
In today's digital age, the protection of sensitive patient information is paramount, making robust cybersecurity measures essential for healthcare CFOs. The landscape of cybersecurity threats is evolving, and healthcare organizations are increasingly vulnerable to attacks that compromise patient data and violate regulations such as HIPAA. CFOs face unique challenges as they navigate these threats while ensuring compliance and safeguarding their organizations' reputations.
To effectively enhance their security posture, healthcare CFOs must implement a comprehensive suite of strategies. Key measures include:
These strategies collectively fortify healthcare organizations against cyber threats, ensuring that patient information remains secure. By prioritizing these essential cybersecurity measures, CFOs can not only protect their organizations but also foster trust among patients and stakeholders. As the stakes continue to rise, it is imperative for healthcare leaders to take decisive action in addressing these challenges head-on.
In an era where cyber threats are increasingly pervasive, the healthcare sector stands at a pivotal crossroads, confronting the dual challenge of safeguarding sensitive patient data and adhering to stringent regulatory requirements. This article explores ten critical cybersecurity measures that CFOs in healthcare must implement to strengthen their organizations against emerging threats. By examining proactive strategies—from robust password policies to comprehensive incident response plans—readers will gain actionable insights that not only protect patient information but also bolster operational resilience. As the stakes escalate, one pressing question persists: how prepared is your organization to navigate this intricate cybersecurity landscape?
In today's healthcare landscape, the importance of robust cyber security measures cannot be overstated. Cyber Solutions Inc. offers a comprehensive array of managed IT and cybersecurity services specifically tailored for the medical industry, addressing the unique challenges faced by healthcare organizations. Their offerings include:
By leveraging cutting-edge technology, Cyber Solutions empowers medical institutions to concentrate on their core activities while ensuring strict security and compliance with essential regulations like HIPAA.
This proactive strategy significantly reduces risks associated with cyber threats and enhances operational efficiency, enabling healthcare providers to deliver superior patient care. With features such as:
Cyber Solutions guarantees that medical facilities remain audit-ready and equipped to tackle regulatory challenges. As the medical IT environment evolves, the integration of managed IT services becomes essential for organizations striving to protect sensitive data and optimize their operations effectively. How prepared is your organization to face these challenges? With Cyber Solutions, you can ensure that your cyber security measures are not just reactive but strategically proactive.
Implementing robust password policies is not just a best practice; it is essential for safeguarding sensitive medical data and ensuring HIPAA compliance. Organizations must enforce the use of unique passwords that are a minimum of 12 characters long, incorporating a combination of uppercase letters, lowercase letters, numbers, and special characters. Regular password updates are vital, as short and simple passwords can be cracked in mere seconds, exposing sensitive patient information to cyber threats. A staggering percentage of medical institutions still struggle with enforcing strong password policies, leaving them vulnerable to attacks such as credential stuffing, where stolen username-password pairs are used to access multiple accounts.
To bolster security, utilizing is highly recommended. These tools not only help generate complex passwords but also securely store them, significantly reducing the likelihood of password reuse across different accounts. Expert guidance stresses that medical institutions should prioritize training personnel on [effective password management practices](http://discovercybersolutions.com/blog-posts/7-managed-security-providers-enhancing-healthcare-cfo-strategies), including the importance of steering clear of common passwords and routinely updating credentials.
Moreover, integrating these password policies into a comprehensive cyber security measure is crucial. This strategy encompasses proactive risk management to identify vulnerabilities, expert advice for adherence, and continuous monitoring to ensure that entities remain audit-ready. By adopting these best practices, CFOs in the medical field can significantly improve their entity's data protection stance and safeguard patient privacy, all while ensuring continuous adherence to HIPAA standards.

