
In today's digital landscape, the significance of robust cybersecurity measures cannot be overstated, particularly for organizations in Greenville, SC. The article delves into the premier managed IT services available, spotlighting Cyber Solutions Inc. and their bespoke strategies designed to address the unique demands of diverse industries. Their tailored approach is especially crucial in enhancing cybersecurity and operational efficiency, empowering organizations to navigate the complexities of modern IT challenges.
Cyber Solutions Inc. offers a comprehensive suite of services, including:
These offerings not only bolster an organization's security posture but also allow them to concentrate on their core business operations. By effectively managing IT challenges, Cyber Solutions ensures that sensitive data remains safeguarded, thereby fostering trust and reliability in their client relationships.
As organizations face an ever-evolving array of cybersecurity threats, the implications for operational integrity are profound. Cyber Solutions Inc. stands ready to address these challenges head-on, providing the expertise and resources necessary to navigate the complexities of cybersecurity in an increasingly hostile environment. Their commitment to client success positions them as a leader in the managed IT services sector, making them an invaluable partner for businesses looking to enhance their cybersecurity framework.
In an era where digital threats are more pronounced than ever, businesses are increasingly acknowledging the imperative for robust managed IT services. For organizations in Greenville, SC, selecting the right IT partner can be pivotal, distinguishing between operational efficiency and costly disruptions. This article explores the foremost managed IT service providers in the region, emphasizing how tailored solutions can not only protect sensitive data but also elevate overall business performance. With numerous options at their disposal, how can business leaders ensure they select the right partner to adeptly navigate the complexities of today’s cybersecurity landscape?
In today's digital landscape, the importance of cybersecurity cannot be overstated, particularly for sectors like healthcare, finance, manufacturing, and government. The company distinguishes itself in Greenville, SC, by offering managed IT services that specifically address the unique requirements of these industries. With a client-focused and compliance-oriented strategy, they enable enterprises to concentrate on their primary operations while Cyber Solutions adeptly manages their IT challenges.
By leveraging advanced technology—such as endpoint protection, threat detection, and secure access controls—alongside proactive IT support and help desk services, Cyber Solutions empowers organizations to enhance their operational efficiency and security posture. This commitment to cybersecurity and compliance not only addresses the pressing challenges faced by CFOs but also positions them as a preferred choice for leaders seeking reliable IT support that aligns with their strategic objectives.
Are you ready to elevate your organization’s cybersecurity framework? With Cyber Solutions, you can rest assured that your IT needs are in capable hands, allowing you to focus on what truly matters—your core business operations.
Tech Services Inc. provides essential round-the-clock help desk assistance, enabling enterprises to swiftly tackle IT challenges and significantly reduce interruptions. This continuous availability is vital for sustaining operational efficiency, allowing organizations to resolve technical issues in real-time. The proactive support model not only enhances productivity but also fosters a culture of reliability and responsiveness within the organization. As cyber threats evolve and the end of life for Windows 10 approaches in 2025, the need for ongoing IT support becomes even more critical. Organizations leveraging 24/7 support can more effectively navigate these challenges, ensuring compliance and protection while minimizing downtime.
Cyber Solutions' advanced cybersecurity offerings—including endpoint protection, email safeguards, firewalls, and threat detection—further bolster this assistance, safeguarding sensitive data and ensuring operational continuity. Moreover, services such as SOC/SIEM, Data Backup Systems, and Patch Management are integral in reinforcing security measures. A recent study revealed that companies utilizing 24/7 support experienced a 30% increase in operational resilience and a 25% improvement in employee satisfaction, as IT issues are resolved proactively before escalating into significant problems. IT experts emphasize that reducing interruptions through continuous assistance is essential for maintaining momentum in today’s fast-paced environment, making it a strategic investment for future growth.

In today's digital landscape, cybersecurity is paramount, especially within the healthcare sector, where sensitive information is constantly at risk. Cyber Solutions Inc. employs advanced threat detection technologies to identify and neutralize potential cyber threats before they can inflict damage.
