
In today's digital landscape, partnering with a cybersecurity compliance company is not just beneficial—it's essential. Organizations face an ever-evolving array of cyber threats, making it crucial to enhance their security posture and ensure compliance with regulatory standards. This partnership not only fortifies business resilience against potential breaches but also cultivates a proactive security culture within the organization.
Such collaborations bring expert knowledge and tailored solutions to the table. By implementing strategies like application allowlisting, organizations can significantly minimize vulnerabilities. This proactive approach reduces the risk of costly breaches and fosters a culture of security awareness among employees.
Consider the implications: without these partnerships, organizations may find themselves ill-equipped to handle the complexities of cybersecurity. The stakes are high, and the cost of inaction can be devastating. By engaging with a cybersecurity compliance company, organizations can navigate these challenges effectively, ensuring they remain ahead of potential threats.
Ultimately, the right partnership can transform an organization's approach to cybersecurity, making it not just a compliance issue but a cornerstone of business strategy. Are you ready to take the necessary steps to safeguard your organization?
In an age where cyber threats loom larger than ever, the significance of cybersecurity compliance cannot be underestimated. Businesses that prioritize compliance not only safeguard sensitive data but also enhance their resilience against potential breaches. As regulatory landscapes become increasingly complex, organizations face pressing challenges: how can they effectively navigate these hurdles and ensure robust security measures?
Partnering with a cybersecurity compliance company offers a strategic solution. This collaboration provides expert guidance and tailored strategies that empower businesses to not only meet compliance standards but also thrive in a competitive environment. By embracing this partnership, organizations can transform compliance from a mere obligation into a powerful asset that fortifies their defenses and positions them for success.
