
The article underscores the imperative of safe data backup for C-suite leaders, highlighting its critical role in safeguarding sensitive information against threats such as cyberattacks and hardware failures, while also ensuring compliance with regulations. It articulates strategies like the 3-2-1 backup method, various backup types, and the essential practice of regular testing and documentation. Collectively, these measures bolster organizational resilience and mitigate the financial repercussions of data loss.
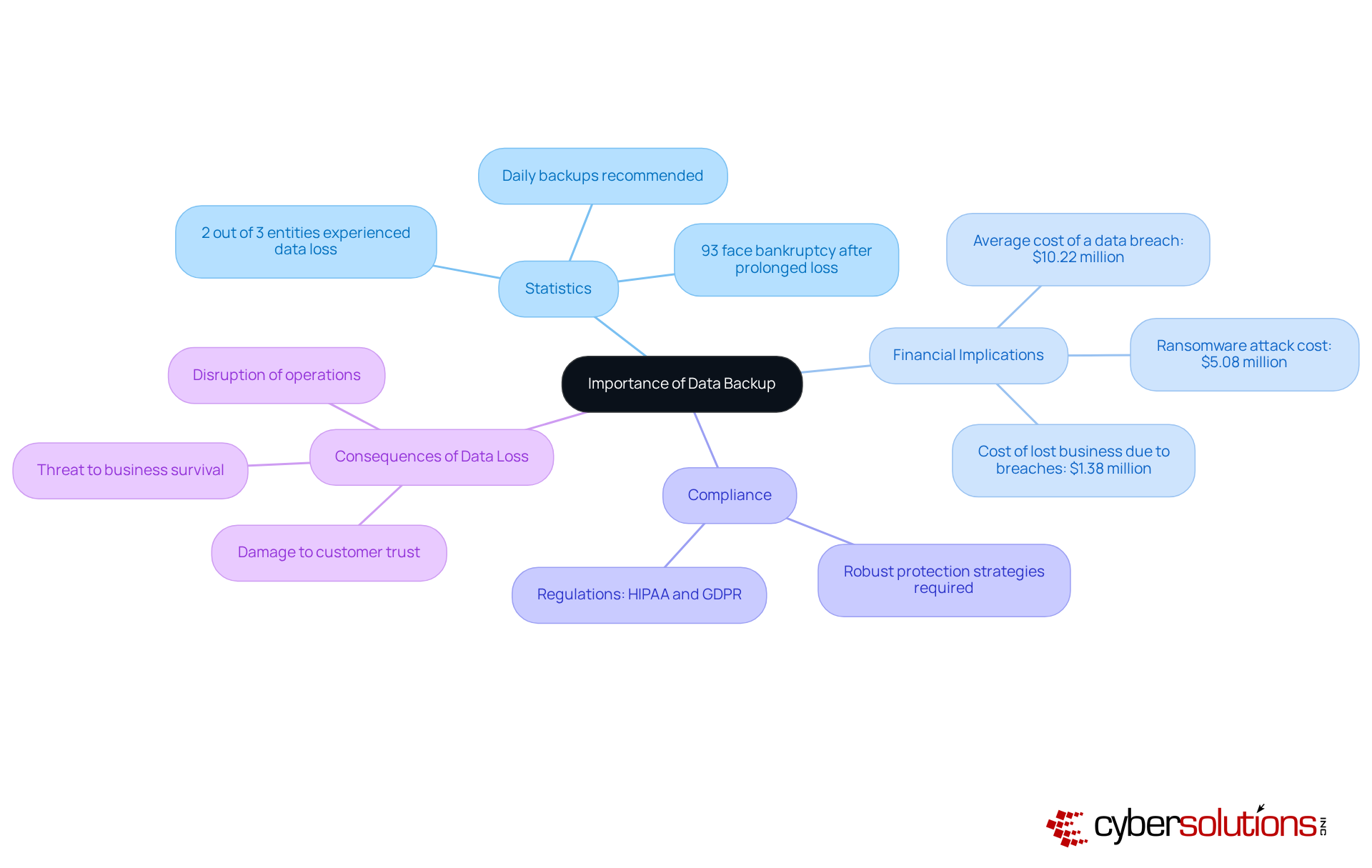
In an era where data is increasingly regarded as the lifeblood of organizations, the stakes for C-suite leaders responsible for safeguarding sensitive information are at an all-time high. Alarming statistics reveal that two-thirds of entities experienced significant data loss in the past year, underscoring the urgent need for robust data backup strategies.
