
In today's digital landscape, understanding attack vectors is crucial for every C-suite leader aiming to bolster their organization's cybersecurity posture. Recognizing these vectors, which encompass threats such as phishing and malware, is not merely an option; it is a necessity. By identifying these vulnerabilities, leaders can implement targeted defenses that not only safeguard sensitive information but also ensure compliance with industry regulations. This proactive approach is essential in mitigating risks and enhancing overall security.
Understanding the myriad ways cybercriminals infiltrate organizations is not just important; it is essential for safeguarding sensitive information, especially in sectors like healthcare where the stakes are exceptionally high. In this context, every C-suite leader must recognize the urgent need to fortify their cybersecurity strategies against evolving threats. This article delves into ten essential attack vectors that leaders must comprehend to effectively protect their organizations.
By exploring these definitions, executives can identify vulnerabilities within their systems and implement robust defenses. Yet, as the landscape of cyber threats continues to evolve, the pressing question remains: how can leaders ensure they stay ahead of these sophisticated attacks while maintaining operational integrity?
In today’s rapidly evolving digital landscape, the importance of cybersecurity cannot be overstated, especially within the healthcare sector. Cyber Solutions Inc. provides a comprehensive suite of cybersecurity services tailored to effectively mitigate various attack vectors definition. Among these, the 24/7 help desk support stands out as a critical component, offering prompt assistance during incidents to significantly reduce potential damage and enhance business protection. Furthermore, the incorporation of endpoint protection, email safeguards, firewalls, and managed defense services strengthens defenses against cyber risks, ensuring that organizations remain resilient in the face of threats.
