
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for C-suite leaders. With the increasing frequency and sophistication of cyber threats, healthcare organizations face unique challenges that demand immediate attention. Proactive measures are essential to safeguard sensitive information and protect against potential breaches.
To enhance organizational cybersecurity, it is crucial to implement several key strategies:
These foundational practices significantly reduce cyber threats. Evidence supports the effectiveness of these measures, demonstrating their role in bolstering security and protecting valuable data.
C-suite leaders must recognize that the responsibility for cybersecurity extends beyond IT departments; it requires a comprehensive approach that involves all levels of the organization. By fostering a culture of security awareness and implementing these best practices, leaders can effectively mitigate risks and enhance their organization's resilience against cyber threats. Taking action now not only protects sensitive information but also strengthens the overall integrity of the healthcare system.
In a world where cyber threats are increasingly sophisticated and prevalent, the stakes have never been higher for C-suite leaders tasked with safeguarding their organizations' sensitive information. This article delves into ten essential safe web browsing tips specifically designed for executives, offering practical strategies that not only enhance security but also foster a culture of vigilance among employees. As cybercriminals constantly adapt their tactics, how can leaders ensure their teams are equipped to navigate these treacherous waters effectively? The following insights will illuminate key practices that can significantly bolster an organization's cybersecurity posture.