By consistently observing network activity and examining data trends, they can swiftly react to unusual behavior, thereby safeguarding sensitive organizational information. This proactive approach not only protects valuable assets but also significantly enhances trust in the organization’s security measures.
In an era where the stakes are higher than ever, the importance of robust cybersecurity solutions cannot be overstated.
In today's unpredictable environment, the importance of robust backup and disaster recovery options cannot be overstated. Organizations must guarantee continuity in the face of unforeseen circumstances, and this is where our comprehensive solutions come into play.
We offer:
These enable businesses to swiftly restore operations after any disruption. This capability not only safeguards critical data but also significantly minimizes potential financial losses associated with downtime.
In today's complex regulatory landscape, Compliance as a Service (CaaS) emerges as a vital strategic approach for organizations navigating the intricate web of requirements such as HIPAA, PCI-DSS, and GDPR. With a dedicated team of specialists, the company ensures that organizations not only meet industry standards but also significantly mitigate the risk of legal challenges, thereby enhancing customer trust.
By seamlessly integrating compliance into their IT strategies, organizations can prioritize growth and innovation, while cybersecurity experts adeptly manage their regulatory responsibilities. This proactive stance not only boosts operational efficiency but also equips companies to swiftly adapt to the ever-evolving compliance landscape, ensuring they remain audit-ready and resilient against potential regulatory hurdles.
In today's digital landscape, the significance of robust cybersecurity cannot be overstated. The company provides managed IT services in Greenville SC that greatly enhance an organization’s security stance through ongoing monitoring and professional evaluation. This proactive strategy is vital, especially as 94% of small enterprises reported being attacked in 2024, marking a significant rise from previous years. By utilizing advanced technologies and a team of skilled experts, Cyber Solutions offers extensive protection against emerging cyber threats, including ransomware and phishing attacks, which constitute a considerable share of incidents targeting small to midsize enterprises.
