
The article underscores the critical importance of an effective business disaster recovery plan, essential for navigating unforeseen disruptions. It delineates ten key elements that are vital for operational continuity, including:
These components are not merely suggestions; they are foundational to minimizing downtime and ensuring that organizations can swiftly recover from unexpected challenges. In a landscape where disruptions can arise at any moment, having a robust recovery plan is not just advantageous—it is imperative.
In a world where unexpected disruptions can jeopardize the very foundation of a business, the significance of a robust disaster recovery plan is paramount. Organizations encounter the formidable challenge of safeguarding their data while ensuring operational continuity amid chaos.
This article explores the ten essential elements that constitute an effective business disaster recovery plan, providing insights into best practices and strategies that can empower companies to emerge resilient from crises.
What transpires when a disaster occurs, and how prepared are businesses to respond with efficacy?
In today's fast-paced digital landscape, Cyber Solutions Inc. provides an extensive range of backup and disaster management services, including a business disaster recovery plan, which are essential for maintaining operational continuity. Central to these offerings are automated backups, which play a crucial role in minimizing downtime and safeguarding critical data. Remarkably, 96% of businesses with reliable backup solutions can fully resume operations after data loss incidents, underscoring the importance of proactive measures in today's environment.
The firm's offerings include:
Both are vital for organizations striving to protect their operations from unforeseen interruptions. A practical framework for developing a robust business disaster recovery plan involves:
Case studies reveal that organizations employing automated backup strategies achieve significantly enhanced restoration outcomes. For instance, 39% of businesses with a comprehensive business continuity management framework can restore all mission-critical operations with minimal issues. This statistic emphasizes the effectiveness of organized restoration planning in bolstering resilience.
As we look toward 2025, approximately 84% of organizations are expected to store data or backups in the cloud, reflecting a shift towards cloud-based solutions that facilitate faster recovery and improved data management. By leveraging these advanced technologies, Cyber Solutions Inc. empowers enterprises to remain operational and profitable, even amidst challenges, showcasing a steadfast commitment to protecting their clients' interests.
Implementing advanced threat detection systems is essential for identifying vulnerabilities and potential cyber threats before they escalate. In today's digital landscape, where cyber threats are increasingly sophisticated, organizations must prioritize cybersecurity to protect sensitive information. Cyber Solutions offers round-the-clock threat monitoring, ensuring that suspicious activities are swiftly identified and halted, thus safeguarding companies from ransomware, phishing, and other malware attacks. These systems leverage machine learning and behavioral analytics to scrutinize network activity, enabling organizations to respond to threats in real-time.
By integrating threat detection into emergency response strategies, organizations can significantly reduce risks and enhance their overall security posture. This proactive approach not only shields against immediate threats but also fortifies the network as operations evolve. In a world where the stakes are high, the need for robust cybersecurity measures has never been more critical.
Compliance as a Service (CaaS) is crucial for organizations navigating the intricate landscape of industry regulations such as HIPAA, PCI-DSS, CMMC, SOX, and GDPR. Our CaaS solutions streamline the process of adhering to these complex requirements by offering:
By seamlessly integrating CaaS into the business disaster recovery plan, businesses can ensure that their restoration strategies align with regulatory mandates, effectively mitigating the risk of non-compliance penalties. This service not only facilitates ongoing evaluations and updates to keep action plans in sync with evolving regulations but also includes incident response solutions designed to minimize the impact of cyber threats.
Moreover, the proactive monitoring and real-time reporting capabilities of CaaS empower organizations to identify compliance gaps early, reinforcing their dedication to regulatory adherence. This strategic approach not only safeguards against potential penalties but also enhances operational resilience, establishing CaaS as a vital component of an effective business disaster recovery plan.
An effective incident response plan is essential for minimizing damage during a disaster. This plan must delineate clear procedures for identifying, responding to, and recovering from incidents, including breach reporting and remediation plans to comply with HIPAA standards. Organizations that establish a dedicated incident response team and predefined protocols can achieve rapid recovery, significantly reducing downtime and associated costs. In 2025, the average cost of a data breach is projected to escalate to $4.56 million, underscoring the financial stakes involved. For small businesses, the average attack can result in losses ranging from $120,000 to $1.24 million, making swift incident response critical.
