
C-suite leaders must recognize the urgent need for custom business software to enhance operational efficiency and security—two critical elements in today’s competitive and rapidly evolving market. Tailored software solutions not only streamline processes but also optimize data management and integrate advanced security features. This approach effectively addresses unique business challenges while ensuring compliance with industry regulations.
In an environment where cybersecurity threats are increasingly sophisticated, the implications for organizations are profound. Customized software can mitigate these risks, allowing businesses to operate with confidence. By investing in such solutions, C-suite leaders can safeguard their operations and maintain a competitive edge.
Ultimately, the call to action is clear: to thrive in this landscape, organizations must adopt tailored software solutions that not only enhance efficiency but also fortify their security posture. The time for action is now.
In an era where digital transformation is not merely an option but an imperative, C-suite leaders confront the urgent challenge of ensuring their organizations remain both competitive and secure. Custom business software emerges as a pivotal solution, providing tailored functionalities that align seamlessly with unique operational needs.
As the landscape evolves, one must consider: how can these bespoke solutions not only streamline processes but also enhance decision-making and fortify cybersecurity?
Delving into the compelling reasons for investing in custom software reveals a pathway to not only meet current demands but also to future-proof businesses against emerging challenges.
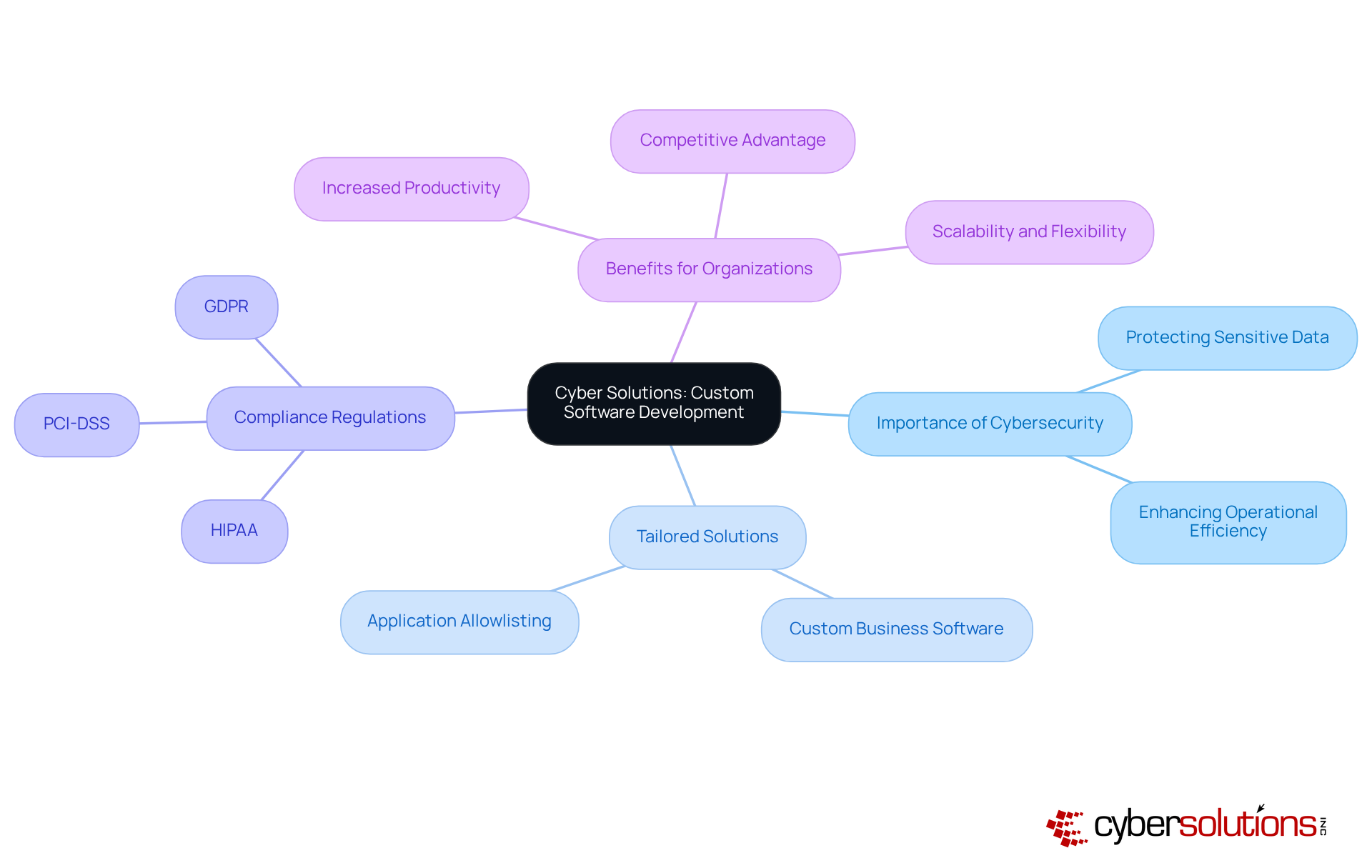
In today's rapidly evolving digital landscape, the significance of cybersecurity cannot be overstated, particularly within the healthcare sector. Cyber Solutions Inc. stands at the forefront of addressing the unique challenges faced by organizations by developing custom business software that is meticulously tailored to meet their distinct needs. By gaining a comprehensive understanding of the specific obstacles that healthcare providers encounter, Cyber Solutions creates bespoke applications that not only enhance operational efficiency but also bolster security measures.
