
In today's rapidly evolving digital landscape, the significance of cybersecurity in healthcare cannot be overstated. Healthcare CFOs must master critical security controls to protect sensitive patient data and ensure compliance with regulations. The unique challenges faced by these executives demand a proactive approach to implementing essential cybersecurity measures. This includes:
Both of which are crucial for mitigating risks associated with data breaches. Such breaches can lead to severe financial and reputational consequences for healthcare organizations, making it imperative for CFOs to act decisively.
The current landscape of cybersecurity threats is alarming. With increasing incidents of data breaches, healthcare organizations are at heightened risk. The implications of these threats are profound, impacting not only financial stability but also patient trust. Therefore, it is essential for CFOs to prioritize cybersecurity as a fundamental aspect of their operational strategy. By adopting robust cybersecurity measures, healthcare organizations can protect themselves against potential breaches and the fallout that follows.
To effectively address these challenges, Cyber Solutions offers a comprehensive suite of services designed to enhance security protocols within healthcare organizations. By focusing on critical areas such as:
CFOs can significantly reduce their vulnerability to cyber threats. The time for action is now; healthcare CFOs must take the lead in safeguarding their organizations against the ever-present dangers of cyberattacks.
In the high-stakes world of healthcare, where sensitive patient information is perpetually at risk, cybersecurity has ascended to a paramount priority—no longer a mere option. This article explores the critical security controls that healthcare CFOs must master to protect their organizations from escalating cyber threats and compliance challenges.
As the landscape of digital security evolves, a pressing question emerges: how can CFOs adeptly navigate the complexities of implementing robust security measures while ensuring financial viability and regulatory adherence? The urgency of this matter cannot be overstated; the consequences of inadequate cybersecurity can be catastrophic, not only for patient safety but also for the financial integrity of healthcare institutions.