Real-world examples demonstrate that entities with strong incident response strategies, including 24-hour on-site support, can recover swiftly from cyber incidents, thereby reducing potential losses. Adhering to incident response best practices enables teams to detect attacks sooner, stop them faster, and minimize escalation, ultimately leading to a more resilient operational framework. Regular training and simulations further enhance preparedness, ensuring that teams are equipped to handle incidents effectively and efficiently.
Additionally, establishing and testing communication channels during incidents is crucial for effective incident management, while post-incident reviews help identify lessons learned and improve future responses. Thorough documentation, including risk assessments and compliance reports, is vital to ensure audit readiness and adherence to HIPAA’s strict timelines.
Routine vulnerability evaluations are crucial for uncovering potential flaws in the business disaster recovery plan's disaster response strategies. These evaluations assess the effectiveness of current measures and pinpoint specific areas needing enhancement. In 2025, entities that conducted regular evaluations reported a significant improvement in recovery effectiveness, with 96% able to fully resume operations after a data loss incident. This proactive approach empowers businesses to address vulnerabilities before they escalate into critical issues, ultimately enhancing their resilience.
A notable case involved a healthcare entity that identified outdated backup systems during a vulnerability assessment. By upgrading their technology and implementing regular testing protocols, they reduced downtime from weeks to mere hours, significantly mitigating operational disruptions. In contrast, numerous entities face a typical restoration period of over a month from ransomware incidents, underscoring the importance of prompt enhancements and the necessity for ongoing oversight to identify suspicious actions before they evolve into threats.
To effectively identify weaknesses in recovery strategies, entities should focus on integrating threat intelligence and automated scanning tools. Cybersecurity experts emphasize that aligning vulnerability management with regulatory frameworks is essential for compliance and operational integrity. As one expert pointed out, "A strong vulnerability management program integrates automated scanning, manual verification, and prioritization, ensuring that entities can swiftly address high-risk vulnerabilities."
Furthermore, implementing 24/7 threat monitoring can significantly bolster a company's capacity to safeguard against ransomware, phishing, and other malware attacks. This proactive cybersecurity solution ensures that suspicious activities are identified and managed promptly, further enhancing emergency response strategies. By incorporating these monitoring solutions into their restoration strategies, entities can ensure a more robust response to potential threats.
To maintain a strong emergency response strategy, entities are urged to arrange quarterly vulnerability evaluations and integrate 24/7 threat monitoring as crucial components of their business disaster recovery plan to ensure that their strategies remain resilient and effective. Frequent vulnerability evaluations not only enhance crisis management plans but also enable entities to navigate the complexities of contemporary threats, ensuring they are prepared for any outcome.
Co-managed IT support is vital for entities seeking to leverage the strengths of both internal and external IT resources, significantly enhancing their disaster response efforts. This collaborative model grants access to a broader range of expertise and advanced tools, empowering businesses to respond more effectively to incidents. By incorporating co-managed assistance into their restoration strategies, organizations can fortify their IT infrastructure, leading to improved resilience and reduced downtime.
Notably, firms experiencing frequent interruptions incur costs that are 16 times greater than those with fewer disruptions, underscoring the financial imperative for effective emergency planning. In ransomware scenarios, immediate action and specialized expertise are paramount, as evidenced by case studies where swift incident response and a structured response plan successfully contained threats.
Furthermore, nearly 49% of organizations are investing in AI and automation to bolster their disaster management capabilities, reflecting a growing recognition of the need for advanced technologies in this domain. Real-world examples illustrate that entities utilizing co-managed IT not only improve their recovery outcomes but also cultivate a more robust operational framework, ensuring preparedness for future disruptions.
As IT leaders assert, collaboration between internal teams and external partners is crucial for navigating the complexities of modern business continuity. The four pillars of crisis recovery—Preparedness, Response, Recovery, and Mitigation—constitute a framework that co-managed IT supports, equipping entities to manage disruptions effectively.

Endpoint protection is essential for safeguarding data during disasters, particularly as organizations increasingly rely on connected devices. By implementing robust security measures across all endpoints—such as laptops, desktops, and mobile devices—entities can ensure that sensitive information remains secure, even in the event of a breach. With 80-90% of successful ransomware attacks originating from unmanaged devices, prioritizing endpoint security is vital for minimizing data loss and maintaining operational continuity during crises.
