
The article underscores the pivotal role of Endpoint Detection and Response (EDR) in contemporary cybersecurity, especially for C-suite leaders. It highlights the necessity of EDR in identifying and addressing sophisticated cyber threats, a concern that cannot be overstated in today's digital landscape. Key functionalities of EDR include:
These elements collectively bolster an organization's cybersecurity posture. Furthermore, the implementation of EDR not only enhances security measures but also significantly mitigates the financial repercussions of potential breaches.
As cyber threats continue to evolve in both complexity and frequency, organizations find themselves at a critical juncture where traditional security measures fall short. Endpoint Detection and Response (EDR) technology emerges as an essential tool in this landscape, providing real-time monitoring, automated responses, and in-depth forensic analysis to combat sophisticated attacks. Yet, as reliance on EDR solutions increases, C-suite leaders face a pressing question:
In today's rapidly evolving digital landscape, the EDR endpoint serves as a critical pillar in advanced cybersecurity technology. Designed to oversee, identify, and respond to threats across terminal devices—including laptops, desktops, and servers—EDR endpoint solutions continuously collect and analyze data from these endpoints. This process enables the detection of suspicious activities, equipping teams with essential tools for investigation and remediation. Given the current risk environment, where traditional security measures frequently falter against sophisticated attacks, adopting a proactive strategy through an EDR endpoint is not just beneficial; it is imperative.
EDR technology not only identifies threats but also automates responses, significantly minimizing the time and effort required to mitigate risks. Key features of EDR include:
Collectively, these functionalities enhance an organization's overall cybersecurity posture. As cyber threats become more sophisticated, the integration of EDR endpoint solutions is essential for organizations striving to safeguard sensitive data while ensuring compliance with regulatory mandates.
Moreover, comprehensive 24/7 network monitoring and alert services are indispensable in this ecosystem, delivering instant alerts and real-time insights that empower swift action to avert downtime or breaches. The significance of application allowlisting cannot be overstated; it proactively prevents unauthorized software from executing, thereby reducing vulnerabilities and assisting organizations in meeting compliance requirements. The market for the EDR endpoint is projected to expand considerably, underscoring its vital role in combating malware, ransomware, and advanced persistent challenges (APCs).
