
In today’s digital landscape, the importance of robust cybersecurity cannot be overstated, particularly for C-suite leaders tasked with safeguarding their organizations. The article delves into essential firewall solutions that these leaders should consider to bolster their cybersecurity posture. It highlights ten prominent firewall solutions, each equipped with advanced features such as real-time monitoring, threat detection, and compliance capabilities. These features are not merely enhancements; they are crucial for protecting sensitive data and ensuring operational efficiency amidst the ever-evolving cyber threats that organizations face.
Understanding the current landscape of cybersecurity threats is paramount. Organizations are increasingly targeted by sophisticated cybercriminals, making it imperative for leaders to implement effective security measures. The implications of inadequate cybersecurity can be severe, leading to financial loss, reputational damage, and regulatory repercussions. In this context, the article presents firewall solutions as vital tools for addressing these challenges, enabling organizations to stay ahead of potential threats.
Each firewall solution discussed offers unique capabilities tailored to meet the diverse needs of organizations. By investing in these advanced technologies, C-suite leaders can not only enhance their cybersecurity defenses but also foster a culture of compliance and vigilance within their teams. As the threat landscape continues to evolve, proactive measures are essential to protect sensitive information and maintain trust with stakeholders.
In conclusion, the article serves as a critical resource for C-suite leaders, providing insights into essential firewall solutions that can significantly enhance their organization’s cybersecurity framework. By prioritizing these technologies, leaders can ensure they are well-equipped to navigate the complexities of the digital age.
In a world where cyber threats are not just increasing but evolving at an alarming pace, the role of firewalls in organizational security has never been more critical. C-suite leaders must navigate a complex landscape of cybersecurity solutions to protect sensitive data and ensure compliance with stringent regulations. This article explores ten essential firewall solutions that not only bolster security but also enhance operational efficiency, offering executives valuable insights into how they can fortify their defenses. As organizations face the daunting challenge of safeguarding against sophisticated attacks, the question remains: which firewall solution will best align with their unique security needs and strategic objectives?
In an era where cybersecurity threats are increasingly sophisticated, organizations must prioritize robust firewall solutions to ensure security. Cyber Solutions offers a strong security system that delivers comprehensive protection tailored for enterprises of all sizes. This firewall solution integrates seamlessly with existing IT infrastructure, enabling organizations to maintain operational efficiency while safeguarding sensitive data. Key features include:
These features not only defend against external threats but also facilitate compliance with industry regulations. This proactive approach significantly enhances security posture and mitigates potential financial risks.
Real-world examples underscore the effectiveness of security system integration. For instance, companies that installed security barriers reported enhanced network performance by filtering out harmful traffic and superfluous data, ensuring seamless operations. Furthermore, a multi-layered security strategy that encompasses protective barriers, regular security audits, and employee training has proven vital in strengthening defenses against cyber threats.
The latest advancements in security technology further empower organizations. Contemporary security systems employ stateful inspection to assess the context of data packets, enabling the identification of advanced attacks. This capability is essential as network security systems act as the first line of defense against cyber threats, including malware and unauthorized access. By preventing recognized malware and dubious traffic, security systems greatly lower the threat of infections that could jeopardize systems or result in data loss.
In summary, Cyber Solutions' security system not only enhances operational efficiency but also plays a critical role in protecting sensitive information, such as customer data and financial records, from unauthorized access. As the cybersecurity landscape evolves, investing in a sophisticated firewall solution is crucial for organizations aiming to navigate the complexities of contemporary IT environments.

In today's digital landscape, a firewall solution is paramount for enterprises, particularly in sectors like healthcare, to ensure cybersecurity. Fortinet's firewall solution stands out as a high-performance security option designed to meet these critical needs. They provide advanced danger protection through robust features such as:
Furthermore, implementing application allowlisting is essential for organizations striving to enhance their cybersecurity posture. This proactive measure effectively prevents malware and unauthorized software from executing, significantly reducing the attack surface and mitigating vulnerabilities.
The importance of application allowlisting cannot be overstated, as it safeguards against threats like ransomware and zero-day attacks. Additionally, it aids organizations in meeting stringent compliance standards such as:
By leveraging Fortinet's Security Fabric architecture, businesses can achieve seamless integration with other protective solutions, including application allowlisting, thereby adopting a comprehensive firewall solution for cybersecurity. This makes Fortinet an ideal choice for organizations looking to bolster their security while managing costs efficiently.

Palo Alto Networks devices represent a pivotal advancement in threat prevention, harnessing cutting-edge machine learning and artificial intelligence to enhance protective measures. In a landscape where cybersecurity threats are increasingly sophisticated, these security systems utilize deep packet inspection to conduct thorough analyses of network traffic, ensuring that only legitimate data is processed. This capability, combined with application awareness and user identification, empowers organizations to implement robust protection policies effectively.