Recent trends show a shift towards advanced Endpoint Detection and Response (EDR) solutions, which provide continuous monitoring and proactive threat detection. These systems utilize machine learning and behavioral analytics to identify suspicious activities, significantly enhancing an organization's ability to respond to emerging threats. In fact, 51% of IT professionals believe that endpoint attacks succeed due to ineffective security solutions, underscoring the necessity of adopting modern protective measures.
Real-world examples demonstrate the impact of effective endpoint security on data loss prevention. Organizations that have adopted comprehensive endpoint protection strategies report a marked decrease in incidents of data breaches and operational disruptions. As we approach 2025, the integration of EDR technologies and a focus on safeguarding connected devices will be crucial for enabling organizations to manage crises with resilience and confidence.
Furthermore, 24/7 threat monitoring is critical in this landscape, ensuring that suspicious activities are detected and addressed before they escalate into significant threats. This continuous vigilance complements application allowlisting, which prevents unauthorized or malicious applications from executing on endpoints, thereby reducing the attack surface and enhancing compliance with regulations such as HIPAA and GDPR. Organizations that implement application allowlisting alongside EDR and continuous monitoring report a notable reduction in incidents of data breaches and operational disruptions, showcasing the effectiveness of a layered security approach.
Cybersecurity experts emphasize that a proactive approach to endpoint security is not merely a technical necessity but a vital organizational strategy. As one expert noted, "In our hyper-connected world, safeguarding data is as critical as any other aspect of business continuity." This perspective highlights the importance of viewing endpoint protection as a fundamental component of a business disaster recovery plan. Additionally, with 80% of successful breaches attributed to new or unknown zero-day attacks, the urgency for modern endpoint protection measures cannot be overstated.
A well-defined communication plan is essential for keeping stakeholders informed during a disaster. This plan must specify the methods of information dissemination, designate responsible individuals for communication, and identify the channels to be utilized. Clear and timely communication not only manages expectations but also fosters trust among clients, employees, and partners during crises.
Consider this: 72% of consumers expect brands to respond to crises within 24 hours. This statistic underscores the necessity for speed in communication. Furthermore, entities that proactively communicate during crises can significantly reduce reputational harm; 89% of businesses with a documented crisis communication strategy successfully minimized such damage. Yet, only 49% of surveyed U.S. firms have a formal crisis communication plan, indicating a notable gap in preparedness.
Experts emphasize that transparency is crucial; 83% of consumers value honesty and accountability during crisis management. As Bryan Strawser notes, effective stakeholder engagement and a robust communication team are vital for navigating crises. Additionally, social media has emerged as a critical channel for real-time crisis communication, enabling brands to control narratives and interact directly with concerned customers.
By adhering to these principles, organizations can enhance stakeholder trust and navigate crises more effectively.
Routine evaluation of emergency response strategies is paramount for maintaining their efficiency. Organizations must implement simulations and drills to rigorously assess their responses to a variety of disaster scenarios. This proactive approach not only uncovers gaps in the response plan but also guarantees that all team members are thoroughly familiar with their roles during an actual incident. A comprehensive risk evaluation is essential for identifying potential threats, while a business disaster recovery plan helps in prioritizing critical IT systems that require restoration. By conducting regular simulations, entities can validate their restoration strategies, ensuring that Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO) are both practical and achievable.
Industry leaders emphasize that crisis management is not a one-time endeavor but rather an ongoing commitment. Regular drills significantly enhance team readiness, empowering groups to refine their strategies and minimize disruptions. For example, companies that engage in quarterly crisis management testing often report improved restoration outcomes, as these practices bolster skill retention among employees and clarify responsibilities. Furthermore, simulation tests provide a realistic assessment of processes, enabling entities to identify bottlenecks and overlooked components before they can be exploited during a genuine crisis.
As we approach 2025, the impact of simulation exercises on crisis restoration outcomes has become increasingly evident, with organizations recognizing that successful restoration hinges on a well-prepared team. Numerous industries now mandate periodic testing for compliance, intensifying the urgency for regular assessments. The longer the interval between crisis management evaluations, the higher the risk of outdated protocols and vulnerabilities. By fostering a culture of continuous improvement through frequent assessments, companies can ensure their contingency plans evolve alongside emerging technologies and risks, ultimately safeguarding their operations against unforeseen disruptions.