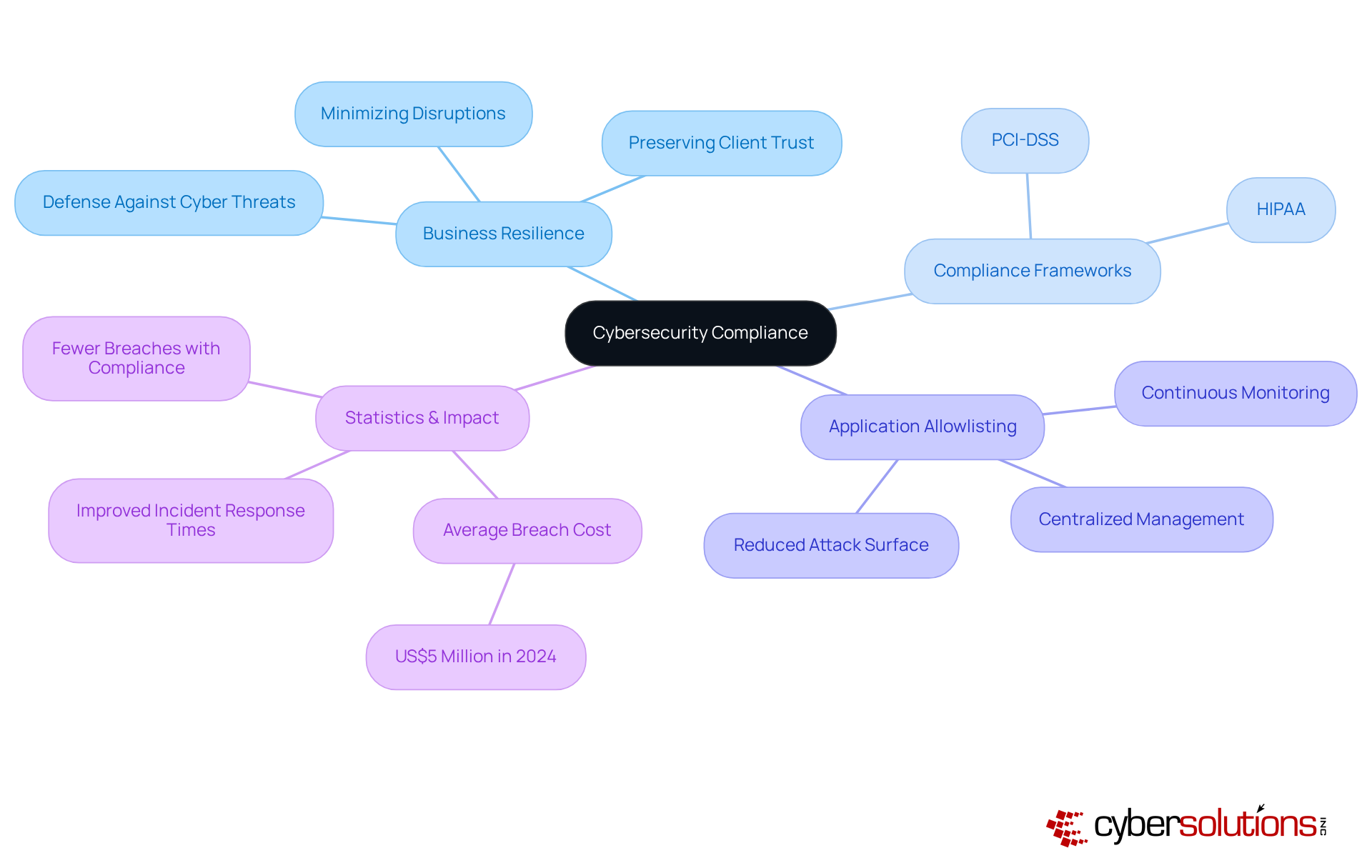
A cybersecurity compliance company emphasizes that compliance is not just a regulatory checkbox; it’s a cornerstone of business resilience, serving as a formidable defense against the rising tide of cyber threats. Organizations that prioritize adherence to industry regulations often partner with a cybersecurity compliance company to safeguard sensitive data and significantly enhance their overall security posture. Compliance frameworks, such as HIPAA for healthcare and PCI-DSS for payment processing, set the standards that enable entities to pinpoint vulnerabilities and implement necessary controls effectively. By aligning with these regulations, businesses bolster their readiness to tackle potential incidents, minimizing disruptions and preserving trust with clients and stakeholders.
A critical aspect of this compliance is application allowlisting, regarded as the gold standard in cybersecurity. This proactive strategy blocks unauthorized or malicious software from executing, drastically reducing the attack surface and minimizing vulnerabilities. By ensuring that only approved applications can run, organizations can effectively thwart malware, ransomware, and zero-day attacks before they inflict damage. Features like centralized management and continuous monitoring further enhance the effectiveness of application allowlisting, allowing entities to manage and update allowlists seamlessly across all devices.
Moreover, fostering adherence cultivates a culture of security awareness within organizations, empowering employees to proactively identify and mitigate risks. Companies that have integrated regulatory frameworks into their operations often collaborate with a cybersecurity compliance company, resulting in improved incident response times and reduced breach impacts. Statistics indicate that entities with robust compliance measures experience fewer breaches, with the average cost of a breach significantly lower than that of their non-compliant counterparts. In fact, the average global data breach cost reached an unprecedented US$5 million in 2024, highlighting the financial ramifications of non-compliance. This proactive approach not