Utilizing advanced risk detection and incident response strategies, Cyber Solutions empowers entities to proactively defend against breaches, safeguarding sensitive data while ensuring compliance with industry regulations. This holistic approach not only fortifies protection but also enhances operational efficiency, allowing businesses to concentrate on their core functions without the complexities of IT management. As organizations navigate the shifting landscape of cyber threats, the adoption of Co-Managed IT Services is increasingly recognized as a strategic investment, aligning protective measures with corporate objectives and bolstering overall resilience.
It is essential to understand that cybersecurity is not a one-time endeavor but an ongoing process that requires continuous oversight and adaptation to emerging challenges. This perspective underscores the importance of viewing cybersecurity as a collective responsibility across the organization, fostering a culture that enhances defensive capabilities and ensures that all team members remain vigilant against potential threats. Moreover, our managed IT services present a cost-effective alternative to maintaining an in-house team, enabling organizations to allocate resources more efficiently while achieving robust protection.

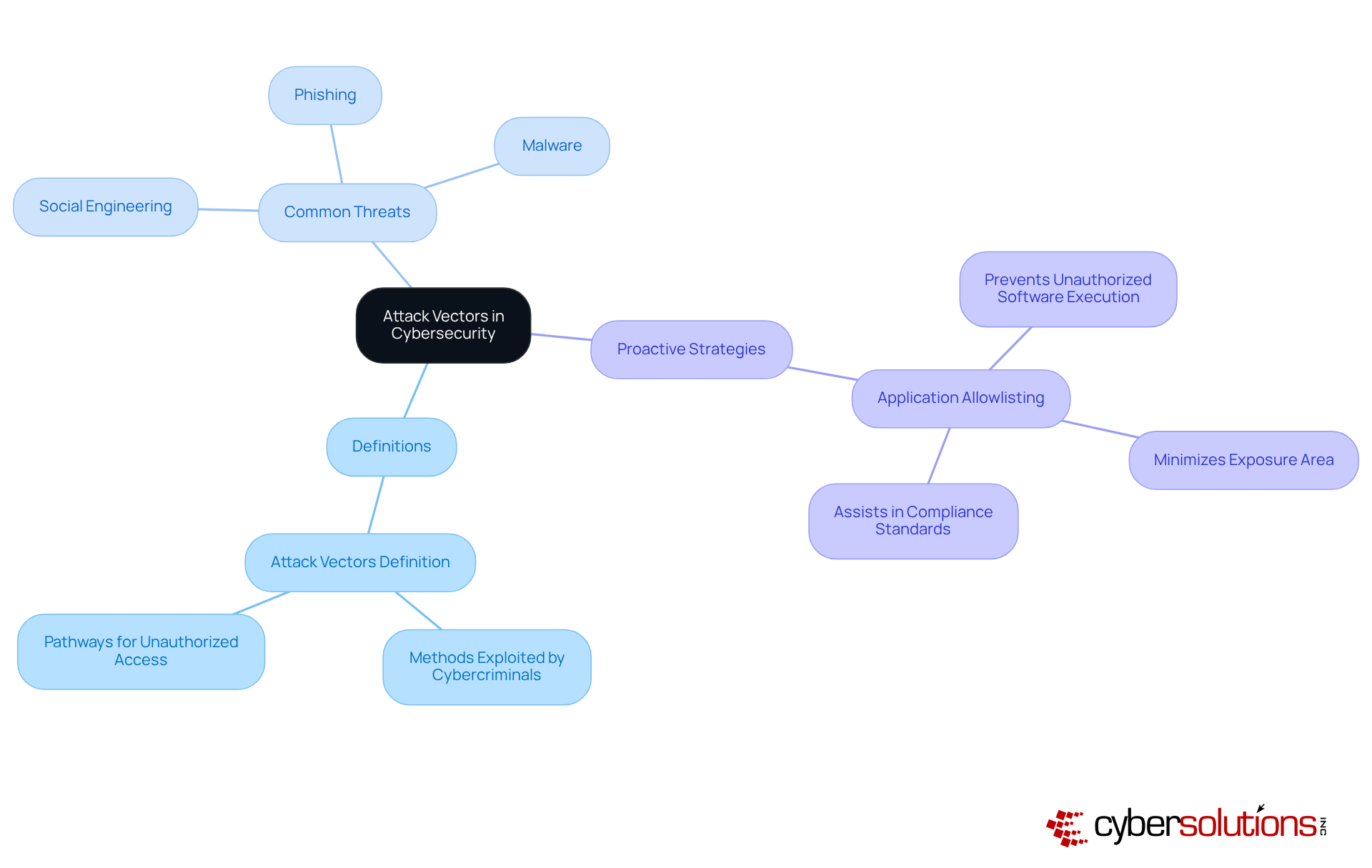
Understanding the attack vectors definition is crucial in the realm of cybersecurity, particularly for organizations aiming to protect their systems and networks. The attack vectors definition refers to the methods or pathways that cybercriminals exploit to gain unauthorized access. By grasping these vectors, business leaders can identify vulnerabilities within their infrastructure, reinforcing their security posture.
The attack vectors definition encompasses common threats such as phishing, malware, and social engineering, each presenting unique challenges. Recognizing these threats empowers organizations to implement targeted defenses, such as application allowlisting. This proactive measure not only prevents unauthorized software from executing but also minimizes the exposure area, thereby enhancing overall security. Furthermore, it assists in meeting compliance standards, ensuring that only authorized applications operate within the network.
Incorporating proactive strategies like application allowlisting enables organizations to allocate resources efficiently, significantly reducing risks associated with these threat vectors. By staying ahead of potential threats, businesses can safeguard their operations and maintain the trust of their stakeholders.
