
In today's digital landscape, cybersecurity is paramount for healthcare organizations, and CVE funding is essential for CFOs aiming to enhance their cybersecurity strategies. This funding supports the identification and management of vulnerabilities that can lead to costly data breaches and compliance violations. Robust CVE funding not only mitigates the financial risks associated with cyberattacks but also fortifies the overall security posture of healthcare organizations. By enabling timely responses to emerging threats and ensuring adherence to regulatory standards, it empowers CFOs to take decisive action in safeguarding sensitive data. As the threat landscape evolves, the need for effective cybersecurity measures has never been more critical.
In a landscape where cyber threats loom large, the healthcare sector faces unprecedented challenges in safeguarding sensitive patient information. For CFOs navigating this complex environment, understanding the pivotal role of Common Vulnerabilities and Exposures (CVE) funding is essential. This financial support not only enhances vulnerability management but also fortifies compliance initiatives, ultimately protecting organizations from costly breaches.
With alarming statistics revealing that 92% of medical organizations encountered cyberattacks last year, the pressing question remains: how can healthcare CFOs effectively leverage CVE funding to transform their cybersecurity strategies and ensure robust defenses against evolving threats?
CVE (Common Vulnerabilities and Exposures) support is crucial in the cybersecurity landscape, especially for medical institutions. It enables the continuous identification and cataloging of vulnerabilities, which is vital for maintaining a robust security posture. For CFOs in healthcare, recognizing the importance of this financial support is imperative, as it directly influences risk management and compliance initiatives. Investing in CVE support allows organizations to enhance the protection of sensitive patient information, significantly reduce the likelihood of costly breaches, and ensure compliance with regulatory standards. This proactive approach not only safeguards valuable assets but also bolsters the overall financial health of the organization by mitigating potential losses from cyber incidents.
The impact of CVE funding on risk management is emphasized by alarming statistics regarding cyberattacks in the medical sector. In 2024:
Case studies illustrate the transformative effects of CVE funding on medical data protection. The evolution of the CVE Program, now encompassing 453 CVE Numbering Authorities (CNAs), has facilitated quicker and more widespread identification of vulnerabilities. This progress provides that empower medical entities to take swift action against potential threats. Furthermore, community engagement within the CVE Program promotes collaboration between the private sector and international governments, enhancing the program's effectiveness and value.
Expert opinions further highlight the importance of CVE support in risk management. Matt Hartman, CISA Acting Executive Assistant Director for Cybersecurity, stated that the CVE Program is an essential resource for network defenders and software developers. By prioritizing CVE resources, healthcare institutions can strengthen their defenses against cyber threats, ensuring compliance with industry standards and ultimately protecting patient care.

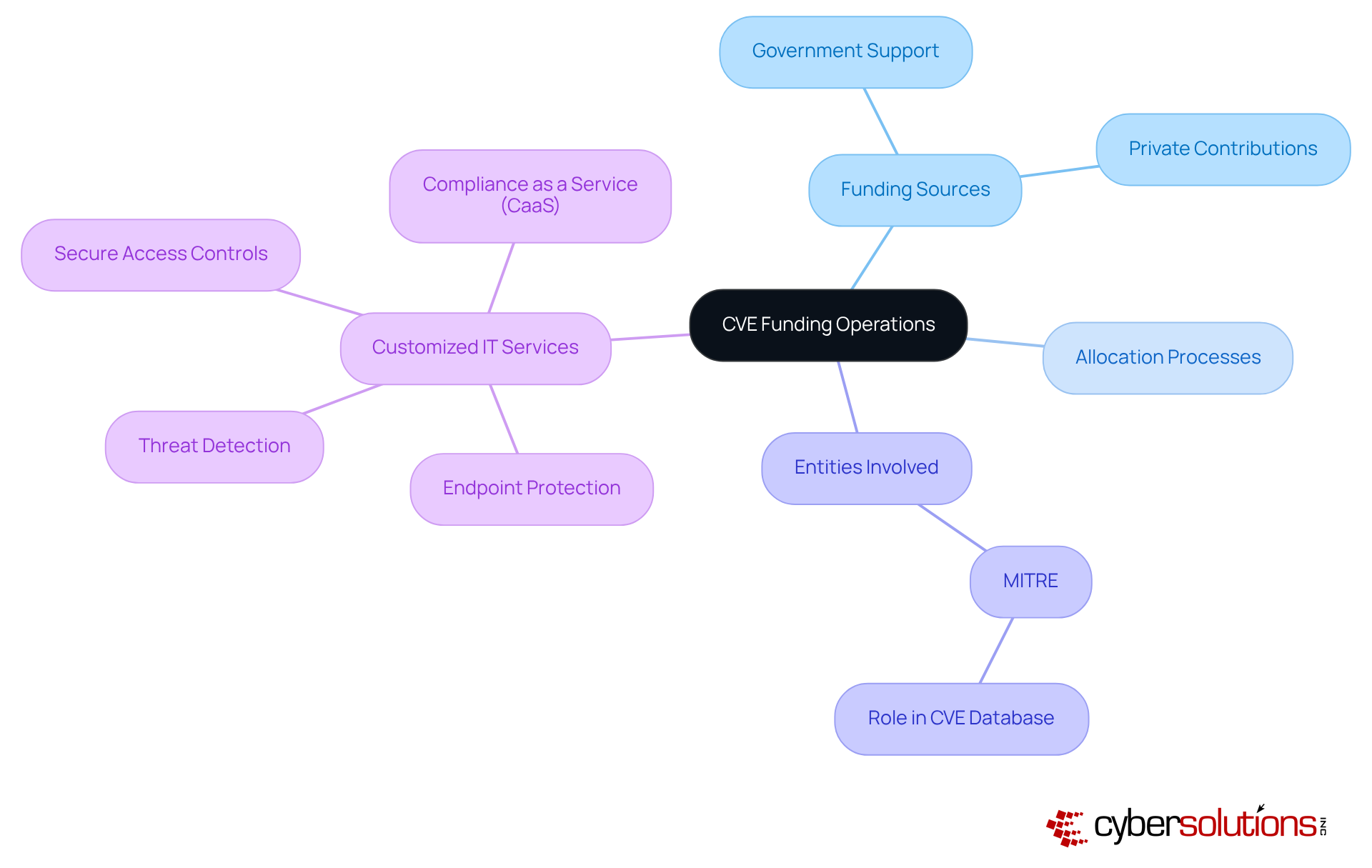
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. CVE funding operates through a combination of government support and private sector contributions, with financial resources primarily allocated to entities such as MITRE, which oversees the CVE database. This ensures that vulnerabilities are meticulously recorded and accessible to cybersecurity professionals. For financial officers in the medical field, understanding this operational framework is not just beneficial; it is essential. Grasping the sources of CVE funding, the allocation processes, and the implications of funding levels on vulnerability management effectiveness is crucial.
Moreover, customized IT services—such as endpoint protection, threat detection, and secure access controls—are vital for addressing the specific security and compliance requirements of the medical sector. By comprehending these mechanisms and the significance of streamlined compliance as a service (CaaS), CFOs can effectively advocate for necessary budget allocations that align with their entity's cybersecurity needs. This understanding empowers them to navigate the complexities of funding and resource allocation, ultimately of their organizations.
Cybersecurity in healthcare is not merely a financial concern; it is a critical component that shapes the very foundation of operational integrity. CVE support is essential for the timely identification and remediation of vulnerabilities, significantly reducing the risk of data breaches and compliance violations.