Continuous monitoring not only mitigates risks but also enhances operational resilience. Organizations that implement such services experience a marked improvement in their ability to respond to incidents swiftly, with the average recovery time for a major cyberattack now standing at 21 working days. Furthermore, statistics reveal that companies employing managed protection services can reduce the likelihood of successful cyberattacks by as much as 63% through routine phishing simulations and training.
For instance, OMV Polska, a leader in intralogistics, significantly improved its cybersecurity posture by adopting a FitSM-based approach, which included comprehensive monitoring and incident response capabilities. This transformation led to enhanced service quality and operational efficiency, illustrating the tangible benefits of managed IT services in Greenville SC. As the demand for these services continues to grow, fueled by the escalating complexity of digital threats, the company remains committed to empowering organizations to navigate this challenging environment securely.

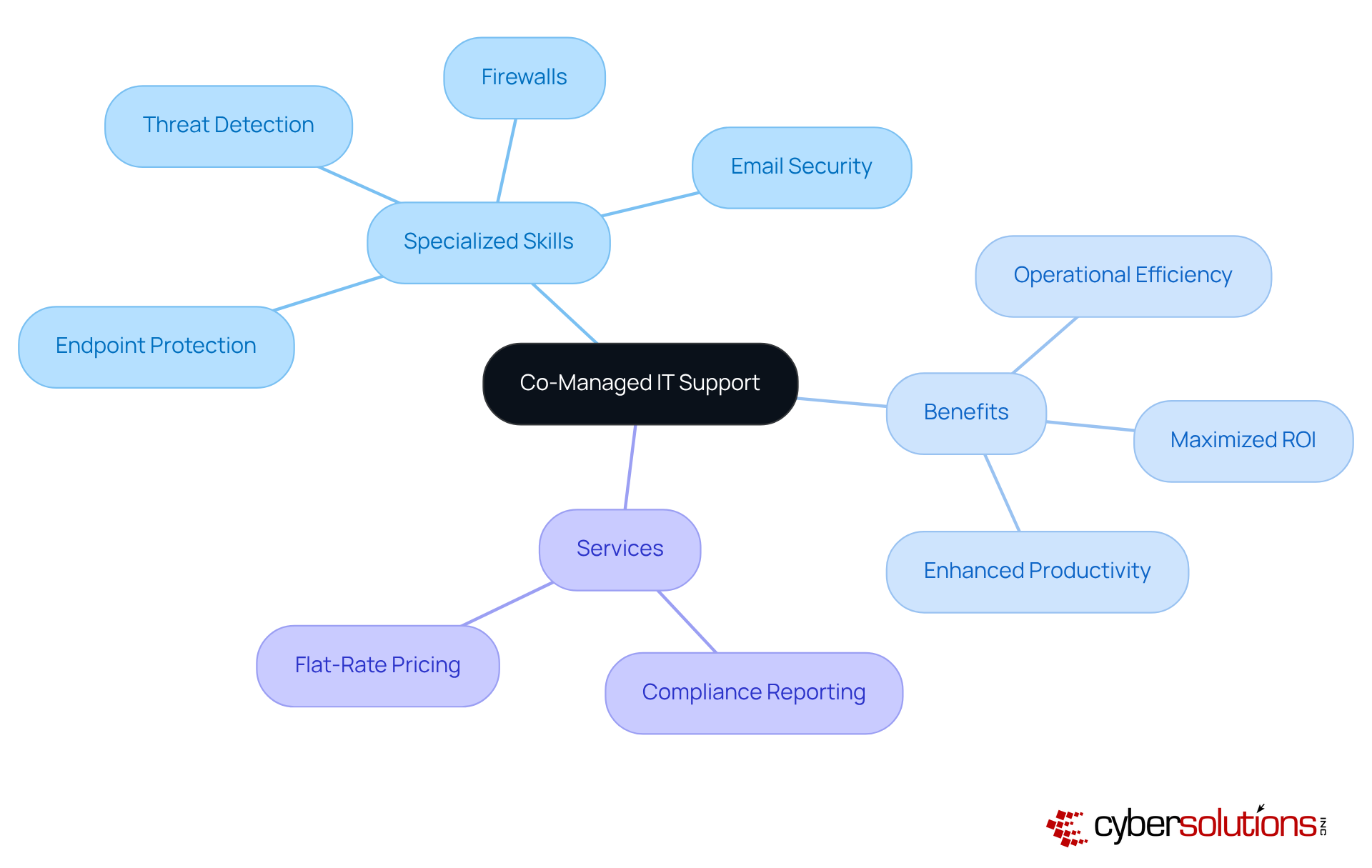
Co-managed IT support from an external firm is essential for organizations in Greenville SC aiming to bolster their internal IT teams by incorporating outside expertise, especially in advanced cybersecurity solutions. This collaborative framework allows organizations to leverage their existing knowledge while gaining specialized skills in:
By cultivating a partnership between internal and external resources, organizations can optimize their IT infrastructure, effectively address challenges, and enhance performance. This strategic approach not only improves operational efficiency but also maximizes ROI by minimizing costly downtime and elevating overall productivity.
Furthermore, our services encompass compliance reporting and flat-rate pricing, ensuring that C-Suite leaders are equipped with the comprehensive support necessary to navigate the ever-evolving digital landscape. In today's climate of increasing cybersecurity threats, it is imperative for healthcare organizations to remain vigilant and proactive.
How can your organization effectively tackle these challenges? By embracing managed IT Greenville SC, you position your team to not only respond to current threats but also anticipate future ones, ultimately safeguarding your operations and reputation.