only safeguards assets but also positions firms as trustworthy partners in an increasingly regulated landscape, ultimately enhancing operational efficiency and client trust. As Allianz Commercial notes, 'cyber incidents rank as the top global risk in the Allianz Risk Barometer,' underscoring the urgent need for effective regulatory strategies.
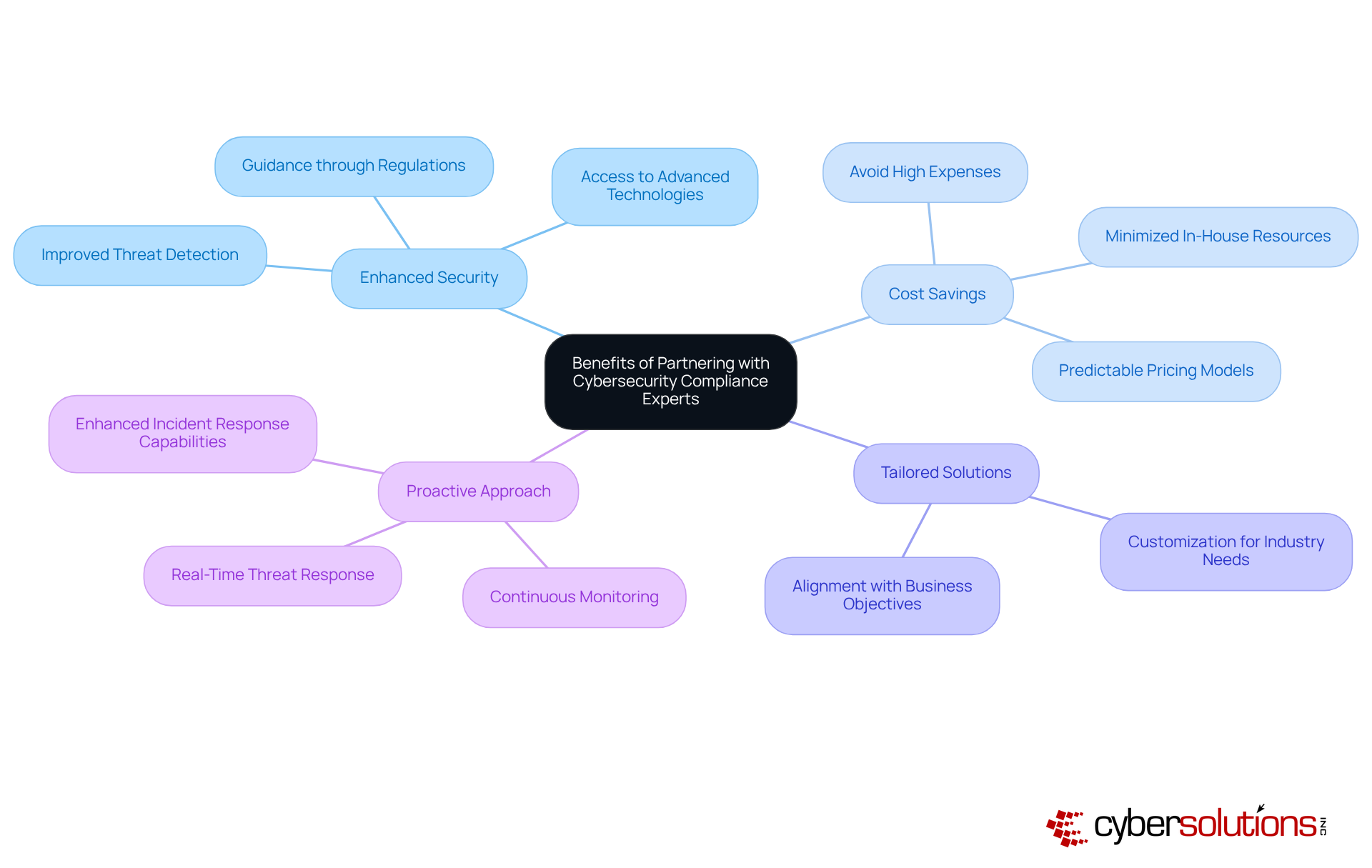
In today's digital landscape, the importance of cybersecurity cannot be overstated. Collaborating with a cybersecurity compliance company is essential for businesses aiming to enhance their security structure. These experts bring invaluable knowledge and experience, guiding organizations through the complex regulatory landscapes that govern their industries. By partnering with these specialists from a cybersecurity compliance company, companies not only gain access to advanced technologies but also adopt optimal practices, ensuring their compliance efforts are both effective and efficient.
Moreover, such partnerships can lead to significant cost savings. By minimizing the need for extensive in-house resources and training, businesses can avoid the high expenses associated with creating a dedicated regulatory team. Instead, they can leverage the expertise of external partners who are already well-versed in the latest regulatory requirements. This approach simplifies regulatory processes and allows companies to allocate resources more strategically.
As a cybersecurity compliance company, cybersecurity specialists also provide tailored solutions that align with specific industry needs. This customization enables organizations to achieve regulatory compliance while maintaining focus on their core business objectives. By ensuring that compliance measures are relevant and practical, businesses can effectively address the unique challenges faced by their sectors.
Ultimately, these collaborations foster a proactive approach to cybersecurity, empowering businesses to stay ahead of emerging threats. By integrating expert insights and resources, organizations can bolster their overall security posture, mitigate risks, and cultivate a reputation for reliability and transparency in an increasingly competitive environment.