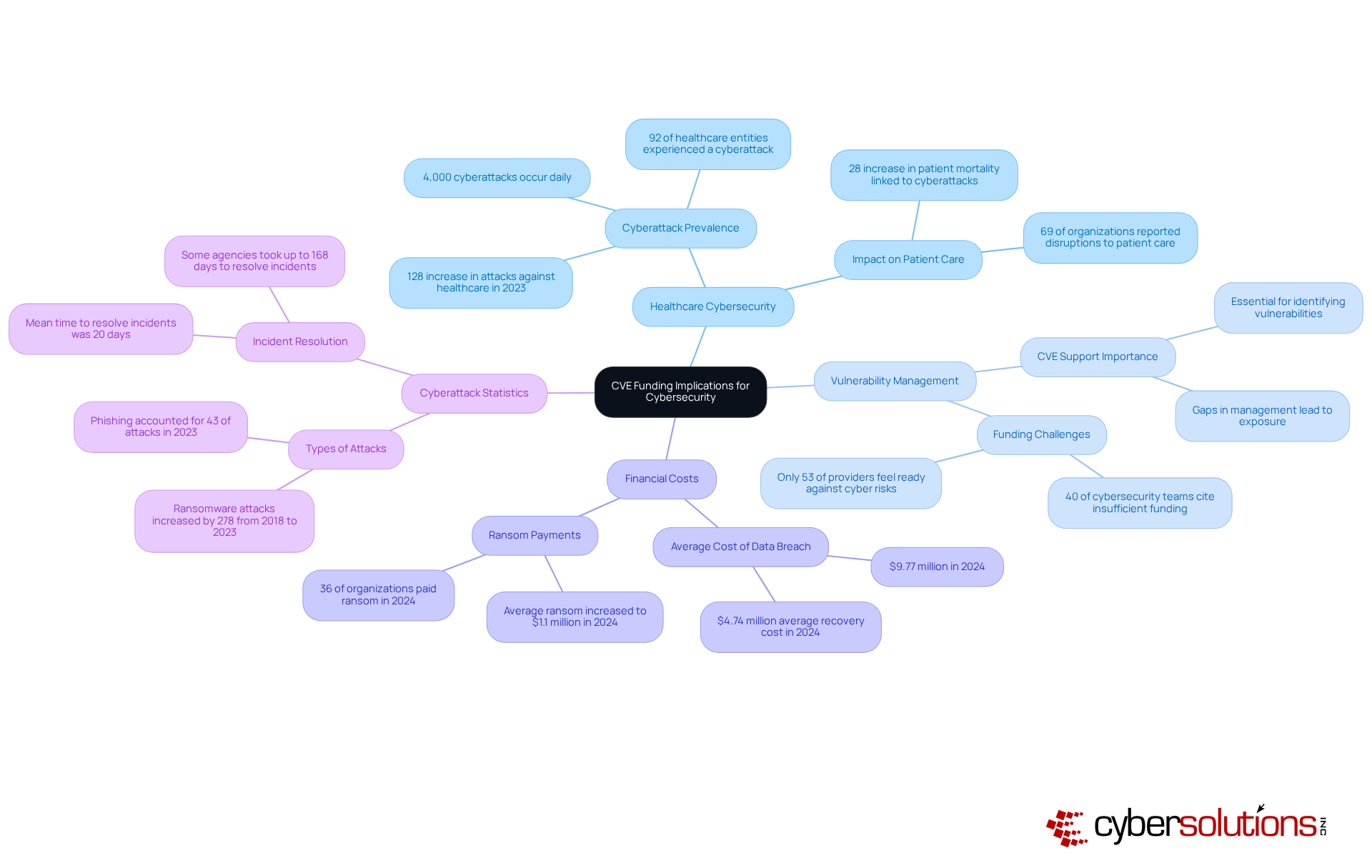
Without adequate CVE funding, healthcare institutions face substantial , which leaves them exposed to cyber threats. In fact, statistics reveal that in 2024, the average cost of a data breach in the medical sector skyrocketed to approximately $9.77 million, underscoring the dire financial repercussions of insufficient cybersecurity strategies.
Furthermore, a staggering 92% of healthcare entities reported experiencing at least one cyberattack in the previous year, many attributing these incidents to inadequate resources for vulnerability management. For CFOs, this analysis serves as a clarion call to champion robust CVE funding as a cornerstone of a comprehensive cybersecurity strategy.