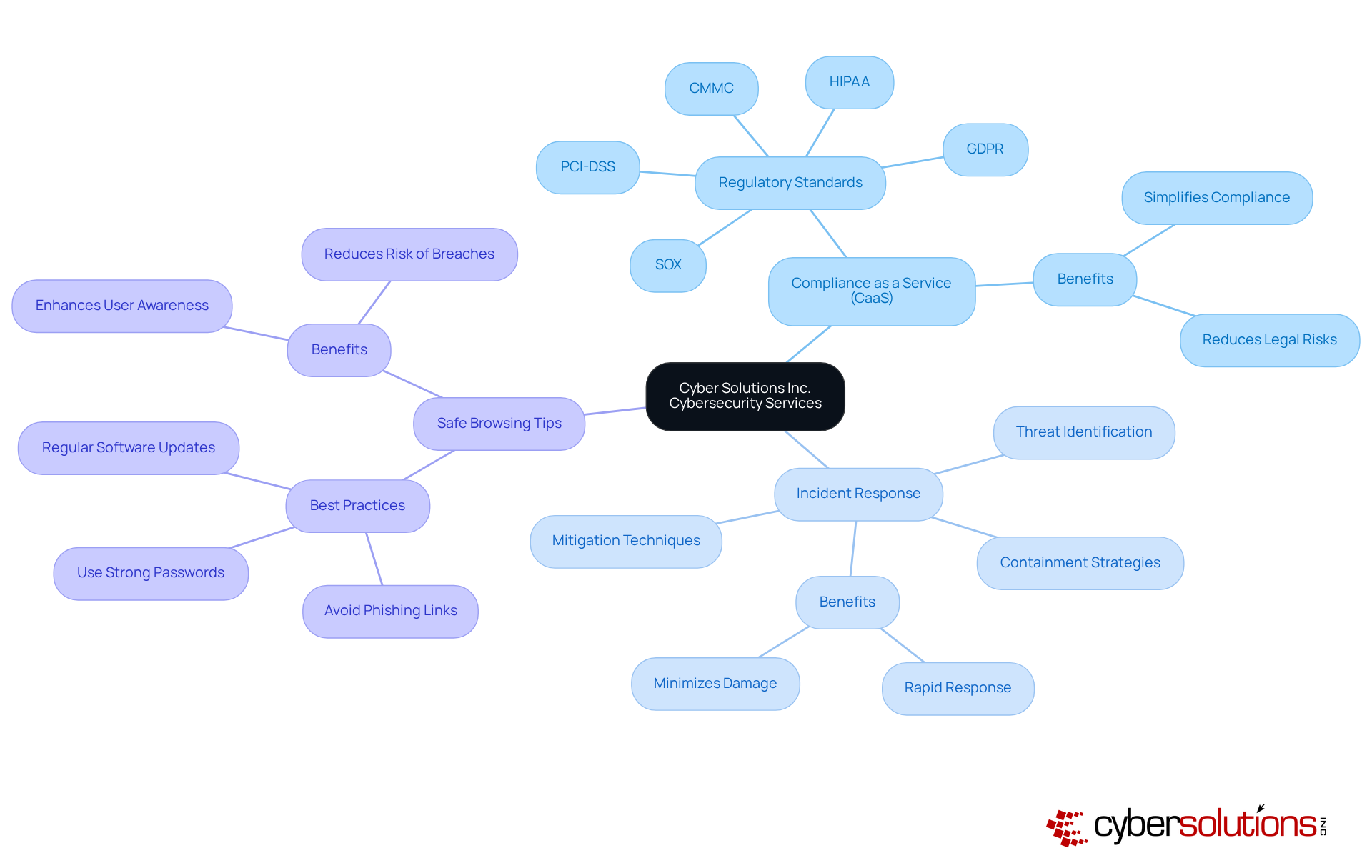
In today's digital landscape, the importance of cybersecurity cannot be overstated. Cyber Solutions Inc. provides a comprehensive range of cybersecurity services designed to offer safe web browsing tips for businesses. With offerings such as Compliance as a Service (CaaS), which simplifies adherence to regulatory standards like HIPAA, PCI-DSS, CMMC, SOX, and GDPR, along with Incident Response solutions that rapidly identify, contain, and mitigate cyber threats, C-suite leaders can ensure their teams are equipped to navigate these challenges securely.
The current landscape of cybersecurity threats poses significant risks for organizations, particularly in sectors where sensitive information is at stake. By utilizing these thorough cybersecurity solutions and following safe web browsing tips, entities can effectively reduce risks linked to web browsing and safeguard sensitive information from emerging cyber threats. This proactive approach not only enhances security but also fosters trust among stakeholders, ultimately supporting business continuity and compliance.
In summary, Cyber Solutions Inc. stands ready to empower businesses with the necessary tools to combat cyber threats, ensuring a secure and compliant operational environment.
Regularly updating your browser is a critical yet straightforward strategy that aligns with safe web browsing tips to bolster cybersecurity. This proactive measure is one of the safe web browsing tips that addresses known vulnerabilities that cybercriminals actively seek to exploit. A recent red team engagement revealed that over 1,000 vulnerabilities were fixed in the latest browser updates, significantly reducing potential attack vectors. C-suite leaders must establish and enforce policies mandating that all employees adhere to safe web browsing tips by updating their browsers to the latest versions. Implementing safe web browsing tips not only mitigates the risk of cyberattacks but also enhances overall organizational security.