This personalized approach streamlines workflows, optimizes data management, and ensures compliance with stringent industry regulations, including cybersecurity standards such as:
One pivotal aspect of our security framework is application allowlisting, which proactively prevents unauthorized applications from executing. This not only safeguards sensitive data but also reinforces compliance with these critical regulations.
As the demand for personalized applications surges—forecasts indicate that up to 70% of new enterprise programs will be developed using Low Code/No Code platforms by 2025—organizations are increasingly recognizing the necessity of investing in custom business software solutions. Industry leaders assert that such investments can yield substantial productivity improvements. By leveraging custom business software, companies can enhance their operations, adapt to market fluctuations, and maintain a competitive edge in an ever-changing environment.
Moreover, integrating advanced security features, such as application allowlisting tailored to an organization's specific risk profile, is essential. This ensures that custom approaches not only meet operational needs but also protect sensitive information effectively. As organizations navigate the complexities of cybersecurity, Cyber Solutions Inc. offers the expertise and innovative solutions necessary to thrive in this challenging landscape.
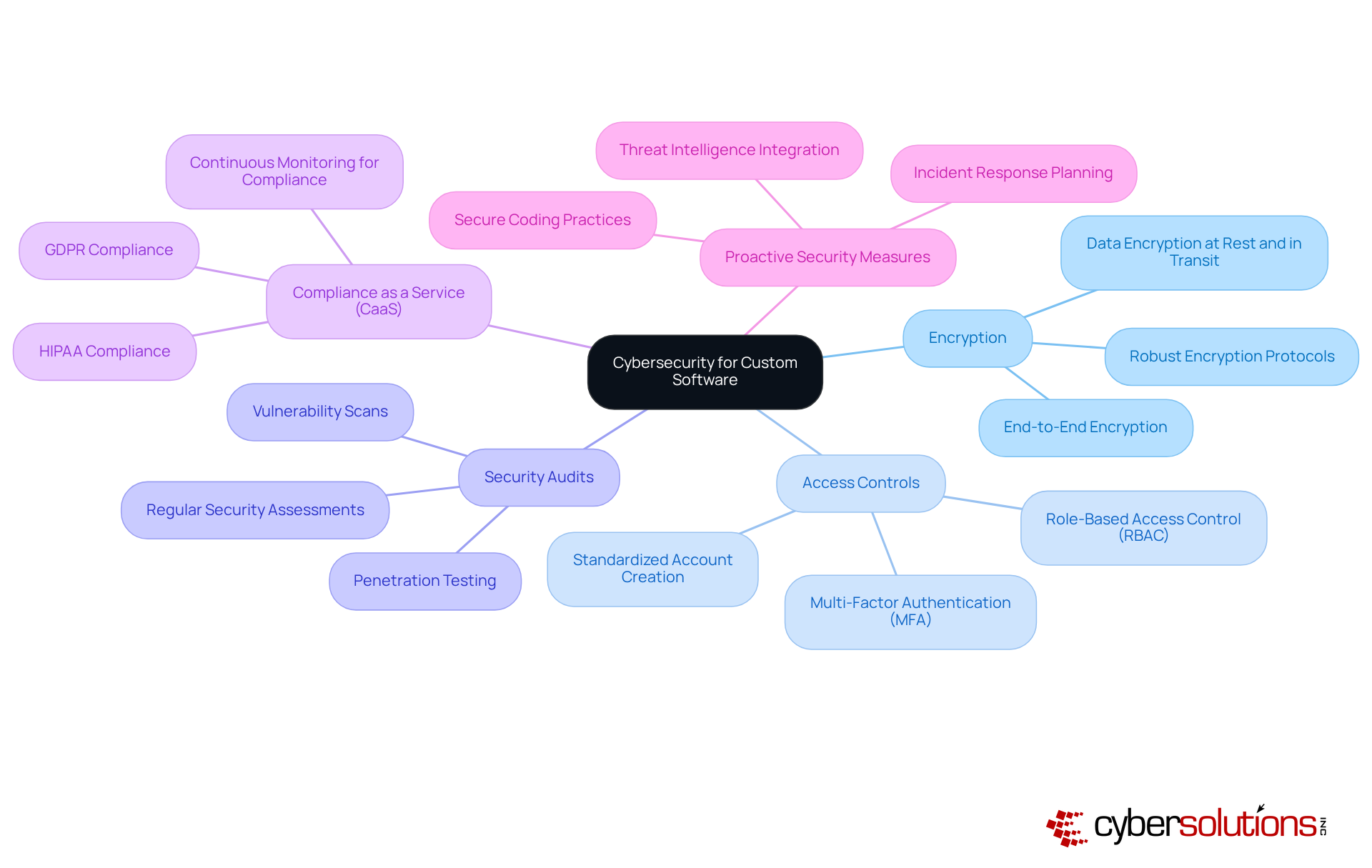
Custom business software provides tailored technology solutions that empower companies to streamline repetitive manual tasks, such as data entry and reporting. By optimizing these processes, organizations can liberate valuable employee time, enabling teams to concentrate on more strategic initiatives. Automation not only boosts productivity but also mitigates the risk of human error, resulting in more accurate and reliable outcomes. This evolution in operational efficiency is not merely advantageous; it is essential for organizations aiming to thrive in an increasingly competitive landscape.