Moreover, integrating application allowlisting into your cybersecurity strategy is not just beneficial; it is essential. Allowlisting proactively prevents unauthorized or malicious applications from executing, significantly reducing the attack surface and minimizing vulnerabilities. This strategic approach not only aids in blocking malware and ransomware but also ensures compliance with stringent regulations such as HIPAA, PCI-DSS, and GDPR.
Investing in Palo Alto's firewall solution, along with application allowlisting, can lead to a substantial reduction in risk exposure. Research indicates that organizations employing these protective measures experience up to a 50% decrease in incidents. Experts consistently affirm the efficacy of Palo Alto Networks security systems, emphasizing their ability to adapt to evolving threats and provide comprehensive defense.
Practical applications of machine learning within these systems demonstrate their capability to detect and mitigate advanced threats in real-time, thereby enhancing their strategic importance for C-suite executives aiming to fortify their organization’s defense posture. As the cybersecurity landscape continues to evolve, the necessity for robust, intelligent solutions becomes increasingly clear.
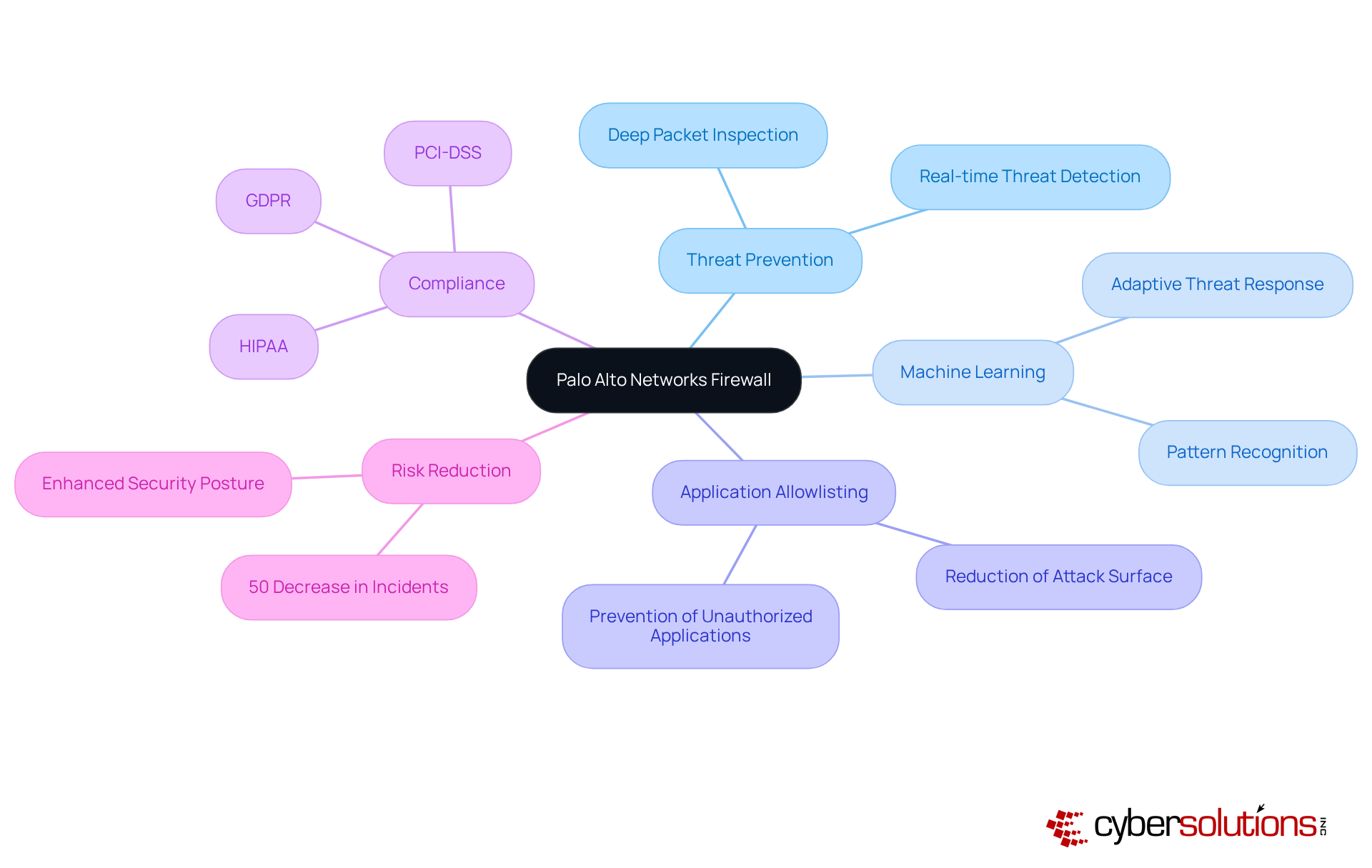
Cisco security devices are recognized as essential network protection solutions, trusted by enterprises globally to defend their systems against evolving threats. In an era where cyberattacks are increasingly sophisticated, these security systems not only protect against intrusions but also ensure secure access for users, a critical requirement in today’s digital landscape. A significant advantage of Cisco security systems lies in their robust compliance capabilities, featuring comprehensive reporting and monitoring tools designed to help organizations meet industry regulations effectively. Statistics reveal that organizations utilizing Cisco security systems achieve compliance success rates exceeding 90%, with many reporting improved adherence to standards.
