
The article underscores a critical step-by-step approach to mastering NIST SP 800-171 Revision 2, essential for safeguarding Controlled Unclassified Information (CUI) in non-federal systems. Understanding the framework's security requirements is paramount, as it lays the foundation for developing a robust System Security Plan (SSP). Furthermore, the implementation of necessary controls is vital, supported by strategies such as:
These elements not only ensure ongoing compliance but also significantly enhance cybersecurity resilience.
Navigating the complexities of cybersecurity compliance is imperative, particularly in the healthcare sector where the stakes are high. The stringent requirements set forth by NIST SP 800-171 Revision 2 present unique challenges for organizations handling Controlled Unclassified Information (CUI). This framework is not just a guideline; it is pivotal for ensuring the security of sensitive data. By delving into this step-by-step guide, readers will uncover essential strategies for achieving compliance, from understanding core security requirements to developing a robust System Security Plan (SSP).
However, with only a fraction of entities fully meeting these standards, the pressing question arises: how can organizations effectively bridge the gap between compliance aspirations and real-world implementation? This guide aims to address that very challenge, providing insights and actionable steps that will empower organizations to navigate the intricate landscape of cybersecurity compliance successfully.
NIST SP 800-171 Revision 2 is essential for protecting Controlled Unclassified Information (CUI) in non-federal systems, especially in the healthcare sector where the stakes are elevated. Begin by familiarizing yourself with the framework's core objectives, which encompass the confidentiality, integrity, and availability of CUI. A thorough review of the document reveals its structure, divided into 14 families of security requirements, including:
This foundational knowledge will not only direct your adherence efforts but also help you identify areas needing immediate attention.
Moreover, leveraging Compliance as a Service (CaaS) significantly enhances your regulatory strategy. CaaS offers comprehensive solutions tailored for regulated sectors, encompassing assessments, policy creation, oversight, and audit preparation. By streamlining the regulatory process, CaaS ensures your organization remains aligned with NIST SP 800-171 Revision 2 standards, providing ongoing oversight and professional advice.
In addition, implementing application allowlisting within your cybersecurity strategies can serve as a proactive defense against malware and unauthorized software. This measure strengthens your regulatory posture and protects sensitive information by ensuring that only authorized applications can operate within your systems. Embracing these strategies is essential for maintaining the integrity of your organization’s cybersecurity framework.

To attain adherence to NIST SP 800-171 Revision 2, entities must first recognize the critical criteria relevant to their operations. Start by examining the 14 groups of security criteria detailed in the standard, which together include 110 specific controls. For entities managing sensitive healthcare information, special focus should be placed on aspects concerning Access Control and Audit and Accountability. These areas are critical for safeguarding Controlled Unclassified Information (CUI) and ensuring regulatory adherence.
Developing a thorough checklist of these pertinent criteria, such as the NIST 800-171 Compliance Checklist, is vital for monitoring progress and guaranteeing that no essential areas are missed. This proactive strategy not only creates a clear plan for compliance but also improves the entity's overall protective stance. Significantly, recent data shows that only a small portion of entities completely satisfy the NIST SP 800-171 Revision 2 standards, emphasizing the necessity for companies to prioritize these controls.
Compliance experts stress the importance of the 14 categories of protective criteria, highlighting that they offer a structured framework for entities to safeguard sensitive information efficiently. By focusing on these requirements, organizations can mitigate risks associated with data breaches and enhance their resilience against cyber threats. Moreover, performing a gap analysis to evaluate current protective measures against NIST SP 800-171 Revision 2 standards is essential for pinpointing areas requiring enhancement. Cyber Solutions Inc. provides customized remediation strategies, including policy updates and system upgrades, to tackle regulatory gaps effectively. Ongoing oversight and enhancement of security protocols are also essential for upholding compliance over time, ensuring that entities are ready to react quickly to incidents, thereby boosting their cybersecurity assurance.

Developing a System Security Plan (SSP) is essential for entities aiming to comply with NIST SP 800-171 Revision 2 standards and maintain eligibility for lucrative government contracts. The time required to create a comprehensive SSP can vary significantly, spanning from several weeks to a few months, influenced by the complexity of the organization's systems and resource availability. Begin by clearly defining your system's boundaries, which encompass hardware, software, and data environments. This foundational step is crucial for understanding where Controlled Unclassified Information (CUI) is processed, stored, or transmitted.
Next, document the specific protective measures you intend to implement for each requirement outlined in NIST SP 800-171 Revision 2. This includes detailing the roles and responsibilities of team members tasked with maintaining these controls, ensuring accountability and clarity in your cybersecurity strategy. A thorough risk assessment should also be included, identifying potential threats and vulnerabilities, along with corresponding mitigation strategies.
