
The article titled "10 Key Insights on Configuration vs Change Management for Leaders" underscores the critical distinctions and interconnections between configuration management and change management. These practices are not just operational necessities; they are pivotal for enhancing organizational efficiency. In today’s fast-paced business environment, effective integration of these management strategies is essential. Why? Because it minimizes risks, ensures compliance, and significantly boosts operational performance. Organizations that adopt robust management strategies are far more likely to achieve their transformation goals.
Consider this: without a solid grasp of both configuration and change management, organizations expose themselves to unnecessary risks. The implications are profound. Leaders must recognize that the seamless integration of these practices can lead to improved decision-making and streamlined processes. This is not merely a theoretical discussion; it’s a call to action for leaders who aspire to drive their organizations forward.
In conclusion, understanding the nuances of configuration and change management is not optional; it’s a necessity for any leader aiming for success in today’s complex landscape. By prioritizing these practices, organizations can position themselves to navigate challenges effectively and seize opportunities for growth.
In today's fast-paced digital landscape, effective management of configuration and change is not just important—it's essential. Organizations are confronted with the dual challenge of ensuring operational stability while navigating the complexities of an ever-evolving IT environment. This article explores ten key insights that clarify the distinctions and intersections between configuration and change management, providing leaders with a strategic roadmap to enhance their approaches.
How can organizations harness these insights to steer through the turbulent waters of transformation while ensuring security and compliance?
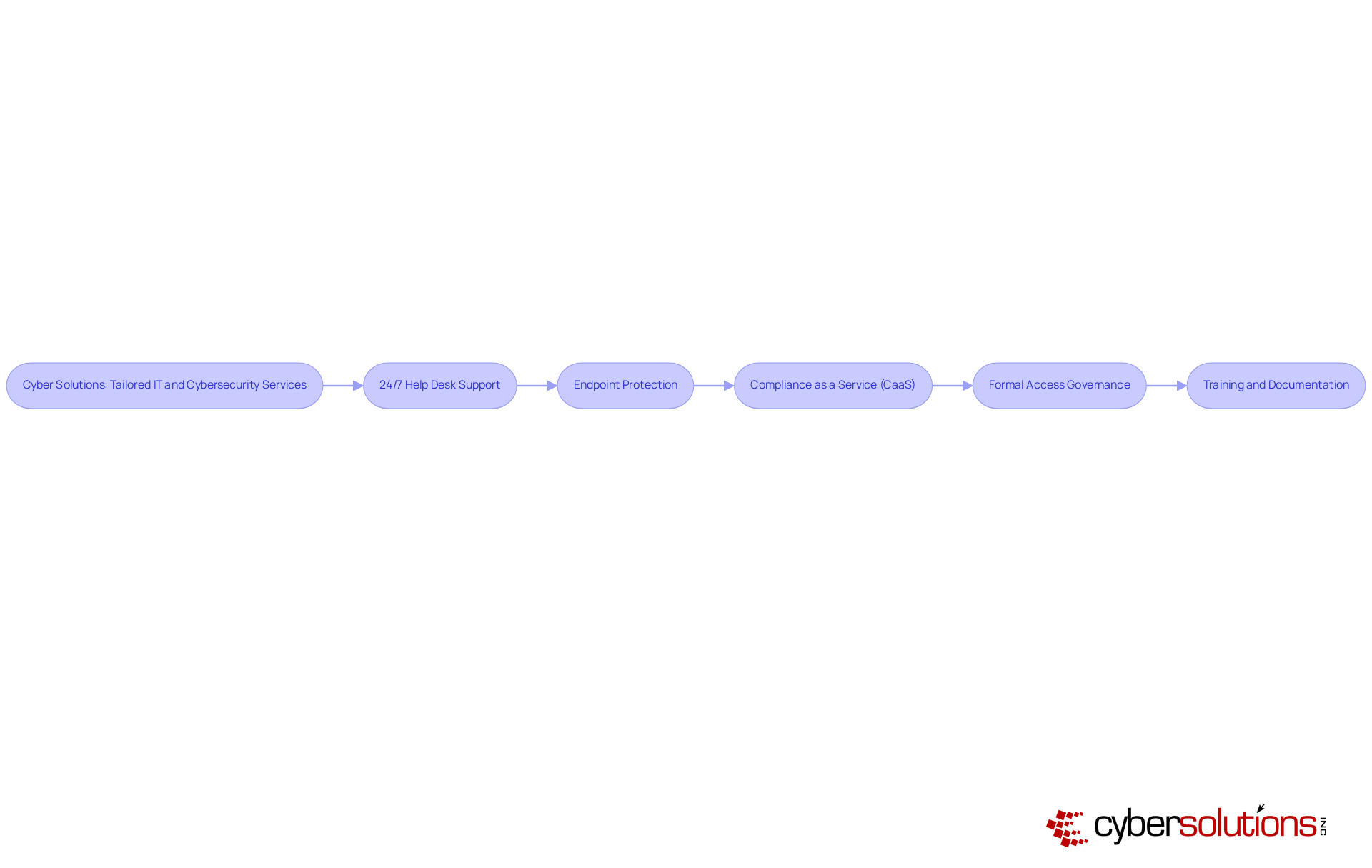
In today's digital landscape, the significance of robust cybersecurity measures cannot be overstated, especially for organizations navigating transformation. Cyber Solutions Inc. stands at the forefront, offering a comprehensive suite of managed IT and cybersecurity services that are vital for effective transformation management. With 24/7 help desk support, companies can swiftly tackle issues that arise during transitions, minimizing downtime and ensuring operational continuity.
Endpoint protection is essential, safeguarding sensitive data against emerging threats. Furthermore, Compliance as a Service (CaaS) assists organizations in navigating complex regulatory landscapes, ensuring adherence to critical standards such as HIPAA and GDPR. This proactive approach not only mitigates risks but also fosters trust among stakeholders.
Cyber Solutions tailors its offerings to meet the distinct requirements of various sectors, facilitating smooth transitions during periods of adjustment. For instance, organizations that implement formal access governance procedures experience 50% fewer access-related security incidents. This statistic underscores the importance of structured support during transformation initiatives. Additionally, integrating cybersecurity into oversight processes is crucial; a dedicated cyber oversight of transformation (MOC) process empowers entities to proactively identify and address vulnerabilities, enhancing operational safety.