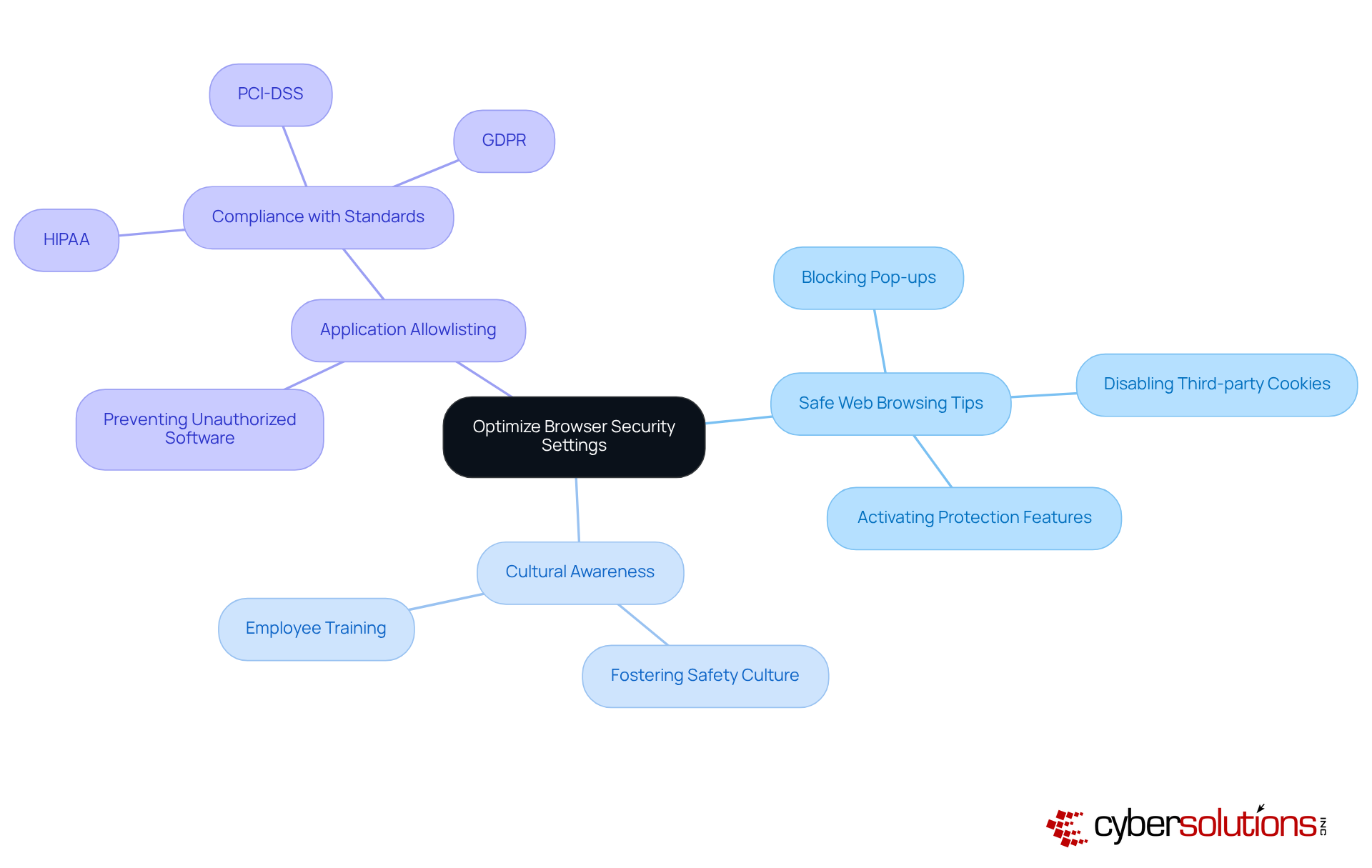
Furthermore, implementing application allowlisting can further strengthen defenses by ensuring that only approved applications run on your network, effectively blocking unauthorized software and malware. Real-world examples, such as the cyber-attack on Suffolk County Council, demonstrate that organizations prioritizing browser updates and application allowlisting have successfully thwarted potential breaches. This reinforces the necessity of these practices in today’s digital landscape. As one expert noted, 'Proactive measures and continuous vigilance are crucial for safeguarding digital assets against evolving threats.

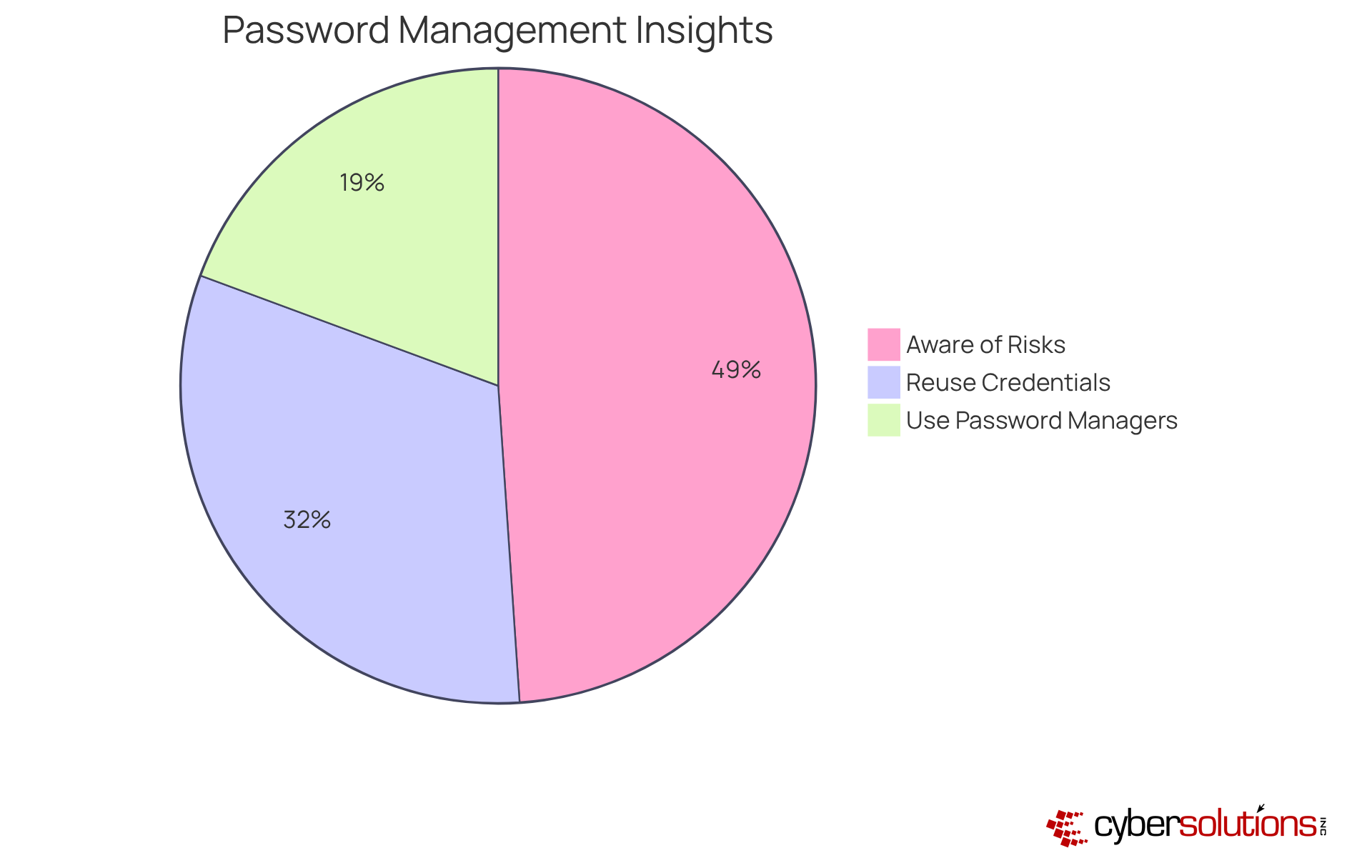
In today's digital landscape, employing robust and distinctive credentials for every account is crucial for protecting sensitive information. C-suite executives must promote the use of credential managers, which not only create complex codes but also keep them secure. This practice effectively minimizes the risk of reusing credentials, a significant vulnerability, as 59% of users still admit to reusing them despite knowing the associated risks. Notably, 91% of users recognize the dangers of reusing credentials, highlighting a concerning gap between understanding and behavior.
Moreover, organizations that adopt credential managers can enhance their overall security stance. These tools support adherence to security frameworks like SOC 2, which require specific credential management practices. Currently, 36% of American adults subscribe to password management services, with 30% utilizing these tools to safeguard their access codes, indicating a growing awareness of their significance.