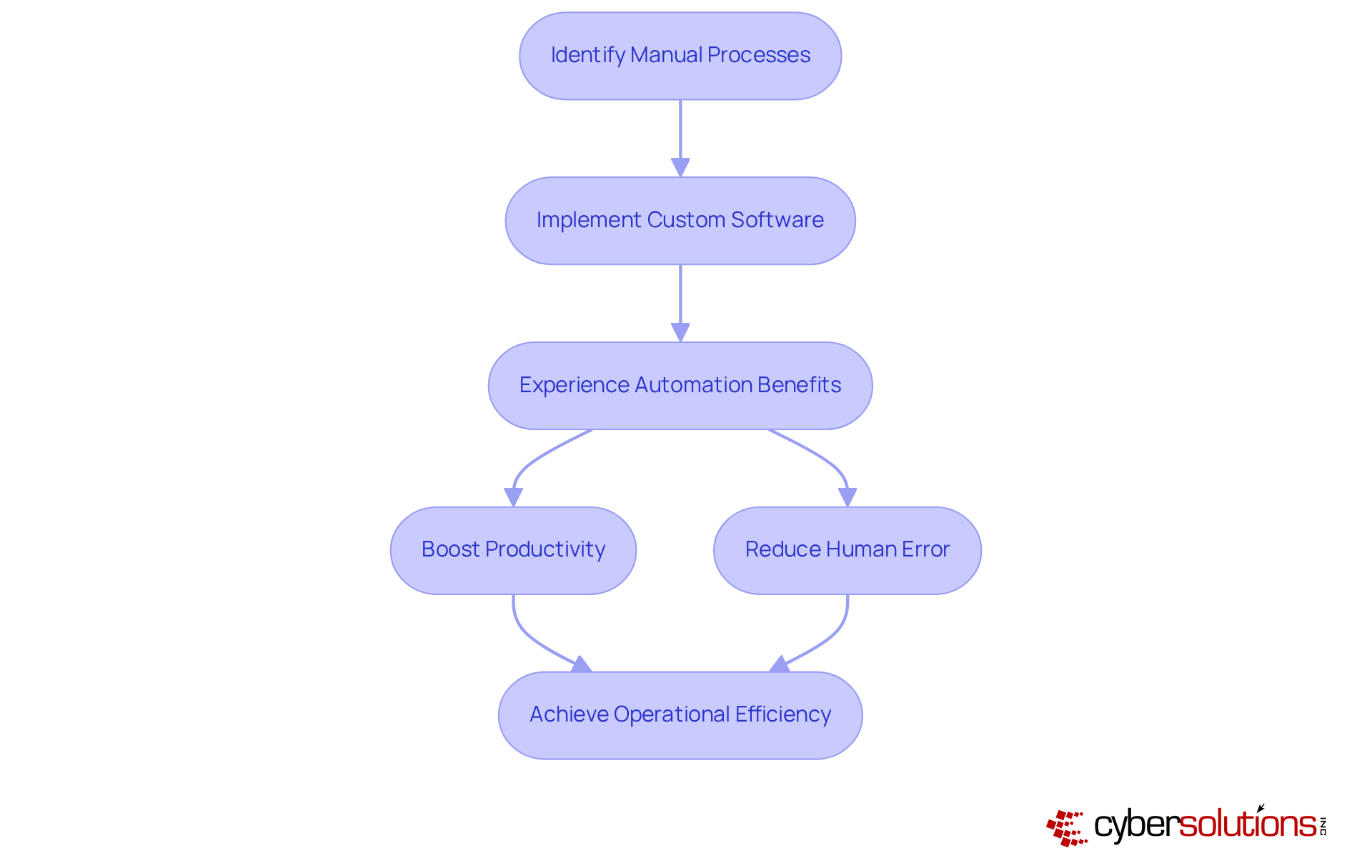
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for custom business software designed for organizations. These applications can be meticulously crafted with advanced security features tailored to address unique vulnerabilities. This involves implementing robust encryption protocols, stringent access controls, and conducting regular security audits to identify and rectify potential weaknesses. By integrating security into the development lifecycle, organizations can significantly mitigate the risk of data breaches and ensure compliance with regulatory standards such as GDPR and HIPAA.
Cybersecurity experts emphasize a proactive approach to security; as one expert noted, "Security isn’t just a box to check at the end of development—it’s something that should be woven into every step of the process." Furthermore, the integration of Compliance as a Service (CaaS) offers businesses comprehensive solutions to meet regulatory requirements, encompassing assessments, policy development, audit preparation, and continuous monitoring. Frequent updates and security evaluations are essential for preserving system integrity against emerging threats.
Moreover, implementing application allowlisting can proactively prevent unauthorized programs from executing, thereby reducing vulnerabilities and ensuring compliance with stringent standards. This tailored approach not only safeguards sensitive information but also enhances overall operational resilience, making custom business software a crucial investment for enterprises aiming to protect their assets in an increasingly intricate digital environment.