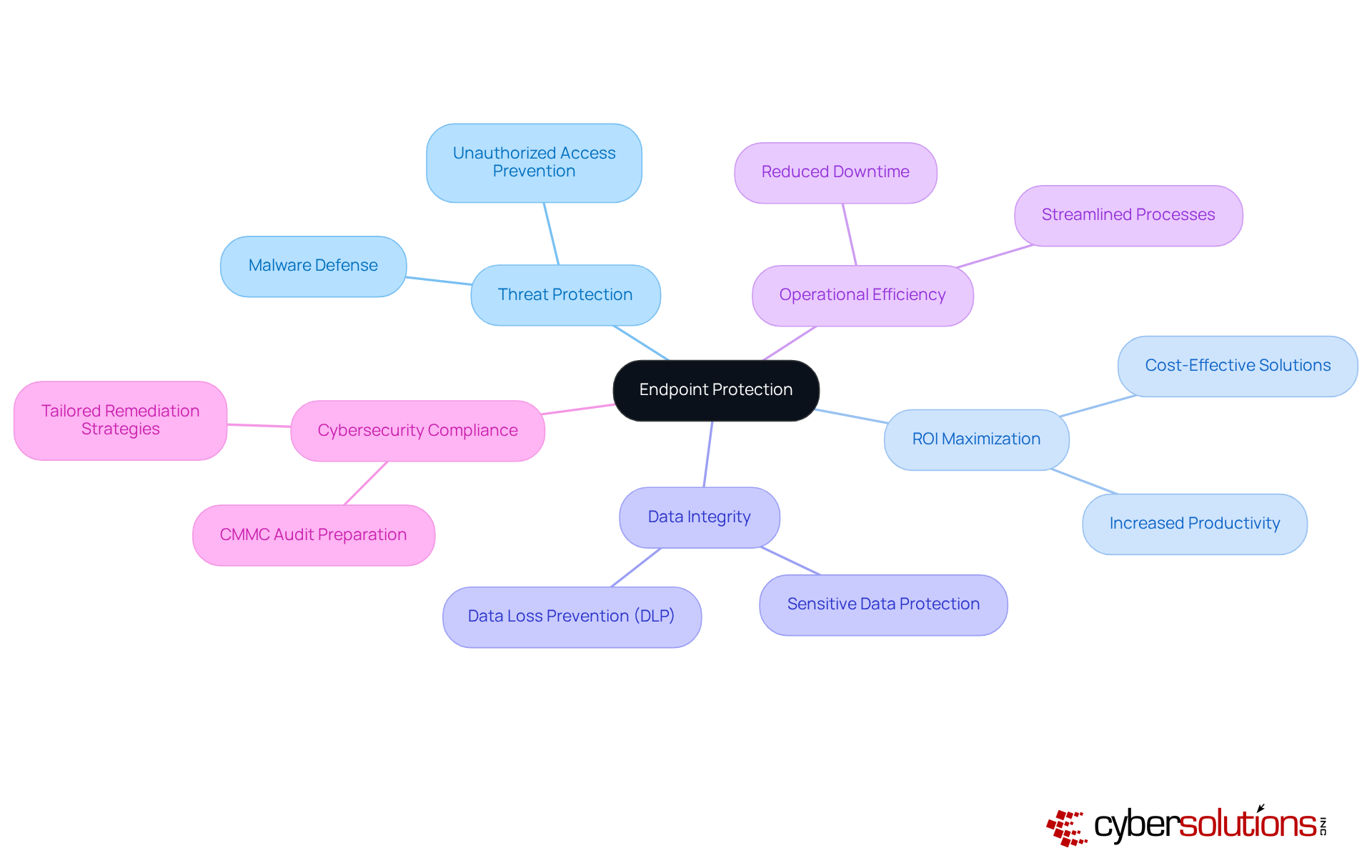
In today's digital landscape, robust endpoint protection is essential for safeguarding devices against ever-evolving threats. This company excels in delivering strong endpoint protection services that not only shield devices from digital threats but also maximize ROI for small to medium enterprises. By implementing sophisticated protection strategies, they ensure that all endpoints—whether desktops, laptops, or mobile devices—are fortified against unauthorized access and malware. This comprehensive approach maintains the integrity of sensitive data while enhancing operational efficiency, effectively reducing costly downtime.
Moreover, the organization plays a crucial role in helping enterprises adhere to vital cybersecurity practices. They equip businesses for CMMC audits through tailored remediation strategies and thorough documentation. This commitment ensures that employees can operate securely, regardless of their location, all while meeting necessary compliance standards. As cybersecurity threats continue to grow, partnering with an expert in endpoint protection is not just a choice; it’s a necessity for enterprises aiming to thrive in a secure environment.
