In today's digital landscape, cybersecurity is not just a necessity; it's a cornerstone of operational integrity. Cybersecurity professionals leverage logs primarily for:
These functions are essential for maintaining robust digital security.
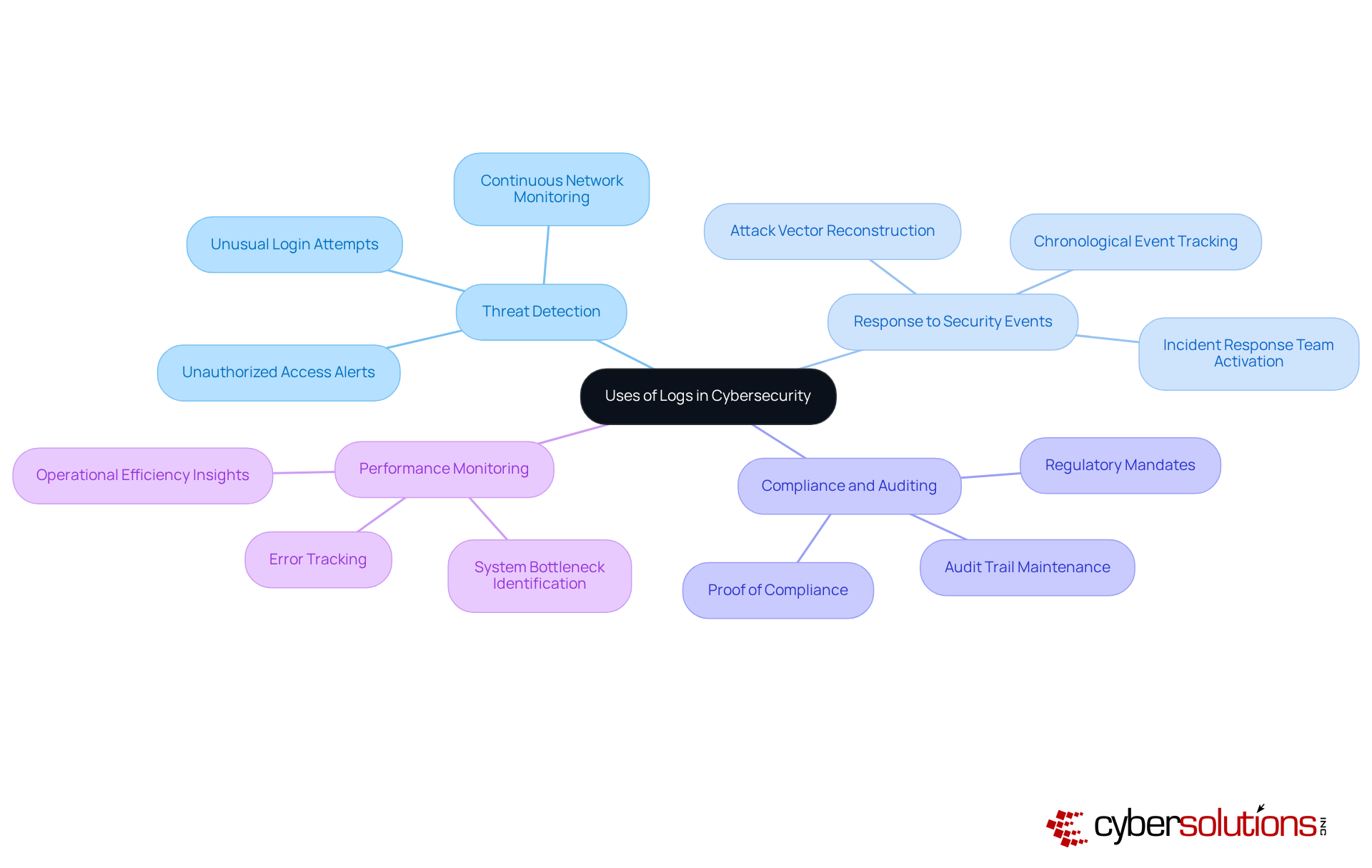
Logs provide critical insights into suspicious activities, enabling professionals to reconstruct security events effectively. They also play a vital role in demonstrating compliance with regulations, which is increasingly important in a world where data breaches can lead to severe penalties. Furthermore, logs facilitate performance oversight, allowing organizations to fine-tune their cybersecurity measures and respond proactively to emerging threats.