This article explores essential practices for ensuring safe data backup, examining various methods, the critical 3-2-1 strategy, and the importance of regular testing alongside suitable storage solutions.
As cyber threats continue to evolve, how can executives effectively navigate the complexities of data protection to shield their organizations from potential disaster?
Safeguarding sensitive information against various threats, including cyberattacks, hardware failures, and human errors, requires safe data backup. A recent study reveals that:
Cyber Solutions offers comprehensive cybersecurity services, featuring advanced endpoint protection and email security, to fortify your systems and sensitive data. Notably:
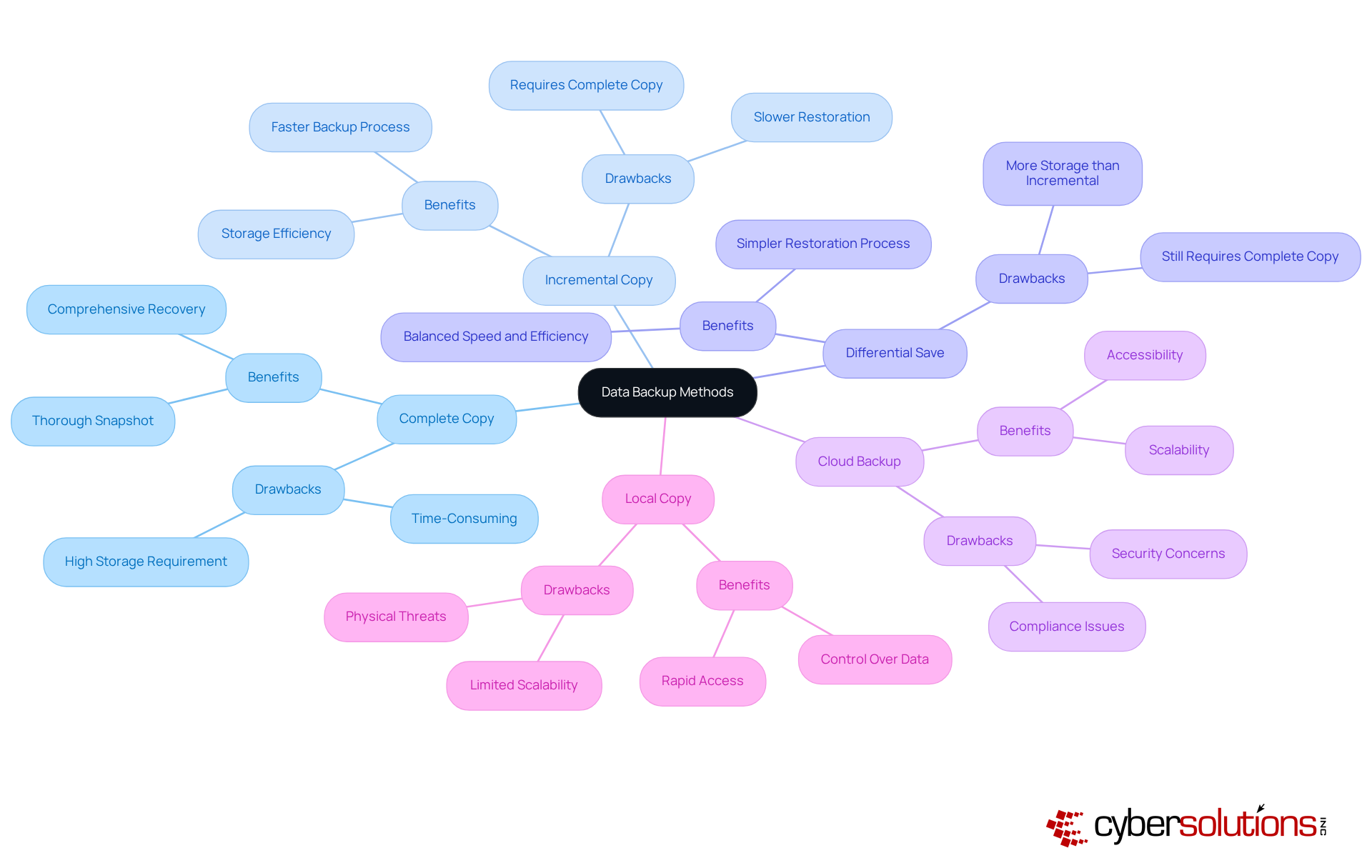
In today's digital landscape, organizations must prioritize techniques for safe data backup to effectively safeguard their data. Various methods exist, each offering distinct benefits and drawbacks that can significantly impact recovery strategies. The primary types include:
Complete Copy: This method involves duplicating all information to a storage site, providing a thorough snapshot of the system. While it guarantees comprehensive information recovery, it can be time-consuming and requires significant storage capacity.