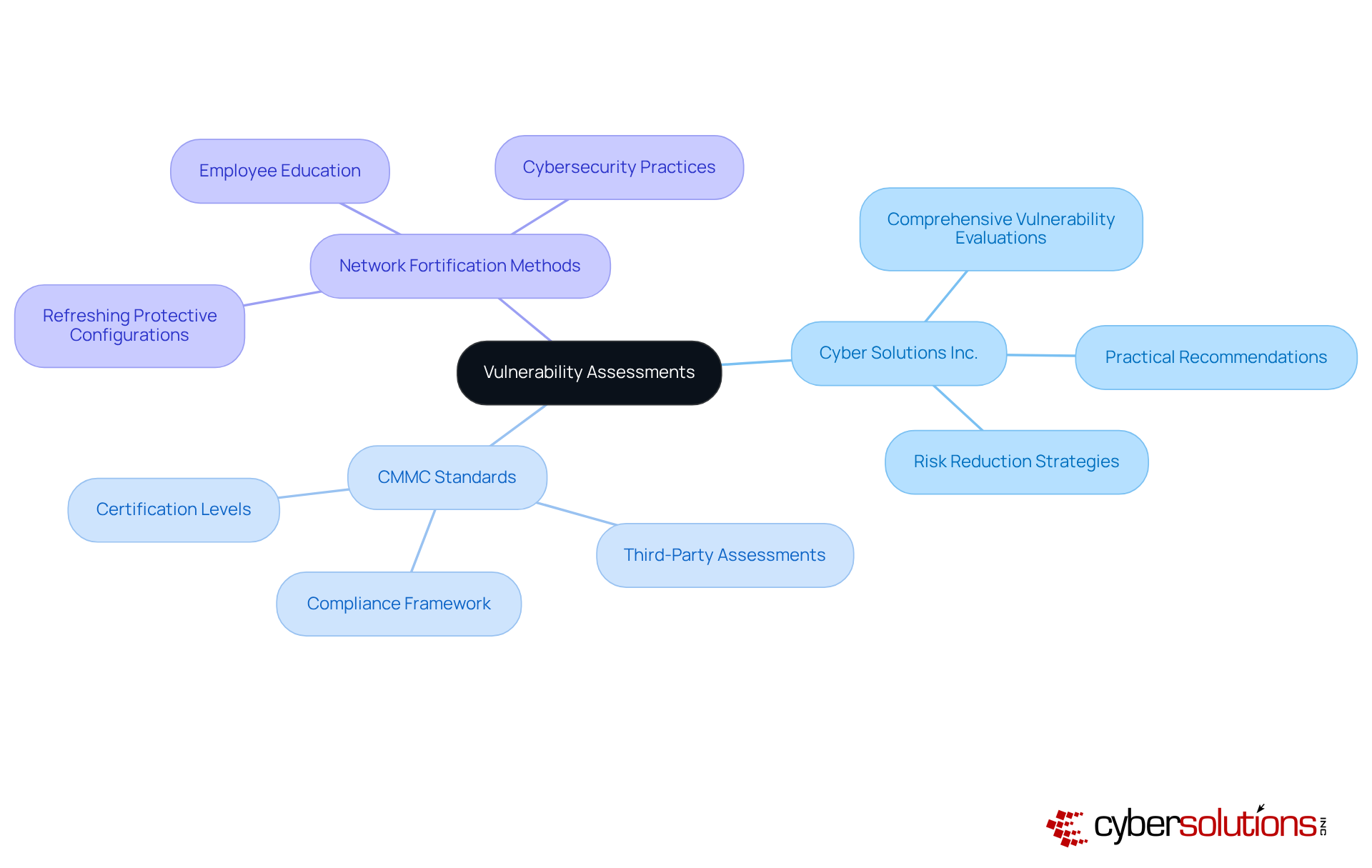
In today's digital landscape, the importance of cybersecurity cannot be overstated—especially for organizations operating within sensitive sectors. Cyber Solutions Inc. performs comprehensive vulnerability evaluations to detect and reduce risks within an organization’s IT framework. By examining systems and networks for possible vulnerabilities, they offer practical recommendations that assist businesses in enhancing their protective strategies. This proactive approach not only improves overall protection but also decreases the chances of costly data breaches.