Effective transformation processes in cybersecurity also hinge on thorough training and documentation. By cultivating a culture of security awareness, organizations can empower employees to recognize and report potential threats, significantly reducing the risk of incidents. As industry leaders emphasize, weaving transformation strategies into cybersecurity efforts not only improves program efficiency but also enhances accountability, resulting in a more resilient organizational structure. The financial repercussions of neglecting these practices are stark, as illustrated by the $200 million lawsuits stemming from the Target breach, highlighting the urgent need for strong governance in cybersecurity.
Moreover, Cyber Solutions' rapid incident response services play a pivotal role in minimizing the impact of cyber threats, ensuring business continuity. This layered approach to cybersecurity reinforces the necessity of comprehensive strategies in safeguarding organizational assets.
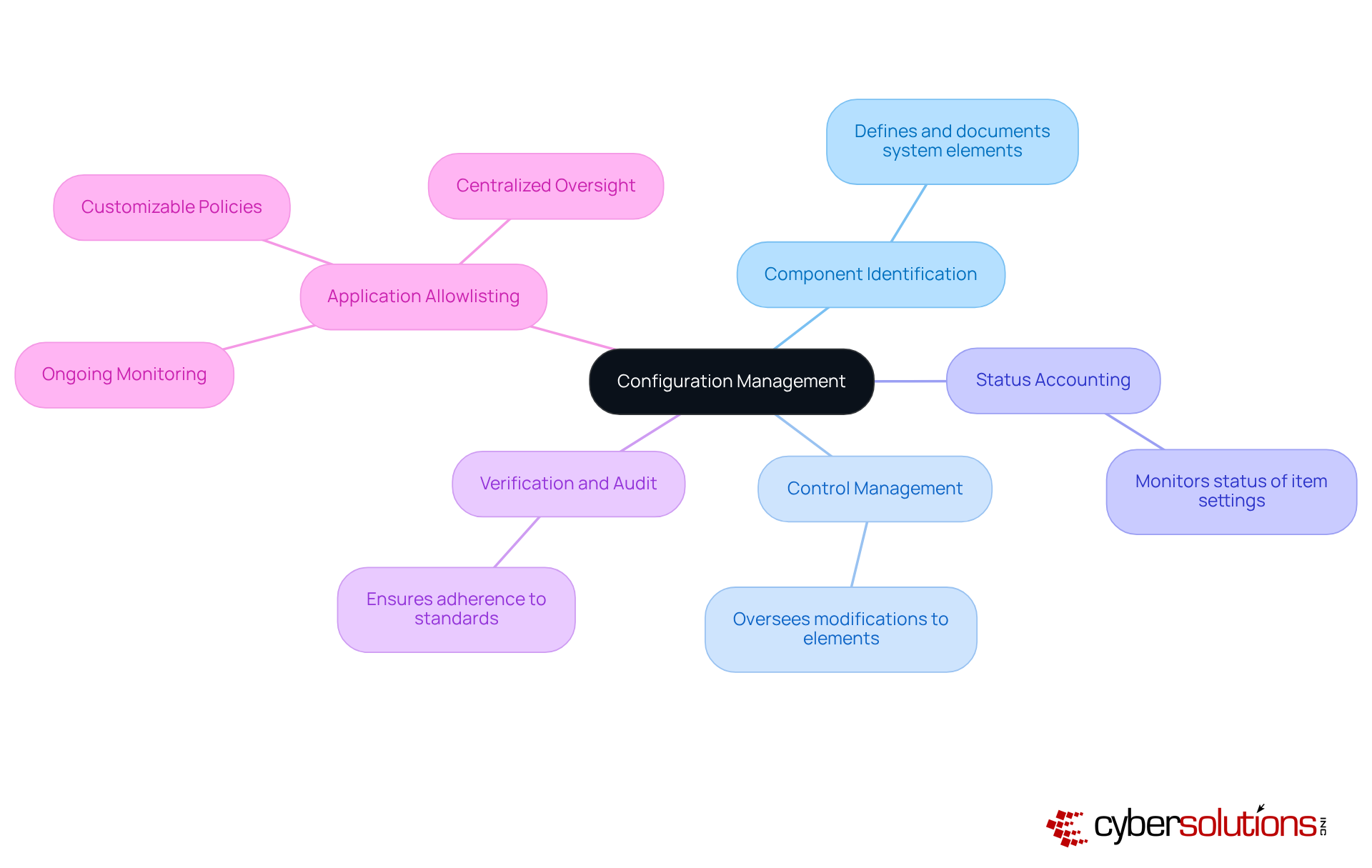
Configuration management stands as a vital pillar in ensuring the integrity and consistency of a system's performance, functional, and physical attributes throughout its lifecycle. In today’s complex IT landscape, where threats loom large, effective oversight of settings is not just beneficial—it's essential. This structured approach encompasses several critical elements:
Together, these components create a comprehensive account of system setups, enabling organizations to efficiently handle configuration vs change management and minimize operational disruptions. As IT environments grow increasingly intricate, the need for robust configuration vs change management becomes paramount, particularly in sectors like telecom and IT-enabled services, where rapid innovations demand scalable solutions.
Moreover, the rising importance of cybersecurity and compliance underscores the necessity for stringent setup oversight practices. Organizations face escalating threats and regulatory demands, making it crucial to adopt proactive measures. Application allowlisting emerges as a key strategy in this context, effectively preventing unauthorized software from executing. This not only reduces vulnerabilities but also ensures compliance with regulations such as HIPAA, PCI-DSS, and GDPR.
Key aspects of application allowlisting include:
These elements collectively enhance the efficiency of configuration control, ensuring that organizations can navigate the complexities of modern cybersecurity challenges with confidence.