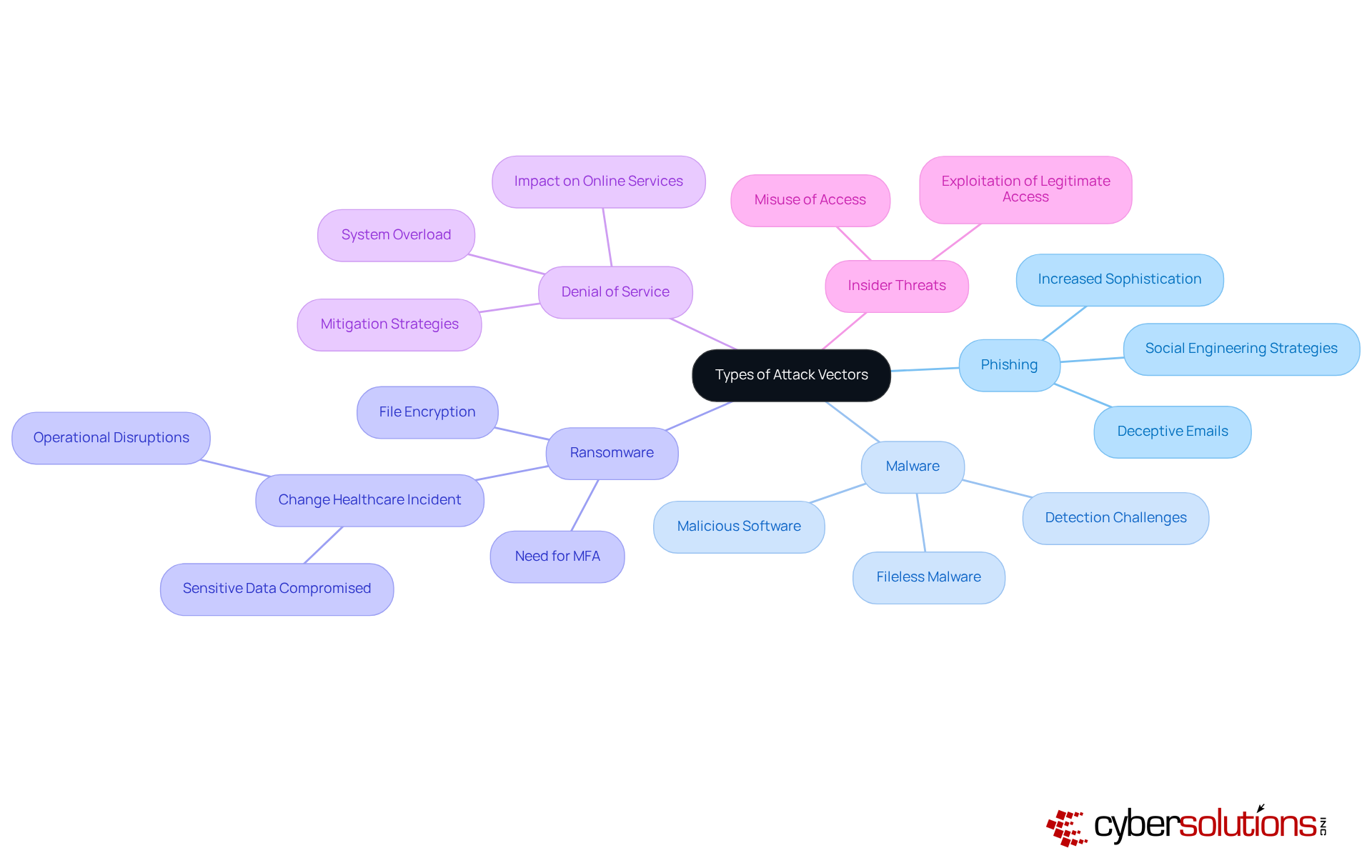
In today's digital landscape, the significance of cybersecurity in healthcare cannot be overstated. Organizations face a myriad of attack vectors that threaten their operational integrity and the confidentiality of sensitive information.
Phishing: Deceptive emails designed to trick users into revealing sensitive information, often leading to unauthorized access to accounts or systems. Recent trends suggest that phishing incidents have become progressively advanced, employing social engineering strategies to exploit human weaknesses.
Malware: Malicious software that disrupts, damages, or gains unauthorized access to systems. In 2025, malware incidents are evolving, with a significant increase in fileless malware that operates in memory, complicating detection efforts.