Incremental Copy: This method saves only the information that has altered since the previous copy, resulting in increased speed and better storage efficiency. However, restoring data can be slower, as it requires the last complete copy along with all subsequent incremental copies.
Differential Save: Comparable to incremental saves, differential saves record modifications made since the last complete save. This approach strikes a balance between speed and storage efficiency, needing only the last complete save and the latest differential save for restoration.
Cloud Backup: Storing information offsite in the cloud offers scalability and accessibility, making it a preferred option among companies. However, security and compliance considerations are paramount when selecting a cloud provider, especially given that a company falls victim to a ransomware attack every 14 seconds.
Local Copy: Keeping copies on physical devices within the entity allows for rapid access and control. However, this method may expose information to physical threats such as theft or natural disasters.
By thoroughly grasping these techniques, C-suite leaders can effectively customize their recovery plans to match their organization's particular requirements and risk appetite, ensuring robust information security, business continuity, and a safe data backup.
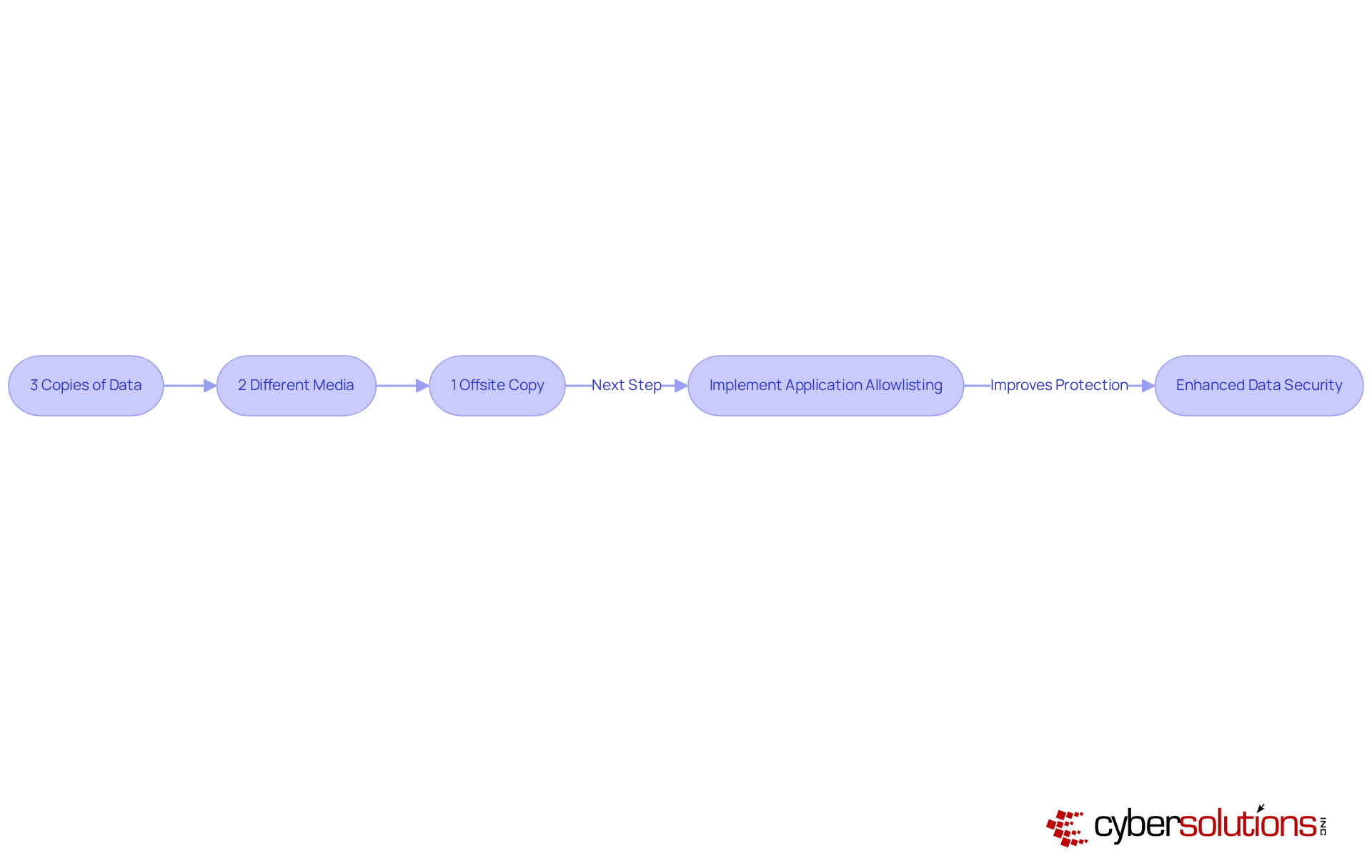
The 3-2-1 backup strategy is a straightforward yet powerful approach to safeguarding data:
Executing this plan greatly reduces the chance of information loss. For instance, in the case of a ransomware incident that jeopardizes local information, having an offsite copy enables recovery without major disruption. Furthermore, incorporating application allowlisting into your cybersecurity framework enhances this approach by proactively blocking unauthorized software from running, thus protecting your backups from malware and ransomware risks.
Application allowlisting features continuous monitoring of application activity and centralized management of allowlists, ensuring that only approved applications can run. This not only safeguards your information but also assists organizations in meeting regulatory obligations such as HIPAA, PCI-DSS, and GDPR. Organizations that embrace the 3-2-1 strategy alongside application allowlisting can demonstrate to stakeholders their unwavering commitment to data security and business continuity.
The significance of offsite data storage cannot be overstated, particularly as companies encounter rising dangers from cyberattacks. Expert insights highlight that without external data storage, organizations are especially susceptible to ransomware attacks, which can result in severe operational and financial repercussions. By implementing the 3-2-1 storage strategy, companies can effectively ensure a safe data backup of their essential information and respond strongly to possible threats.
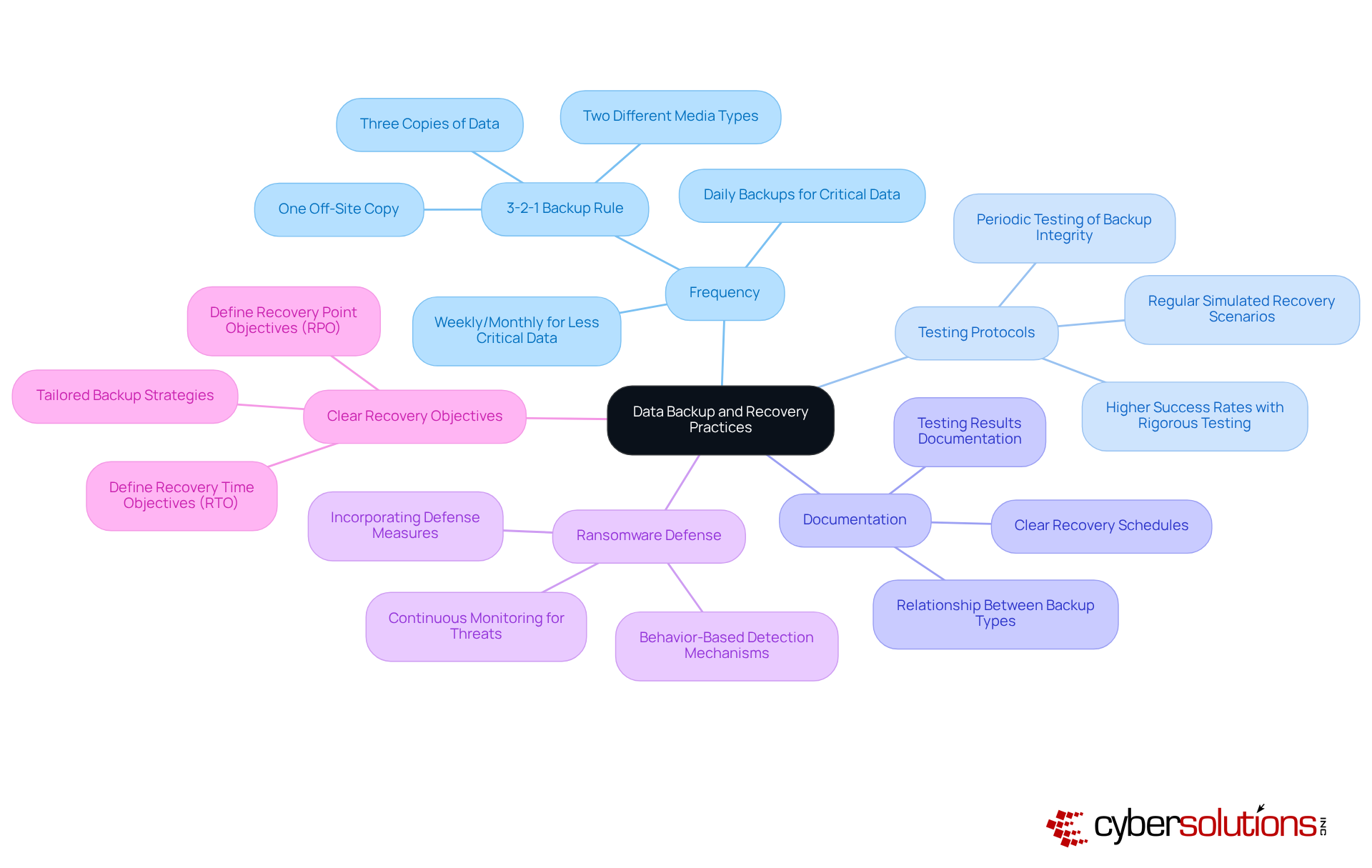
Creating a regular recovery timetable is crucial for ensuring consistent information security. Organizations must adopt best practices to safeguard their data effectively:
Frequency: The frequency of backups must be tailored to data volatility. For essential business information, daily or even hourly copies are recommended to mitigate potential losses, while less critical data may be saved weekly or monthly. This approach aligns with the 3-2-1 storage guideline, promoting the retention of three copies of information across two distinct media types, which ensures safe data backup with one copy stored off-site.
Testing Protocols: Regular examination of recovery systems is essential to guarantee effective information restoration. Organizations should conduct simulated recovery scenarios to identify and address potential issues before a real disaster occurs. Statistics indicate that organizations implementing rigorous testing protocols experience significantly higher success rates in data restoration, thereby enhancing overall resilience against data loss incidents.
Documentation: Clear documentation of recovery schedules, procedures, and testing results is vital. This transparency not only fosters accountability but also aids compliance audits, ensuring that all stakeholders are aware of the recovery plan's effectiveness. Furthermore, documenting the relationship between complete and differential data sets within the disaster recovery plan provides clarity during recovery scenarios.
Ransomware Defense: Incorporating ransomware defense measures into recovery plans is essential to protect information integrity and security against evolving cyber threats. Continuous monitoring ensures that suspicious activities are detected and halted before escalating into significant threats, thereby safeguarding your business from ransomware, phishing, and other malware attacks.
Clear Recovery Objectives: Organizations should define Clear Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO) for various types of information, allowing for tailored backup strategies that meet specific business needs.
