
The primary focus of this article is to delineate the essential components of a security assessment report that leaders must consider. In today's landscape, where cybersecurity threats loom large, a comprehensive report is not just beneficial but imperative. It should encompass critical elements such as:
These components must be tailored to address specific vulnerabilities and compliance requirements within organizations, especially those operating in regulated industries. This approach not only enhances the security posture but also aligns with best practices in risk management.
In an era where cyber threats loom larger than ever, the significance of security assessment reports has become paramount for organizational leaders across various industries. These reports illuminate vulnerabilities and serve as strategic blueprints for risk management and compliance assurance. As organizations grapple with the complexities of cybersecurity, they must consider: what are the essential elements that make a security assessment report not just informative, but transformative in safeguarding assets and ensuring regulatory adherence?
Understanding the current landscape of cybersecurity threats is crucial. Organizations face an array of risks that can compromise their operations and reputation. The implications for businesses are profound, as they navigate regulatory requirements and the need for robust risk management strategies.
Cyber Solutions can effectively address these challenges, providing insights that empower organizations to fortify their defenses. By leveraging comprehensive security assessment reports, leaders can make informed decisions that not only protect their assets but also ensure compliance with industry standards.
Ultimately, the right security assessment report can be a game-changer, transforming how organizations approach cybersecurity and risk management.
In today's digital landscape, the importance of cybersecurity cannot be overstated, particularly in sectors such as healthcare, finance, and government. Cyber Solutions Inc. specializes in creating security assessment reports that are meticulously tailored to meet the unique needs of these industries. By thoroughly understanding the specific regulatory and operational challenges they face, Cyber Solutions ensures that each security assessment report not only identifies vulnerabilities but also aligns seamlessly with industry standards and regulatory requirements.
A pivotal aspect of these evaluations is the emphasis on application allowlisting, a proactive strategy designed to combat malware and unauthorized software. This tailored approach significantly enhances the relevance and effectiveness of the evaluations, transforming them into indispensable tools for organizational leaders focused on compliance assurance and risk mitigation.
As the threat landscape evolves, healthcare organizations must recognize the implications of these challenges. Cyber Solutions stands ready to equip them with the insights and strategies necessary to navigate this complex environment effectively, ensuring that they remain ahead of potential threats.

The main aim of a safety evaluation document is to deliver a comprehensive analysis of an organization's protective stance. In today's landscape, where cybersecurity threats are ever-present, it is crucial to identify vulnerabilities, assess risks, and provide actionable recommendations to mitigate potential threats. By serving as a guide for risk management, these documents empower leaders to prioritize security initiatives, allocate resources effectively, and ensure compliance with regulatory standards such as HIPAA, PCI-DSS, and GDPR.
Moreover, integrating Compliance as a Service (CaaS) into the assessment process grants organizations access to enterprise-level compliance expertise, simplifying the compliance journey while safeguarding against potential penalties. The document also underscores the significance of application allowlisting as a proactive strategy against malware and unauthorized software, ensuring that only approved applications can operate within the organization. Ultimately, these documents are vital in protecting organizational assets and maintaining operational integrity.