In today's rapidly evolving digital landscape, the significance of cybersecurity cannot be overstated, particularly in healthcare. EDR systems operate through several key functionalities that are essential for modern cybersecurity:
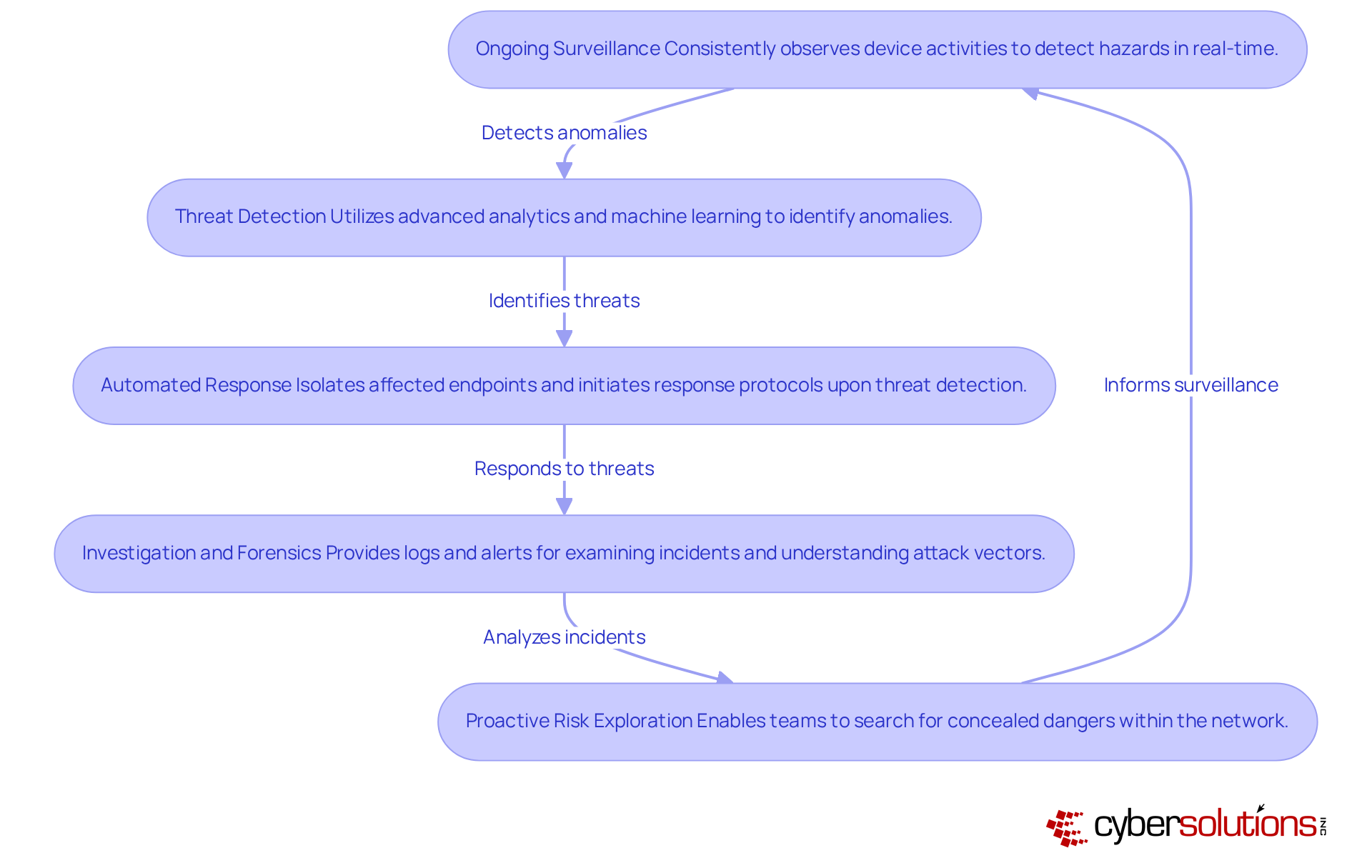
Ongoing Surveillance: EDR solutions consistently observe device activities, gathering telemetry information to detect possible hazards in real-time. This ongoing surveillance is crucial, especially as nearly 70% of breaches originate from EDR endpoints. Cyber Solutions improves this by offering round-the-clock monitoring of your network to identify anomalies and potential vulnerabilities, ensuring that suspicious activities are recognized and managed before they escalate into serious risks.
Threat Detection: Utilizing advanced analytics, machine learning, and behavioral analysis, the EDR endpoint can detect anomalies and indicators of compromise (IOCs) that signify malicious activity. Organizations with effective incident response teams can save an average of $1.2 million per breach, highlighting the importance of timely detection. With Cyber Solutions' cutting-edge risk intelligence, businesses are further safeguarded against ransomware, phishing, and other malware attacks.
Automated Response: Upon detecting a danger, EDR endpoint systems can automatically isolate affected endpoints, block malicious processes, and initiate predefined response protocols to contain the situation. This rapid remediation minimizes the impact of attacks, reducing recovery costs by up to 30%. Cyber Solutions enhances this capability with instant alerts and real-time insights, allowing for swift action to prevent downtime or breaches.
Investigation and Forensics: EDR tools offer comprehensive logs and alerts that aid teams in examining incidents, comprehending attack vectors, and collecting forensic evidence for additional analysis. This capability is vital for organizations to learn from breaches and enhance their defenses. Continuous monitoring from Cyber Solutions ensures that all suspicious activities involving the EDR endpoint are logged, providing a comprehensive overview for forensic analysis.
The EDR endpoint facilitates proactive risk exploration, enabling teams to search for concealed dangers within the network before they can inflict harm. By examining previous incident data, protection teams can reveal weaknesses and avert future attacks. With Cyber Solutions' tailored access controls and restrictions, organizations can ensure that only authorized users have access, further strengthening their defenses.