Ransomware: A specific type of malware that encrypts files and demands payment for decryption. The impact of ransomware incidents can be devastating, as demonstrated by the Change Healthcare event in February 2024, where sensitive patient data was compromised, leading to significant operational disruptions and financial losses. This incident underscores the critical need for adopting multi-factor authentication (MFA) and swift incident response strategies. For instance, Cyber Solutions Inc. restored 4,500 endpoints following a ransomware breach, ensuring continuity of care and compliance in healthcare environments. A structured response plan and specialized expertise are essential for effectively managing such incidents.
Denial of Service (DoS): Attacks that overwhelm systems, rendering them unavailable to users. These assaults can incapacitate organizations, particularly those reliant on online services, highlighting the necessity for robust mitigation strategies.
Insider Threats: Risks posed by employees or contractors who misuse their access to harm the organization. Insider threats can be particularly insidious, as they often exploit legitimate access to sensitive information.
Understanding the attack vectors is crucial for organizations to effectively tailor their protective strategies. Cybersecurity experts emphasize that a proactive approach—incorporating employee training, the implementation of multi-factor authentication (MFA), and application allowlisting—can significantly reduce the risk of successful intrusions. Application allowlisting, in particular, serves as a gold standard in cybersecurity by preventing unauthorized software from executing, thereby enhancing overall protection and ensuring compliance with regulations.
