
In today's digital landscape, the risk of cyber attacks in healthcare is alarmingly high. To combat this threat, CFOs must take decisive action by implementing four essential steps:
These strategies not only enhance security by addressing vulnerabilities and unauthorized access, but they also foster a culture of awareness and preparedness within healthcare organizations. Ultimately, this proactive approach safeguards sensitive data and ensures the financial health of the organization.
In an era where digital threats are more pronounced than ever, the healthcare sector stands at a pivotal crossroads. Cyber attacks not only endanger patient data but also inflict substantial financial repercussions, with healthcare organizations experiencing an average loss exceeding $11 million per incident. For CFOs, the stakes are particularly elevated as they navigate the intricate landscape of financial integrity and operational security.
How can they effectively shield their organizations from these persistent threats while ensuring compliance and preserving trust? This article explores essential strategies that CFOs must implement to mitigate the risk of cyber attacks, empowering them to bolster their defenses and safeguard their financial health.
In today's digital landscape, is not just important; it's essential. Cyber threats manifest in various forms, including:
Each presents unique challenges that can significantly impact healthcare organizations. Ransomware, for example, can encrypt critical data and demand hefty ransoms for its release, while phishing schemes often lead to unauthorized access to sensitive financial information. The are staggering; in 2025, healthcare entities reported an average expense of $11.45 million per incident, the highest across all industries. Direct costs encompass ransom payments, legal fees, and substantial losses due to operational downtime.
Consider this: 94% of hospitals affected by recent cyber incidents reported , with 33% indicating disruptions that affected more than half of their revenue. The reputational damage from such breaches can erode customer trust, leading to long-term revenue loss. Understanding these dynamics is crucial for CFOs aiming to develop a that incorporates while also safeguarding the financial health of their organizations.
To combat these threats, it is imperative to establish as a key strategy for how to reduce the risk of cyber attack. Continuous observation ensures that suspicious behaviors are detected and addressed before they escalate into significant risks, which is a key strategy in how to reduce the risk of cyber attack, protecting your organization from ransomware, phishing, and other forms of malware. Additionally, designed specifically for the healthcare sector—including comprehensive firewall and network protection strategies—can further bolster your defenses against these evolving cyber threats.