Understanding these dynamics is essential for CFOs aiming to fortify their organizations against the relentless tide of cyber threats.
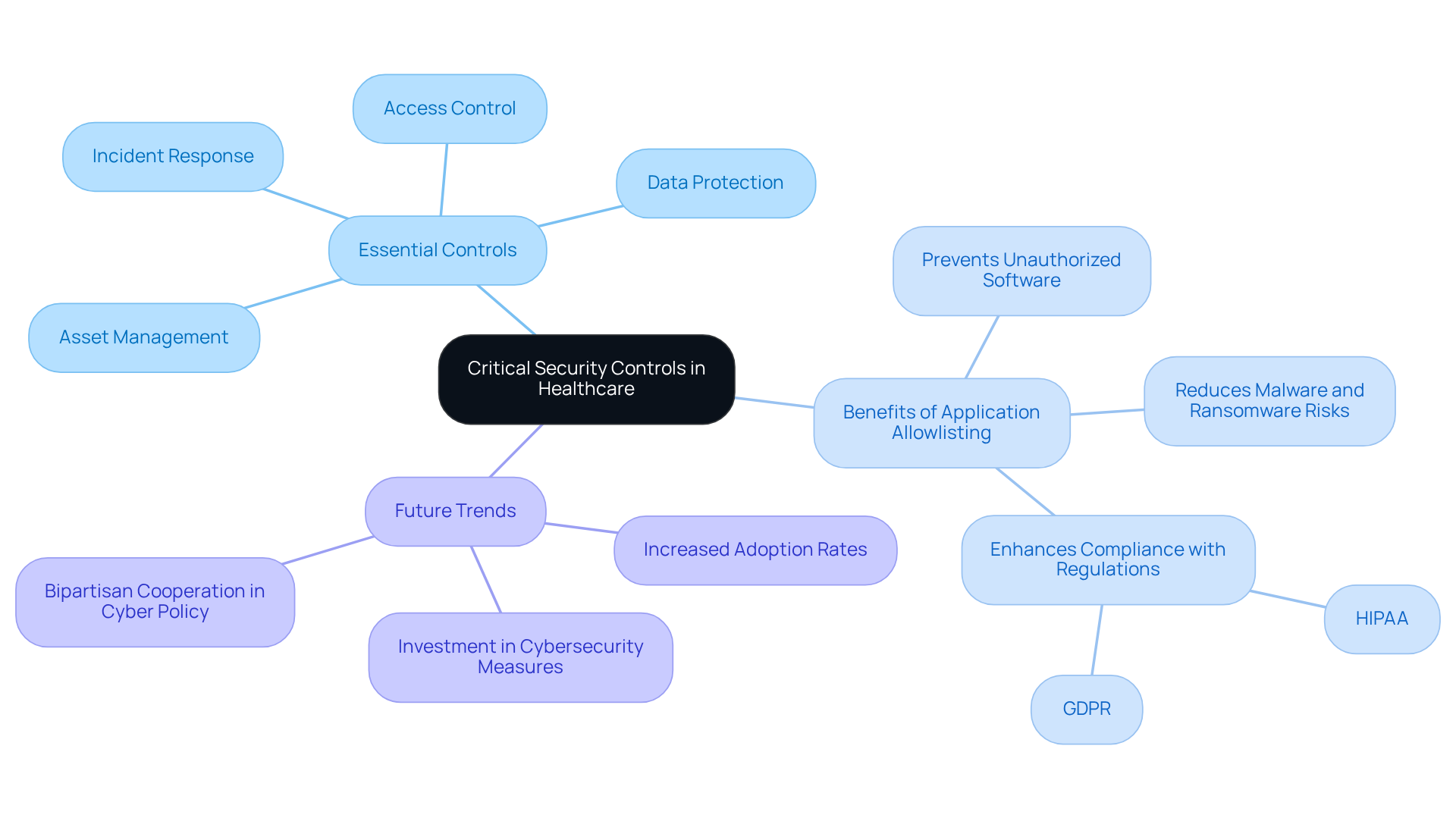
In the realm of healthcare, cybersecurity is not just an option; it is a necessity. The framework of best practices provided by essential controls, particularly critical security control, is vital for mitigating cybersecurity risks, especially for organizations that handle sensitive patient information and face stringent regulatory requirements. The Center for Internet Protection (CIP) has identified 18 essential protective controls that should be prioritized, including:
Among these, application allowlisting emerges as a proactive measure that effectively prevents unauthorized software from executing, significantly diminishing the risk of malware, ransomware, and compliance violations. This strategy not only bolsters security but also aids in such as HIPAA and GDPR.
As we look towards 2025, adoption rates of these controls within healthcare are anticipated to surge, reflecting a growing awareness of cybersecurity threats. Organizations that have embraced these controls, particularly application allowlisting, have reported a notable decline in data breaches and enhanced incident response times. A prime example is Bridgestone Americas, which underscores the necessity of robust security measures, including application allowlisting, to effectively restore operations.
Moreover, security specialists assert that aligning financial strategies with these essential controls is imperative for CFOs. By investing in CIS-aligned cybersecurity measures, medical organizations can achieve significant risk reduction and ensure compliance, ultimately enhancing operational efficiency and fostering patient trust. As the landscape of cyber threats evolves, remaining informed about the latest critical security control measures is essential for safeguarding sensitive information and ensuring regulatory compliance.