Real-world examples demonstrate Cisco's advanced risk defense in action, significantly mitigating threats and enhancing overall security posture. By integrating application allowlisting into your cybersecurity strategy, you can further amplify the effectiveness of Cisco security systems. This proactive approach prevents unauthorized software from executing, thereby reducing the attack surface and minimizing vulnerabilities. Application allowlisting continuously monitors application behavior, ensuring swift identification and mitigation of risks, which fortifies the already strong protection provided by Cisco devices.
As cybersecurity threats continue to escalate, the importance of secure access and reliable firewall solutions cannot be overstated. Cisco protective systems, including their firewall solution, are a vital component of any organization’s cybersecurity strategy. Cybersecurity expert Lexi Croisdale aptly states, 'With breaches increasing, it’s essential to prioritize cybersecurity,' underscoring the critical need for robust solutions like Cisco security systems.
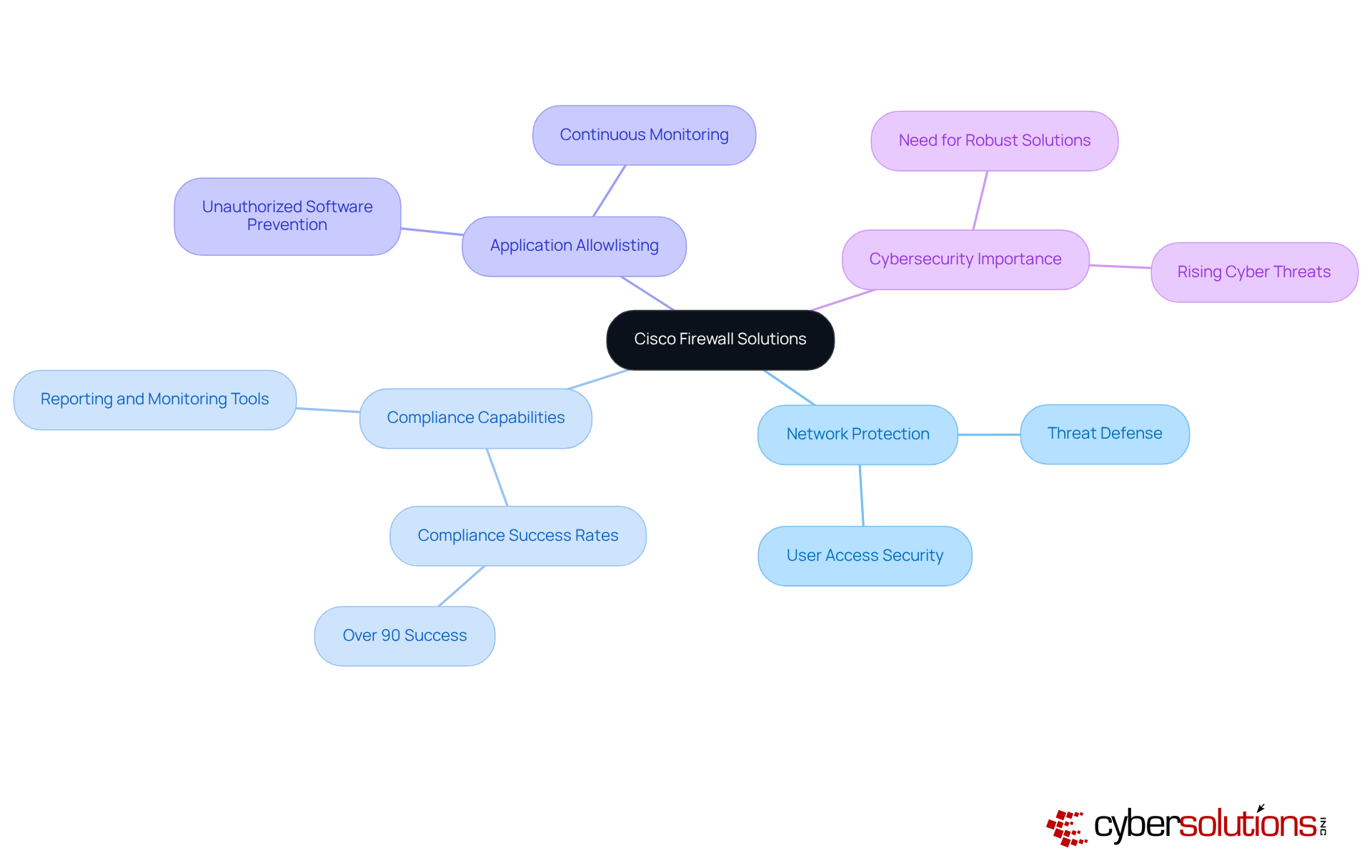
In today's rapidly evolving digital landscape, the significance of cybersecurity in healthcare cannot be overstated. Check Point's firewall solution serves as a bulwark against a myriad of threats, ensuring compliance with stringent regulatory frameworks. This makes them indispensable for organizations operating in highly regulated sectors such as healthcare and finance.