Cybersecurity specialists emphasize that robust and distinct access keys are essential; however, they also stress that once a key is compromised, its strength becomes meaningless. By utilizing credential managers, entities can not only enhance access code hygiene but also reduce the risks linked to credential theft, which is involved in 49% of all data breaches. Furthermore, 81% of hacking-related breaches in corporate environments arise from weak or reused access credentials. This proactive strategy for credential management is essential for C-suite executives seeking to safeguard their organizations from evolving cyber threats.
Activating two-factor authentication (2FA) across all accounts is imperative for enhancing cybersecurity. In a landscape rife with threats, relying solely on passwords is simply insufficient. 2FA introduces a crucial second layer of verification—such as a text message or an authentication app—making unauthorized access significantly more challenging for attackers.
C-suite leaders must take decisive action by mandating 2FA for all employees, thereby fortifying the organization’s defenses against potential breaches. This proactive measure not only protects sensitive data but also instills confidence among stakeholders regarding the organization's commitment to security.

C-suite leaders must strongly advise employees against using public Wi-Fi for accessing sensitive information. In today's digital landscape, statistics reveal that 73% of remote employees utilize personal devices for work, often connecting to unsecured networks in public spaces. This alarming practice exposes companies to considerable risks, as public Wi-Fi is a frequent target for cybercriminals aiming to capture sensitive data.