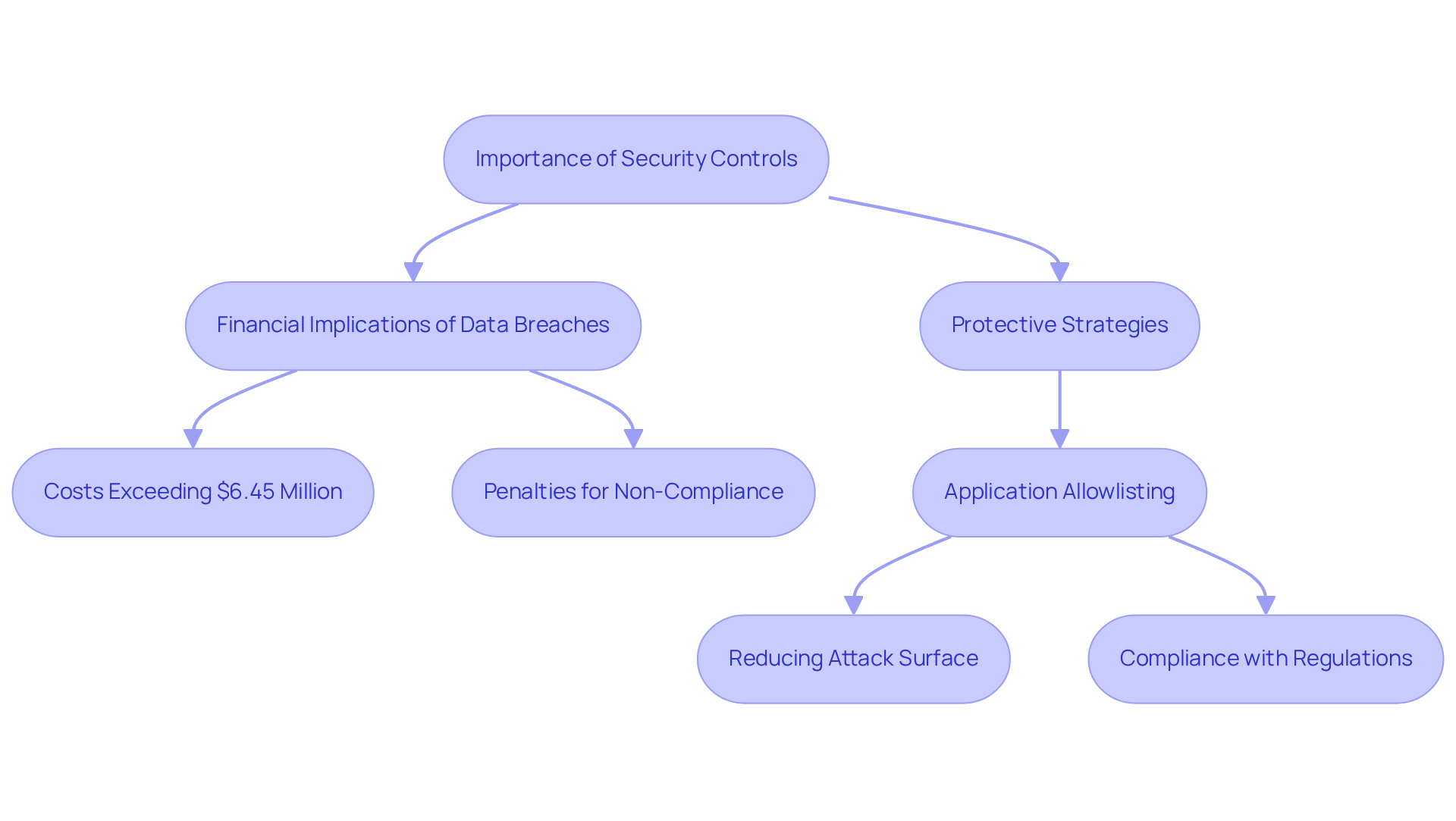
In today's healthcare landscape, the significance of robust cybersecurity measures cannot be overstated, as data breaches can result in substantial financial and reputational harm. For CFOs, grasping the financial ramifications of insufficient protective measures is crucial. A single data breach can incur costs exceeding $6.45 million, encompassing fines, legal fees, and lost revenue. Regulatory bodies enforce stringent penalties for non-compliance with laws such as HIPAA, leading medical entities to face severe consequences for failing to protect sensitive patient information.
Notably, the healthcare sector accounted for 61.55% of all data breaches from 2005 to 2019, with 3,912 verified incidents, underscoring the urgent need for effective protective strategies. By recognizing the critical security control of implementing comprehensive protective measures, including application allowlisting, CFOs can advocate for essential investments in cybersecurity. This ensures their organizations not only meet compliance standards but also build resilience against evolving threats.