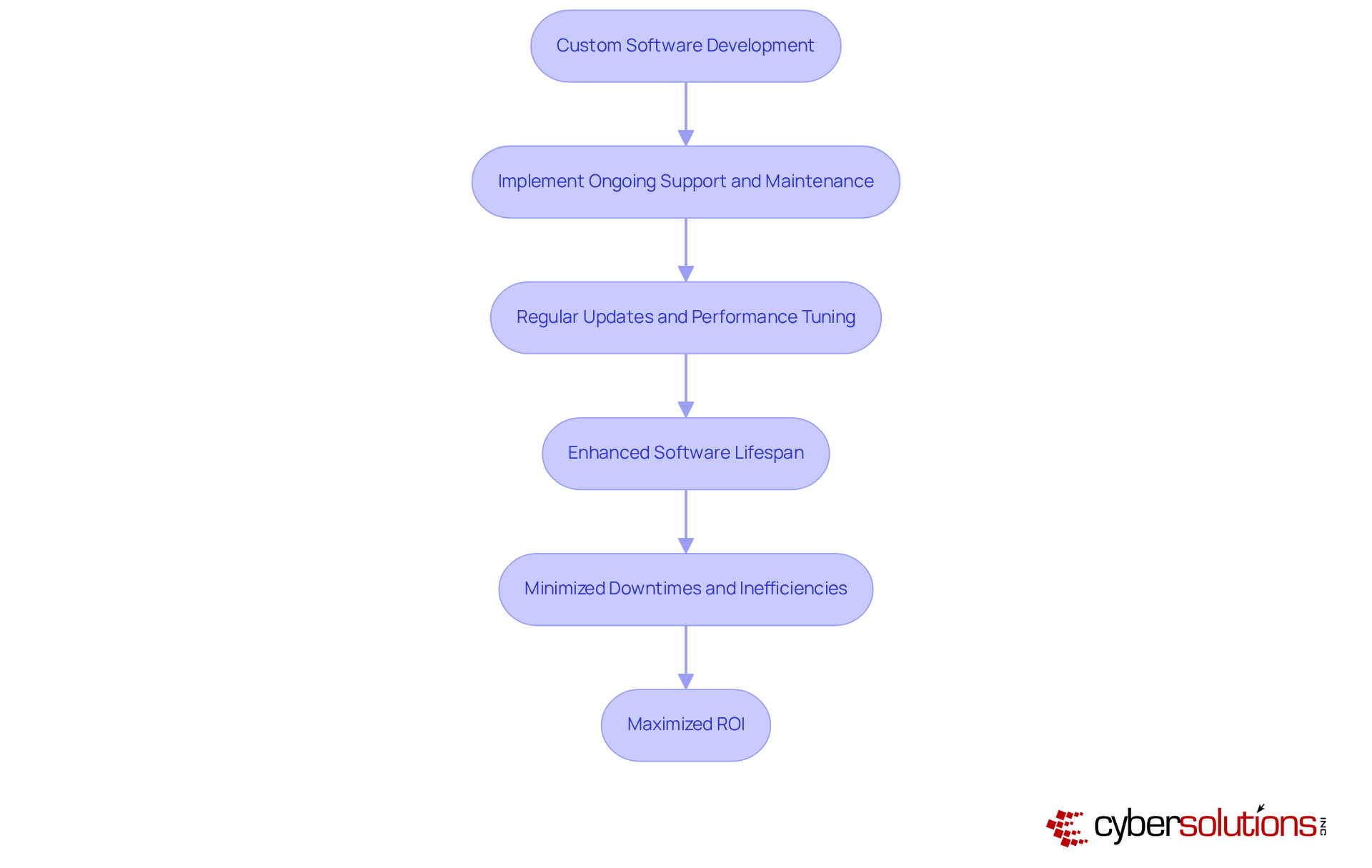
Investing in custom business software development demands a steadfast commitment to ongoing support and maintenance. Regular updates are not merely beneficial; they are essential for keeping applications functional and secure, enabling them to adapt to the ever-evolving landscape of business needs and technological advancements. This proactive approach not only extends the system's lifespan but also maximizes return on investment by minimizing costly downtimes and inefficiencies. Consider a well-crafted maintenance schedule: it acts as a safeguard, preventing minor issues from escalating into major technological crises, thus significantly lowering long-term costs.
Moreover, the average lifespan of custom business software can be dramatically enhanced through consistent updates and performance tuning, ensuring it remains relevant and effective in a rapidly changing digital environment. As emerging technologies such as AI and cloud computing reshape IT maintenance strategies, organizations that prioritize these practices are better positioned to leverage their applications for sustained growth and a competitive advantage. Industry specialists emphasize that 'Ongoing maintenance and support are crucial to the success of a tailored app.' Neglecting these critical aspects can lead to frustrated users, diminished productivity, and lost sales, highlighting the urgent necessity for a robust maintenance strategy.
Small enterprises must actively evaluate custom business software when facing inefficiencies in their current systems. Common indicators of these inefficiencies include:
For instance, teams often find themselves investing hours re-entering data and managing various applications, leading to frustration and wasted resources. Recognizing these signs early is essential; businesses that neglect to address operational bottlenecks risk stagnation and may struggle to adapt as they grow.
Industry specialists indicate that a trend of low workflow efficiency frequently signals the need for custom business software that can optimize processes and enhance productivity. By investing in custom business software, organizations can align their technology with unique operational needs, ultimately positioning themselves for sustainable growth and enhanced service delivery.