By aligning financial resources with cybersecurity initiatives, organizations can bolster their defenses against cyber threats, enhance operational resilience, and ensure compliance with stringent industry regulations.
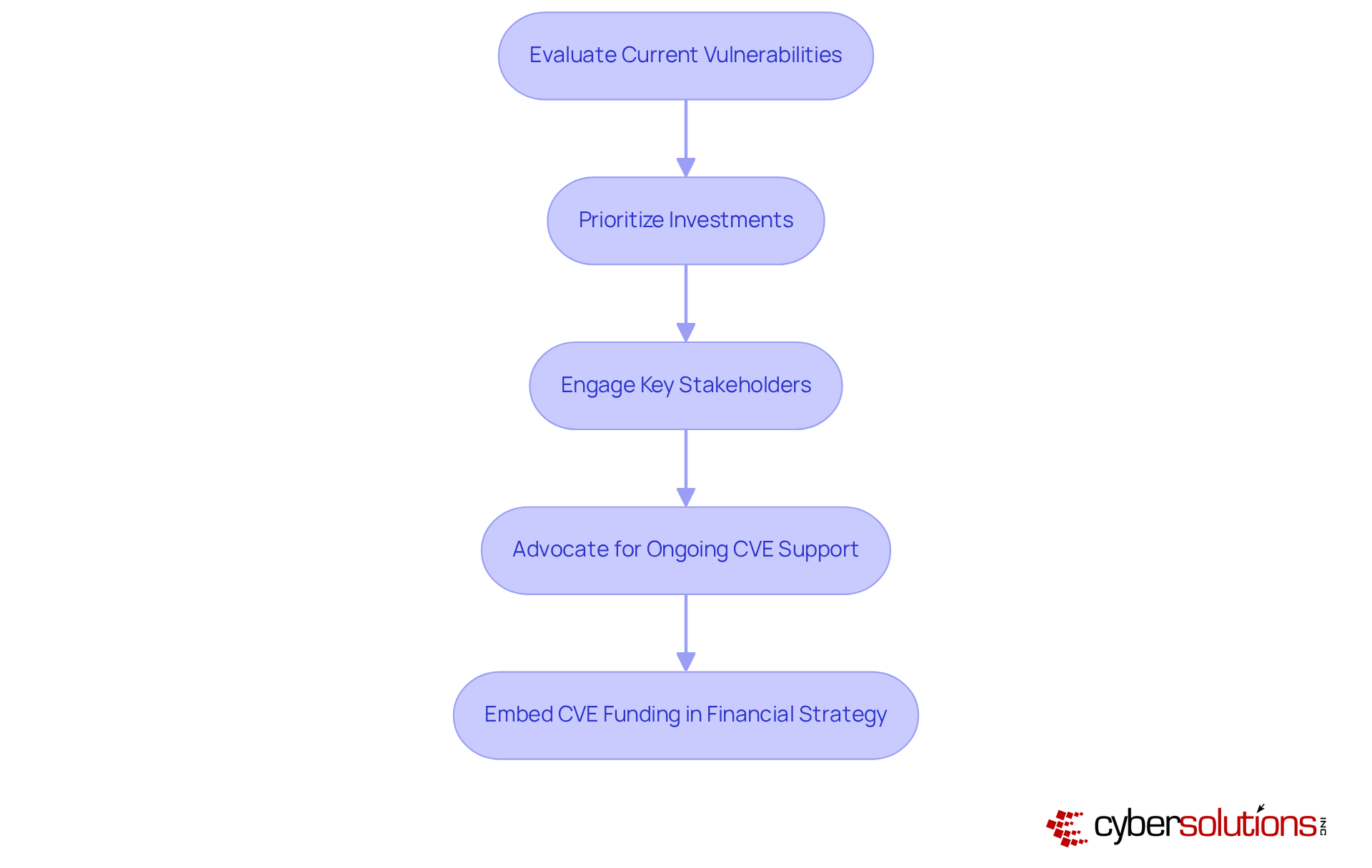
In today's digital landscape, the effectiveness of CVE funding is paramount for healthcare organizations. To navigate the complex challenges posed by , healthcare CFOs must adopt a strategic framework that aligns financial resources with the organization's cybersecurity objectives. This begins with a comprehensive evaluation of current vulnerabilities, enabling CFOs to pinpoint areas where financial investments can yield the most significant impact.