In 2025, the incorporation of the EDR endpoint within protective frameworks is increasingly acknowledged as vital for preserving operational continuity amid changing cyber risks. As one expert noted, "Without real-time monitoring, it becomes difficult to detect attacks that do not match known signatures or exhibit unusual behavior." Incorporating case studies demonstrating EDR's effectiveness in real-world scenarios would further illustrate its critical role in modern cybersecurity.
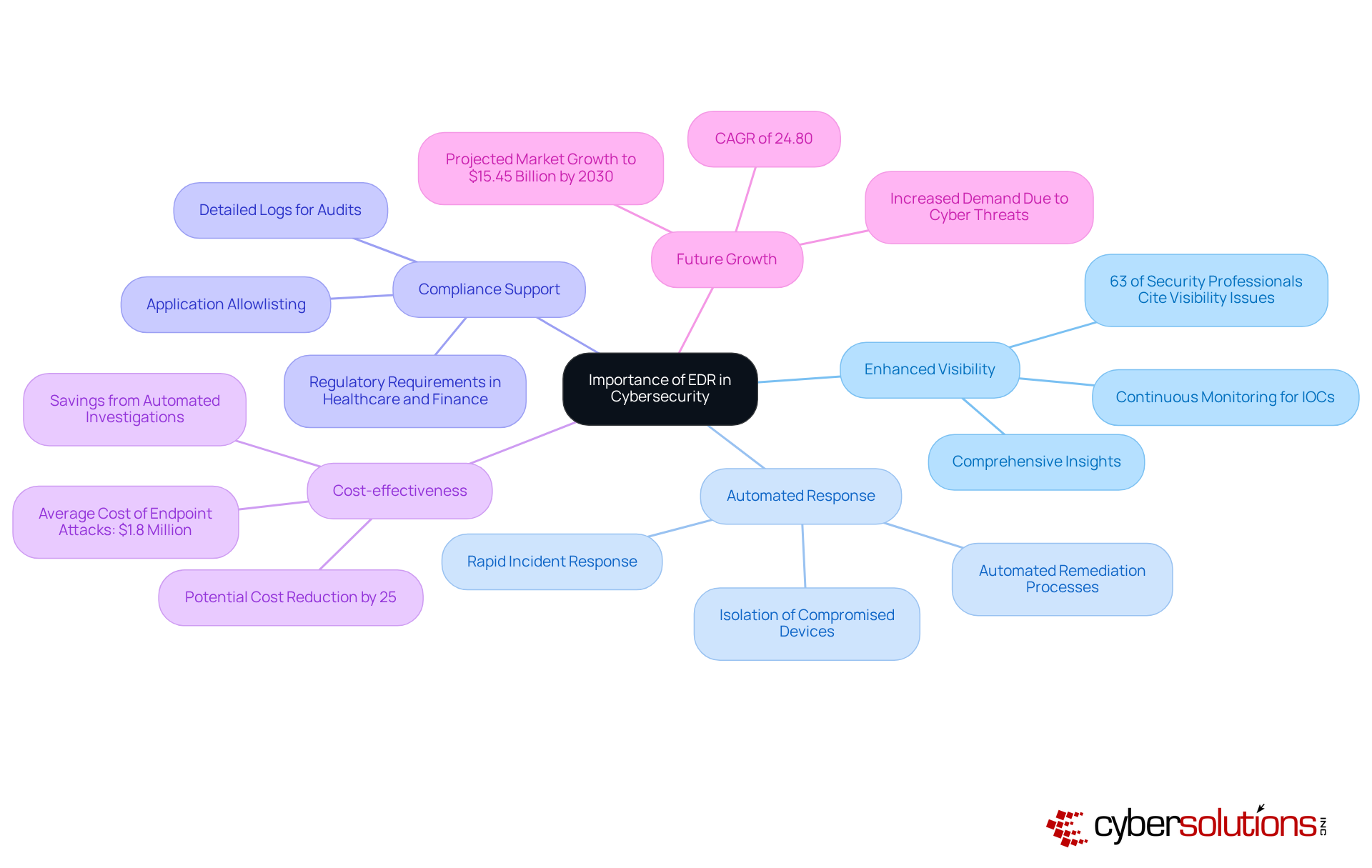
The significance of the EDR endpoint in cybersecurity cannot be overstated, especially as organizations face increasingly sophisticated cyber threats that often outpace traditional defenses. EDR effectively addresses this challenge by offering several key advantages:
With automated response capabilities, the EDR endpoint significantly reduces the time required for rapid incident response to contain and resolve incidents. This swift action minimizes potential damage, allowing organizations to respond effectively to threats before they escalate. For example, the EDR endpoint systems can immediately isolate compromised devices upon threat detection, greatly limiting malware propagation. Additionally, professional malware eradication and system restoration services, such as those offered by Cyber Solutions, ensure that each affected device is meticulously cleaned, patched, and reimaged. This process involves identifying vulnerabilities, applying necessary updates, and restoring systems to a secure state, further enhancing overall security.