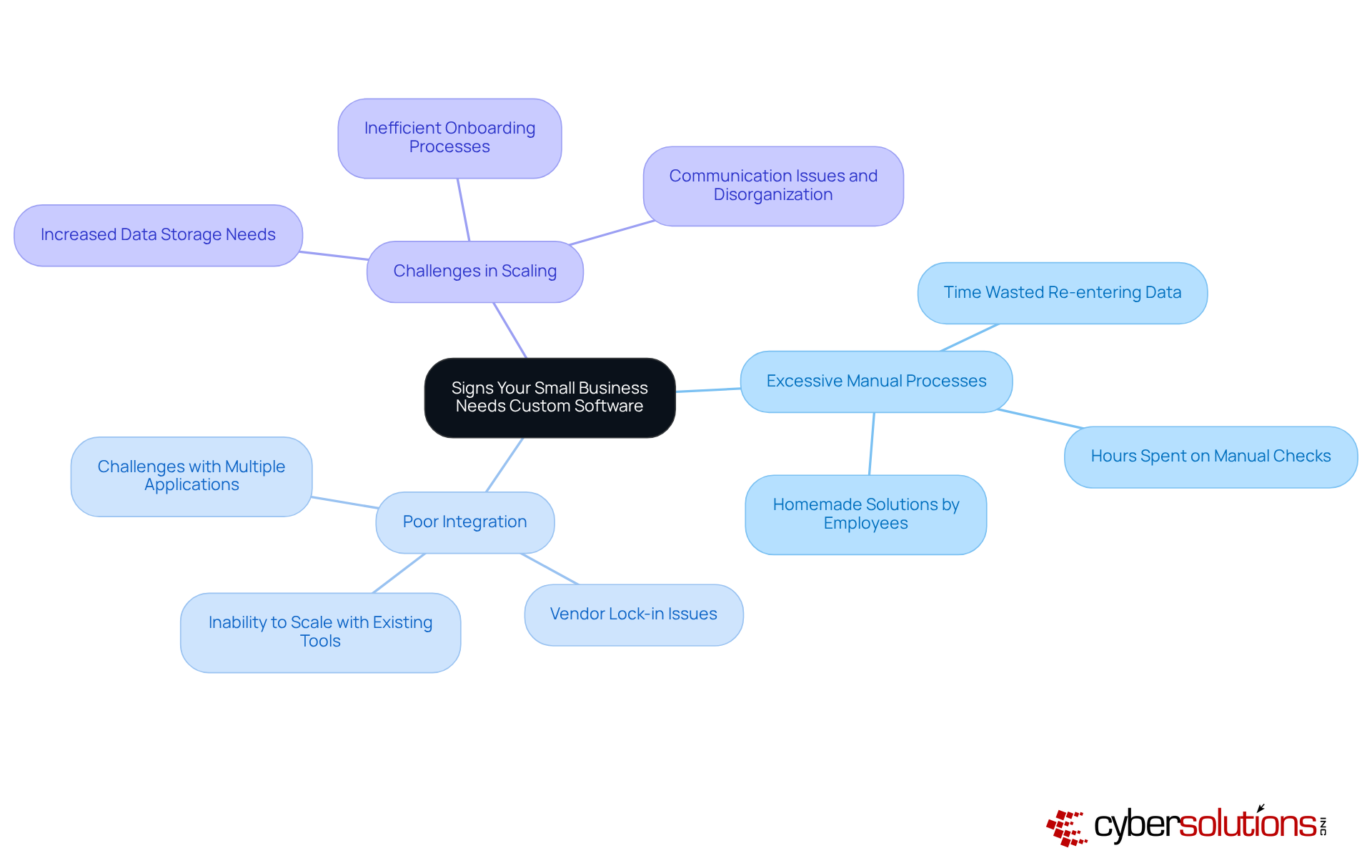
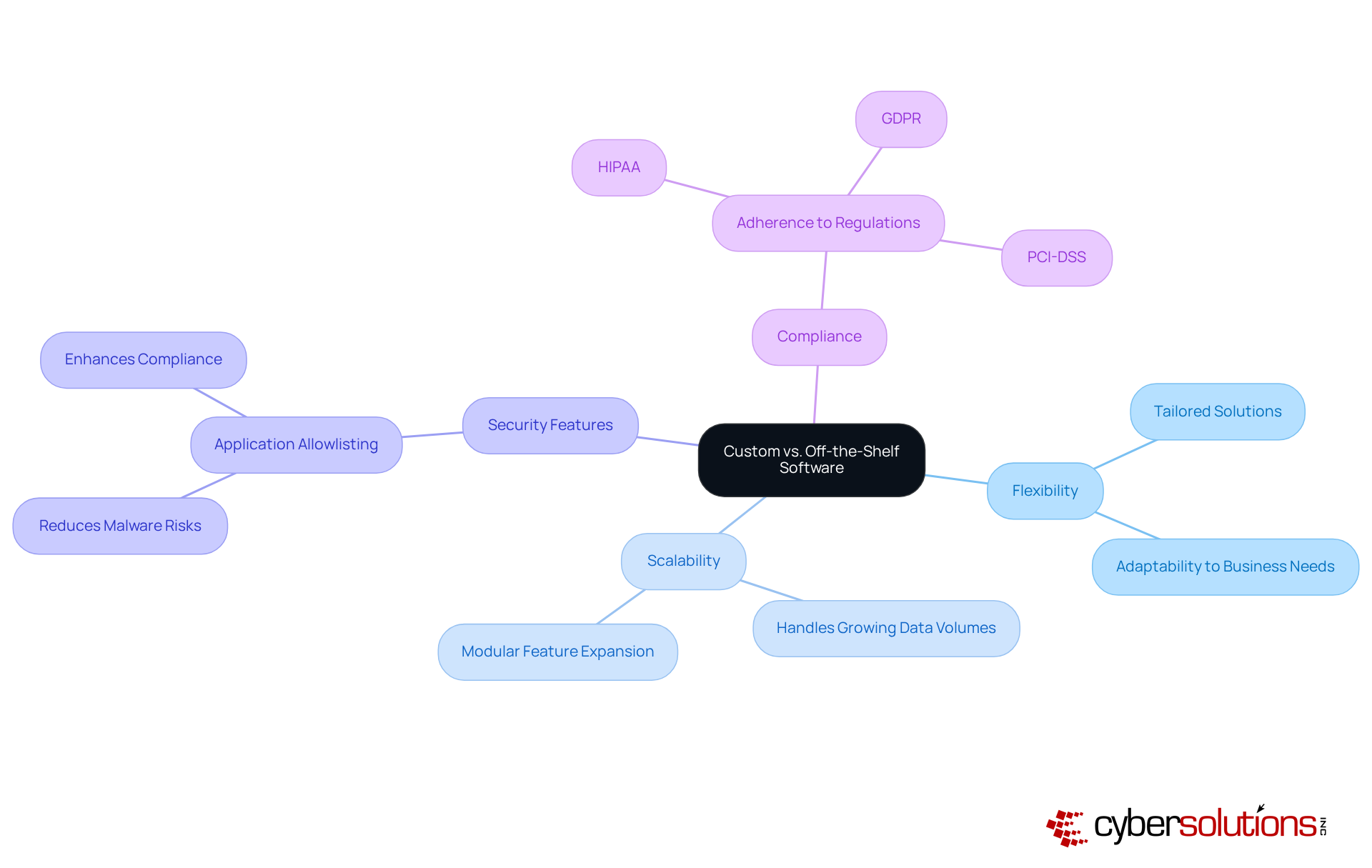
In today's digital landscape, cybersecurity has become a paramount concern, particularly for healthcare organizations. While off-the-shelf applications may offer prompt solutions, they frequently lack the flexibility and customization essential for companies seeking to scale efficiently with custom business software. Custom business software is meticulously crafted to align with specific organizational needs, enabling seamless integration with existing systems and processes. This tailored approach not only enhances scalability but also facilitates the incorporation of advanced security features, such as application allowlisting.