Essential elements of a successful SSP consist of:
Organizations have effectively recorded their protective measures by employing organized templates and credible references, which not only simplify the process but also enhance trustworthiness.
As highlighted by cybersecurity advisors focusing on audit support and governance management, the effectiveness of an SSP is assessed based on its alignment with NIST SP 800-171 Revision 2 security requirements and its function in safeguarding federal data. A well-organized SSP serves not only as a regulatory document but also as a dynamic record of your cybersecurity program's integrity and maturity. It directs your regulatory efforts and acts as a reference during audits and evaluations.

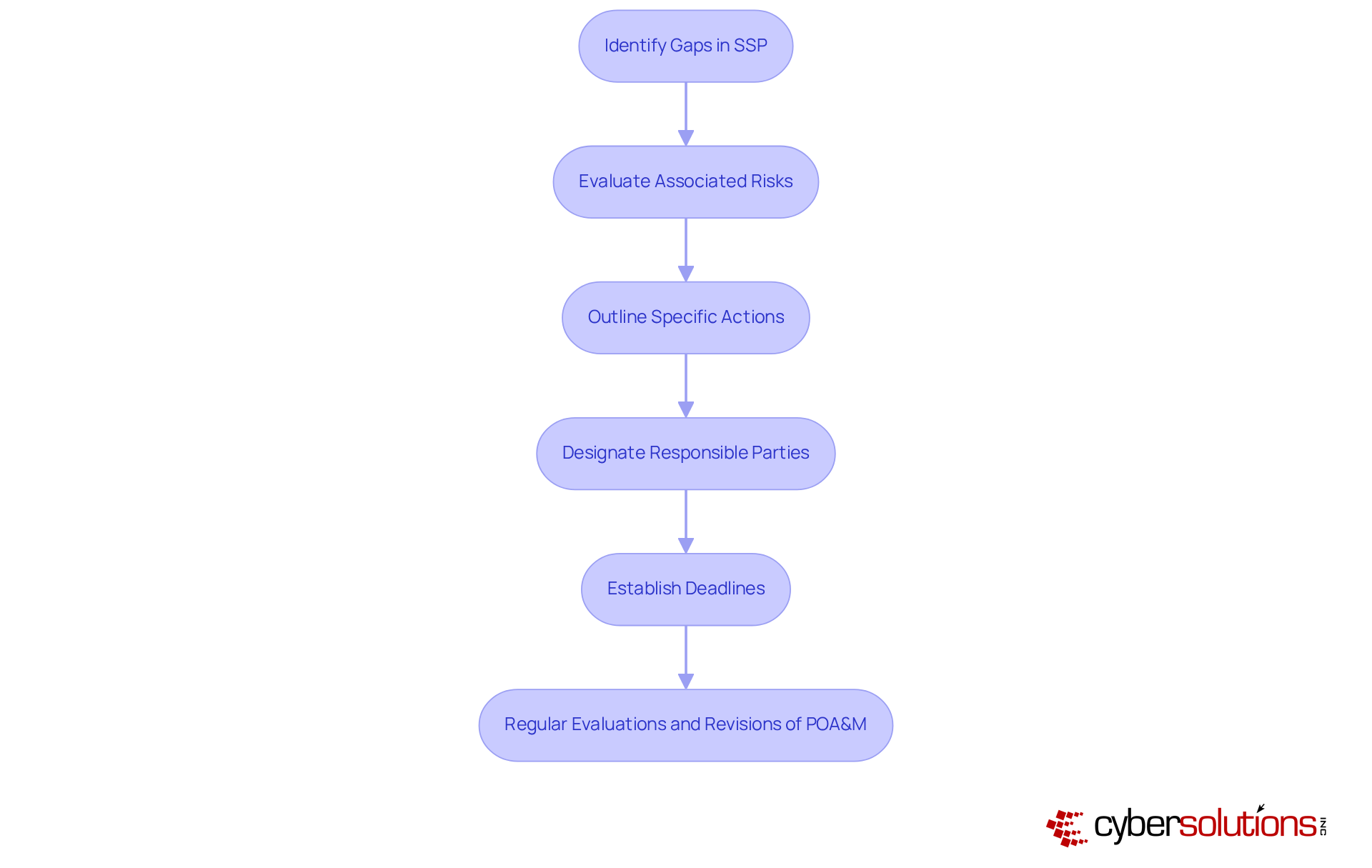
Addressing gaps in your System Security Plan (SSP) related to NIST SP 800-171 Revision 2 compliance is imperative. Developing a Plan of Action and Milestones (POA&M) is crucial in this process. Begin by listing each necessity that is not fully implemented and evaluate the associated risks for each. For every identified gap, outline specific actions to be taken, designate responsible parties, and establish deadlines. It is advisable for entities to aim for at least five milestones per POA&M to effectively track progress and ensure accountability.