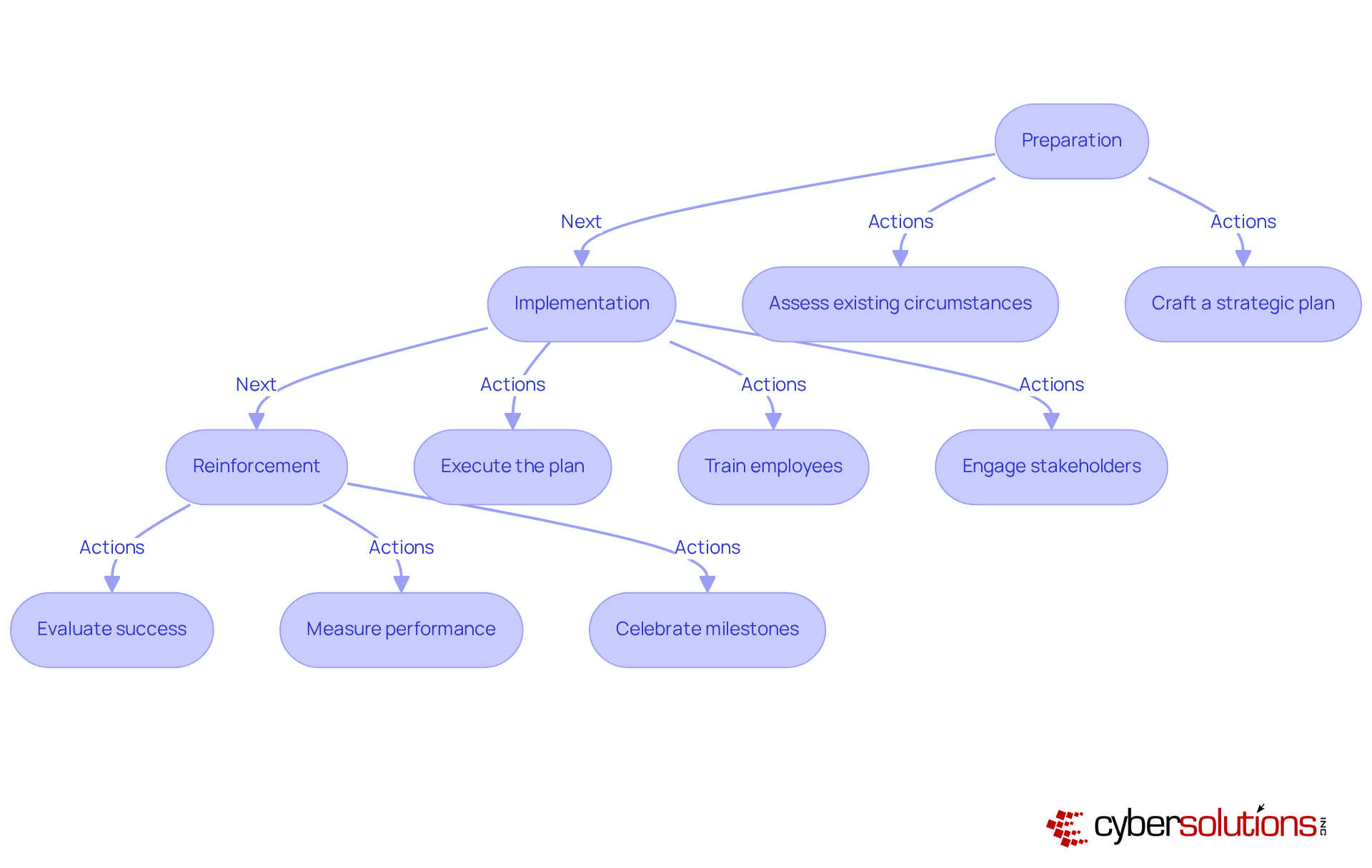
Change management is not just a process; it’s a vital strategy that organizations must embrace to navigate the complexities of today’s business landscape. By guiding individuals, teams, and processes from their current state to a desired future state, change management ensures that transformations are not only effective but also sustainable. This structured approach unfolds in three core phases: preparation, implementation, and reinforcement.
In the preparation phase, organizations assess their existing circumstances and craft a strategic plan for transformation. This initial step is crucial, as it lays the groundwork for what’s to come. Next, the implementation phase comes into play, focusing on executing the plan. This includes training employees and engaging stakeholders to foster buy-in. Have you considered how involving stakeholders early in the transformation process can establish trust and gather valuable insights? This involvement is essential for promoting smoother transitions.
Finally, the reinforcement phase evaluates the success of the modifications. It measures performance and collects feedback to ensure sustainability. Celebrating milestones during this phase not only aids in maintaining momentum but also reinforces dedication to the transformation initiative.
Efficient change oversight is critical for minimizing resistance and enhancing approval among stakeholders. Research shows that organizations with robust change management practices are significantly more likely to achieve their project goals. Today’s C-Suite leaders grapple with challenges like rapid technological advancements, cybersecurity threats, and the pressing need for workforce adaptability. Addressing these challenges demands a structured approach that aligns with organizational goals while facilitating smooth transitions.
Insights from transformation specialists reveal that an engaging vision for evolution is paramount. This vision not only motivates teams but also serves as a roadmap for success, ensuring that everyone understands the rationale behind the changes. As industry leaders emphasize, clear objectives, adequate resources, and strong leadership support are essential for navigating the complexities of transformation effectively. Moreover, leveraging technology—such as project coordination software and analytical tools—can streamline the transition process, making it more efficient and impactful.