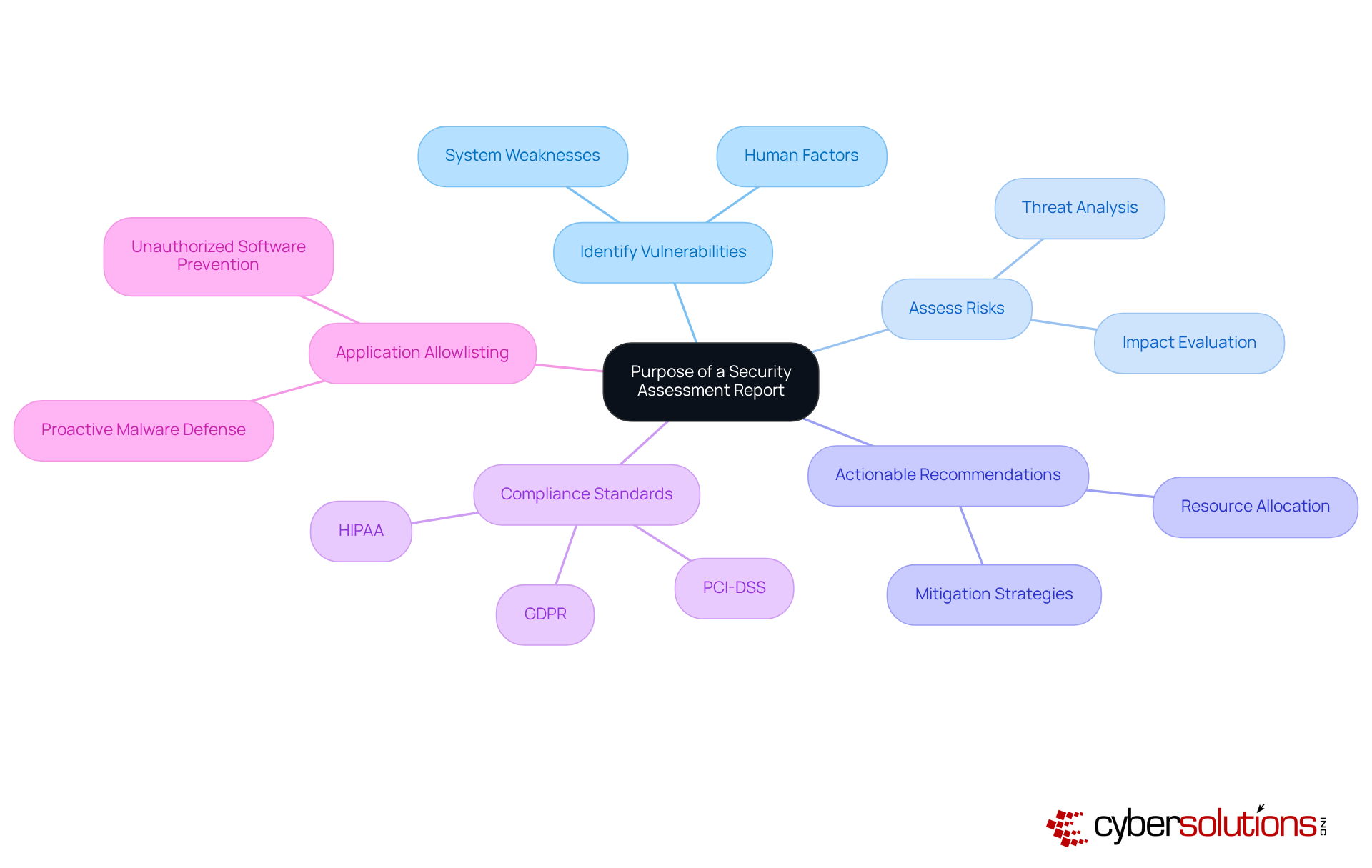
A comprehensive security assessment report is essential for protecting healthcare organizations from evolving cyber threats. It should include the following key components:
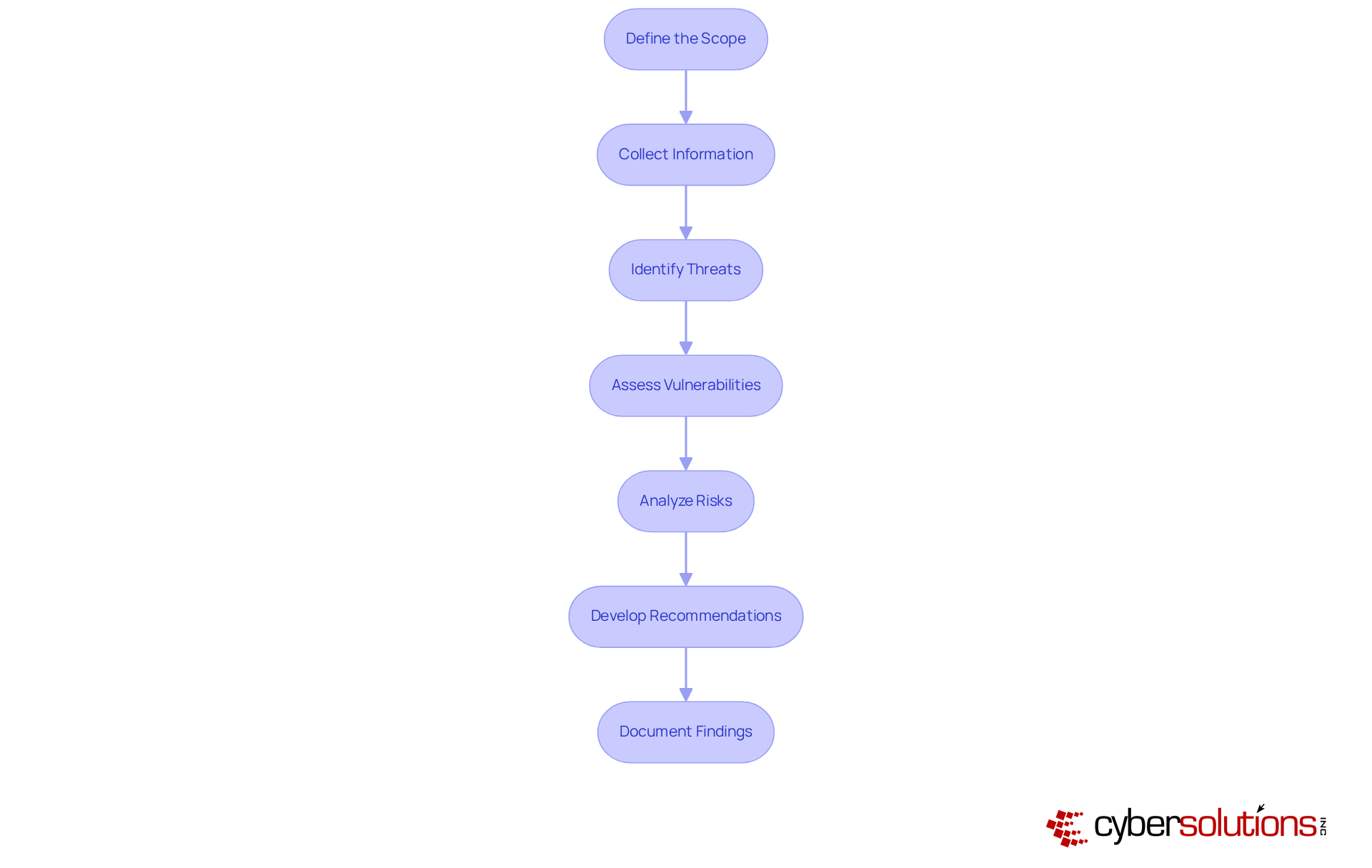
Conducting a security assessment is paramount in the realm of cybersecurity, particularly within healthcare organizations. The following critical steps outline a comprehensive approach to safeguarding valuable assets:
By following these steps, healthcare CFOs can effectively navigate the complex landscape of cybersecurity threats and implement robust strategies to protect their organizations.