If accessing confidential information is unavoidable, employees should consider using a mobile hotspot or a secure VPN connection. Implementing these measures can drastically reduce the likelihood of information interception by malicious actors. Moreover, businesses should proactively instruct their workforce on the risks associated with public Wi-Fi and provide safe web browsing tips to promote the use of company-sanctioned tools and secure connections. This approach not only enhances individual security but also fortifies the overall cybersecurity posture of the organization.

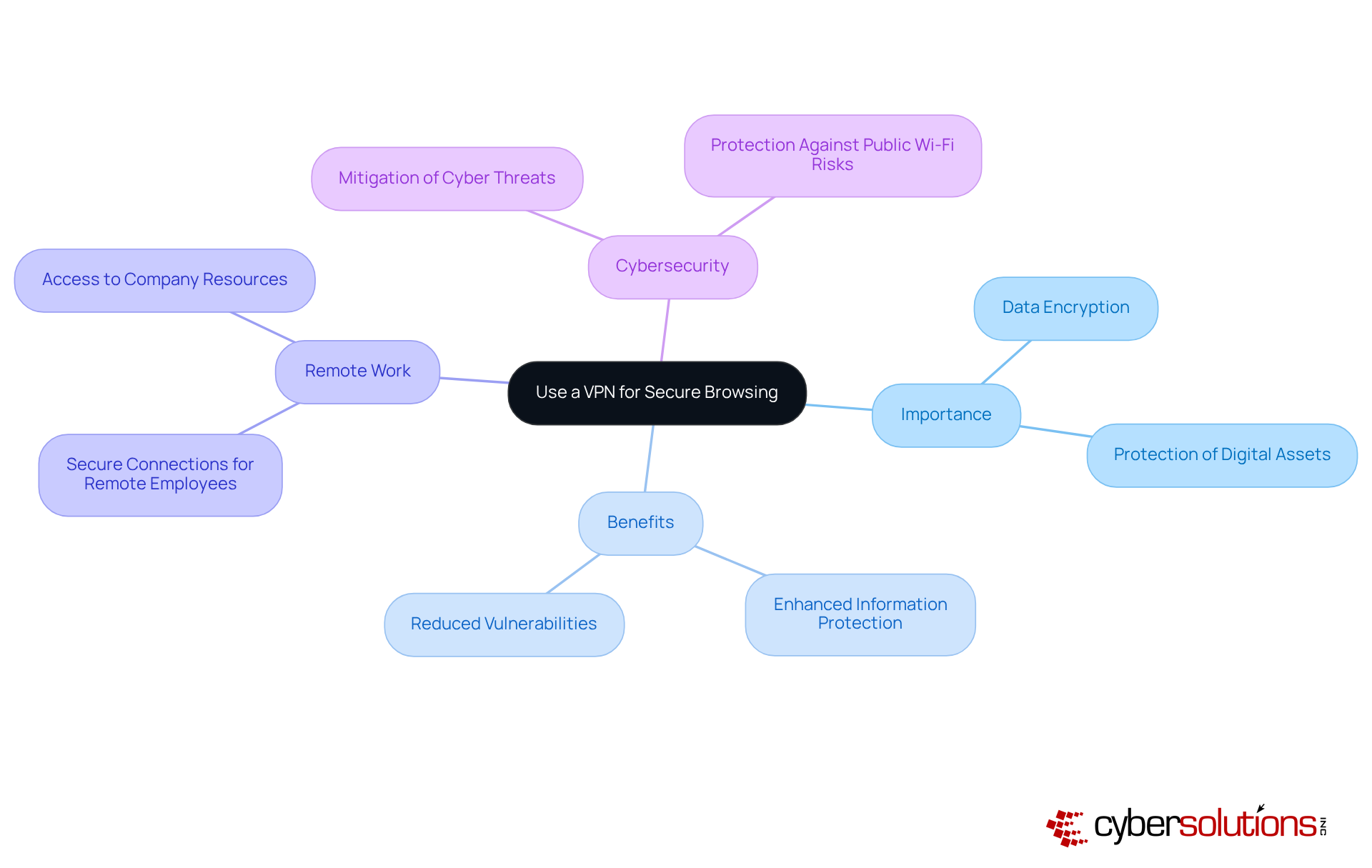
Implementing a VPN is not just a precaution; it is essential for securing internet connections, especially when dealing with sensitive information. In an era where cyber threats are rampant, a VPN encrypts data, significantly reducing the risk of interception by cybercriminals. This makes it an indispensable tool for C-suite leaders who prioritize the protection of their organization’s digital assets.