The advanced threat prevention capabilities of Check Point, coupled with centralized management and automated compliance reporting, not only streamline security processes but also enhance operational efficiency. For instance, organizations leveraging Check Point's solutions can significantly reduce the average 277 days it typically takes to detect and contain a data breach. This reduction is crucial, as the potential financial impact of such breaches can average $4.44 million per incident.
Moreover, implementing a firewall solution such as Check Point facilitates adherence to vital regulations like HIPAA and PCI DSS, ensuring that sensitive data remains protected and compliance requirements are consistently met. The practical application of automated compliance reporting further streamlines regulatory adherence, empowering organizations to proactively manage their risk posture.
Additionally, organizations can bolster their defenses through practical measures such as:
By investing in Check Point's solutions, businesses can effectively mitigate risks, safeguard sensitive information, and uphold a robust compliance framework.
C-Suite executives should consider conducting a comprehensive evaluation of their current security posture and explore how the integration of a firewall solution can enhance their cybersecurity strategy.
In today's digital landscape, a robust firewall solution is essential for small and medium-sized enterprises (SMBs) to ensure cybersecurity. Sophos protective systems offer accessible firewall solutions tailored specifically for these organizations, addressing the unique challenges they face. With straightforward deployment processes and intuitive management interfaces, SMBs can effectively secure their networks with a firewall solution, without the need for extensive IT resources.
Sophos stands out by integrating sophisticated functionalities, such as synchronized protection, which facilitates real-time risk intelligence sharing between endpoints and gateways. This advanced integration significantly enhances overall protection efficiency, empowering businesses to respond swiftly to emerging threats. The practical applications of Sophos systems have demonstrated their capacity to bolster protective measures, making their firewall solution a preferred choice for entities dedicated to safeguarding sensitive information while maintaining operational efficiency.
By choosing Sophos, organizations can navigate the complexities of cybersecurity with confidence, ensuring they remain resilient against evolving threats. The time to act is now—secure your enterprise with Sophos and safeguard your critical assets.