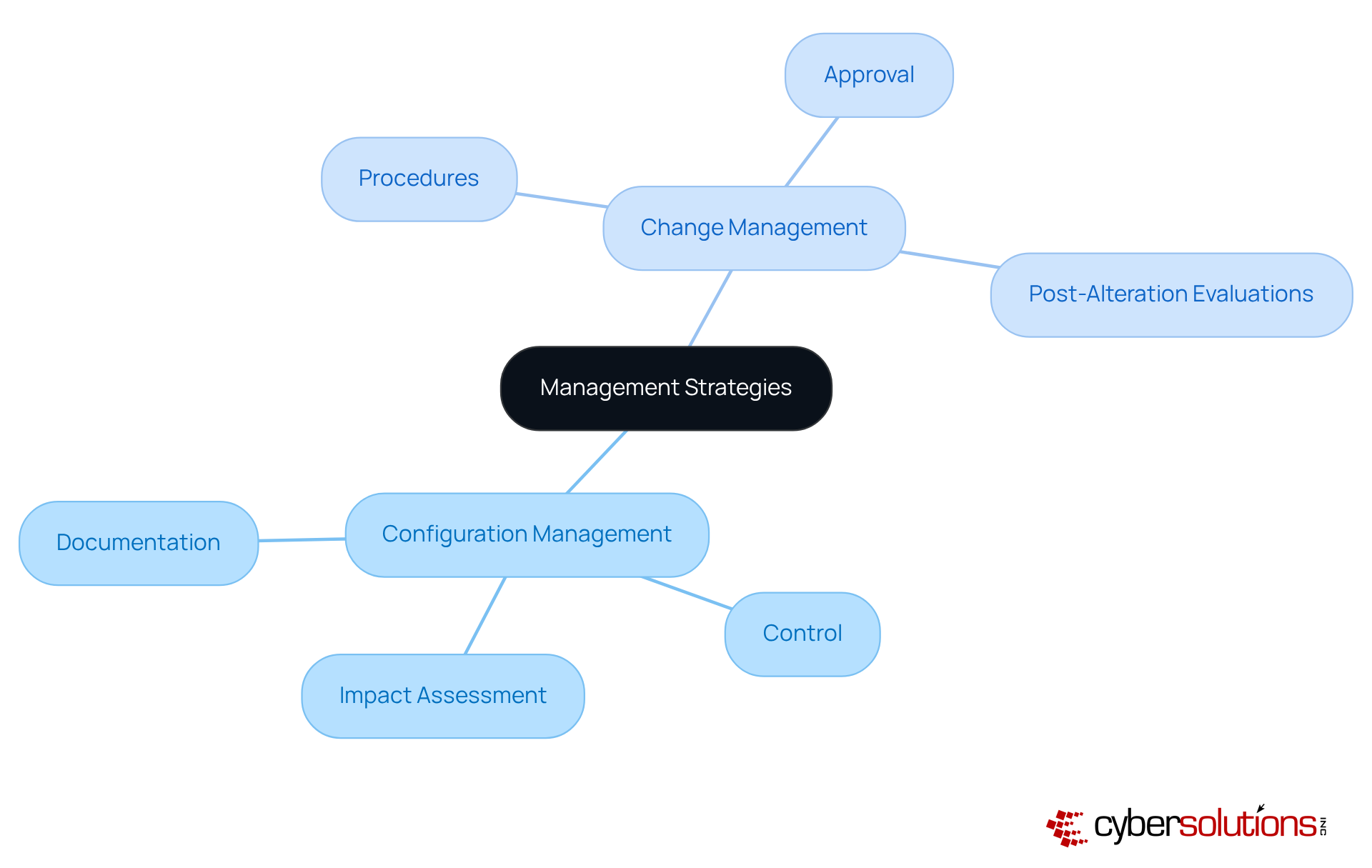
Configuration oversight plays a crucial role in maintaining the integrity of a system's configurations. It ensures that every component is meticulously documented and controlled. On the other hand, alteration oversight focuses on the organized procedures for implementing modifications, which include communication, approval, and execution. Understanding the distinctions between configuration vs change management is vital for organizations aiming to enhance their IT operations.
Consider this: efficient alteration oversight significantly reduces risks associated with system adjustments. Meanwhile, configuration oversight provides a comprehensive view of configuration items (CIs) and their interrelations, which is essential for assessing the impact of proposed changes. By integrating these two disciplines, organizations can boost their operational efficiency and maintain system stability during updates.
Current industry standards underscore the importance of aligning configuration vs change management practices. This alignment not only facilitates smoother transitions during technology updates but also ensures that all modifications are documented and approved, highlighting the importance of configuration vs change management in minimizing the risk of service disruptions.
In practice, organizations can implement unified strategies, such as utilizing a Configuration Management Database (CMDB) to track both items and modification requests. For instance, Virima's CMDB supports a reliable system for overseeing configurations by providing real-time insights into the relationships among assets and changes. This fosters collaboration among IT teams and stakeholders. By leveraging these insights, leaders can drive more effective change initiatives while maintaining robust configuration oversight processes.
As Adam Bertram aptly notes, "Change oversight is a collection of standardized methods and procedures that minimize the effect of change-related incidents within the IT organization." This structured approach is essential for ensuring that modifications are well-planned and executed.
Moreover, post-alteration evaluations are critical for documenting lessons learned and ensuring continuous improvement in both change and configuration oversight processes. By integrating these evaluations, organizations can refine their strategies and bolster their resilience against future disruptions.
Configuration and alteration oversight are not just connected processes; they are essential to preserving system integrity and operational efficiency. Effective configuration vs change management lays the groundwork by providing critical information and context for modification management. This enables organizations to accurately assess the potential impacts of proposed changes. Such integration is crucial for mitigating risks associated with modifications, ensuring that every change is thoroughly documented and managed.
Consider organizations that have successfully embraced a unified approach to these practices. For instance, Kimberly-Clark emphasizes the importance of involving business units in the transformation process. This collaboration fosters alignment between technology and business priorities, enhancing the execution of AI solutions and strengthening the overall transformation framework.
Expert insights reveal that merging configuration and alteration oversight yields significant benefits, including enhanced visibility into the IT environment and improved risk assessment capabilities. By mapping relationships among Configuration Items (CIs), organizations can anticipate the effects of changes, streamlining operations and minimizing downtime.
Current best practices advocate for a well-defined system control procedure that seamlessly integrates with configuration vs change management oversight. This approach ensures that modifications to system settings do not compromise security, safeguarding sensitive information and maintaining compliance with regulatory standards. As organizations navigate the complexities of modern IT landscapes, the synergy between configuration vs change management becomes increasingly vital for achieving operational excellence.