For organizations with remote employees, VPN solutions do more than just safeguard browsing practices; they bolster overall cybersecurity. Numerous success stories illustrate this point, with businesses reporting enhanced information protection and reduced vulnerabilities following the implementation of VPN technology. As remote work becomes increasingly prevalent, the demand for secure connections grows, ensuring that sensitive company information remains protected, even on public Wi-Fi networks.
By adopting a VPN, leaders can foster a secure digital environment, empowering employees to work confidently from any location. This approach not only preserves the integrity of communications and information but also reinforces the organization's commitment to cybersecurity. In a landscape fraught with challenges, the adoption of VPN technology is a proactive step toward safeguarding the future.
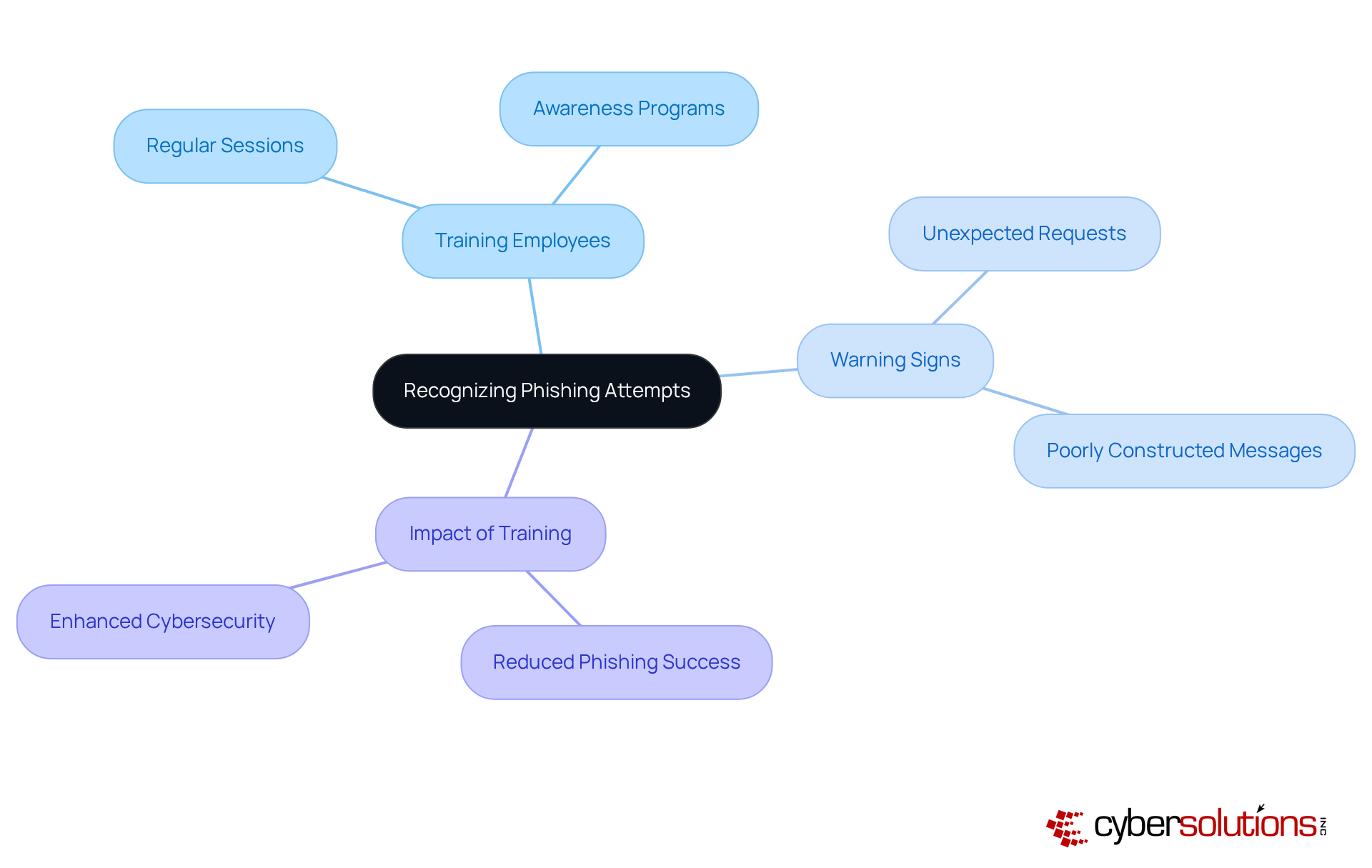
C-suite leaders must prioritize training employees to identify phishing attempts, which frequently manifest as suspicious emails or links. In today's digital landscape, where cyber threats loom large, regular training sessions are essential for equipping staff with the skills to recognize warning signs, such as unexpected requests for sensitive information or poorly constructed messages. This proactive approach is vital in thwarting phishing attacks, particularly when studies indicate that over 15% of employees fall victim to such schemes.