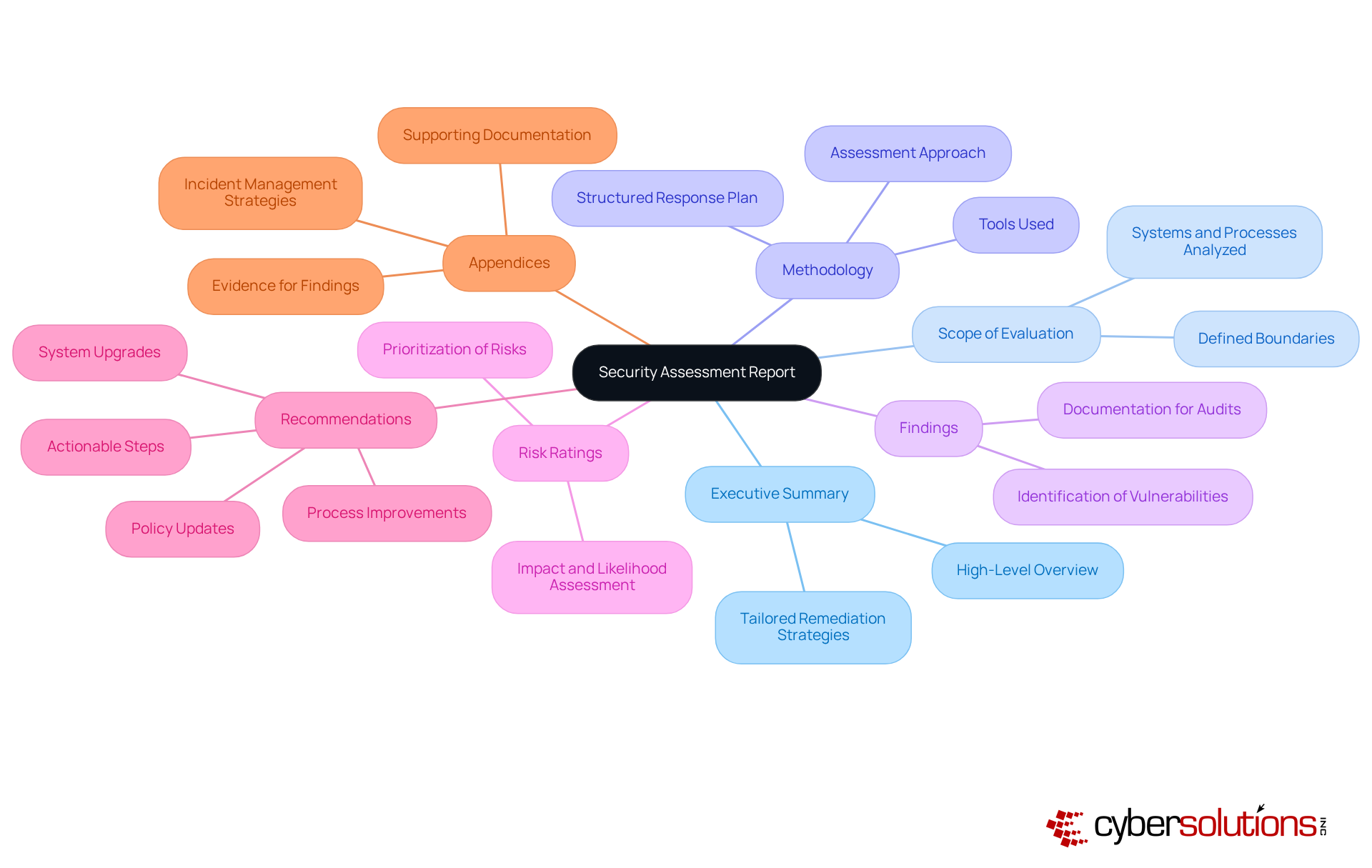
Thorough documentation of discoveries and suggestions is crucial for the influence of the security assessment report. To effectively communicate this importance, consider the following best practices:

Adherence factors are essential in safety evaluations, particularly for entities in regulated sectors such as healthcare, finance, manufacturing, and legal. Understanding these factors is crucial for maintaining compliance and safeguarding organizational integrity.