Application allowlisting serves as a proactive defense, preventing unauthorized or malicious applications from executing on systems. By permitting only pre-approved software to operate, organizations can significantly diminish their attack surface and reduce vulnerabilities, complicating efforts for attackers to exploit systems. This strategy not only aids in but also ensures adherence to stringent regulations such as HIPAA, PCI-DSS, and GDPR.
Furthermore, ongoing monitoring of application activity and centralized management of allowlists enhance the effectiveness of this protective measure. Experts assert that proactive protective strategies are vital in averting the financial repercussions of data breaches, which can jeopardize patient care and trust. Therefore, prioritizing critical security control transcends mere regulatory compliance; it is a strategic imperative for medical institutions.
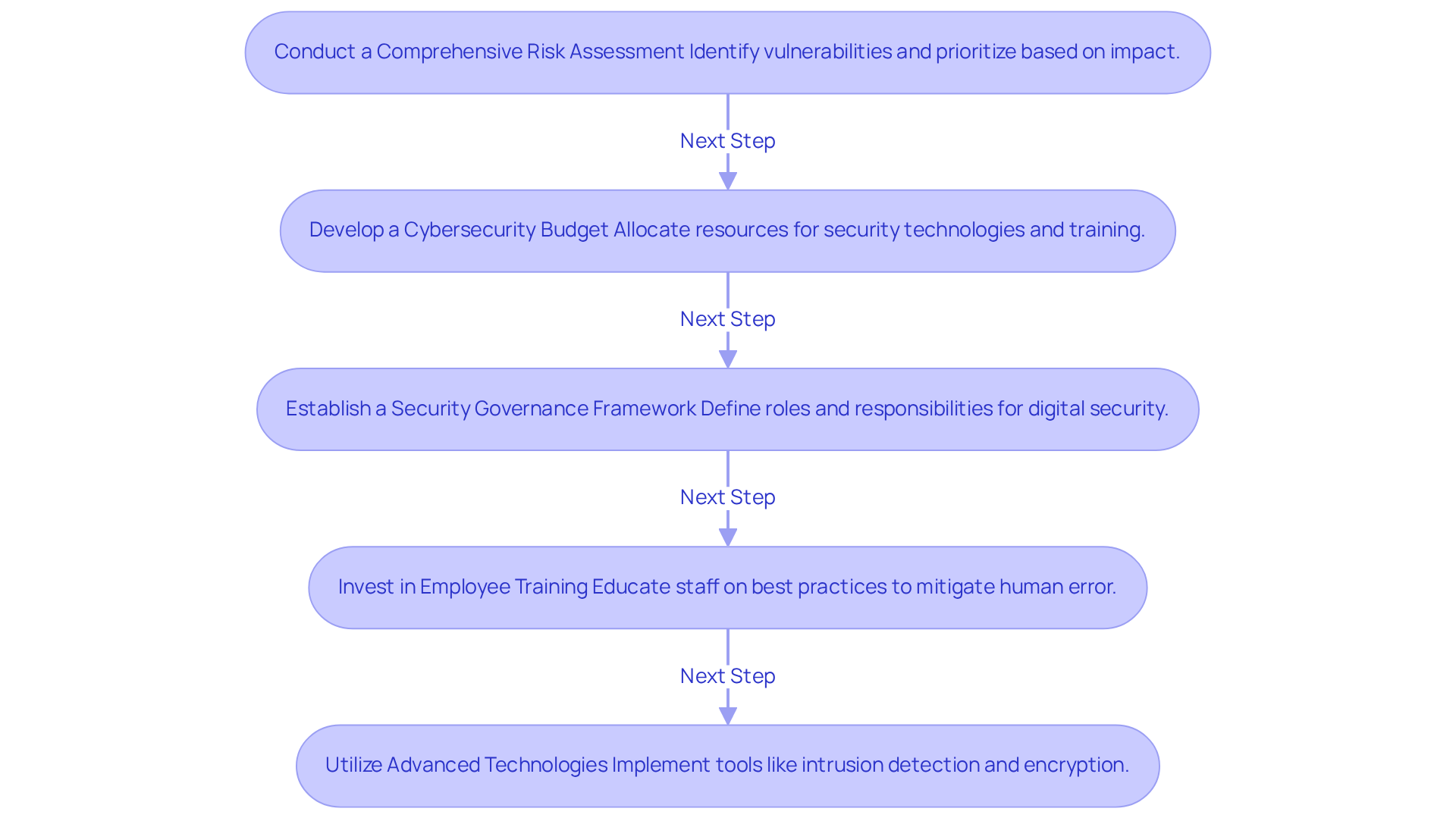
In today's healthcare landscape, cybersecurity is not just an option; it's a necessity. CFOs in the medical field must implement effective critical security control strategies to protect sensitive patient data and ensure compliance. Here are actionable steps to consider:
By following these strategies, CFOs can ensure their organizations are well-equipped to confront security challenges, ultimately safeguarding sensitive patient data and maintaining compliance.