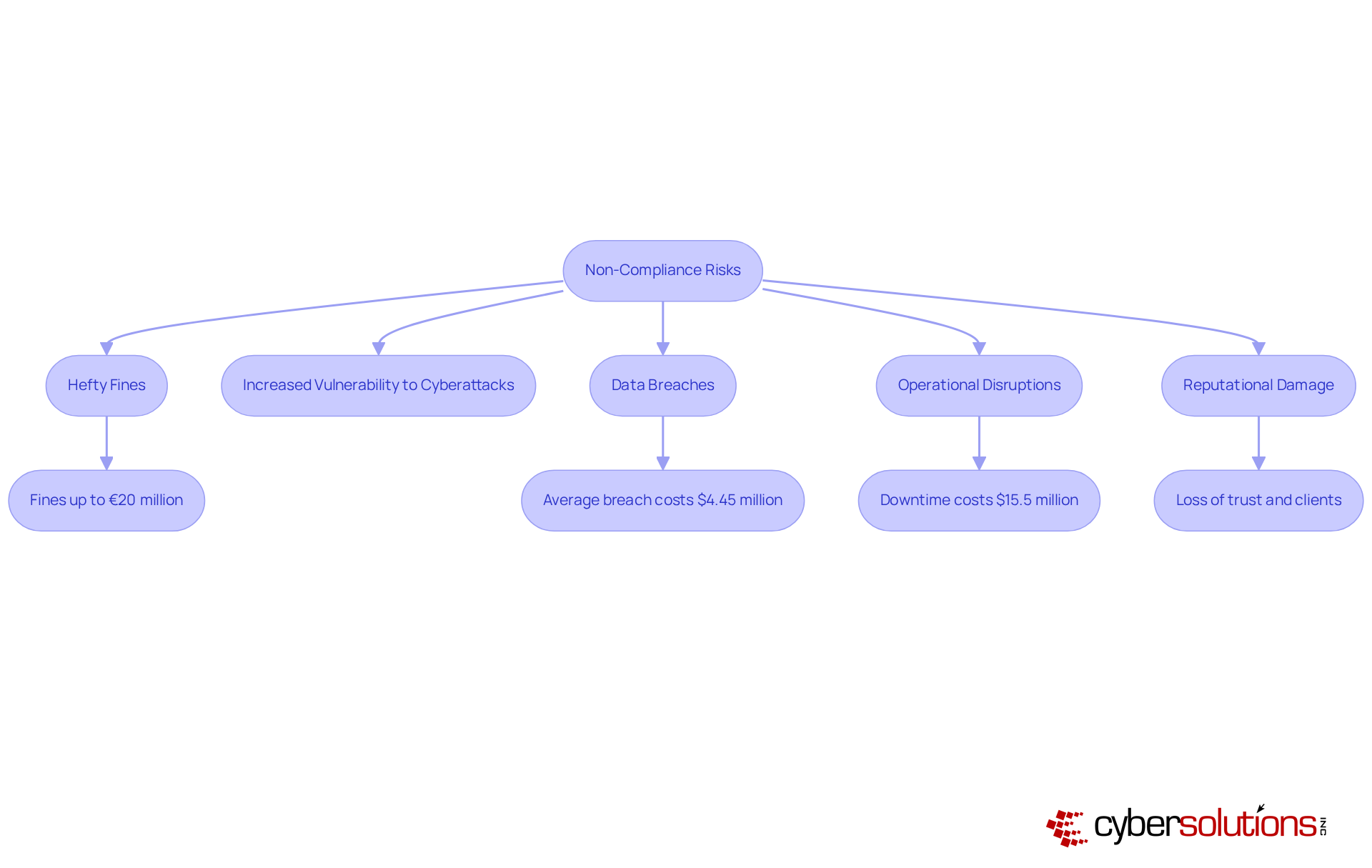
Non-compliance with cybersecurity regulations poses serious risks that can jeopardize the operational integrity and financial health of a cybersecurity compliance company. The stakes are high: failing to meet established standards can lead to hefty fines, with the average penalty for insufficient legal justification for processing soaring to EUR 2.7 million in 2024. Legal repercussions can escalate rapidly; for example, violations of GDPR can result in fines of up to €20 million or 4% of annual global turnover. Such financial burdens can significantly strain cash flow and profitability.
Moreover, non-compliance heightens vulnerability to cyberattacks, as organizations may lack essential protections like application allowlisting to shield sensitive data, which can be mitigated by a cybersecurity compliance company. Application allowlisting not only blocks unauthorized software execution but also incorporates features such as continuous monitoring and centralized management, which are vital for risk mitigation. This lack of safeguards can lead to data breaches, which, according to IBM's 2023 report, cost an average of $4.45 million. The potential for lawsuits from affected parties further complicates recovery efforts. Additionally, the operational disruptions caused by security incidents can result in substantial downtime, with healthcare entities projected to incur costs of $15.5 million in 2023 alone.