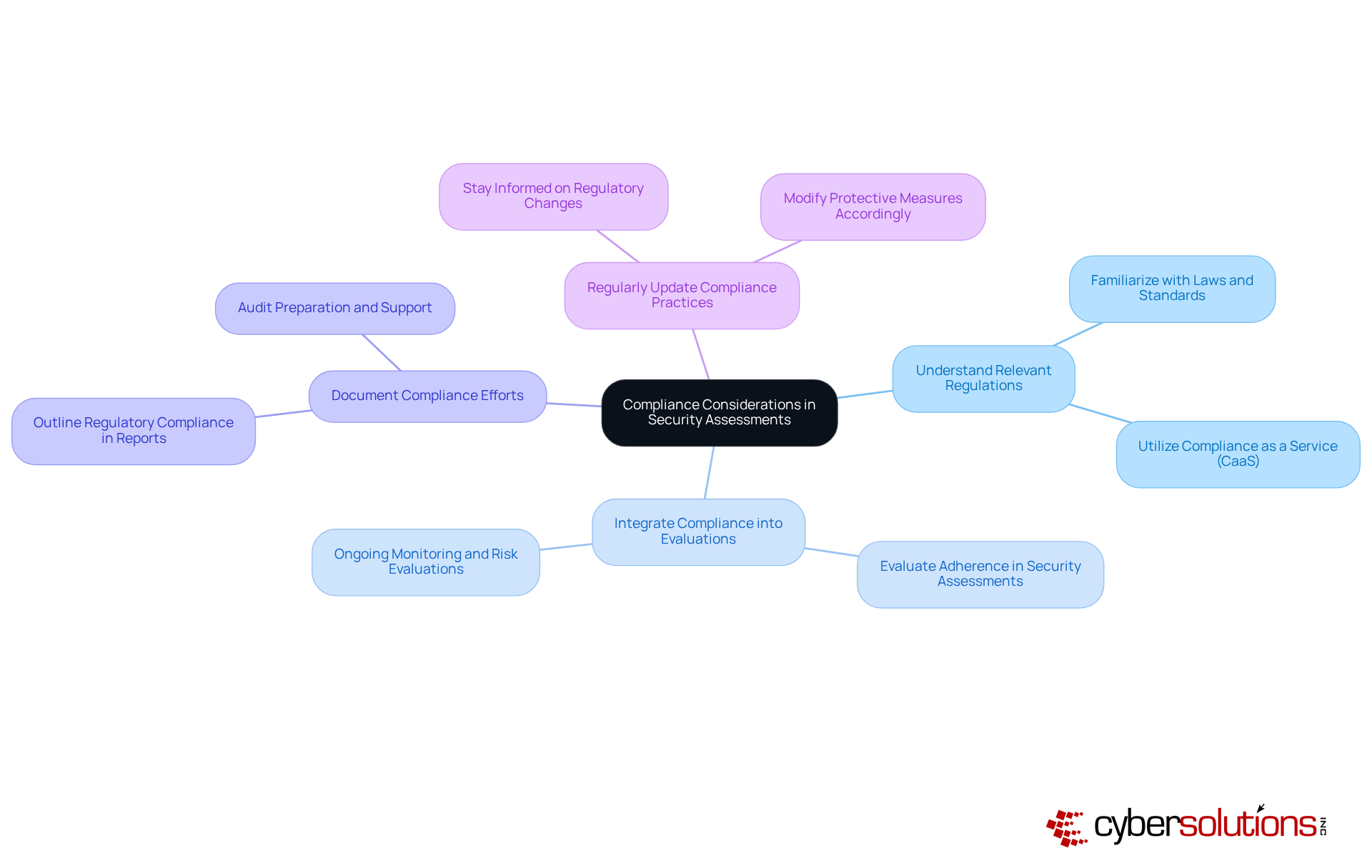
Risk evaluation is an essential component of evaluation reports. It encompasses several critical steps:
Ongoing enhancement is crucial for preserving the significance of evaluation reports in the ever-evolving landscape of cybersecurity. Regularly reviewing and updating the security assessment report is essential; schedule periodic reviews to ensure that the security assessment report reflects the current security landscape and compliance requirements.
Additionally, integrating new threat intelligence is vital. Stay informed about rising threats and modify evaluations as needed, ensuring that remediation strategies—including policy updates and system upgrades—are customized to effectively address regulatory gaps.
Engaging stakeholders throughout the review process is equally important. Involve key stakeholders to gather insights and feedback, which is essential for developing comprehensive documentation that supports adherence during audits.
Finally, documenting changes is necessary for transparency. Clearly outline any updates made to the evaluation documents, including policy updates and system upgrades, in the security assessment report to demonstrate compliance readiness.
In today's rapidly evolving cybersecurity landscape, leveraging technology is essential for enhancing the quality and efficiency of security assessment reports. By integrating advanced tools and technologies, organizations can effectively address the unique challenges they face in safeguarding sensitive information.