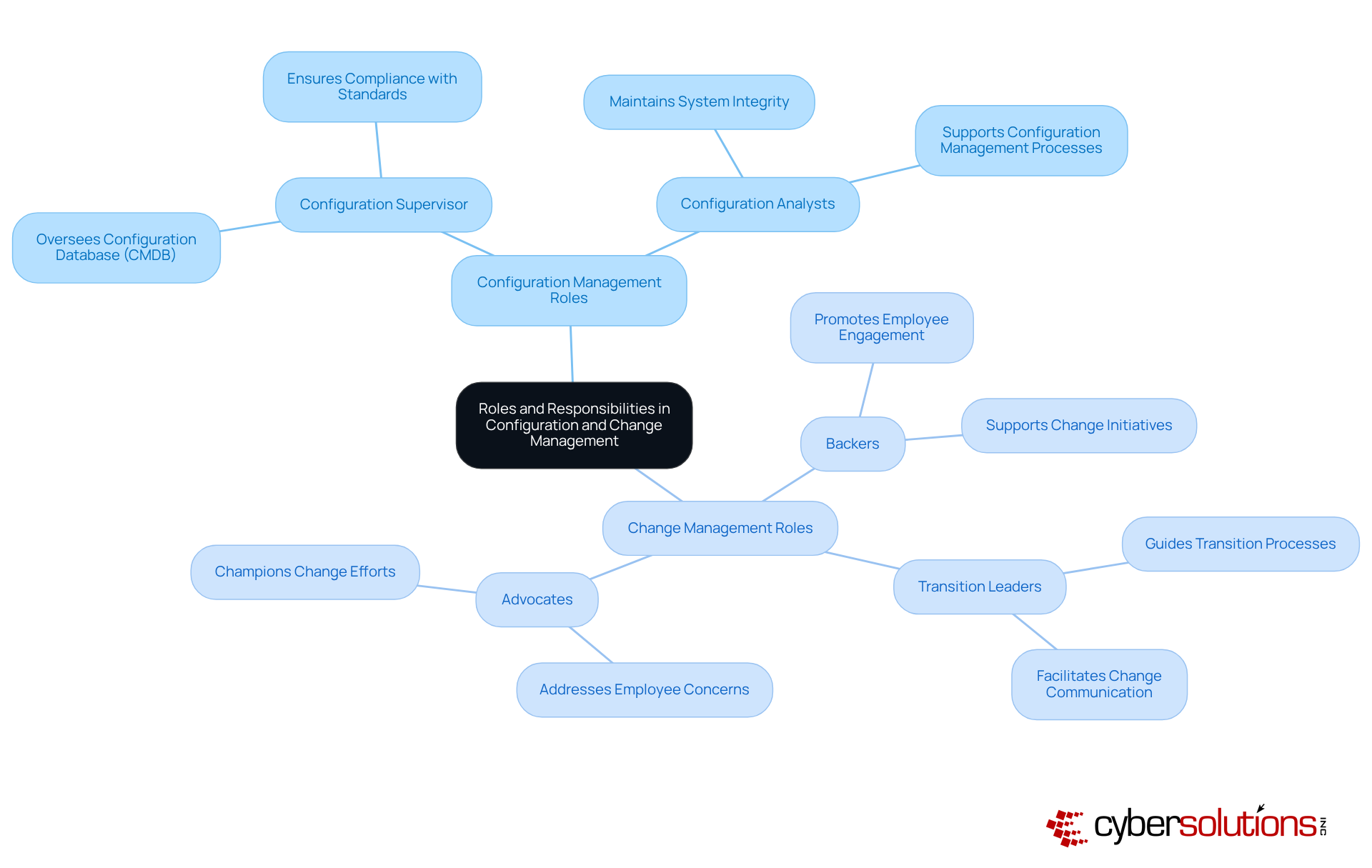
In the realm of configuration vs change management, pivotal roles such as the configuration supervisor and configuration analysts are essential. The configuration supervisor oversees the configuration database (CMDB), while configuration analysts help maintain system integrity and ensure compliance with established standards. Transition oversight also relies on vital positions like transition leaders, backers, and advocates, who facilitate and communicate modifications across the enterprise. Clearly defined roles are crucial for efficient oversight of both processes in configuration vs change management, ensuring accountability and clarity at every level.
As organizations increasingly recognize the need for systematic management of changes, the demand for qualified experts in configuration vs change management is on the rise. In fact, 73% of organizations anticipate an increase in transformation initiatives, underscoring the importance of having dedicated staff to manage these transitions effectively. Moreover, research indicates that organizations prioritizing employee participation in transformation processes see a significant boost in success rates. Such involvement not only enhances productivity but also reduces resistance to change.
However, it’s critical to acknowledge that 50% of transformation initiatives fail completely, highlighting the urgent need for effective transition practices. As we move toward 2025, focusing on clearly defined responsibilities in transition processes will be vital for steering successful transformations and achieving strategic goals. According to McKinsey, success rates can increase 3.5 times when organizations effectively communicate expected outcomes before implementing solutions, further emphasizing the necessity of organized transformation.