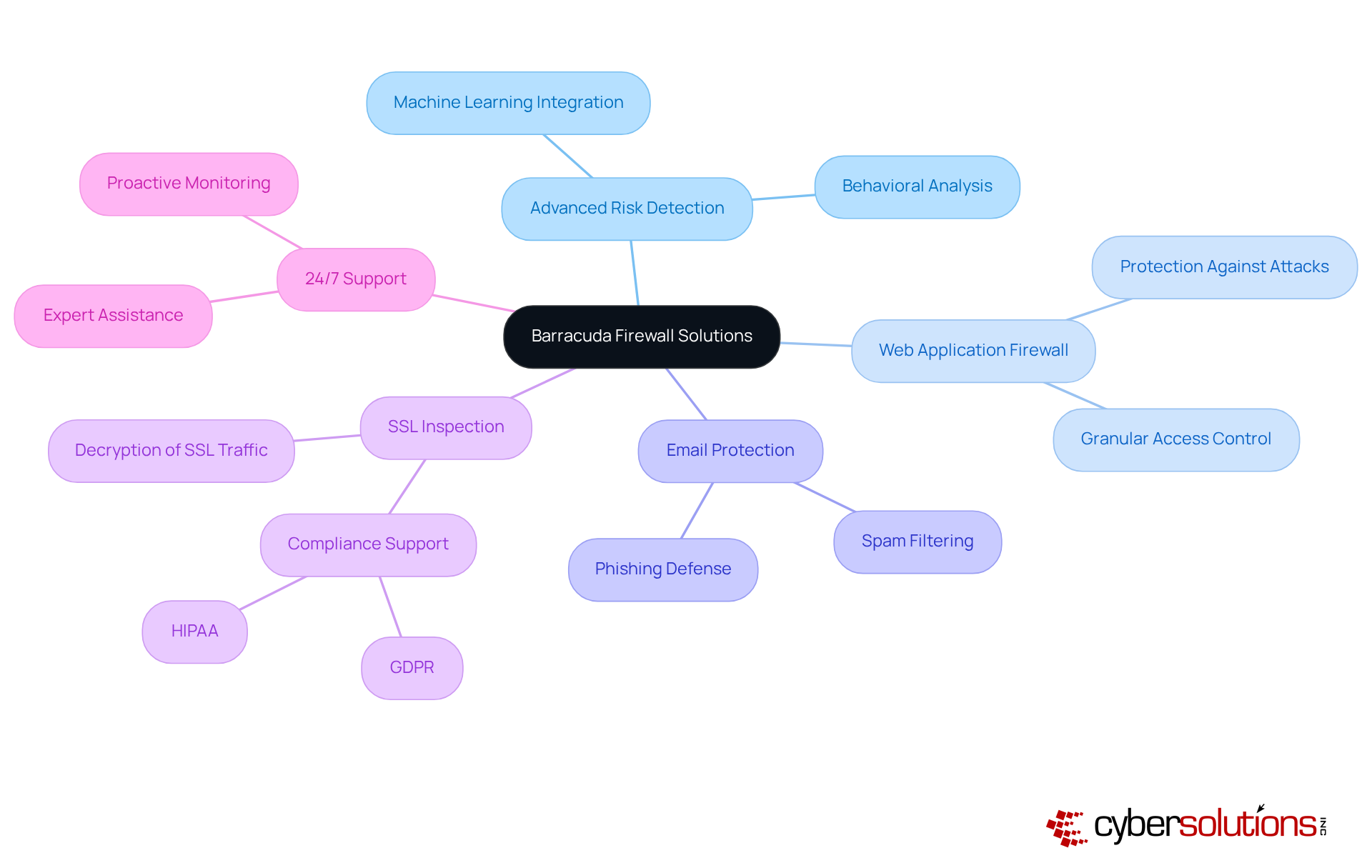
In today's rapidly evolving digital landscape, the significance of robust cybersecurity measures cannot be overstated, particularly in the healthcare sector. Barracuda security systems provide a comprehensive firewall solution as part of their risk management solutions, designed to shield organizations from a multitude of cyber threats. Their offerings, including advanced risk detection, a firewall solution for web applications, and email protection solutions, are essential in addressing the unique challenges faced by CFOs and other executives in safeguarding sensitive information.
With a staggering 34% increase in the exploitation of vulnerabilities as an initial access vector since 2024, the urgency for effective defenses has reached critical levels. Barracuda’s multi-faceted defense strategy, featuring an effective firewall solution, ensures extensive protection against both known and emerging threats, making it an indispensable choice for C-suite executives determined to fortify their security frameworks. The integration of machine learning and behavioral analysis within their Advanced Threat Protection feature significantly enhances the ability to detect and thwart sophisticated attacks.
Moreover, Barracuda’s SSL Inspection capabilities allow for the decryption and examination of SSL traffic, exposing hidden dangers that could compromise organizational integrity. This proactive approach not only mitigates risks but also supports compliance with regulatory standards such as GDPR and HIPAA, thereby reinforcing Barracuda's status as a leader in enterprise protection solutions. As organizations navigate the complexities of cybersecurity, the need for innovative and reliable firewall solutions like those offered by Barracuda becomes increasingly paramount.
In today's digital landscape, the importance of a firewall solution for cybersecurity cannot be overstated, especially for large organizations facing evolving threats. Juniper Networks devices provide a scalable firewall solution designed to tackle these challenges head-on, ensuring robust defense against emerging cyber risks. Equipped with advanced threat intelligence features, this firewall solution empowers organizations to proactively identify and mitigate potential threats, thereby reinforcing their security posture.
Automated policy enforcement simplifies the management of these protections, allowing for the consistent application of protocols across the network. This is crucial in a realm where human error remains a significant vulnerability in cybersecurity. Furthermore, Juniper's centralized management capabilities enable real-time monitoring and reporting, which are essential for compliance with stringent regulations such as GDPR and HIPAA.