Application allowlisting is a proactive measure that significantly reduces the risk of malware, ransomware, and compliance issues by ensuring that only approved applications can run. This strategy is particularly vital for organizations striving to adhere to stringent regulatory requirements, including HIPAA, PCI-DSS, and GDPR. By continuously monitoring application activity, organizations can detect and block unauthorized attempts, thus fortifying their defenses against cyber threats.
Moreover, deploying tailored programs that incorporate application allowlisting guarantees a robust defense, making personalized approaches a more secure and strategic option in the long term. As healthcare CFOs navigate the unique challenges of cybersecurity, the necessity for custom solutions that address these vulnerabilities becomes increasingly clear. Investing in such tailored applications not only safeguards against potential breaches but also supports the overall integrity and trustworthiness of healthcare services.
Minor enterprises stand to gain significantly from custom business software applications, especially in areas like Customer Relationship Management (CRM) and Enterprise Resource Planning (ERP). These systems can be meticulously customized as custom business software to align with each organization's specific workflows and processes, ensuring optimal efficiency and effectiveness. For instance, tailored CRM systems simplify customer interactions and enhance sales processes, while ERP systems integrate various organizational functions, providing a comprehensive view of operations.
Current trends reveal that:
Industry leaders highlight the transformative effect of these systems. As one expert noted, 'Custom business software aligns with unique workflows, automates tasks, and scales with business growth, providing a competitive edge.' This perspective reflects a broader understanding that customized approaches not only enhance operational efficiency but also foster long-term growth and adaptability in a rapidly changing market landscape.