Automated Scanning Tools play a pivotal role by utilizing software to swiftly and accurately identify vulnerabilities. This not only expedites the evaluation process but also ensures that critical weaknesses are addressed promptly.
Data Analytics is another crucial component, enabling organizations to analyze evaluation data and uncover trends and patterns that inform strategic decision-making. This insight is invaluable for anticipating potential threats and mitigating risks.
Additionally, Collaboration Platforms facilitate seamless communication and teamwork among evaluation team members, fostering a more cohesive approach to security assessments. This collaborative effort is essential for thorough evaluations and the effective implementation of the security assessment report.
Finally, Reporting Software streamlines the generation of reports, ensuring consistency in documentation and clarity in communication. By adopting these technologies, organizations not only enhance their security posture but also build a foundation for ongoing improvement in their cybersecurity efforts.
Effective communication of the security assessment report findings is crucial for driving action in the realm of cybersecurity. To navigate the unique challenges faced by organizations, particularly in healthcare, consider the following best practices:
The significance of a well-crafted security assessment report cannot be overstated, particularly for leaders navigating the complexities of cybersecurity within their organizations. These reports serve as critical tools that not only identify vulnerabilities but also provide actionable insights tailored to meet the unique challenges faced by various industries. By prioritizing compliance and risk mitigation, leaders can make informed decisions that enhance their organization’s security posture.
Key elements of an effective security assessment report include:
Emphasizing the importance of continuous improvement, organizations are encouraged to regularly update their assessments to reflect the evolving threat landscape and compliance requirements. Moreover, leveraging technology and effective stakeholder communication further enhances the impact and clarity of these reports, ensuring that findings are not only understood but acted upon.
Ultimately, the journey toward robust cybersecurity begins with a comprehensive security assessment report. By recognizing its value and implementing best practices, organizations can foster a culture of security awareness and preparedness, safeguarding their assets and maintaining compliance in an increasingly digital world. Taking proactive steps today will lay the foundation for a more secure tomorrow, encouraging leaders to prioritize and invest in their cybersecurity strategies.
What is the primary focus of Cyber Solutions Inc.?
Cyber Solutions Inc. specializes in creating tailored security assessment reports for various industries, particularly healthcare, finance, and government, addressing their unique regulatory and operational challenges.
Why are security assessment reports important?
Security assessment reports provide a comprehensive analysis of an organization's protective stance, helping to identify vulnerabilities, assess risks, and offer actionable recommendations to mitigate potential threats, thereby guiding risk management.
What is application allowlisting, and why is it emphasized in security assessments?
Application allowlisting is a proactive strategy that allows only approved applications to operate within an organization, combating malware and unauthorized software. It is emphasized in security assessments to enhance their relevance and effectiveness.
How do security assessment reports assist in compliance with regulatory standards?
These reports help organizations ensure compliance with standards such as HIPAA, PCI-DSS, and GDPR by identifying risks and providing recommendations that align with regulatory requirements.
What are the key components of a comprehensive security assessment report?
Key components include an executive summary, scope of evaluation, methodology, findings, risk ratings, recommendations, and appendices with supporting documentation.
What does the executive summary of a security assessment report include?
The executive summary provides a high-level overview of findings and recommendations, focusing on tailored remediation strategies for compliance.
What role does Compliance as a Service (CaaS) play in security assessments?
CaaS provides organizations with access to enterprise-level compliance expertise, simplifying the compliance journey and helping to safeguard against potential penalties.
How does the report prioritize risks?
The report includes risk ratings that prioritize identified risks based on their potential impact and likelihood, facilitating informed decision-making for resource allocation.
What types of recommendations are typically included in a security assessment report?
Recommendations include actionable steps to mitigate identified risks, such as policy updates, system upgrades, and process improvements, with specific examples for practical application.
Why is rapid incident management important in the context of a security assessment report?
Rapid incident management is crucial for responding to threats like ransomware, and the report highlights the need for specialized expertise in this area to enhance the organization's protection posture.