Organizations that have implemented comprehensive awareness training programs have reported significant reductions in successful phishing attempts. This showcases the effectiveness of these initiatives and underscores the importance of fostering a culture of vigilance. By doing so, companies can enhance their overall cybersecurity posture and protect sensitive data from malicious actors. In an era where the stakes are higher than ever, investing in employee training is not just a recommendation; it is a necessity.
Implementing safe web browsing tips, such as customizing browser privacy settings, is essential for safeguarding against malware and various online threats. C-suite leaders must actively foster a culture of awareness regarding safety among employees by encouraging them to review and customize their browser settings, incorporating safe web browsing tips. Key adjustments as safe web browsing tips include:
Research indicates that 76% of Americans believe companies should improve their information protection efforts, underscoring the increasing need for strong protective measures. Furthermore, 92% of Americans express concern about their online privacy, highlighting the necessity for organizations to take proactive measures in this area. Notably, 44% of data breaches involve exposure of personal information, emphasizing the stakes involved in neglecting browser security.
In addition to browser settings, implementing application allowlisting can significantly enhance a company's cybersecurity posture. By allowing only approved applications to run, organizations can proactively prevent malware, ransomware, and unauthorized software from executing. This approach not only reduces the attack surface but also helps meet compliance requirements for standards such as HIPAA, PCI-DSS, and GDPR.
Organizations that implement safe web browsing tips, along with browser protection configurations and application allowlisting, not only reduce risks but also enhance their overall cybersecurity stance. By creating an environment where employees are prepared to handle their browser protection efficiently, companies can greatly lessen their susceptibility to cyber threats by providing safe web browsing tips. C-suite leaders should implement these changes as safe web browsing tips to ensure a safer browsing experience for their teams.
Installing trustworthy protection software is vital for defending against malware and other cyber threats. C-suite leaders must ensure that all devices within the organization are equipped with current protective software, which offers real-time defense against potential attacks. Organizations focusing on endpoint security have noted considerable decreases in breaches, with efficient software solutions able to block more than 90% of recognized malware threats.
The effect of keeping up-to-date protective software cannot be emphasized enough; outdated systems are prime targets for cybercriminals, as they often exploit unpatched vulnerabilities. Entities that neglect to enhance their protective measures encounter a 200% rise in data breaches, highlighting the importance of proactive cybersecurity strategies.
Incorporating application allowlisting into your security framework is a critical step in enhancing your entity's defenses. This approach prevents unauthorized applications from executing and significantly reduces the attack surface, making it harder for attackers to exploit vulnerabilities. By permitting only sanctioned applications to operate, entities can successfully prevent malware, ransomware, and zero-day attacks before they inflict damage. Additionally, application allowlisting supports compliance with regulatory requirements, ensuring that your organization adheres to strict data protection protocols.
Expert insights show that combining advanced protective solutions, such as Next-Generation Antivirus (NGAV) with machine learning capabilities, improves the ability to identify and counteract emerging threats. Organizations employing AI and automation for protection save an average of $2.22 million each year compared to those that do not, demonstrating the financial advantages of adopting advanced protective solutions. These solutions not only safeguard sensitive data but also bolster overall organizational resilience against cyberattacks.