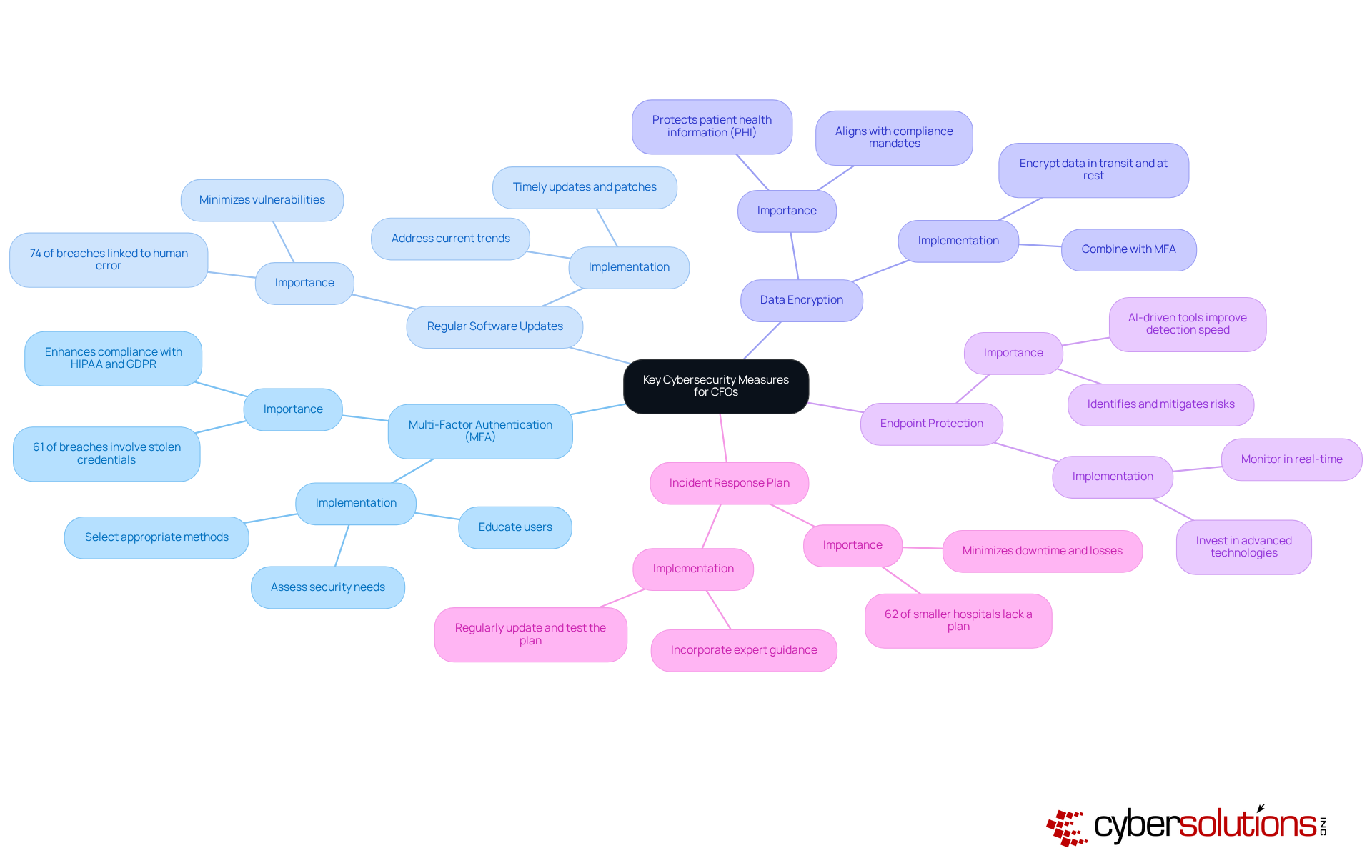
CFOs must prioritize key that are essential for safeguarding their organizations to learn how to reduce the risk of cyber attack effectively. Cybersecurity in healthcare is not just a necessity; it is a critical component of operational integrity. With the , the implications for healthcare organizations are profound. Here are the vital strategies that can fortify defenses and promote a .
By implementing these strategies, CFOs can greatly improve their entity’s protective stance, minimize the chances of successful breaches, and promote a culture of cybersecurity that aligns with wider business goals, specifically focusing on how to reduce the risk of cyber attack. Additionally, it is important to recognize that is an ongoing process that requires continuous monitoring, updates, and expert oversight.
Informing staff about how to is essential for cultivating a robust within the organization. In today's landscape, where cyber threats are ever-evolving, it is crucial to equip employees with the knowledge of how to reduce the risk of cyber attack to protect . Here are some effective strategies that can significantly enhance your cybersecurity posture:
By fostering a knowledgeable workforce, organizations can learn how to reduce the risk of cyber attack that may result from human error. The commitment to continuous improvement in cybersecurity practices not only protects sensitive data but also enhances overall organizational resilience.

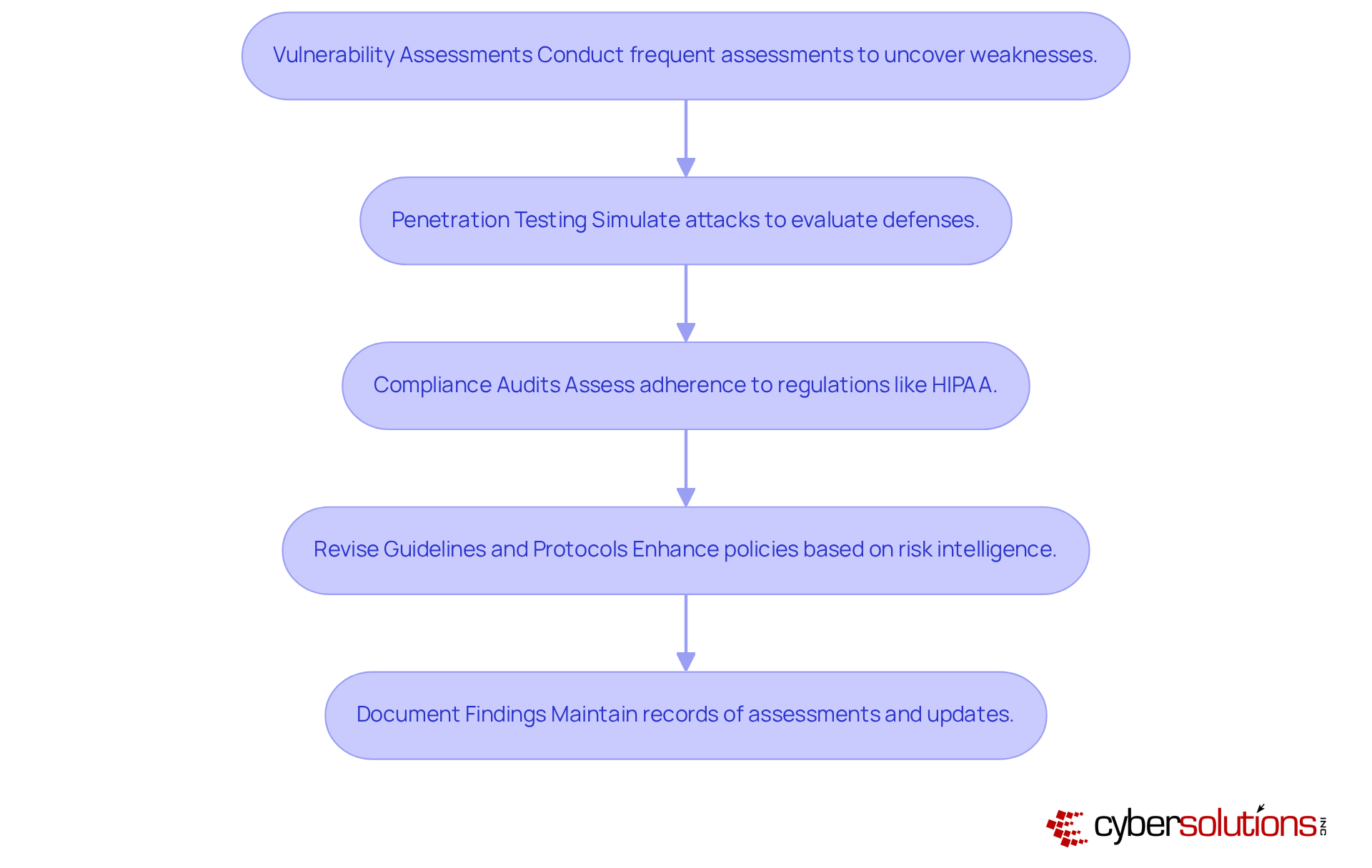
In the rapidly evolving landscape of healthcare, it is essential to know how to and maintain a robust cybersecurity stance. Regular evaluations and updates are essential for understanding how to reduce the risk of cyber attack while against emerging threats. Here’s how to implement this effectively:
By integrating these practices into the organizational routine, CFOs can ensure that their alongside emerging threats, ultimately safeguarding sensitive patient data and maintaining trust.
In the face of escalating cyber threats, it is essential for CFOs to prioritize cybersecurity as a cornerstone of their organizational strategy. The article delineates crucial steps that can significantly mitigate the risk of cyber attacks, underscoring that a proactive approach is not merely advantageous but vital for the financial health and operational integrity of healthcare organizations.