By incorporating application allowlisting, organizations can significantly enhance their protective measures. This proactive approach prevents unauthorized or harmful applications from executing, thereby reducing the attack surface and minimizing vulnerabilities. As organizations grow, the ability to adjust protective measures not only bolsters safety but also enhances operational efficiency, making Juniper Networks an indispensable asset for businesses navigating complex regulatory environments.

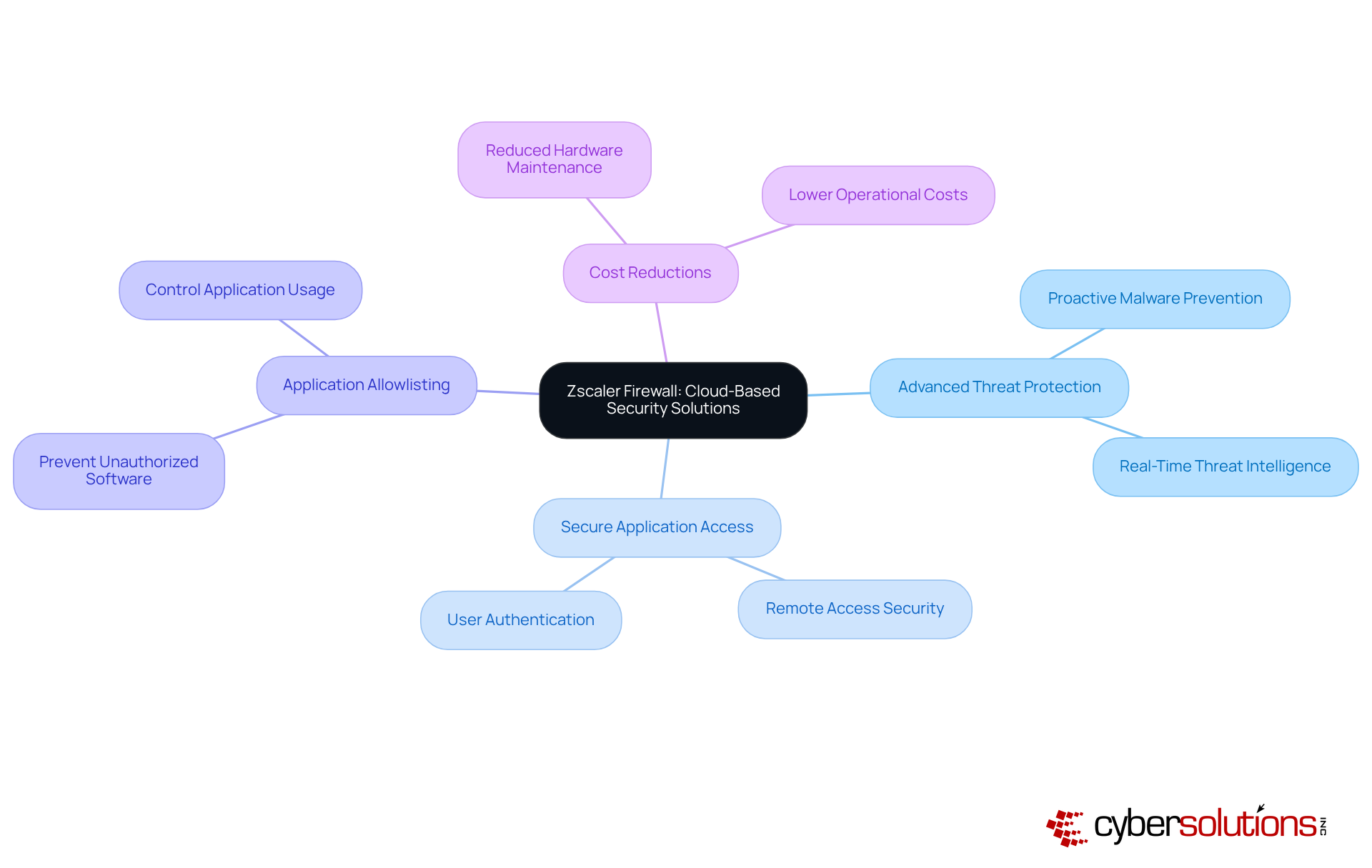
In today's digital landscape, the need for a robust firewall solution to ensure cybersecurity is paramount. Zscaler firewalls offer strong cloud-based protection that enables companies to safeguard their networks without relying on traditional on-premises hardware. This innovative platform not only delivers advanced threat protection and secure access to applications but also underscores the critical role of application allowlisting, proactively preventing malware and unauthorized software from executing. By adopting Zscaler's cloud solutions, businesses can significantly reduce expenses associated with conventional hardware while enhancing their protective measures.