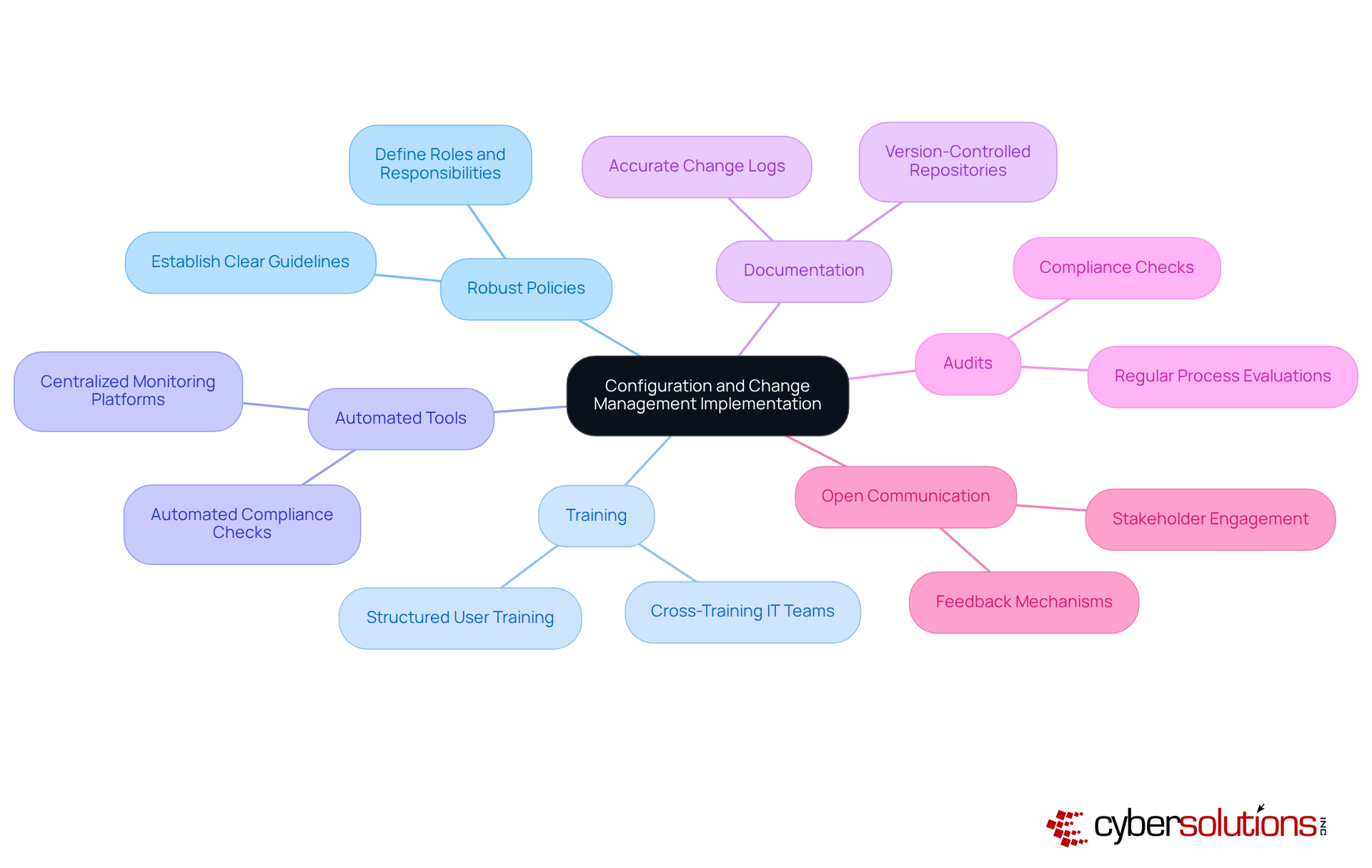
To achieve efficient setup and alteration oversight, organizations must establish robust policies and procedures that consider configuration vs change management, prioritize training for essential staff, and leverage automated tools for monitoring modifications and setups. Training is particularly vital; it equips employees with the necessary skills to navigate new systems and reduces resistance to change. Without adequate training, organizations risk significant financial losses and decreased productivity. Therefore, investing in effective training programs that emphasize practical applications is crucial, ensuring that staff can confidently utilize new technologies without disrupting workflows.
Utilizing modern tools, such as centralized setup oversight platforms, enhances visibility and control over network modifications. These tools facilitate real-time monitoring of setups, enabling swift detection of discrepancies and unauthorized changes. Accurate and up-to-date documentation is a fundamental aspect of effective adjustment and setup oversight, ensuring that all modifications are logged and easily accessible. Regular audits and evaluations of processes related to configuration vs change management are essential for identifying areas for improvement and ensuring compliance with industry standards.
Moreover, fostering a culture of open communication and collaboration among stakeholders is critical. This approach minimizes resistance to change and encourages buy-in from all levels of the organization. By implementing these practices, companies can streamline their transition processes, enhance operational efficiency, and maintain a secure and compliant network environment.
Compliance factors in setup and alteration processes are not just important; they are essential in today’s regulatory landscape. With industry regulations like HIPAA, PCI-DSS, and GDPR becoming increasingly stringent, organizations must meticulously document all modifications. This ensures that configurations align with compliance requirements, effectively mitigating risks associated with regulatory violations. For instance, organizations that have successfully navigated HIPAA compliance have established robust protocol systems, incorporating regular audits and comprehensive staff training. This proactive approach significantly reduces the likelihood of breaches and penalties.
Current trends reveal that regulatory scrutiny is intensifying, with enforcement actions on the rise across various sectors, particularly in healthcare and finance. This reality underscores the necessity for organizations to integrate compliance evaluations into their operational processes. By doing so, they not only bolster their security posture but also uphold operational integrity. Regular training sessions on regulatory updates are crucial, equipping teams with the knowledge to adapt to the ever-evolving compliance landscape.
Moreover, leveraging automated tools for configuration vs change management can streamline compliance efforts. These tools facilitate real-time monitoring and documentation of changes, ensuring adherence to regulations while fostering a culture of accountability and vigilance within the organization. As industry experts emphasize, entities that prioritize compliance as a strategic function are better positioned to thrive amidst the complexities of modern regulatory environments.