The multifaceted role of logs in enhancing cybersecurity practices cannot be overstated. By utilizing logs, organizations not only bolster their defenses but also foster a culture of accountability and transparency. As cybersecurity threats continue to evolve, the importance of these tools will only grow, making it imperative for organizations to prioritize their logging strategies.
In the realm of cybersecurity, logs are the unsung heroes, capturing the essence of digital interactions and protecting organizations from potential threats. These records are not just data entries; they are essential tools that cybersecurity professionals depend on for:
As the volume and complexity of log data continue to grow, organizations must ask: how can they effectively harness this information to strengthen their defenses?
Exploring the multifaceted uses of logs reveals both the immense value they provide and the challenges that must be navigated to optimize their management and utility. The current landscape of cybersecurity threats is daunting, particularly for healthcare organizations that face unique challenges. By understanding the critical role logs play, organizations can better prepare themselves against evolving threats and enhance their overall security posture.
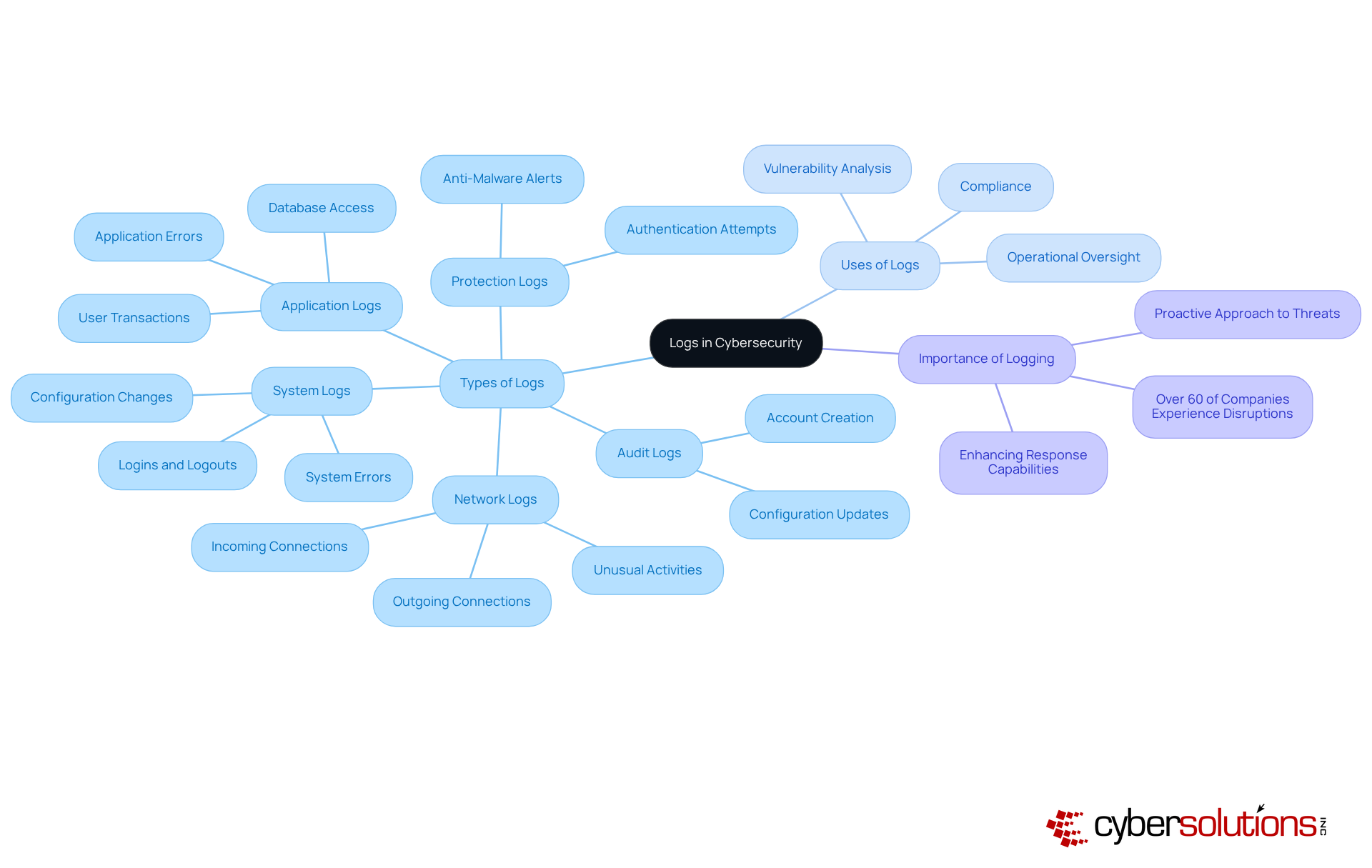
In the realm of cybersecurity, records are not just entries; they are the backbone of digital safety, documenting critical events within systems, networks, or applications. These records capture a wide range of activities—from user actions and system processes to errors and incidents—serving as a historical archive that provides invaluable insights into system behavior. For example, they encompass access attempts, transaction details, and error notifications, making them indispensable for operational oversight and vulnerability analysis.