Furthermore, research indicates that users of custom business software experience a 20% to 30% reduction in operational expenses within the initial years, further solidifying the case for custom business software solutions. The projected cost range for CRM or ERP for small enterprises is between $15,000 and $40,000, a critical consideration for C-suite leaders evaluating these investments. Organizations can also expect a return on investment of two to three times within three to five years, reinforcing the financial benefits of investing in tailored solutions.
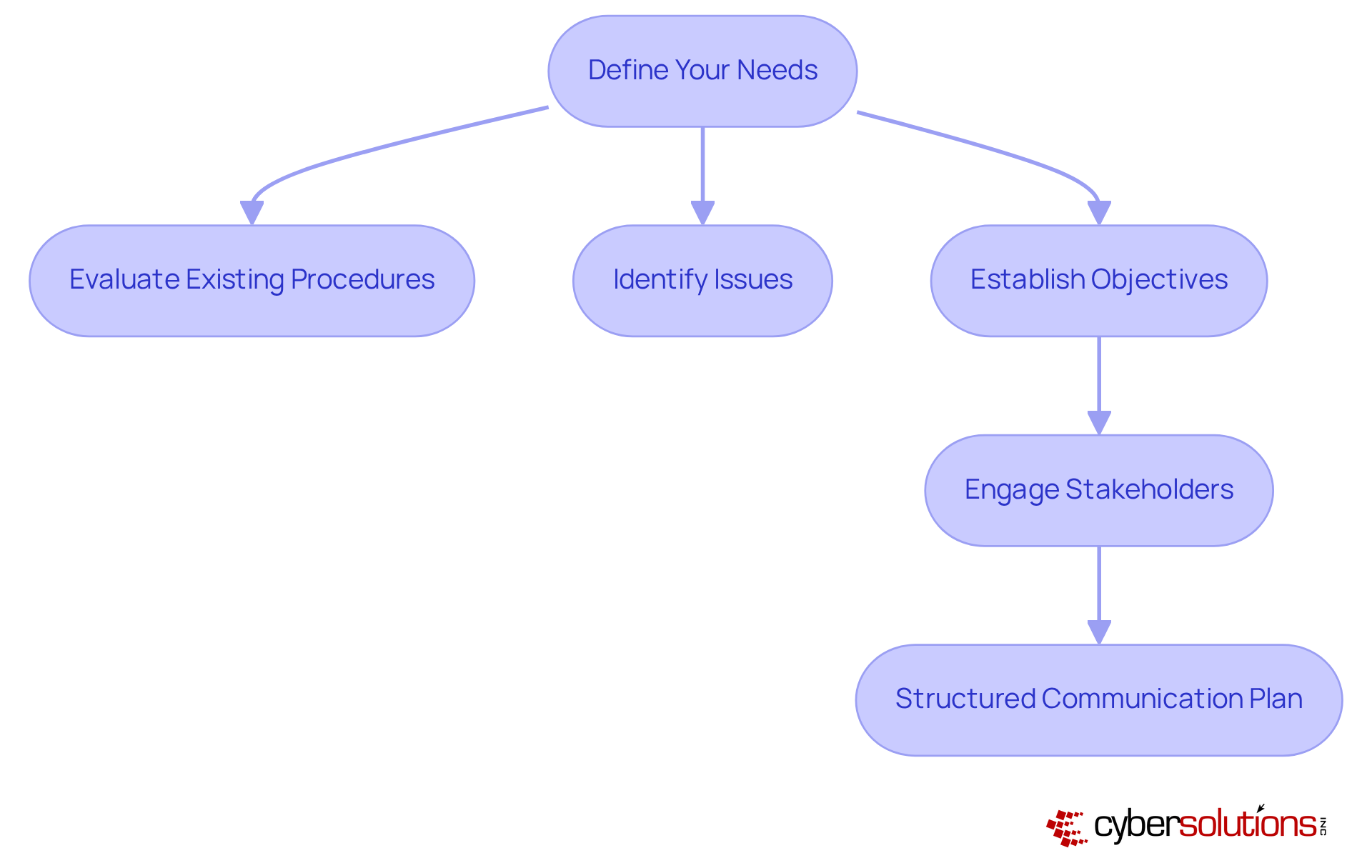
Before embarking on custom business software development, it is crucial for companies to clearly outline their requirements. This begins with a comprehensive evaluation of existing procedures, identifying issues, and establishing precise objectives for the application. Engaging stakeholders in this process is essential, as it ensures that the final product aligns with the overall business strategy and meets user expectations. Effective stakeholder engagement significantly enhances development success rates; it fosters collaboration and trust among all parties involved.
Consider this: companies that actively involve stakeholders in early requirement gathering sessions often experience smoother project execution and reduced risks of scope creep. As noted by industry experts, 'Software implementations involve more than just technology - they are organizational change projects.' This perspective underscores the importance of aligning custom business software with the diverse requirements of stakeholders, ultimately resulting in more effective and user-friendly outcomes.
Furthermore, a structured communication plan is indispensable for managing stakeholder expectations throughout the project lifecycle. This approach ensures that all voices are heard and considered, contributing to a more cohesive and successful development process.
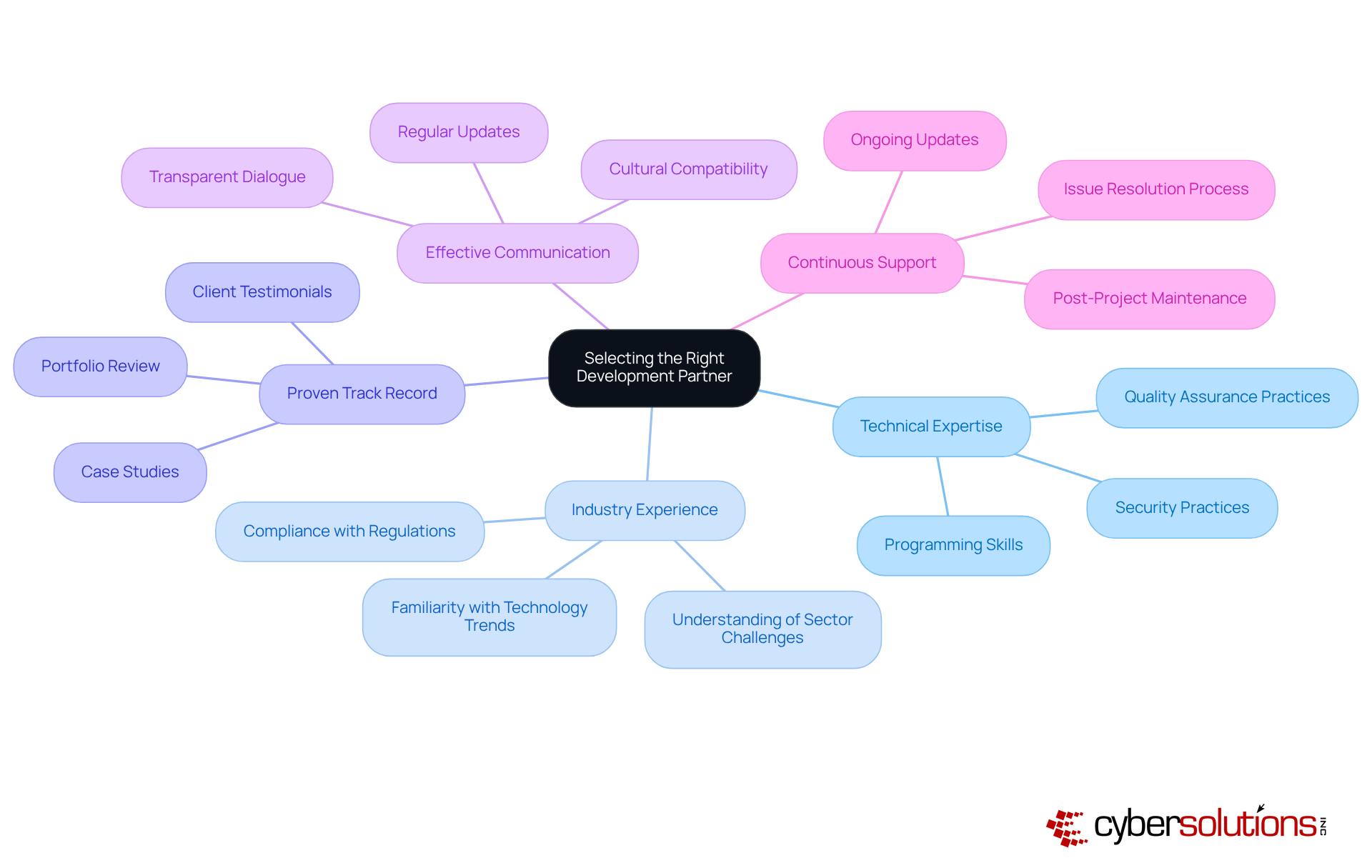
Selecting the right development partner for custom software is paramount for organizational success. Key factors to consider include:
Effective communication and a collaborative approach to project management are essential for ensuring alignment with your business objectives. As Stoyan Mitov, CEO of Dreamix, emphasizes, the right partner can navigate IT complexities and optimize expenses, delivering high-quality results that enhance operational efficiency.