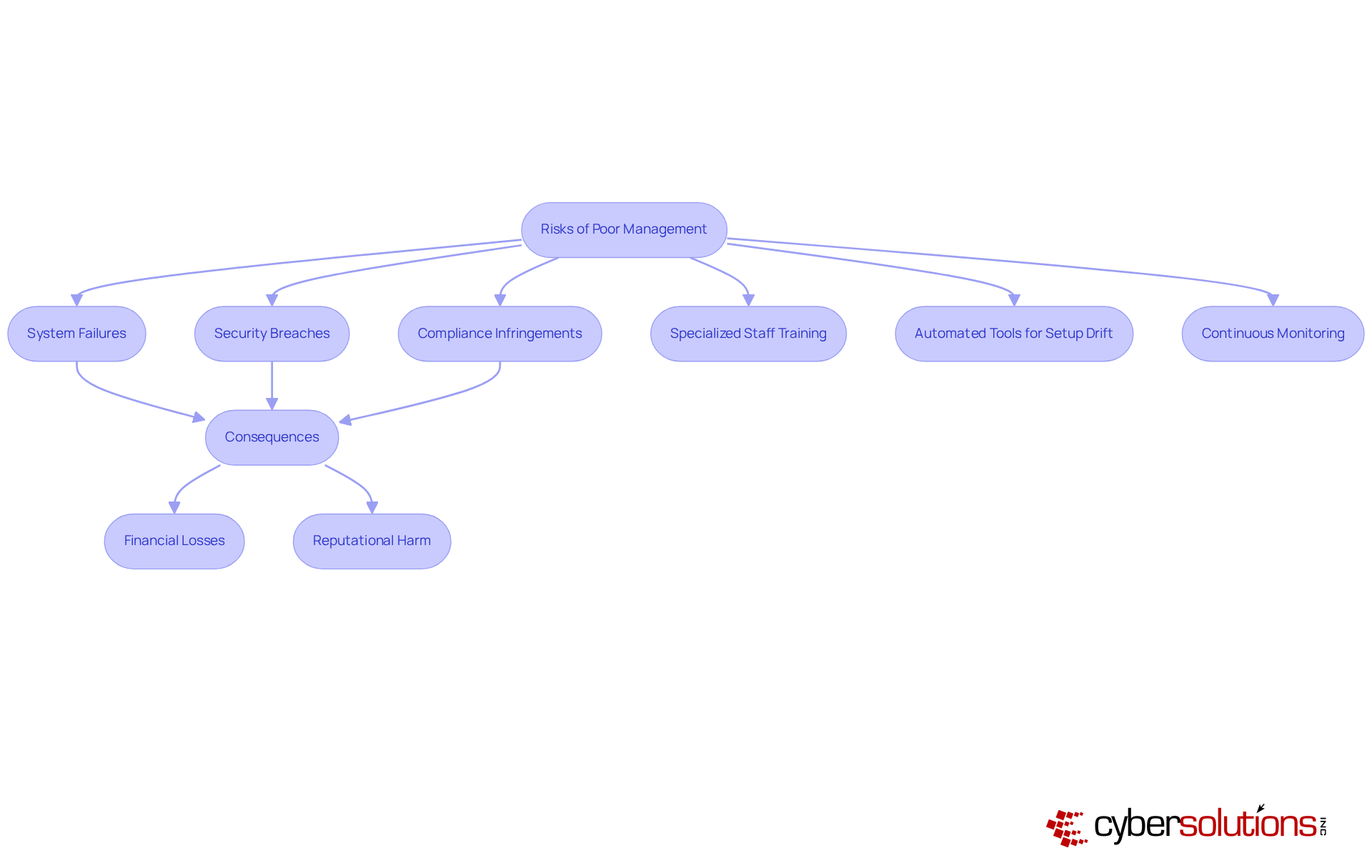
In today's digital landscape, the importance of cybersecurity cannot be overstated. Inefficient setups and oversight in configuration vs change management expose organizations to significant dangers, including system failures, security breaches, and compliance infringements. These vulnerabilities not only jeopardize operational integrity but can also lead to substantial financial losses and reputational harm. For instance, the Deepwater Horizon catastrophe, linked to insufficient configuration vs change management oversight, resulted in over $65 billion in cleanup expenses and penalties, underscoring the disastrous potential of poor administration.
Healthcare organizations face unique challenges in this arena. Misconfigurations highlight the critical importance of configuration vs change management, as they remain one of the most common and easily exploitable vulnerabilities in modern IT environments, often targeted by cybercriminals seeking easy entry points into networks. The implications are severe; entities may incur legal penalties for failing to meet regulatory standards, compounding the financial impact. How can organizations safeguard against these threats?
To combat these risks, proactive network hardening strategies are essential. Organizations must implement specialized training for staff on cyber hygiene and establish rapid incident management protocols. Automated tools can assist in identifying setup drift and highlight potential security concerns before exploitation occurs. Continuous monitoring of configurations vs change management is essential for detecting and addressing drift in real time.
By recognizing these risks and implementing strong oversight procedures, including regular compliance assessments against frameworks like CIS benchmarks, leaders can ensure their entities remain secure, compliant, and resilient against the complexities of modern IT environments. The time to act is now—protect your organization and its data from the ever-evolving landscape of cybersecurity threats.
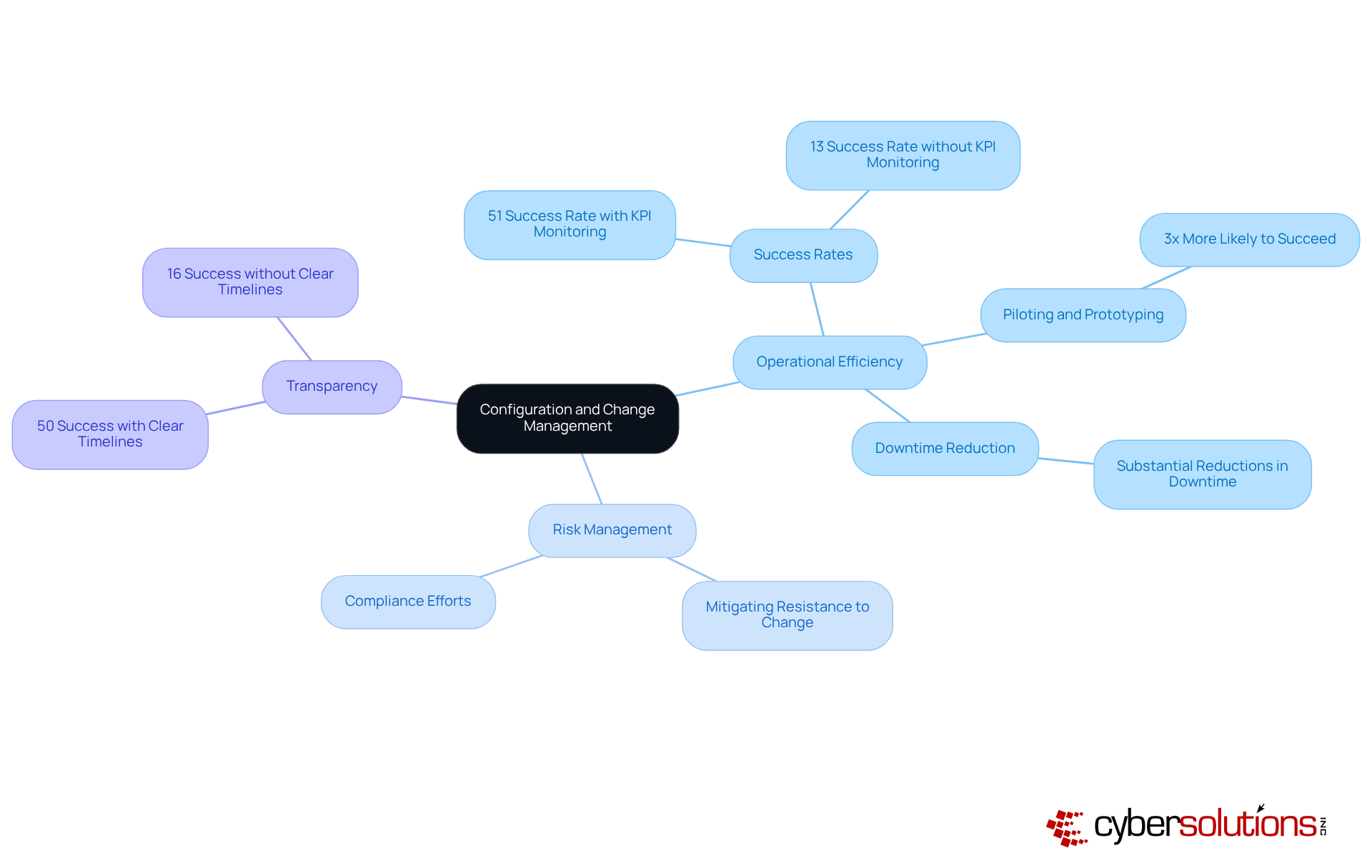
Configuration and transformation oversight are vital for enhancing operational efficiency within organizations. By ensuring that systems are precisely configured and modifications are systematically managed, businesses can significantly reduce downtime and improve service delivery. Efficient oversight processes not only streamline operations but also bolster risk management and compliance efforts, which are essential in today’s regulatory landscape. For instance, organizations that implement robust transformation strategies report a remarkable 51% success rate in achieving their goals, compared to a mere 13% for those that neglect to monitor key performance indicators (KPIs). This stark contrast underscores the necessity of monitoring and adapting processes to drive productivity.
Moreover, numerous successful examples illustrate how organizations have harnessed these management practices to boost productivity. Those that utilize piloting and prototyping in their transformation initiatives are three times more likely to succeed in their digital transformation efforts. This approach not only mitigates resistance to change but also amplifies the benefits derived from transformation initiatives.
Current data indicates that efficient organizational processes can lead to substantial reductions in operational downtime, thereby enhancing overall productivity and financial performance. IT leaders stress the importance of clearly communicating implementation timelines; a McKinsey survey revealed that 50% of respondents achieved success when timelines were transparently shared, in stark contrast to only 16% when they were not. This highlights the critical role of transparency in fostering a culture of adaptability and resilience.
In summary, integrating configuration vs change management is essential for organizations striving to enhance operational efficiency, mitigate risks, and maintain a competitive edge in the market.