By integrating these practices, organizations can significantly enhance their data resilience, ensuring safe data backup and preparedness for any potential data loss events. Regular testing and documentation not only improve operational efficiency but also instill confidence in the organization's ability to recover swiftly from disruptions. Moreover, having a rapid incident response plan in place, as demonstrated in recent case studies, can minimize the impact of ransomware attacks and reinforce overall cybersecurity measures.
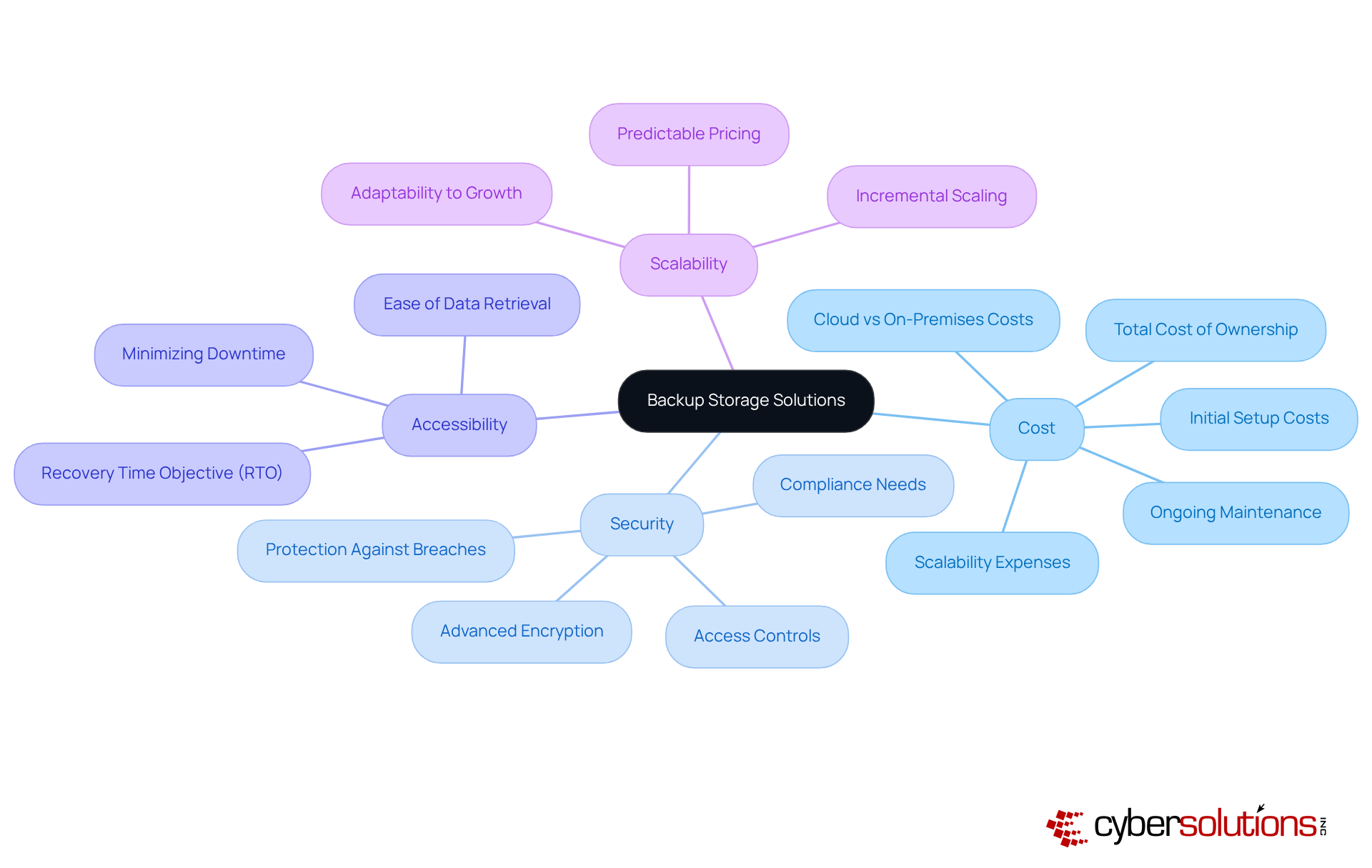
Selecting the right backup storage solutions is imperative for organizations aiming to achieve a safe data backup effectively. A thorough evaluation of several key factors is essential to ensure optimal decision-making.