Moreover, industry-specific knowledge cannot be overlooked; partners with a profound understanding of your sector can anticipate challenges and propose effective solutions, ensuring compliance with regulations and alignment with strategic goals. It is critical to recognize that poor communication accounts for 60% of project failures, highlighting the necessity for clear and consistent dialogue throughout the partnership.
Additionally, continuous support and maintenance following project completion are vital for long-term success, as they help address any issues that may arise and ensure the system remains up-to-date. Successful collaborations often lead to significant improvements in project outcomes, underscoring the importance of careful selection in the development process. To reinforce your decision, consider establishing clear expectations and regular check-ins with your partner to maintain alignment and cultivate a productive relationship.
Investing in tailored applications is not merely a response to immediate organizational needs; it is a strategic move that equips entities to tackle future challenges. These bespoke solutions are meticulously crafted with scalability at their core, enabling organizations to swiftly adjust to shifting market dynamics and technological innovations. Such adaptability is vital for sustaining competitiveness and effectively addressing customer expectations.
Consider this:
As organizations navigate an increasingly volatile landscape, the capacity to integrate emerging technologies and respond adeptly to market fluctuations becomes essential. Thus, custom business software emerges as a crucial element of strategies aimed at future-proofing, ensuring that businesses remain resilient and poised for growth.
Investing in custom business software is no longer a luxury; it is an absolute necessity for C-suite leaders who aim to navigate the complexities of today’s digital landscape. Tailored solutions not only address unique operational challenges but also provide a competitive advantage by enhancing efficiency, security, and adaptability. As organizations face increasing demands for personalized applications, the shift towards custom software development becomes imperative to effectively meet specific business needs.
Throughout this article, key points have been underscored, including the critical role of custom software in:
Recognizing the signs that indicate the need for custom solutions—such as inefficiencies and poor integration—has been emphasized. Moreover, the advantages of custom software over off-the-shelf solutions, particularly regarding scalability and compliance, reinforce the argument for tailored approaches in business operations.
Ultimately, as organizations strive to future-proof their operations, the adoption of custom business software emerges as a strategic move that not only addresses current challenges but also prepares businesses for future growth. By investing in tailored solutions, C-suite leaders can ensure their organizations remain resilient and responsive to evolving market demands. The time to act is now; embracing custom software is essential for fostering innovation, enhancing productivity, and securing a sustainable competitive edge in an ever-changing business environment.
What is the primary focus of Cyber Solutions Inc.?
Cyber Solutions Inc. focuses on developing custom business software tailored to the unique needs of organizations, particularly in the healthcare sector, to enhance operational efficiency and bolster security measures.
How does Cyber Solutions Inc. ensure compliance with industry regulations?
Cyber Solutions ensures compliance with industry regulations such as HIPAA, PCI-DSS, and GDPR by creating bespoke applications that streamline workflows, optimize data management, and integrate security features like application allowlisting.
What is application allowlisting and why is it important?
Application allowlisting is a security measure that prevents unauthorized applications from executing, safeguarding sensitive data and reinforcing compliance with critical regulations.
What is the trend regarding custom software development by 2025?
By 2025, it is forecasted that up to 70% of new enterprise programs will be developed using Low Code/No Code platforms, indicating a growing demand for personalized applications.
How does custom software improve operational efficiency?
Custom software automates repetitive manual tasks, such as data entry and reporting, freeing up employee time for strategic initiatives, boosting productivity, and reducing the risk of human error.
What advanced security features can be integrated into custom software?
Advanced security features for custom software can include robust encryption protocols, stringent access controls, regular security audits, and application allowlisting to address unique vulnerabilities.
What is the significance of integrating security into the software development lifecycle?
Integrating security into the development lifecycle is essential for mitigating the risk of data breaches and ensuring compliance with regulatory standards, as security should be a continuous focus rather than a final checklist item.
What is Compliance as a Service (CaaS)?
Compliance as a Service (CaaS) offers businesses comprehensive solutions to meet regulatory requirements, including assessments, policy development, audit preparation, and continuous monitoring.
Why is it essential for organizations to invest in custom business software solutions?
Investing in custom business software solutions is essential for organizations to enhance operations, adapt to market changes, maintain a competitive edge, and effectively protect sensitive information in a complex digital environment.