Recent advancements in protective software include features like automated endpoint isolation, which can contain malware and prevent the spread of infections, and secure web gateways, which provide an additional layer of defense by monitoring and filtering web traffic in real time, along with safe web browsing tips. Continuous monitoring of application activity is also crucial, as it ensures immediate identification and blocking of unauthorized software attempts. By implementing these latest protective solutions, including application allowlisting, organizations can significantly reduce the risks linked to malware and ensure a strong cybersecurity stance.

Consistent oversight and evaluation of browser extensions are paramount in maintaining a robust protective posture against cyber threats. C-suite leaders must champion the uninstallation of unnecessary extensions and endorse the exclusive use of those sourced from trusted providers. This proactive strategy significantly mitigates the risk of vulnerabilities that cybercriminals may exploit. For instance, during the Cyberhaven attack, nearly 400,000 users were impacted due to a compromised extension, underscoring the potential hazards of unmonitored browser tools. Furthermore, statistics reveal that a considerable percentage of employees manage browser extensions, frequently without sufficient oversight, leading to security gaps.
To alleviate these risks, organizations should implement comprehensive extension management policies that delineate clear guidelines on approved extensions and conduct regular audits to identify potentially harmful ones. Expert recommendations indicate that thorough inspections of installed extensions, along with ongoing employee education about recognizing risky add-ons, are essential safe web browsing tips for safeguarding sensitive data. By cultivating a culture of vigilance and compliance regarding browser extensions, organizations can fortify their overall security framework and effectively guard against emerging cyber threats.

In a landscape where cyber threats are continually evolving, the imperative for C-suite leaders to prioritize safe web browsing practices cannot be overstated. By adopting a proactive approach to cybersecurity, executives can significantly bolster their organization’s defenses against potential breaches. The strategies outlined here underscore the necessity of implementing robust security measures—from regular browser updates to the use of strong passwords and two-factor authentication—ensuring that sensitive information remains well-protected.
Key insights, such as the importance of:
highlight the multifaceted nature of online security. Each recommendation serves as a crucial component in constructing a comprehensive cybersecurity framework that not only safeguards data but also fosters trust among stakeholders. Organizations that embrace these safe web browsing tips are better equipped to navigate the complexities of the digital landscape.
The significance of these practices extends beyond mere compliance; they embody a commitment to protecting digital assets in a world where security breaches can lead to dire consequences. C-suite leaders are urged to champion these initiatives within their organizations, cultivating a culture of vigilance and responsibility. By taking decisive action and prioritizing cybersecurity, businesses can not only shield their sensitive information but also ensure long-term success and resilience in the face of emerging threats.
What services does Cyber Solutions Inc. provide for cybersecurity?
Cyber Solutions Inc. offers a comprehensive range of cybersecurity services, including Compliance as a Service (CaaS) for regulatory adherence and Incident Response solutions to identify, contain, and mitigate cyber threats.
Why is it important for organizations to follow safe web browsing tips?
Following safe web browsing tips helps organizations reduce risks associated with web browsing, safeguard sensitive information, enhance security, foster trust among stakeholders, and support business continuity and compliance.
How can regularly updating a browser improve cybersecurity?
Regularly updating a browser addresses known vulnerabilities that cybercriminals exploit, significantly reducing potential attack vectors and enhancing overall organizational security.
What is application allowlisting and how does it contribute to cybersecurity?
Application allowlisting is a security practice that ensures only approved applications run on a network, effectively blocking unauthorized software and malware, thereby strengthening defenses against cyber threats.
What is the significance of using strong passwords for online accounts?
Using strong and unique passwords for every account is crucial for protecting sensitive information and minimizing the risk of credential theft, which is involved in a significant percentage of data breaches.
How can credential managers enhance security for organizations?
Credential managers create complex passwords and securely store them, reducing the risk of reusing credentials and helping organizations adhere to security frameworks that require specific credential management practices.
What statistics highlight the risks associated with weak or reused passwords?
59% of users admit to reusing credentials despite knowing the risks, and 81% of hacking-related breaches in corporate environments arise from weak or reused access credentials.
What proactive strategies can C-suite executives implement to safeguard their organizations from cyber threats?
C-suite executives can implement safe web browsing tips, enforce browser updates, utilize application allowlisting, and promote the use of credential managers to enhance security and protect against evolving cyber threats.