Integrating configuration and change management is not just beneficial; it’s essential for organizations striving to boost operational efficiency and tackle the complexities of today’s IT environments. These two disciplines work in tandem, ensuring that systems are not only configured correctly but that changes are implemented in a controlled manner. This approach ultimately protects against potential risks and disruptions.
Key insights throughout this discussion underscore the significance of structured methodologies in both configuration and change management. By understanding the distinct roles and responsibilities involved, as well as the critical need for compliance and risk management, it becomes evident that effective oversight can greatly influence an organization’s success. Furthermore, the integration of these processes promotes collaboration and transparency, making transitions during periods of change much smoother.
Given the rapidly evolving digital landscape, organizations must prioritize robust configuration and change management strategies. Investing in training, utilizing modern tools, and cultivating a culture of open communication can significantly enhance resilience against cybersecurity threats and regulatory challenges. Ultimately, the proactive adoption of these practices not only drives operational excellence but also positions organizations to excel in an increasingly competitive market.
What services does Cyber Solutions Inc. offer for change management?
Cyber Solutions Inc. provides a comprehensive suite of managed IT and cybersecurity services, including 24/7 help desk support, endpoint protection, and Compliance as a Service (CaaS) to assist organizations during transformation.
How does Compliance as a Service (CaaS) benefit organizations?
CaaS helps organizations navigate complex regulatory landscapes, ensuring adherence to standards such as HIPAA and GDPR, which mitigates risks and fosters trust among stakeholders.
What impact does formal access governance have on security incidents?
Organizations that implement formal access governance procedures experience 50% fewer access-related security incidents, highlighting the importance of structured support during transformation initiatives.
Why is integrating cybersecurity into oversight processes important?
Integrating cybersecurity into oversight processes allows organizations to proactively identify and address vulnerabilities, enhancing operational safety during transformations.
What role does training and documentation play in cybersecurity transformation?
Thorough training and documentation cultivate a culture of security awareness, empowering employees to recognize and report potential threats, which significantly reduces the risk of incidents.
What financial repercussions can arise from neglecting cybersecurity practices?
Neglecting cybersecurity practices can lead to severe financial consequences, as exemplified by the $200 million lawsuits stemming from the Target breach.
What is configuration management, and why is it important?
Configuration management ensures the integrity and consistency of a system's performance and attributes throughout its lifecycle, which is essential for minimizing operational disruptions in complex IT environments.
What are the key components of configuration management?
The key components include component identification, control management, status accounting, and verification and audit, which together help manage system setups effectively.
How does application allowlisting enhance cybersecurity?
Application allowlisting prevents unauthorized software from executing, reducing vulnerabilities and ensuring compliance with regulations such as HIPAA, PCI-DSS, and GDPR.
What are the core phases of change management?
The core phases of change management are preparation, implementation, and reinforcement, which guide organizations from their current state to a desired future state.
Why is stakeholder involvement important in change management?
Involving stakeholders early in the transformation process helps establish trust and gather valuable insights, promoting smoother transitions.
What factors contribute to effective change management?
Effective change management relies on clear objectives, adequate resources, strong leadership support, and leveraging technology to streamline the transition process.