Cost-effectiveness can be realized through the EDR endpoint, which prevents data breaches and reduces incident response times, resulting in substantial cost savings. The average cost of endpoint attacks is estimated to be $1.8 million per year, and implementing EDR can lower this cost by up to 25% through automation in investigation and remediation processes.
Looking ahead to 2025, the global EDR endpoint market is projected to grow significantly, underscoring its critical role in addressing endpoint-focused challenges. Organizations that embrace the EDR endpoint not only bolster their cybersecurity posture but also equip themselves to navigate the complexities of modern regulatory landscapes effectively. With continuous network monitoring and alert services, businesses can proactively defend against ransomware and phishing attacks, ensuring a robust shield against evolving cyber threats.
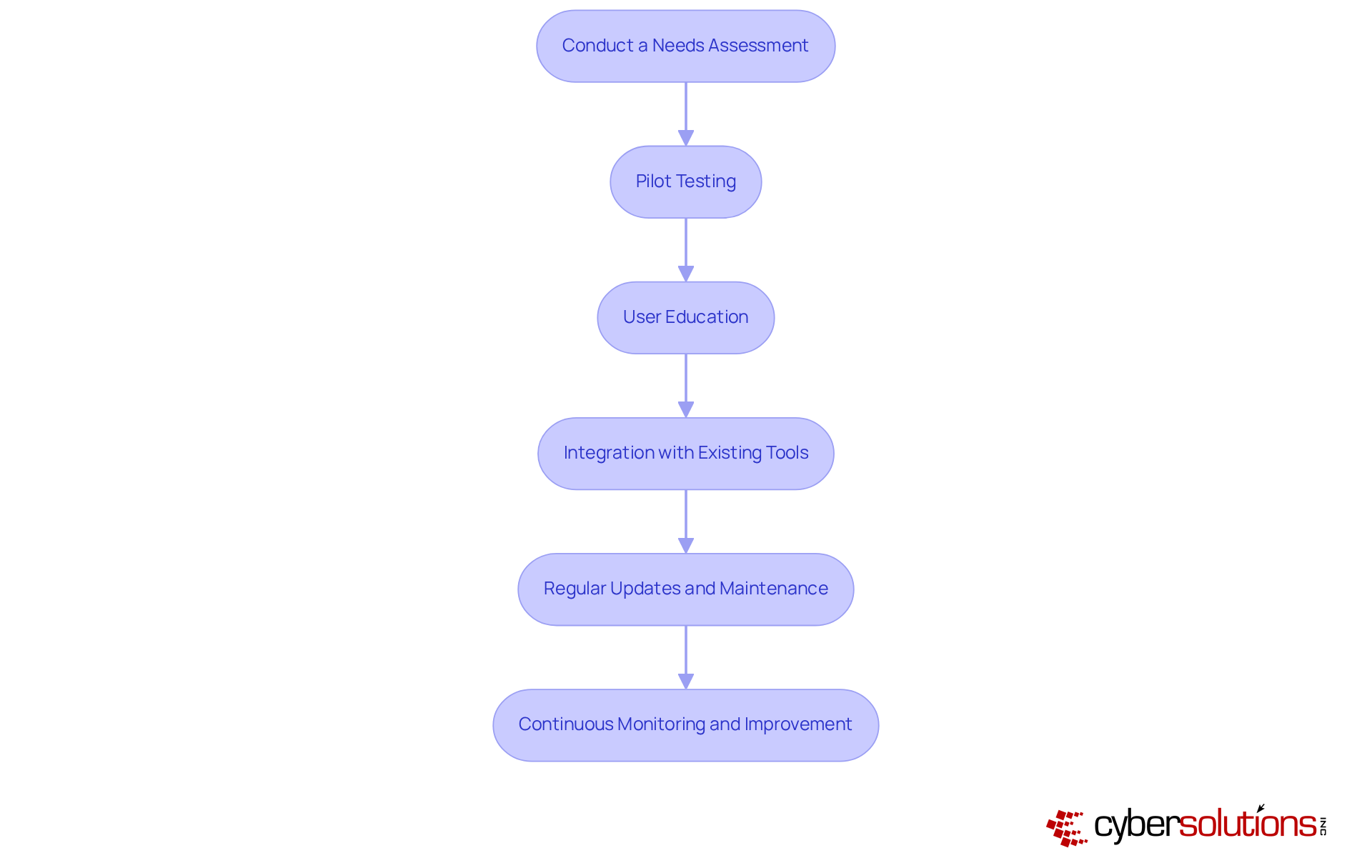
Effectively implementing the EDR endpoint is crucial for safeguarding healthcare organizations against evolving cybersecurity threats. To navigate this landscape successfully, consider the following best practices:
By adhering to these practices, organizations can enhance their cybersecurity posture and effectively mitigate risks.
The integration of Endpoint Detection and Response (EDR) technology is not just beneficial; it is increasingly essential for organizations striving to enhance their cybersecurity frameworks. As cyber threats become more complex and frequent, EDR endpoints offer a proactive solution for monitoring, detecting, and responding to potential risks. This transition from traditional security measures to advanced EDR solutions is a fundamental necessity for protecting sensitive data and ensuring compliance with industry regulations.
Key insights throughout the article emphasize the critical functionalities of EDR systems, such as:
These features significantly enhance visibility into endpoint activities while streamlining investigation and remediation processes, ultimately reducing the financial impact of cyber incidents. Additionally, the discussion on best practices for EDR implementation highlights the importance of tailored strategies, user education, and continuous monitoring to optimize security measures effectively.