Understanding what cyber security professionals can use logs for, including application logs, system logs, protection logs, audit logs, and network logs, is crucial. A robust logging strategy is vital, especially considering that over 60% of companies experience at least one significant operational or safety disruption annually. This statistic underscores the necessity of efficient log management for identifying threats.
Real-world scenarios illustrate that spikes in outbound DNS traffic can trigger alerts in centralized systems, allowing teams to trace issues back to compromised hosts and thwart data exfiltration. By leveraging these records, organizations can enhance their response capabilities and ensure compliance with regulatory frameworks, ultimately strengthening their overall cybersecurity posture, highlighting what cyber security professionals can use logs for.
In a landscape where threats are ever-evolving, the importance of comprehensive logging cannot be overstated. Are you prepared to safeguard your organization against potential breaches? Embrace a proactive approach to log management and fortify your defenses today.
In today's digital landscape, cybersecurity is not just a necessity; it's a critical component of operational integrity. Cybersecurity professionals leverage logs for a variety of essential functions that enhance security and operational efficiency:
Current trends indicate a growing emphasis on proactive threat hunting, focusing on what cyber security professionals use logs for, as security teams regularly analyze historical log data to identify stealthy behaviors and correlate findings with known indicators of compromise. This method greatly improves the likelihood of identifying slow-burning or targeted attacks, strengthening the overall security stance.
Optimal methods in incident response highlight the significance of keeping records for an adequate duration—usually 6 to 12 months—to aid comprehensive investigations and forensic examination. As security leaders shift from an emphasis on prevention to resilience, understanding what cyber security professionals use logs for becomes increasingly essential in managing the intricacies of contemporary cyber threats. As Gary Barlet, Public Sector CTO at Illumio, emphasizes, "Not all records are created equal," highlighting the critical need for quality record management in cybersecurity.
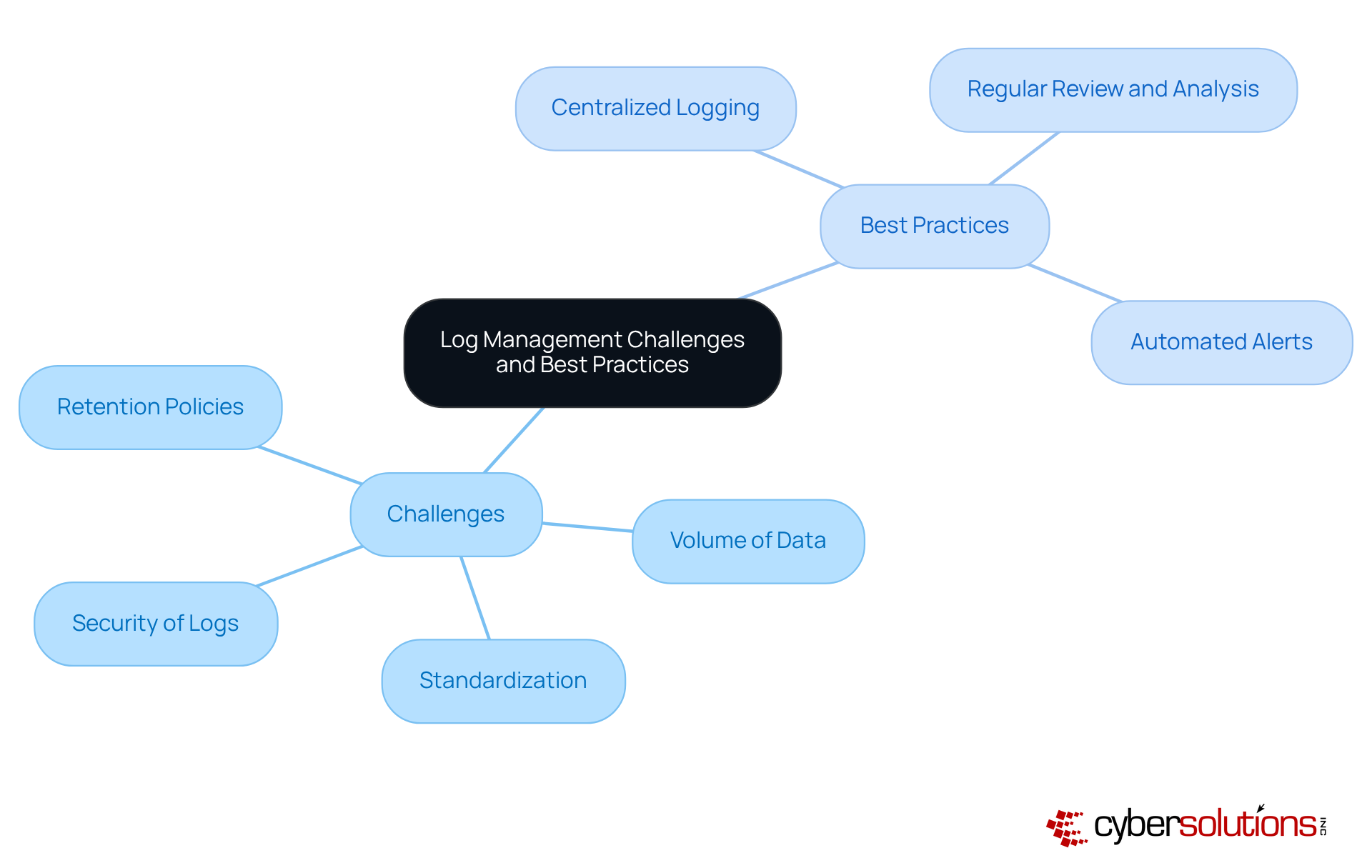
Effective log management is crucial for organizations to determine what cyber security professionals can use logs for, especially in the face of increasing cybersecurity threats. The challenges it presents are significant and multifaceted:
To effectively address these challenges, organizations should adopt best practices that enhance their log management processes:
By implementing these strategies, organizations can significantly improve their log management processes, ultimately strengthening their cybersecurity posture. Are you ready to take action and enhance your organization's security measures?