Regular evaluations and revisions of the POA&M are essential to adapt to changes within your entity or alterations in regulatory standards. This proactive approach not only aids in upholding regulations but also strengthens your overall security posture. Regulatory specialists emphasize that a well-organized POA&M significantly enhances a company's ability to navigate the complexities of cybersecurity mandates, safeguarding sensitive information and ensuring operational integrity.
Entities that have successfully addressed gaps in their NIST SP 800-171 Revision 2 adherence frequently report improved security frameworks and reduced vulnerabilities. Engaging with regulatory experts can further streamline this process, ensuring your entity remains resilient against evolving threats while complying with federal standards.
With your System Security Plan (SSP) and Plan of Action and Milestones (POA&M) established, the next critical step is to implement the necessary controls and practices. Prioritize these controls based on thorough risk assessments and compliance requirements. Organizations that identify weaknesses in access controls, for instance, should prioritize implementing:
This approach not only enhances protection but also aligns with the best practices outlined in NIST SP 800-171 Revision 2.
Educating staff on these new practices is vital; they must comprehend their responsibilities in upholding security and regulations. Regular monitoring of the effectiveness of these controls is essential, allowing for timely adjustments to address emerging threats or vulnerabilities. This proactive stance is crucial for achieving adherence and safeguarding your organization against potential cyber threats.

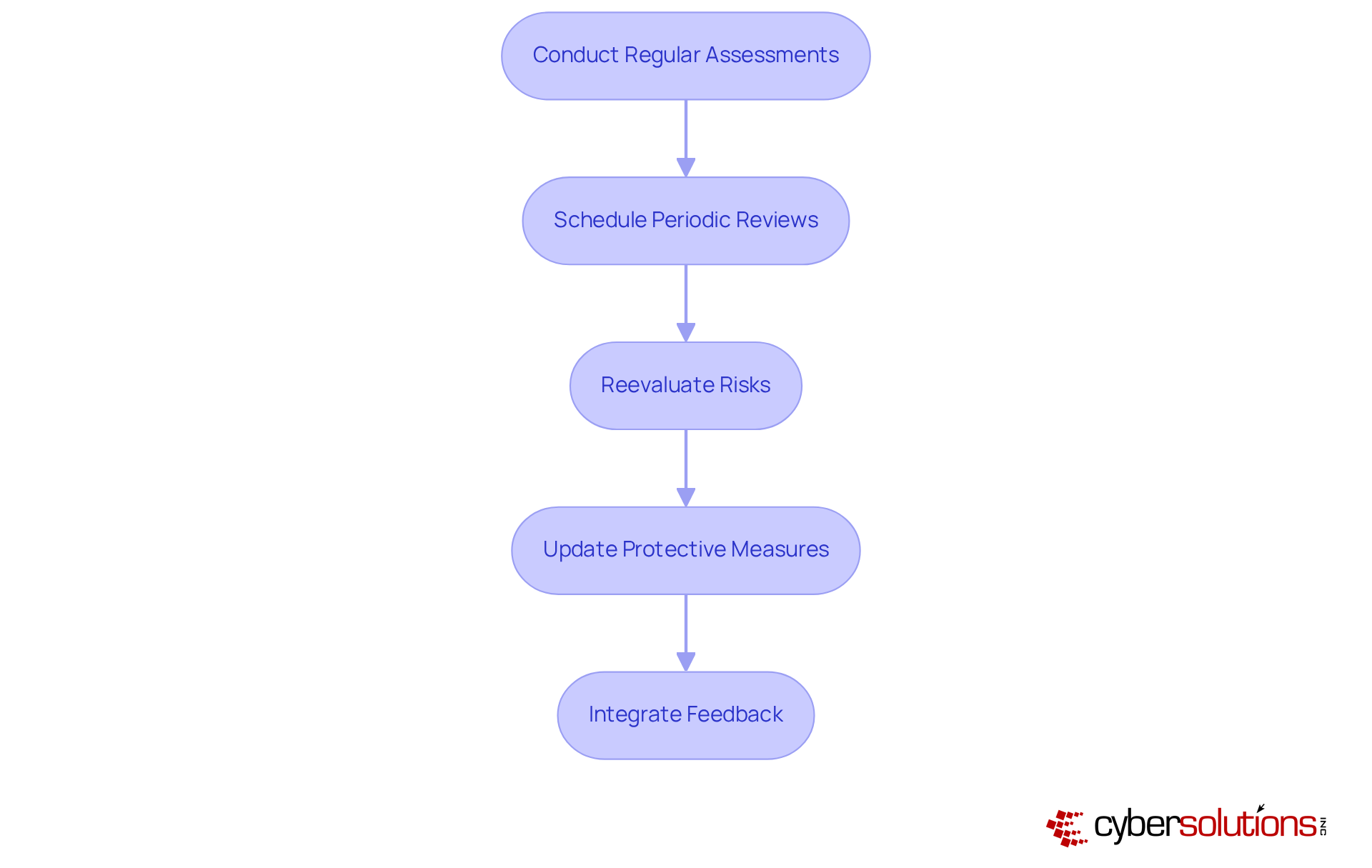
Regular evaluations and updates are essential for upholding the standards set by NIST SP 800-171 Revision 2. Organizations must prioritize scheduling periodic reviews of their System Security Plan (SSP) and Plan of Action and Milestones (POA&M) to guarantee their relevance and effectiveness in an ever-evolving cybersecurity landscape. This vital process encompasses reevaluating risks, updating protective measures, and integrating feedback from audits or incidents.