For instance, organizations utilizing Zscaler have reported substantial reductions in operational costs, as the necessity for extensive hardware maintenance and upgrades diminishes. Cybersecurity specialists emphasize that a firewall solution within cloud-based protective systems simplifies management and improves overall efficiency, allowing entities to allocate resources more effectively. As organizations navigate the complexities of contemporary cybersecurity threats, the financial and operational advantages of cloud security systems make them an increasingly attractive option for C-suite executives aiming to strengthen their security strategies.
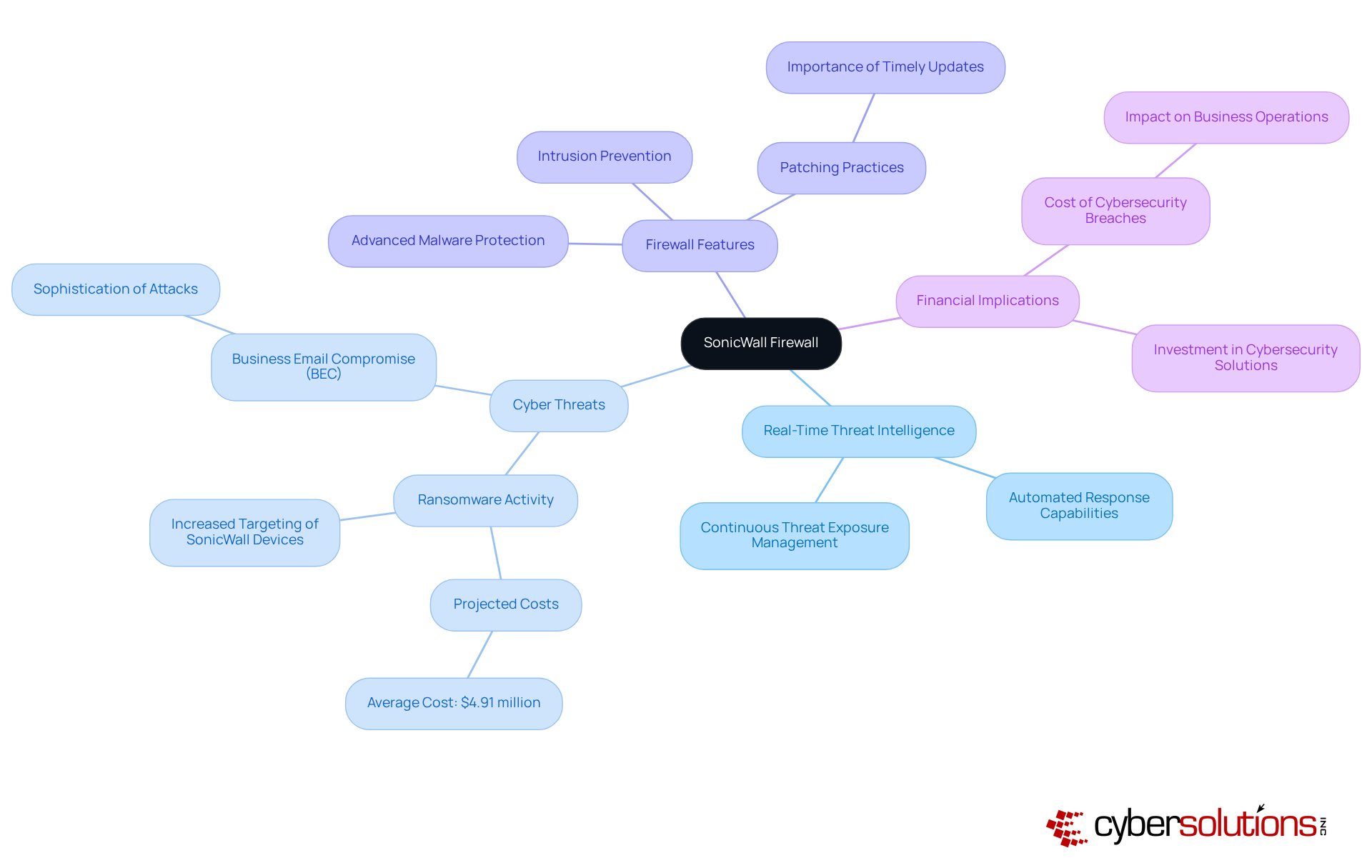
SonicWall's firewall solution is pivotal in delivering real-time risk intelligence and robust defenses against emerging cyber threats, particularly for organizations handling federal data. Their comprehensive firewall solution includes advanced malware protection, intrusion prevention, and automated response capabilities—essential elements in today’s fast-paced digital environment. By leveraging SonicWall's real-time threat intelligence and implementing a firewall solution, organizations can respond swiftly to emerging risks, significantly mitigating exposure and ensuring compliance with stringent cybersecurity standards vital for protecting Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
This proactive approach is underscored by a striking statistic: ransomware incidents are projected to cost businesses an average of $4.91 million in 2024. This highlights the urgent financial necessity for effective cybersecurity measures. The recent surge in ransomware targeting SonicWall devices further underscores the critical need for organizations to maintain current patching practices and implement automated response strategies. In response to such threats, Cyber Solutions Inc. exemplifies rapid incident response by implementing a firewall solution, mobilizing specialized teams to contain ransomware attacks and bolster system defenses, ensuring that organizations remain eligible for lucrative government contracts.