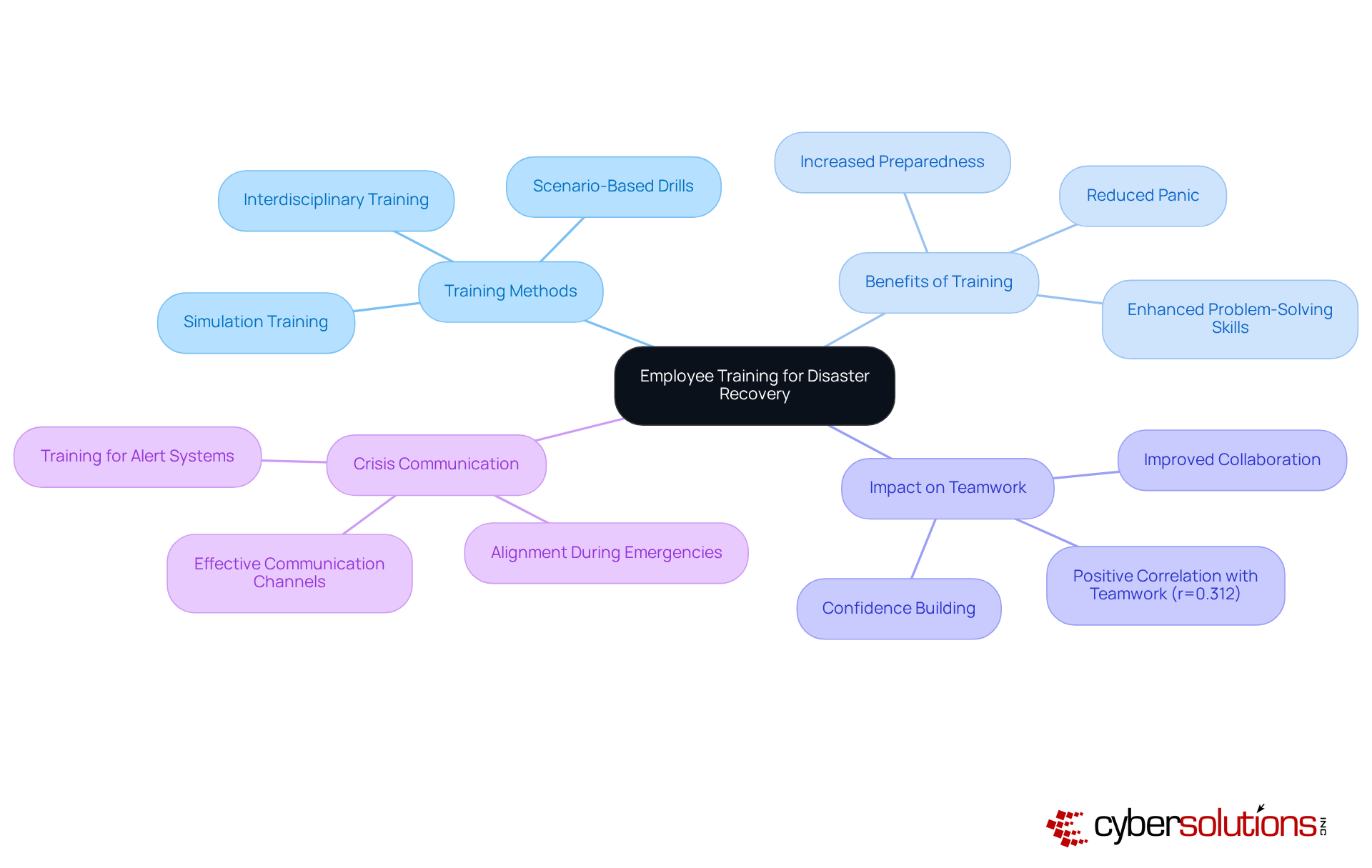
Employee training is a pivotal element in a strong business disaster recovery plan. Organizations must implement regular training sessions to ensure that all employees are adept in their roles and responsibilities during a crisis. For instance, simulation-based training has demonstrated remarkable effectiveness, with participants reporting significantly higher preparedness levels compared to those who received solely theoretical instruction. This hands-on approach not only bolsters confidence but also enhances teamwork capabilities, as evidenced by a moderate positive correlation (r=0.312) between interdisciplinary training and improved collaboration.