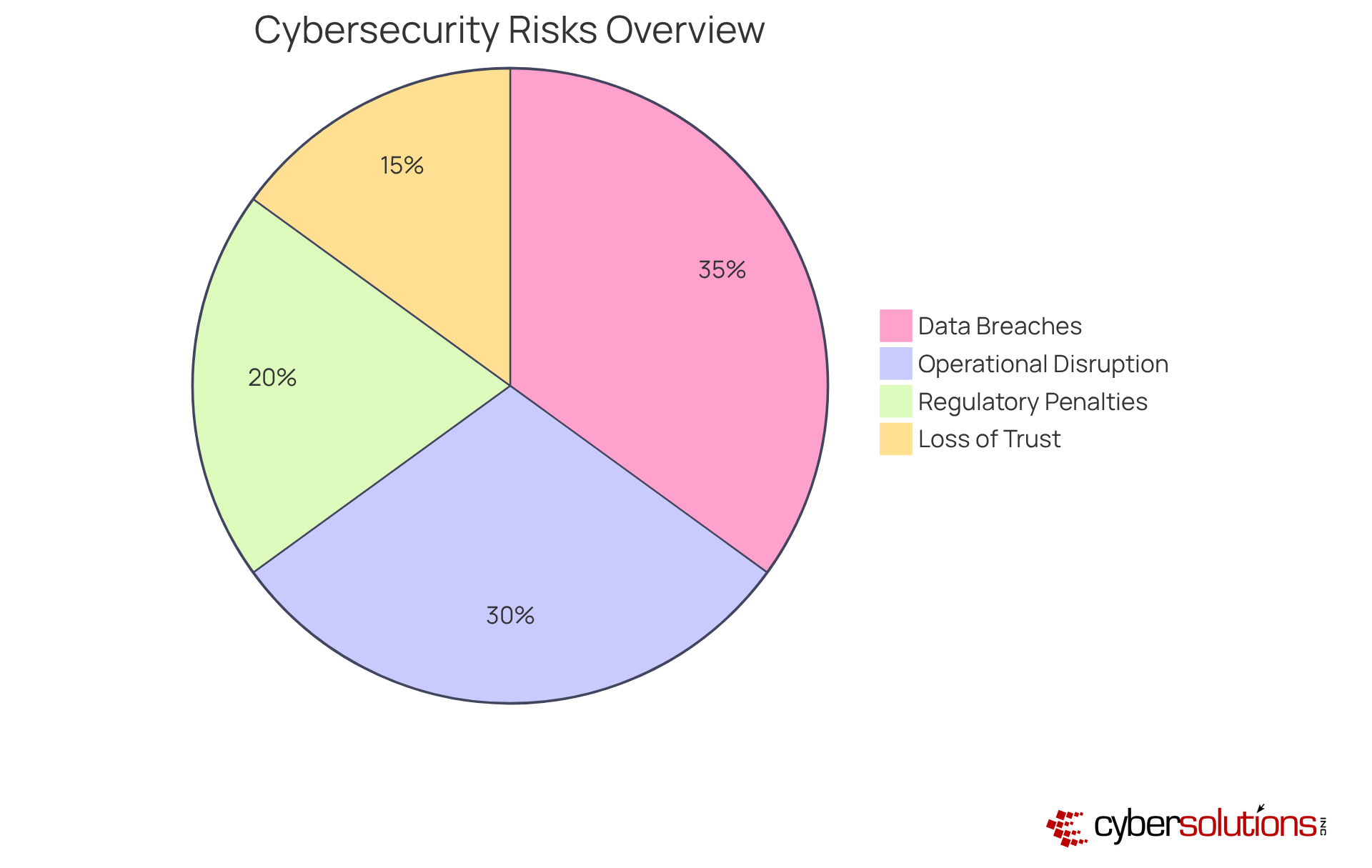
The attack vectors definition highlights the profound impact they have on system security, underscoring the critical need for robust cybersecurity measures in healthcare. Consider the following significant risks:
Understanding these risks is essential for C-suite leaders, particularly CFOs, to advocate for necessary cybersecurity investments. The current landscape of cybersecurity threats demands immediate attention and action.
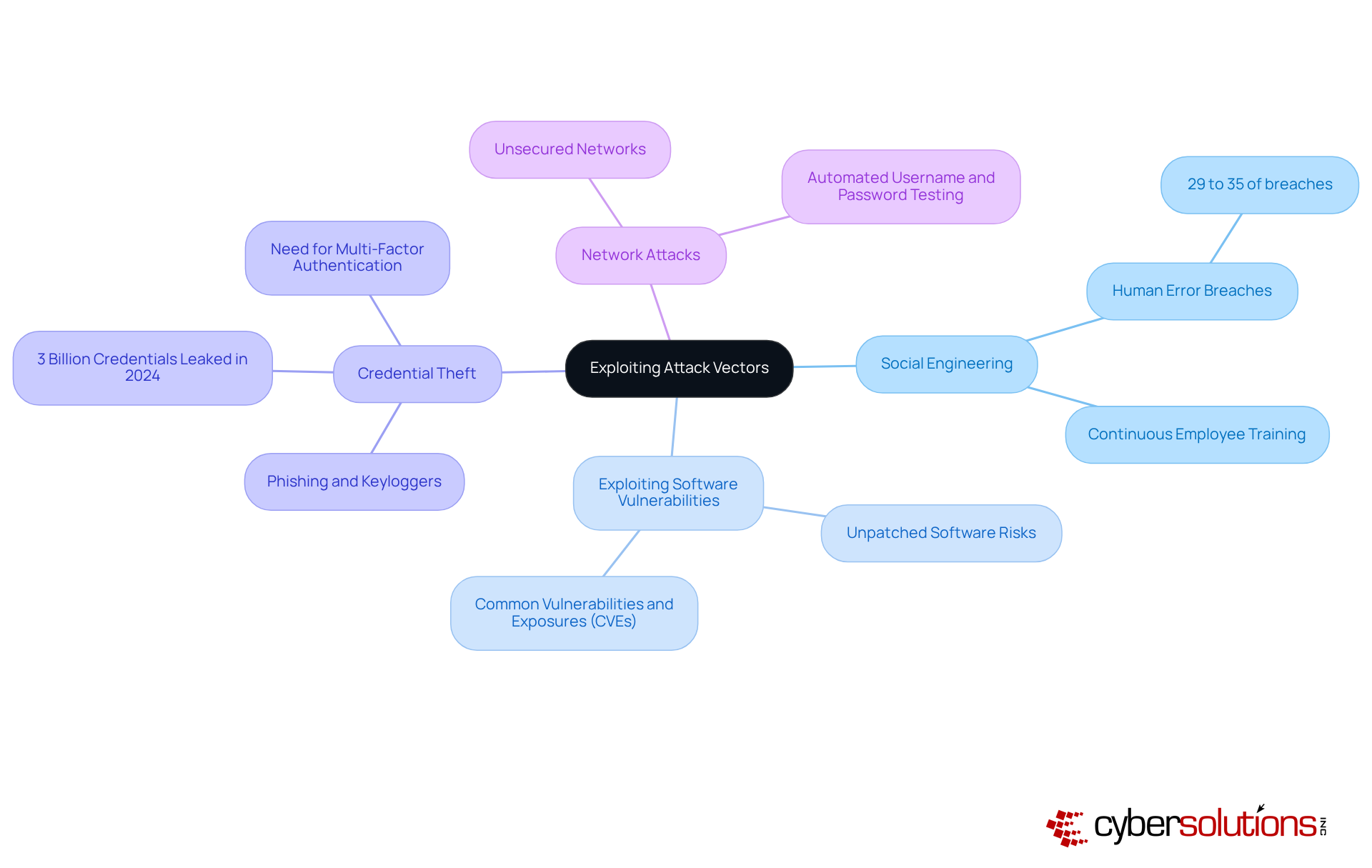
Cybercriminals are increasingly exploiting attack vectors definition through a variety of sophisticated methods that demand urgent attention from organizations, particularly in the healthcare sector. Understanding these tactics is vital for establishing robust cybersecurity measures that can safeguard sensitive data.
Social Engineering: This tactic involves manipulating individuals into revealing confidential information. Human error is a significant factor in breaches, with studies indicating that between 29% to 35% of reported breaches arise from such errors. Continuous employee training is essential to recognize and resist these manipulative tactics, thereby reducing vulnerability.
Exploiting Software Vulnerabilities: Cybercriminals often take advantage of unpatched software to gain unauthorized access. Attackers frequently exploit Common Vulnerabilities and Exposures (CVEs) in widely utilized applications, underscoring the necessity for organizations to uphold stringent patch management protocols.
Credential Theft: Techniques such as phishing and the use of keyloggers are prevalent in capturing login credentials. In 2024 alone, nearly 3 billion unique sets of credentials were leaked. This alarming statistic underscores the critical need for robust identity verification processes and the implementation of multi-factor authentication to mitigate risks effectively.
Network Attacks: Gaining access through unsecured networks or devices remains a common strategy for cybercriminals. Automated tools are frequently utilized to test various username and password combinations, making it crucial for companies to implement robust network protection measures, including firewalls and intrusion detection systems.
By comprehensively understanding the attack vectors definition, organizations can implement more robust protective measures to thwart potential breaches. This proactive approach not only safeguards sensitive data but also maintains compliance in an increasingly regulated environment.
In the realm of cybersecurity, understanding the attack vectors definition is paramount to safeguarding sensitive information. Attack vectors can be classified into two primary categories: passive and active.
Passive Attack Vectors: These tactics involve monitoring or collecting data without making any alterations to the system. A common example is eavesdropping on network traffic, where cybercriminals capture sensitive information such as login credentials or confidential communications without detection. This form of assault can significantly undermine data security, as it enables intruders to collect information for future exploits without triggering alerts.
Active Intrusion Vectors: Conversely, active intrusion vectors entail direct interaction with the system to cause harm. This includes tactics such as injecting malware, executing denial-of-service operations, or manipulating data. These assaults are more forceful and can result in sudden interruptions in operations, data breaches, or loss of sensitive information.