Industry leaders assert that adopting proactive cybersecurity strategies is essential for safeguarding sensitive data and ensuring compliance in an increasingly regulated landscape. For C-suite executives seeking to fortify their cybersecurity frameworks, a firewall solution such as SonicWall emerges as a crucial element in the quest for comprehensive protection and operational resilience.
In the realm of cybersecurity, the significance of implementing robust firewall solutions cannot be overstated, especially for C-suite leaders navigating the complexities of modern threats. The current landscape of cybersecurity threats demands attention, as organizations face evolving risks that jeopardize sensitive data and operational integrity. This article highlights a selection of essential firewall solutions, each tailored to meet the diverse needs of enterprises while ensuring comprehensive protection against these risks.
Key insights reveal the multifaceted benefits of various firewall solutions:
The integration of these firewalls not only fortifies defenses but also streamlines compliance processes, thereby reducing the potential financial impact of data breaches.
As the cybersecurity landscape continues to evolve, the imperative for C-suite executives to adopt innovative and reliable firewall solutions becomes increasingly clear. Investing in these technologies is not merely a defensive measure; it is a strategic decision that can significantly bolster an organization's security posture and operational resilience. By taking proactive steps to evaluate and implement the right firewall solutions, leaders can ensure their organizations remain secure in an increasingly digital world. The call to action is clear: prioritize advanced security measures to safeguard sensitive data and enhance operational efficiency.
What is the purpose of Cyber Solutions Firewall?
The Cyber Solutions Firewall provides comprehensive protection for businesses by integrating seamlessly with existing IT infrastructure to safeguard sensitive data and enhance operational efficiency.
What are the key features of Cyber Solutions Firewall?
Key features include real-time monitoring, threat detection, and automated incident response, which help defend against external threats and facilitate compliance with industry regulations.
How does the Cyber Solutions Firewall enhance network performance?
By filtering out harmful traffic and unnecessary data, the Cyber Solutions Firewall enhances network performance, ensuring seamless operations for organizations.
What is the significance of a multi-layered security strategy?
A multi-layered security strategy, which includes protective barriers, regular security audits, and employee training, is vital for strengthening defenses against cyber threats.
How does stateful inspection contribute to network security?
Stateful inspection assesses the context of data packets, enabling the identification of advanced attacks, which is essential for preventing malware and unauthorized access.
What role does Fortinet Firewall play in cybersecurity for enterprises?
Fortinet Firewall provides advanced security solutions for enterprises, particularly in sectors like healthcare, with features such as intrusion prevention systems, application control, and web filtering.
What is application allowlisting, and why is it important?
Application allowlisting prevents malware and unauthorized software from executing, significantly reducing the attack surface and mitigating vulnerabilities, thus enhancing cybersecurity posture.
How does Fortinet Firewall assist with compliance standards?
Fortinet Firewall aids organizations in meeting compliance standards such as HIPAA, PCI-DSS, and GDPR through its advanced security features and application allowlisting.
What advancements does Palo Alto Networks Firewall offer?
Palo Alto Networks Firewall utilizes machine learning and artificial intelligence for threat prevention, employing deep packet inspection to analyze network traffic effectively.
Why is application allowlisting essential in cybersecurity strategies?
Application allowlisting is essential as it proactively prevents unauthorized or malicious applications from executing, thereby reducing the attack surface and ensuring compliance with regulations.
What benefits do organizations experience by using Palo Alto Networks Firewall?
Organizations using Palo Alto Networks Firewall experience a substantial reduction in risk exposure, with research indicating up to a 50% decrease in incidents.
How does machine learning enhance the effectiveness of Palo Alto Networks Firewall?
Machine learning enables real-time detection and mitigation of advanced threats, enhancing the strategic importance of Palo Alto Networks Firewall for organizations' defense postures.