Prioritizing investments in advanced vulnerability management tools, targeted training programs, and robust incident response capabilities is essential for fortifying the organization's overall cybersecurity posture. Engaging with key stakeholders to advocate for ongoing CVE support is not just beneficial; it is crucial. This advocacy underscores the importance of these resources in safeguarding sensitive data and maintaining compliance with regulatory standards.
By embedding CVE funding into the organization's financial strategy, CFOs can facilitate substantial enhancements in cybersecurity resilience and risk management. This proactive approach ultimately protects the organization from evolving digital threats, ensuring that it remains secure in an increasingly perilous environment.
CVE funding is indispensable in strengthening the cybersecurity landscape within healthcare organizations. By understanding and leveraging this financial support, CFOs can significantly enhance their institutions' capacity to identify and address vulnerabilities, thereby safeguarding sensitive patient information and ensuring compliance with stringent regulations.
The statistics surrounding cyberattacks in the medical sector are alarming, underscoring the urgent need for robust cybersecurity measures. With 92% of healthcare entities experiencing cyber incidents and the average breach costing millions, it is clear that investing in CVE funding is not merely an option but a necessity. Moreover, the operational mechanisms of CVE funding illustrate how strategic resource allocation can empower organizations to construct resilient defenses against evolving threats.
In light of these insights, healthcare CFOs are urged to prioritize CVE funding as a crucial element of their cybersecurity strategies. By advocating for necessary investments and aligning financial resources with comprehensive security initiatives, organizations can mitigate potential risks while enhancing their overall operational integrity. The time to act is now; embracing CVE funding is essential for navigating the complexities of cybersecurity in healthcare and ensuring a secure future for patient care.
What is the significance of CVE funding in cybersecurity, particularly for medical institutions?
CVE funding is crucial for continuously identifying and cataloging vulnerabilities, which is essential for maintaining a robust security posture in medical institutions. It directly influences risk management and compliance initiatives, helping to protect sensitive patient information and reduce the likelihood of costly breaches.
How does CVE support impact financial health in healthcare organizations?
Investing in CVE support enhances the protection of sensitive data, mitigates potential losses from cyber incidents, and ensures compliance with regulatory standards. This proactive approach bolsters the overall financial health of the organization by reducing the risks associated with cybersecurity breaches.
What statistics underline the need for CVE funding in the medical sector?
In 2024, 92% of medical organizations reported experiencing at least one cyberattack, averaging 40 attacks per organization. The average cost of a cybersecurity breach reached $4.74 million, and breaches compromised approximately 45.6 million medical records, highlighting the urgent need for effective data protection strategies.
How has the CVE Program evolved to enhance data protection in medical institutions?
The CVE Program has evolved to include 453 CVE Numbering Authorities (CNAs), facilitating quicker and more widespread identification of vulnerabilities. This progress provides essential insights that empower medical entities to act swiftly against potential threats.
What role does community engagement play in the CVE Program?
Community engagement within the CVE Program promotes collaboration between the private sector and international governments, enhancing the program's effectiveness and value in addressing cybersecurity challenges.
What expert opinions emphasize the importance of CVE support in risk management?
Matt Hartman, CISA Acting Executive Assistant Director for Cybersecurity, stated that the CVE Program is an essential resource for network defenders and software developers. Prioritizing CVE resources helps healthcare institutions strengthen their defenses against cyber threats, ensuring compliance with industry standards and protecting patient care.