Networks First, aptly states, "ROI is not just a financial number; it should take into account value delivered, management hassle removed, and innovation delivered." This perspective underscores the multifaceted advantages offered by a managed IT support company.
In conclusion, integrating a managed IT support company not only streamlines operations but also empowers organizations to leverage their strengths, ultimately enhancing ROI and securing a sustained competitive edge.
Choosing a managed IT support company is not just a decision; it’s a strategic move that can dramatically boost your business efficiency, security, and resilience in today’s complex digital landscape. In an era where cyber threats are constantly evolving, leveraging specialized expertise and comprehensive services allows organizations to concentrate on their core operations while ensuring robust protection.
Consider the key advantages of managed IT support:
Each of these elements plays a crucial role in minimizing downtime, safeguarding sensitive data, and ensuring compliance with industry regulations. The result? Improved operational performance and peace of mind for businesses.
As organizations face the challenges of modern technology, the significance of adopting managed IT services cannot be overstated. Are you evaluating your current IT strategies? It’s time to consider the benefits of outsourcing to specialized providers. By doing so, you not only enhance your cybersecurity posture but also position your business for sustainable growth and long-term success in a competitive environment.
What services does Cyber Solutions Inc. offer for managed IT support?
Cyber Solutions Inc. offers a comprehensive range of managed IT support services, including endpoint protection, email security, firewalls, and threat detection, tailored to meet the needs of industries like healthcare, finance, manufacturing, and government.
How does managed IT support enhance business efficiency?
Managed IT support allows businesses to focus on their core operations by handling IT management complexities, leading to quicker growth, improved security, and reduced downtime compared to internal IT management.
What is the projected growth of the managed IT support sector?
The managed IT support sector is projected to grow at a compound annual growth rate of 14.1%, reaching a market size of USD 731.08 billion by 2030.
How does Cyber Solutions Inc. ensure continuous business operations?
Cyber Solutions Inc. provides 24/7 help desk support, addressing technical issues promptly to enhance employee productivity and reduce downtime, which directly correlates with increased output and morale.
What are the benefits of having 24/7 help desk support?
Continuous IT support fosters reliability and trust within organizations, allowing employees to focus on their primary responsibilities without worrying about unresolved technical issues. It also improves operational efficiency by proactively detecting anomalies and potential vulnerabilities.
What cybersecurity measures does Cyber Solutions Inc. implement?
Cyber Solutions Inc. employs advanced threat detection systems, robust incident response protocols, regular vulnerability assessments, and a layered security approach to protect sensitive data and ensure compliance with regulations.
How do advanced threat detection systems benefit organizations?
Organizations using advanced threat detection systems can detect breaches an average of 108 days faster than those using traditional methods, significantly reducing costs associated with prolonged exposure to security incidents.
Why are incident response protocols important for organizations?
Incident response protocols are vital for compliance with cybersecurity standards and help minimize potential damage from security incidents, ensuring operational continuity.
What is the impact of strong cybersecurity measures on a company's reputation?
Strong cybersecurity measures foster customer trust and enhance a company's reputation, positioning them as reliable partners. Additionally, 32% of organizations express concern over reputational damage following a cyberattack, highlighting the importance of maintaining robust security.