Cost: Assessing the total cost of ownership for each storage option is crucial. This includes initial setup, ongoing maintenance, and scalability expenses. For instance, while cloud backup solutions can significantly reduce annual operating costs by up to 80%, on-premises systems may incur higher cumulative costs over time due to substantial upfront investments and ongoing maintenance requirements.
Security: In an era where cyber threats are ever-evolving, it is essential to choose storage solutions that provide robust security features. Advanced encryption and strict access controls are non-negotiable. Ensuring information protection against unauthorized access and breaches is paramount.
Accessibility: The ability to retrieve information promptly during recovery cannot be overstated. Solutions that facilitate rapid recovery times are vital for minimizing downtime and maintaining operational continuity. For example, GitProtect.io offers a 10-minute Recovery Time Objective (RTO) for S3 storages, underscoring the significance of speed in recovery.
Scalability: Organizations must select solutions that can adapt to their expanding information requirements. Cloud solutions, in particular, enable gradual scaling with predictable pricing, making them suitable for businesses anticipating varying information volumes.
By meticulously analyzing these factors, C-suite leaders can make strategic decisions that not only enhance their organization's data protection framework but also ensure a safe data backup while optimizing costs effectively.
Ensuring a secure and effective data backup strategy transcends operational necessity; it stands as a vital strategic imperative for C-suite leaders. The potential financial repercussions of data loss illuminate the critical need to prioritize robust backup solutions and recovery methods. By adopting a comprehensive approach to data protection, organizations can effectively safeguard their sensitive information from a myriad of threats, enhancing resilience and preserving their competitive edge.
The article outlines several key strategies for achieving safe data backup, such as:
Each of these elements plays a pivotal role in mitigating risks associated with data loss, underscoring the necessity for C-suite leaders to proactively engage in their data protection efforts. Moreover, the importance of testing recovery protocols and ensuring compliance with industry regulations cannot be overstated, as these practices equip organizations to adeptly respond to potential data breaches.
In a landscape rife with increasingly sophisticated cyber threats, the imperative for executives is unmistakable: prioritize data backup as an essential component of organizational strategy. By investing in effective backup solutions and cultivating a culture of data resilience, leaders can shield their organizations from the devastating impacts of data loss, ensuring not only compliance but also the long-term sustainability of their business operations. Embracing these best practices will not only fortify data security but also bolster stakeholder confidence in an organization's unwavering commitment to safeguarding its most critical assets.
Why is data backup important for organizations?
Data backup is crucial for safeguarding sensitive information against threats like cyberattacks, hardware failures, and human errors. A study showed that 2 out of 3 entities experienced significant information loss in the past year, highlighting the need for effective recovery methods.
What are the financial implications of data loss for C-suite executives?
The average cost of a security breach in 2025 is projected to be around $10.22 million. This underscores that investing in recovery solutions is a strategic financial imperative, not just a technical necessity.
What regulations mandate data backup strategies?
Regulations such as HIPAA and GDPR require organizations to implement robust protection strategies, including safe data backup.
What are the consequences of prolonged information loss?
Organizations that experience information loss lasting 10 days or more face a 93% risk of bankruptcy within the following year, emphasizing the importance of effective recovery strategies.
What types of data backup methods are available?
The primary types of data backup methods include: Complete Copy: Duplicates all information, ensuring comprehensive recovery but requiring significant storage and time. Incremental Copy: Saves only changed information since the last copy, offering speed and storage efficiency, but slower restoration. Differential Save: Records changes since the last complete save, balancing speed and storage efficiency for restoration. Cloud Backup: Stores information offsite in the cloud, providing scalability and accessibility, with security considerations being crucial. Local Copy: Keeps copies on physical devices for rapid access, but may expose data to physical threats.
How can organizations enhance their data backup strategies?
Organizations can enhance their data backup strategies by prioritizing data preservation, routinely testing disaster recovery plans, and leveraging services like Compliance as a Service (CaaS) for audit support and regulatory adherence. This helps bolster operational resilience and protect against the costly repercussions of data loss.