The key arguments presented highlight the necessity of:
By conducting regular security assessments and ensuring compliance with industry regulations, CFOs can empower their organizations to better manage potential breaches and reduce financial losses tied to cyber incidents.
Ultimately, the onus of safeguarding sensitive data and maintaining trust with stakeholders rests heavily on the shoulders of CFOs. By embracing these strategies and committing to continuous education and enhancement of cybersecurity practices, organizations can fortify themselves against the ever-evolving landscape of cyber threats. Adopting a comprehensive cybersecurity framework transcends mere defense; it emerges as a strategic imperative that will protect both financial and reputational assets in an increasingly digital world.
What are the main types of cyber threats faced by healthcare organizations?
The main types of cyber threats in healthcare include phishing, ransomware, and denial-of-service incidents.
What are the potential impacts of ransomware on healthcare organizations?
Ransomware can encrypt critical data and demand large ransoms for its release, leading to significant operational downtime and financial losses.
How much do healthcare organizations spend on average per cyber incident?
In 2025, healthcare entities reported an average expense of $11.45 million per incident, making it the highest across all industries.
What percentage of hospitals reported financial impacts from cyber incidents?
94% of hospitals affected by recent cyber incidents reported financial impacts.
What are some of the direct costs associated with cyber attacks in healthcare?
Direct costs include ransom payments, legal fees, and substantial losses due to operational downtime.
How can cyber attacks affect a hospital's revenue?
33% of hospitals indicated that disruptions from cyber incidents affected more than half of their revenue.
What is the importance of understanding cyber threats for CFOs in healthcare?
Understanding these dynamics is crucial for CFOs to develop a robust cybersecurity strategy that reduces the risk of cyber attacks while safeguarding the financial health of their organizations.
What is a key strategy for reducing the risk of cyber attacks?
Establishing round-the-clock monitoring is a key strategy to detect and address suspicious behaviors before they escalate into significant risks.
What tailored IT solutions can help protect healthcare organizations from cyber threats?
Tailored IT solutions for healthcare, including comprehensive firewall and network protection strategies, can bolster defenses against evolving cyber threats.