Understanding the attack vectors definition, including the difference between passive and active threat vectors, is essential for organizations striving to strengthen their cybersecurity stance. For instance, organizations can establish strong monitoring systems to identify unusual network activity suggesting passive intrusions, while also utilizing advanced threat detection solutions to combat active dangers.
As cybersecurity experts stress, a proactive method for recognizing and addressing these threat vectors is crucial for protecting sensitive information and ensuring operational integrity. Organizations that effectively defend against passive intrusion vectors not only safeguard their data but also strengthen their overall security framework, ensuring compliance with regulatory standards and fostering trust with stakeholders.

In today's digital landscape, the significance of robust cybersecurity measures cannot be overstated, especially within the healthcare sector. Organizations must adopt best practices to defend against an array of attack vectors that threaten sensitive information and operational integrity.
Regular Security Audits are essential. Conducting frequent assessments allows organizations to identify vulnerabilities and ensure compliance with critical standards such as CMMC and HIPAA. This proactive approach not only mitigates risks but also reinforces the organization's commitment to safeguarding patient data.
Employee Training is equally vital. By educating staff on recognizing phishing attempts and other threats, organizations can foster a culture of vigilance. Emphasizing the importance of application allowlisting is crucial to prevent unauthorized software execution, thereby fortifying the organization's defenses.
Implementing Multi-Factor Authentication adds extra layers of security for sensitive systems, significantly improving protection against breaches. This measure is a fundamental step in creating a resilient cybersecurity framework.
Patch Management is another critical practice. Ensuring all software is current mitigates vulnerabilities, which is essential for maintaining compliance and protection. Regular updates are a straightforward yet effective way to enhance security.
An Incident Response Plan should be developed and regularly updated. This plan is vital for responding effectively to security breaches, ensuring that documentation aligns with compliance requirements and that the organization is prepared to act swiftly in the face of an incident.
Finally, 24/7 Threat Monitoring is imperative. Utilizing proactive cybersecurity solutions helps protect against ransomware and phishing incidents, ensuring continuous oversight of application activity. This constant vigilance is key to maintaining a secure environment.
By adopting these best practices, organizations can significantly lower the risk of successful intrusions while ensuring compliance with regulatory standards. The proactive implementation of these strategies not only enhances security but also instills confidence among stakeholders in the organization's commitment to cybersecurity.
Utilizing security intelligence is crucial for companies seeking to strengthen their cybersecurity measures against evolving intrusion methods. As we approach 2025, the landscape of cyber risks continues to shift dramatically, marked by a notable increase in sophisticated phishing schemes and AI-driven initiatives. Statistics reveal that over 60% of entities reported encountering new attack vectors definition in the past year, underscoring the importance of staying informed.
To effectively monitor emerging threats, organizations should:
Organizations such as Whitehorse City Council exemplify efficient oversight through their Managed Security Operation Centre (SOC), which operates continuously to identify and address risks in real-time. This ongoing vigilance has significantly bolstered their security stance, highlighting the importance of dedicated resources in tackling cyber challenges.
Industry leaders emphasize the necessity of understanding the attack vectors definition within the changing risk landscape. As one specialist noted, "It is crucial to watch for emerging dangers and trends; to achieve success, we must first comprehend the changing risk environment." By prioritizing threat intelligence, entities can protect their assets while ensuring compliance with regulatory frameworks, ultimately fostering a more secure digital environment.
Compliance with industry regulations is vital for mitigating risks associated with the attack vectors definition. Organizations must:
By emphasizing adherence, entities not only lower the risk of penalties but also enhance their protections against emerging cyber dangers. As regulatory bodies continue to enforce stringent measures, the importance of maintaining compliance in 2025 cannot be overstated.
C-suite executives must cultivate a strategic understanding of the attack vectors definition to effectively safeguard their enterprises. In today’s rapidly evolving cybersecurity landscape, understanding the attack vectors definition is not merely an option but a necessity. In fact, a staggering 84% of C-suite leaders in 2025 reported a heightened emphasis on cybersecurity compared to just three years prior, illustrating the critical importance of staying informed about emerging threats such as deepfakes and sophisticated phishing schemes.