In conclusion, as the cybersecurity landscape continues to evolve, embracing EDR technology is imperative for organizations aiming to mitigate risks and safeguard their digital assets. The projected growth of the EDR market by 2025 underscores its vital role in combating sophisticated cyber threats. Organizations must prioritize the adoption of EDR solutions and implement best practices to navigate the complexities of modern cybersecurity effectively. Taking decisive action today will not only fortify defenses against current threats but also prepare organizations for the challenges of tomorrow.
What is Endpoint Detection and Response (EDR)?
EDR is a cybersecurity technology designed to oversee, identify, and respond to threats across terminal devices such as laptops, desktops, and servers. It continuously collects and analyzes data from these endpoints to detect suspicious activities.
Why is EDR important in today's cybersecurity landscape?
EDR is crucial because traditional security measures often fail against sophisticated attacks. It provides a proactive strategy to detect and respond to threats, which is imperative for safeguarding sensitive data and ensuring compliance with regulatory mandates.
What are the key features of EDR?
Key features of EDR include real-time monitoring, behavioral analysis for anomaly detection, and incident response capabilities that facilitate immediate action against threats.
How does EDR enhance an organization's cybersecurity posture?
EDR enhances cybersecurity by automating threat detection and response, minimizing the time and effort required to mitigate risks, and providing comprehensive monitoring and alert services for swift action against potential breaches.
What role does application allowlisting play in EDR?
Application allowlisting prevents unauthorized software from executing, thereby reducing vulnerabilities and assisting organizations in meeting compliance requirements.
What is the projected market trend for EDR solutions?
The market for EDR solutions is projected to expand considerably, highlighting its vital role in combating malware, ransomware, and advanced persistent challenges (APCs).