Aligning with the Cybersecurity Maturity Model Certification (CMMC) standards is crucial for organizations, particularly those handling Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). CMMC encompasses various certification levels that necessitate third-party assessments, thereby establishing a robust compliance framework. Tech Inc. emphasizes the significance of network fortification methods, which include:
This comprehensive strategy not only fortifies the organization’s defenses but also fosters a culture of security awareness, ensuring minimal operational disruption and adherence to a zero trust security model. As organizations strive to navigate the complex cybersecurity landscape, partnering with experts like Cyber Solutions Inc. can be the key to safeguarding sensitive information and maintaining regulatory compliance.
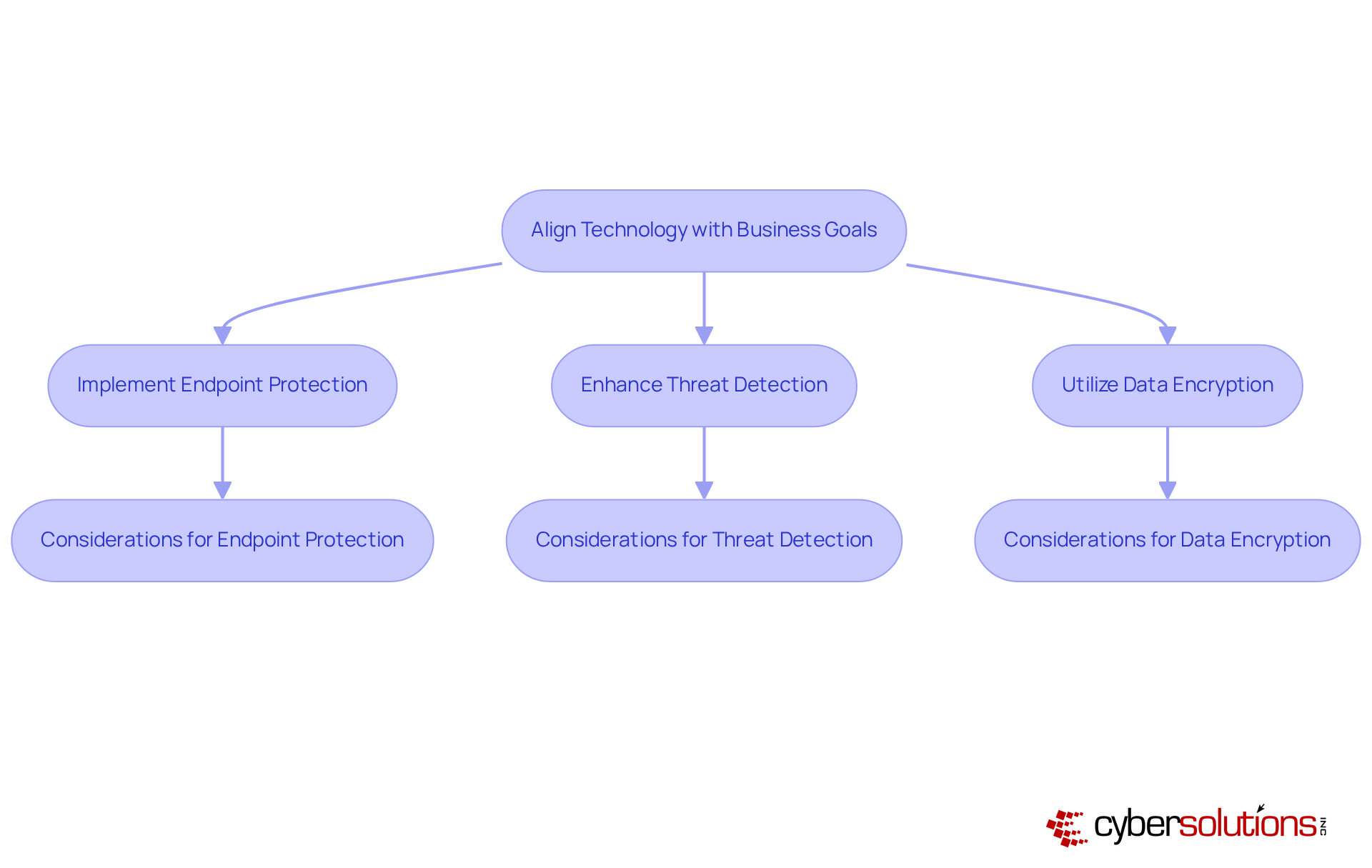
In today's digital landscape, the importance of strategic IT planning cannot be overstated, especially in sectors like healthcare, finance, manufacturing, and government. Cyber Solutions Inc. recognizes that aligning technology initiatives with organizational objectives is crucial for success. By understanding an organization’s specific goals, we can recommend tailored IT and cybersecurity solutions—such as endpoint protection, threat detection, and data encryption—that not only drive efficiency but also support growth and ensure compliance with industry standards.