Engaging with cybersecurity experts is paramount to grasping the attack vectors definition. With executives facing social engineering attacks at a rate 12 times higher than that of regular employees, the insights gained from professionals can significantly fortify a company's defenses. This collaboration not only enhances understanding of vulnerabilities but also empowers leaders by providing them with the attack vectors definition necessary to make informed decisions regarding their cybersecurity strategies.
Moreover, understanding the attack vectors definition is essential for integrating cybersecurity into the overall business strategy. Organizations that view cybersecurity as a strategic investment rather than a mere cost center are better positioned to effectively understand the attack vectors definition and mitigate risks. For instance, 75% of Chief Information Security Officers (CISOs) attribute a reduction in incidents to increased investment in artificial intelligence, underscoring the necessity of incorporating advanced technologies into protection strategies.
By fostering a culture of security awareness and proactive engagement, C-suite leaders can better shield their organizations from the ever-evolving landscape of cyber threats.
Understanding the intricacies of attack vectors is vital for C-suite leaders aiming to safeguard their organizations against the ever-evolving landscape of cyber threats. This article has highlighted the critical definitions and implications of various attack vectors, emphasizing their role as pathways exploited by cybercriminals to gain unauthorized access. By grasping these concepts, executives can better identify vulnerabilities within their systems and implement effective strategies to bolster their cybersecurity posture.
Key insights discussed include:
In conclusion, fostering a culture of security awareness and proactive engagement among C-suite leaders is essential in navigating the complexities of cybersecurity. By prioritizing a strategic approach to understanding attack vectors, organizations can not only protect sensitive information but also build trust with stakeholders. The time to act is now; investing in robust cybersecurity measures is not merely a defensive strategy but a fundamental aspect of ensuring long-term business resilience and success.
What services does Cyber Solutions Inc. provide to enhance cybersecurity?
Cyber Solutions Inc. offers a comprehensive suite of cybersecurity services that include 24/7 help desk support, endpoint protection, email safeguards, firewalls, and managed defense services to mitigate various attack vectors.
Why is 24/7 help desk support important in cybersecurity?
The 24/7 help desk support is crucial as it provides prompt assistance during incidents, helping to significantly reduce potential damage and enhance overall business protection.
What are attack vectors in the context of cybersecurity?
Attack vectors refer to the methods or pathways that cybercriminals exploit to gain unauthorized access to systems and networks.
What are some common types of attack vectors?
Common attack vectors include phishing, malware, ransomware, denial of service (DoS) attacks, and insider threats.
How can organizations protect against phishing attacks?
Organizations can protect against phishing attacks by implementing employee training programs that raise awareness about deceptive emails and by utilizing targeted defenses.
What is malware and how does it affect organizations?
Malware is malicious software that disrupts, damages, or gains unauthorized access to systems. Its impact can include operational disruptions and data breaches.
What is ransomware and what are its potential consequences?
Ransomware is a type of malware that encrypts files and demands payment for decryption. Its consequences can include significant operational disruptions and financial losses, as seen in the Change Healthcare incident.
What strategies can organizations employ to mitigate the risk of ransomware?
Organizations can adopt multi-factor authentication (MFA) and develop swift incident response strategies to effectively manage ransomware incidents.
What is the significance of application allowlisting in cybersecurity?
Application allowlisting is a proactive strategy that prevents unauthorized software from executing, thus minimizing exposure to threats and ensuring compliance with regulations.
Why is cybersecurity considered an ongoing process?
Cybersecurity is an ongoing process because it requires continuous oversight and adaptation to emerging challenges, emphasizing the need for a collective responsibility across the organization.
How do managed IT services benefit organizations?
Managed IT services provide a cost-effective alternative to maintaining an in-house team, enabling organizations to allocate resources more efficiently while achieving robust protection against cyber threats.