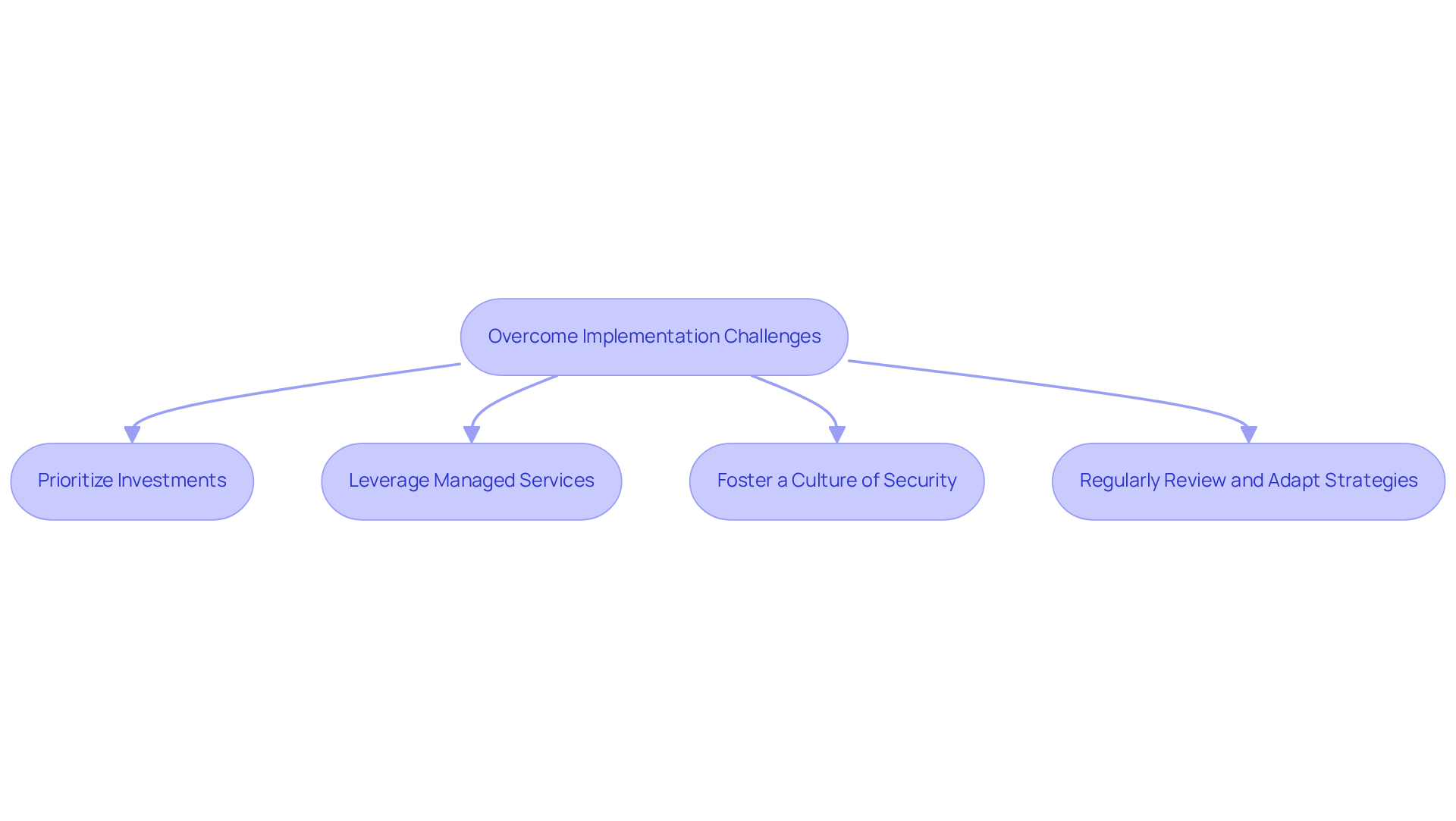
Addressing implementation challenges in digital security is a critical security control for healthcare organizations. The current landscape reveals significant obstacles, including budget constraints, a shortage of skilled personnel, and resistance to change. To effectively navigate these challenges, CFOs can take decisive actions:
By proactively addressing these challenges, CFOs can significantly enhance their organization's cybersecurity posture through the implementation of critical security controls and ensure long-term resilience.
In the healthcare sector, mastering critical security controls is not just important; it is essential for CFOs entrusted with safeguarding sensitive patient information and ensuring compliance with stringent regulations. The focus on cybersecurity transcends mere trendiness; it is a vital necessity that influences both financial stability and patient trust. By prioritizing fundamental controls such as application allowlisting, organizations can significantly mitigate vulnerabilities and strengthen their defenses against the ever-evolving landscape of cyber threats.
This article outlines key strategies for implementing effective security controls, including:
Each of these steps is crucial in mitigating risks associated with data breaches, which can be both costly and damaging to healthcare organizations. Moreover, overcoming implementation challenges through prioritization and collaboration with managed services can lead to a more robust cybersecurity posture.
Ultimately, the significance of critical security controls cannot be overstated. As healthcare CFOs navigate the complexities of cybersecurity, adopting a proactive approach to implementing these strategies will not only protect sensitive data but also enhance organizational resilience. By embracing best practices, healthcare organizations can prepare for the future and maintain the trust of patients and stakeholders alike, ensuring that their financial and reputational interests are well safeguarded against potential cyber threats.