Investing in comprehensive training programs can dramatically diminish downtime during emergencies. Studies indicate that organizations with a business disaster recovery plan and proactive training strategies can respond swiftly, minimizing confusion and facilitating a quicker return to normal operations. In 2025, the impact of such training was evident when companies that had equipped their teams successfully managed to sustain productivity despite significant interruptions caused by natural events. Importantly, 65.6% of participants had not received any prior emergency preparedness training, underscoring a substantial gap that highlights the necessity for such programs.
Optimal methods for training staff on emergency response include scenario-based drills that enhance problem-solving and decision-making abilities. These exercises prepare teams to tackle unexpected challenges with agility and confidence. Furthermore, effective communication during emergencies is critical; training should encompass the use of appropriate channels for alerts and updates, ensuring that everyone is aligned and working cohesively. As Mitchel Rosen emphasizes, responders must be equipped with both the knowledge and skills to act decisively during crises.
Insights from training professionals reinforce the necessity of a business disaster recovery plan that includes routine disaster preparedness training. By fostering a culture of preparedness through regular training, organizations not only enhance their operational resilience but also demonstrate a commitment to employee safety, ultimately building trust and morale within the workforce.
A robust business disaster recovery plan is not just beneficial; it is essential for organizations striving to maintain continuity and resilience in the face of unforeseen disruptions. This article has outlined ten critical elements that contribute to an effective disaster recovery strategy, emphasizing the importance of preparation, proactive measures, and continuous improvement to safeguard operations.
Key insights reveal the necessity of automated backups and meticulous restoration planning, both of which significantly enhance recovery outcomes. The integration of threat detection technologies, compliance as a service, and incident response strategies further solidifies the framework for managing risks effectively. Additionally, routine vulnerability assessments, co-managed IT support, and endpoint protection are vital components that empower organizations to swiftly adapt to challenges while maintaining data integrity. Regular testing and employee training are crucial for refining response strategies and equipping teams to act decisively during crises.
Ultimately, the emphasis on a comprehensive and well-structured disaster recovery plan cannot be overstated. Organizations must recognize that investing in these key elements not only mitigates risks but also fortifies their operational resilience. By adopting best practices and remaining vigilant against emerging threats, businesses can navigate the complexities of disaster recovery with confidence, ensuring they are well-prepared for whatever challenges may arise in the future.
What services does Cyber Solutions Inc. provide for backup and disaster recovery?
Cyber Solutions Inc. offers a comprehensive range of backup and disaster management services, including automated backups, data duplication, and meticulous restoration planning to ensure operational continuity.
Why are automated backups important for businesses?
Automated backups minimize downtime and safeguard critical data, allowing businesses to fully resume operations after data loss incidents. Studies show that 96% of businesses with reliable backup solutions can recover successfully.
What steps are involved in developing a business disaster recovery plan?
A robust business disaster recovery plan involves identifying critical systems and data, classifying essential operations, and implementing automated processes to ensure regular data capture.
How do automated backup strategies impact restoration outcomes?
Organizations employing automated backup strategies experience significantly enhanced restoration outcomes. For example, 39% of businesses with a comprehensive business continuity management framework can restore all mission-critical operations with minimal issues.
What is the expected trend for data storage by 2025?
By 2025, approximately 84% of organizations are expected to store data or backups in the cloud, indicating a shift towards cloud-based solutions for faster recovery and improved data management.
What is the role of threat detection in cybersecurity?
Advanced threat detection systems are essential for identifying vulnerabilities and potential cyber threats before they escalate. Cyber Solutions Inc. offers round-the-clock threat monitoring to swiftly identify and halt suspicious activities.
How does Cyber Solutions Inc. enhance security posture for organizations?
By integrating threat detection into emergency response strategies, organizations can reduce risks and enhance their overall security posture, shielding against immediate threats and fortifying their network.
What is Compliance as a Service (CaaS)?
Compliance as a Service (CaaS) helps organizations navigate industry regulations such as HIPAA, PCI-DSS, CMMC, SOX, and GDPR by providing comprehensive risk assessments, policy development, and continuous compliance monitoring.
How does CaaS benefit business disaster recovery plans?
CaaS ensures that restoration strategies align with regulatory mandates, mitigating the risk of non-compliance penalties. It includes ongoing evaluations and updates to keep action plans in sync with evolving regulations.
What capabilities does CaaS offer to organizations?
CaaS provides proactive monitoring and real-time reporting to identify compliance gaps early, enhancing operational resilience and safeguarding against potential penalties.