Statistics reveal that entities conducting regular updates significantly enhance their adherence stance and security efficiency. Furthermore, maintaining awareness of regulatory changes and emerging threats is crucial for adapting adherence strategies effectively. Auditors emphasize that a revised SSP and POA&M not only demonstrate a company’s commitment to cybersecurity but also serve as indispensable resources for showcasing compliance during evaluations.
For instance, organizations that have successfully revised their SSP and POA&M report improved clarity in their security protocols and a stronger alignment with operational realities. By fostering a culture of continuous improvement, your organization can adeptly navigate the evolving cybersecurity landscape and ensure sustained compliance.
Mastering NIST SP 800-171 Revision 2 is essential for organizations, particularly within the healthcare sector, to safeguard Controlled Unclassified Information (CUI). In an era where cybersecurity threats are increasingly sophisticated, understanding this framework's core objectives becomes paramount. Implementing effective strategies, such as Compliance as a Service (CaaS) and application allowlisting, can significantly enhance cybersecurity measures. By navigating the 14 families of security requirements and developing a robust System Security Plan (SSP), organizations position themselves to elevate their compliance efforts and protect sensitive data effectively.
Key insights from this guide underscore the necessity of:
Regular assessments and updates are equally vital for adapting to the evolving cybersecurity landscape. Organizations prioritizing these steps not only mitigate risks but also cultivate a proactive stance against potential threats, ensuring their cybersecurity frameworks remain resilient and effective.
Ultimately, the commitment to mastering NIST SP 800-171 Revision 2 transcends mere regulatory compliance; it embodies the pursuit of a culture rooted in continuous improvement and vigilance. Organizations are encouraged to engage with compliance experts, stay abreast of regulatory changes, and consistently refine their security protocols. By doing so, they not only safeguard sensitive information but also enhance their overall operational integrity in an increasingly complex digital world.
What is NIST SP 800-171 Revision 2 and why is it important?
NIST SP 800-171 Revision 2 is a framework designed to protect Controlled Unclassified Information (CUI) in non-federal systems, particularly critical in sectors like healthcare where the stakes are high. It focuses on ensuring the confidentiality, integrity, and availability of CUI.
How is NIST SP 800-171 Revision 2 structured?
The framework is divided into 14 families of security requirements, which include Access Control, Incident Response, and Risk Assessment, among others.
What role does Compliance as a Service (CaaS) play in adhering to NIST SP 800-171 Revision 2?
CaaS provides comprehensive solutions for regulated sectors, including assessments, policy creation, oversight, and audit preparation. It streamlines the regulatory process and ensures ongoing alignment with NIST SP 800-171 Revision 2 standards.
What is application allowlisting and how does it contribute to cybersecurity?
Application allowlisting is a cybersecurity strategy that allows only authorized applications to run within a system. This proactive measure helps defend against malware and unauthorized software, strengthening regulatory compliance and protecting sensitive information.
What are the key compliance requirements for NIST SP 800-171 Revision 2?
Key compliance requirements include recognizing the 14 groups of security criteria that encompass 110 specific controls. Special attention should be given to Access Control and Audit and Accountability, especially for entities managing sensitive healthcare information.
Why is it important to develop a checklist for NIST SP 800-171 compliance?
Developing a checklist, such as the NIST 800-171 Compliance Checklist, helps monitor progress and ensures that no critical areas are overlooked. It creates a clear compliance plan and enhances the organization's overall protective measures.
What is a gap analysis in the context of NIST SP 800-171 Revision 2?
A gap analysis evaluates current protective measures against the standards of NIST SP 800-171 Revision 2 to identify areas needing improvement. This assessment is essential for enhancing compliance and addressing regulatory gaps.
How can organizations maintain compliance with NIST SP 800-171 Revision 2 over time?
Organizations can maintain compliance by implementing ongoing oversight and enhancement of security protocols, ensuring they are prepared to respond quickly to incidents and improve their cybersecurity assurance.