Logs are a cornerstone of cybersecurity, serving as detailed records that capture a wide range of activities and events within digital systems. Their importance goes far beyond simple documentation; they are vital for threat detection, incident response, compliance, and performance monitoring. By leveraging logs effectively, cybersecurity professionals can significantly strengthen their organizations' defenses against an increasingly complex threat landscape.
This article has delved into the various applications of logs, showcasing their critical role in:
However, challenges like data volume and standardization highlight the urgent need for organizations to adopt best practices such as centralized logging and regular analysis. These strategies empower teams to navigate the complexities of log data with confidence.
Proactively managing logs is not merely a technical necessity; it is a strategic imperative for protecting digital assets. Organizations must prioritize the establishment of robust log management practices to enhance their cybersecurity posture. By doing so, they can not only respond to current threats but also anticipate and mitigate future risks, ensuring a resilient and secure operational environment. Embracing this proactive approach to log management is essential for any organization committed to maintaining its integrity and security in the digital age.
What are logs in the context of cybersecurity?
In cybersecurity, logs are records that document critical events within systems, networks, or applications. They capture a range of activities, including user actions, system processes, errors, and incidents, serving as a historical archive that provides insights into system behavior.
What types of logs are important in cybersecurity?
Important types of logs in cybersecurity include application logs, system logs, protection logs, audit logs, and network logs.
Why is a robust logging strategy essential for organizations?
A robust logging strategy is essential because over 60% of companies experience at least one significant operational or safety disruption annually. Efficient log management helps identify threats and enhances operational oversight.
How can logs be used to respond to cybersecurity threats?
Logs can trigger alerts in centralized systems, such as spikes in outbound DNS traffic, allowing teams to trace issues back to compromised hosts and thwart data exfiltration, thereby enhancing response capabilities.
What role do logs play in regulatory compliance?
Logs are crucial for ensuring compliance with regulatory frameworks, as they provide necessary documentation and evidence of system behavior and security measures.
What is the overall importance of comprehensive logging in cybersecurity?
Comprehensive logging is vital in an ever-evolving threat landscape, as it helps organizations safeguard against potential breaches and strengthens their overall cybersecurity posture.