The ramifications of non-compliance extend beyond immediate financial consequences; they can also inflict enduring reputational damage. Take Meta, for instance, which faced a staggering fine exceeding €1.2 billion in 2023 for inadequate data protection measures. Such breaches can erode customer trust and lead to significant business losses. Therefore, recognizing the risks associated with non-compliance is essential for organizations striving to maintain their competitive edge and achieve sustainable success, which is why partnering with a cybersecurity compliance company is crucial in an increasingly regulated environment. Implementing proactive measures, such as application allowlisting and robust incident response strategies, is crucial for safeguarding against these risks.
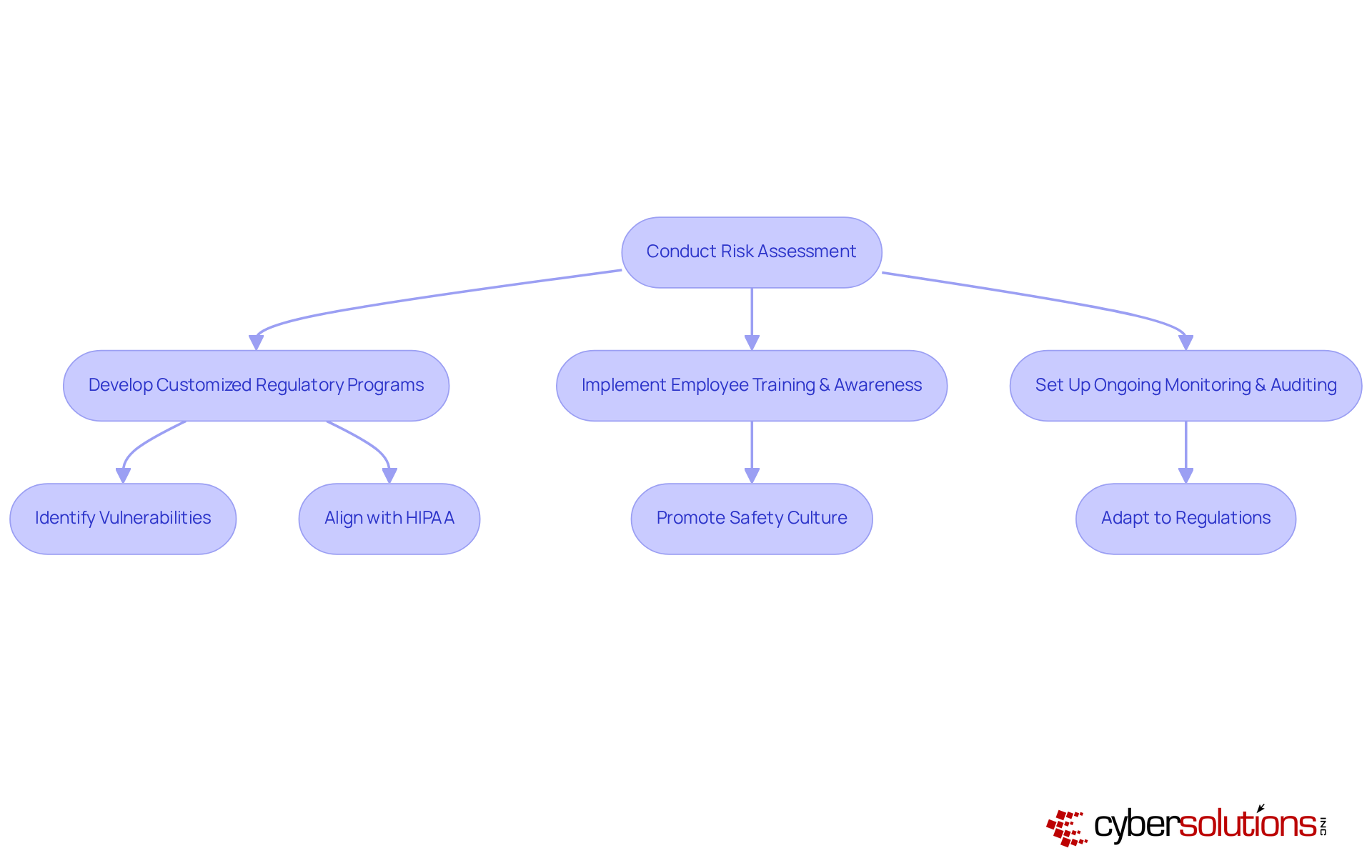
In today’s healthcare landscape, the importance of robust cybersecurity cannot be overstated. With increasing regulatory demands and the constant threat of cyberattacks, organizations must prioritize partnerships with cybersecurity experts who can adeptly navigate the complexities of compliance. A foundational step in this collaboration is conducting a thorough risk assessment, which identifies vulnerabilities and gaps in existing security measures. This evaluation is crucial, as it enables entities to concentrate on critical risks that could disrupt operations or lead to substantial financial penalties due to non-compliance.