This alignment is essential, as it maximizes the return on IT investments and acts as a catalyst for business success. The current landscape of cybersecurity threats presents unique challenges, particularly for healthcare organizations where data integrity and patient safety are paramount. How can organizations enhance their resilience against these evolving threats? The answer lies in implementing tailored solutions that address these pressing concerns.
To maintain eligibility for government contracts and safeguard sensitive information, consider adopting these strategic IT measures:
By doing so, your organization can navigate the complexities of cybersecurity with confidence, ensuring that you remain a step ahead in this ever-changing environment.
In the rapidly evolving digital landscape, the significance of managed IT services in Greenville, SC, cannot be overstated. Organizations seeking to enhance their operational efficiency and security posture must prioritize tailored solutions that address their unique challenges. By partnering with expert providers like Cyber Solutions Inc., businesses can focus on their core operations while ensuring robust cybersecurity measures are in place.
The article highlights several key aspects of managed IT services, including:
Each of these services plays a crucial role in maintaining business continuity and safeguarding sensitive information against emerging cyber threats. Furthermore, strategies such as co-managed IT support and endpoint protection are essential for fortifying an organization’s defenses and optimizing internal resources.
Ultimately, embracing managed IT services is not just a strategic investment; it is a necessary step for organizations aiming to thrive in an increasingly complex digital environment. By taking proactive measures and aligning technology with business goals, leaders can navigate the challenges of cybersecurity with confidence, ensuring their operations remain resilient and secure. Now is the time to evaluate your organization’s IT strategies and consider how managed services can elevate your business success.
What services does Cyber Solutions Inc. offer?
Cyber Solutions Inc. offers tailored managed IT services, including cybersecurity solutions, endpoint protection, threat detection, secure access controls, and help desk support, specifically designed for industries like healthcare, finance, manufacturing, and government.
How does Cyber Solutions Inc. enhance operational efficiency for businesses?
By leveraging advanced technology and providing proactive IT support, Cyber Solutions helps organizations manage their IT challenges effectively, allowing them to focus on their core business operations.
What is the significance of 24/7 help desk support?
The 24/7 help desk support provided by Cyber Solutions ensures continuous operational efficiency by enabling organizations to address IT challenges in real-time, reducing interruptions and enhancing productivity.
How does Cyber Solutions Inc. address cybersecurity threats?
Cyber Solutions employs advanced threat detection technologies to monitor network activity and identify potential cyber threats, allowing them to neutralize risks before they can cause damage.
What are the benefits of using 24/7 support according to recent studies?
Companies utilizing 24/7 support experienced a 30% increase in operational resilience and a 25% improvement in employee satisfaction, as IT issues are resolved proactively before escalating into significant problems.
Why is cybersecurity particularly important for the healthcare sector?
Cybersecurity is crucial for the healthcare sector because it handles sensitive information that is constantly at risk of cyber threats, making robust security measures essential for protecting valuable data.
What additional services does Cyber Solutions provide to reinforce security measures?
In addition to threat detection, Cyber Solutions offers services such as SOC/SIEM, data backup systems, and patch management to further enhance security and ensure operational continuity.