Why is cybersecurity essential in healthcare?
Cybersecurity is essential in healthcare because it is necessary for mitigating risks associated with handling sensitive patient information and complying with stringent regulatory requirements.
What are the critical security controls identified by the Center for Internet Protection (CIP)?
The Center for Internet Protection has identified 18 essential protective controls, which include asset management, access control, data protection, and incident response.
What is application allowlisting and how does it enhance security?
Application allowlisting is a proactive measure that prevents unauthorized software from executing, significantly reducing the risk of malware, ransomware, and compliance violations while aiding in adherence to regulations like HIPAA and GDPR.
What is expected regarding the adoption of critical security controls in healthcare by 2025?
Adoption rates of critical security controls within healthcare are anticipated to surge by 2025, reflecting a growing awareness of cybersecurity threats.
How have organizations that implemented these controls fared in terms of data breaches?
Organizations that have embraced critical security controls, particularly application allowlisting, have reported a notable decline in data breaches and improved incident response times.
What role do CFOs play in aligning financial strategies with cybersecurity measures?
CFOs are encouraged to align financial strategies with essential cybersecurity controls to achieve significant risk reduction, ensure compliance, enhance operational efficiency, and foster patient trust.
Why is it important to stay informed about critical security control measures?
Staying informed about the latest critical security control measures is essential for safeguarding sensitive information and ensuring regulatory compliance as the landscape of cyber threats evolves.