Cybersecurity experts play a vital role in developing customized regulatory programs that align with industry standards, ensuring that all necessary controls are in place. For instance, healthcare entities must comply with HIPAA guidelines, which mandate strict information protection measures. Additionally, understanding the various tiers of CMMC adherence is essential for organizations managing federal data, as each tier requires specific protective measures to safeguard sensitive information.
Consistent training and awareness initiatives for employees are essential. They promote a culture of safety and ensure that staff are prepared to identify and address potential threats. Moreover, integrating incident response services into regulatory strategies is crucial for promptly addressing any breaches and preserving operational integrity.
Setting up ongoing monitoring and auditing procedures is also essential for upholding standards and adapting to changing regulations. This proactive strategy not only assists entities in remaining compliant but also enhances their overall security posture. By leveraging expert knowledge and resources, including our Compliance as a Service (CaaS) offerings, businesses can develop a robust strategy that meets regulatory obligations while protecting sensitive data. Furthermore, involving leadership early in the compliance process and regularly reviewing policies and procedures will further strengthen the organization’s compliance framework.
Partnering with a cybersecurity compliance company isn’t just a strategic choice; it’s a vital investment in the resilience and security of any organization. In today’s digital landscape, compliance transcends mere regulatory obligation; it forms a critical foundation that strengthens businesses against rising threats. By aligning with established compliance frameworks, organizations can effectively pinpoint vulnerabilities, implement robust controls, and enhance their overall security posture. This proactive approach safeguards sensitive data and maintains trust with clients and stakeholders.
Key insights throughout this discussion reveal the multifaceted benefits of such partnerships. For instance, the implementation of application allowlisting stands out as a gold standard in cybersecurity, significantly reducing the attack surface and mitigating risks tied to unauthorized software. Collaborating with cybersecurity experts not only streamlines compliance efforts but also leads to substantial cost savings and tailored strategies that meet specific industry needs. Evidence shows that organizations with strong compliance measures experience fewer breaches and lower financial impacts, reinforcing the necessity of proactive cybersecurity strategies.
The significance of cybersecurity compliance cannot be overstated. Organizations must grasp the severe risks posed by non-compliance, which can include hefty fines, operational disruptions, and reputational damage. By embracing expert partnerships, businesses can foster a culture of security awareness, implement effective compliance strategies, and position themselves as trustworthy entities in an increasingly regulated environment. Taking action now to prioritize cybersecurity compliance will not only protect assets but also pave the way for sustainable success in the future.
What is the role of cybersecurity compliance in business resilience?
Cybersecurity compliance is a cornerstone of business resilience, serving as a defense against cyber threats. It helps organizations safeguard sensitive data and enhance their overall security posture by adhering to industry regulations.
What are some examples of compliance frameworks?
Examples of compliance frameworks include HIPAA for healthcare and PCI-DSS for payment processing. These frameworks set standards that help organizations identify vulnerabilities and implement necessary controls.
What is application allowlisting and why is it important?
Application allowlisting is a proactive cybersecurity strategy that blocks unauthorized or malicious software from executing. It is important because it drastically reduces the attack surface and minimizes vulnerabilities, helping to thwart malware, ransomware, and zero-day attacks.
How does application allowlisting enhance security?
Application allowlisting enhances security through features like centralized management and continuous monitoring, allowing organizations to manage and update allowlists seamlessly across all devices.
How does fostering compliance impact organizational culture?
Fostering compliance cultivates a culture of security awareness within organizations, empowering employees to proactively identify and mitigate risks.
What are the benefits of integrating regulatory frameworks into operations?
Integrating regulatory frameworks improves incident response times and reduces the impact of breaches. Organizations with robust compliance measures experience fewer breaches and lower average costs associated with breaches.
What are the financial implications of non-compliance?
The average global cost of a data breach reached US$5 million in 2024, highlighting the financial ramifications of non-compliance.
Why is cybersecurity considered a top global risk?
Cyber incidents rank as the top global risk according to the Allianz Risk Barometer, underscoring the urgent need for effective regulatory strategies in cybersecurity.