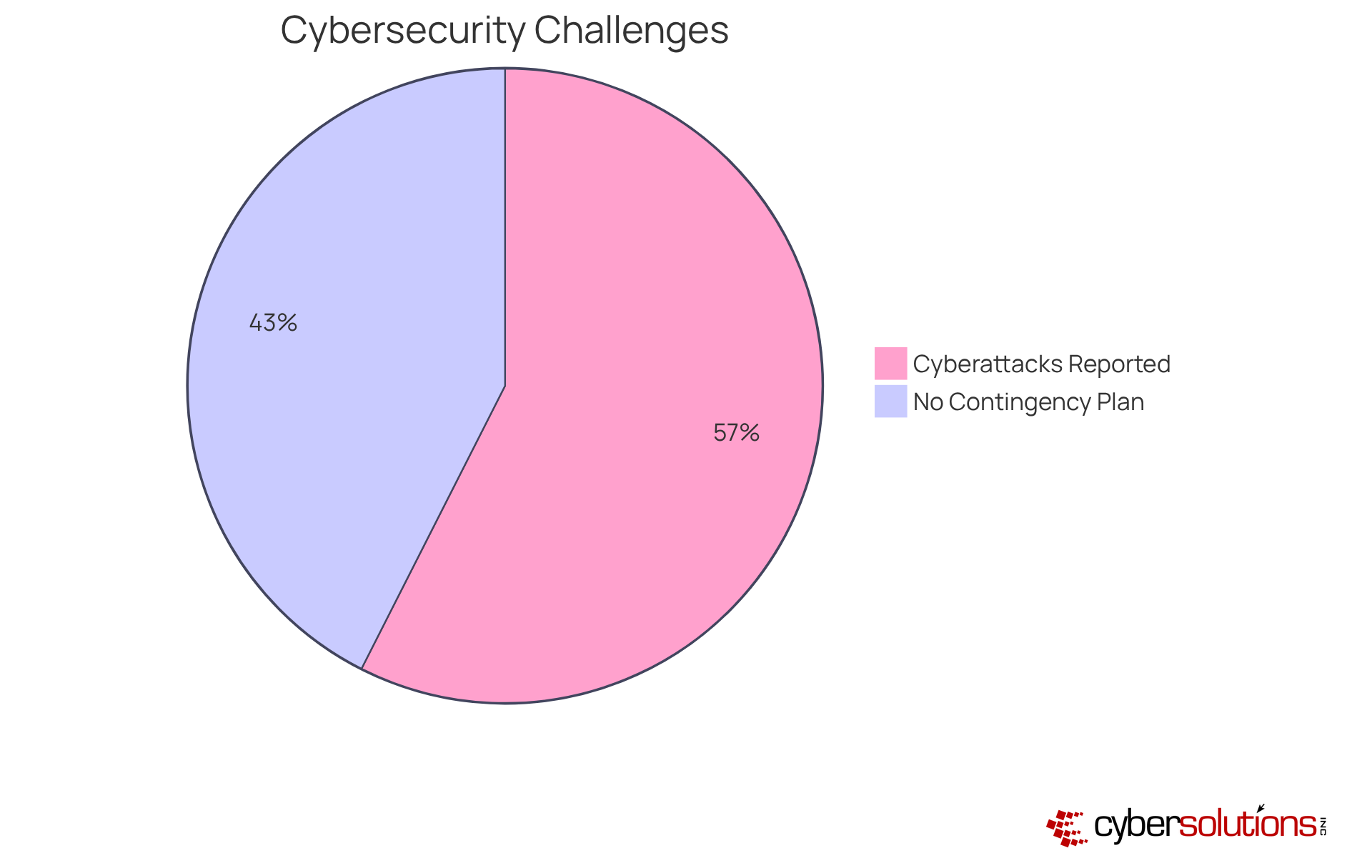
In today's healthcare landscape, prioritizing a cyber security measure is not just a necessity—it's a mandate. With a staggering 50% of medical institutions reporting cyberattacks, the urgency to implement robust as a cyber security measure across all systems—including operating systems, applications, and security software—cannot be overstated. Establishing an automated update schedule is essential; it ensures timely patching of vulnerabilities, significantly reducing the risk of exploitation by cybercriminals.
Consider the recent data breach at Northwest Medical Specialties, where unauthorized data copying occurred. This incident serves as a stark reminder of the consequences that arise from neglecting software updates. Furthermore, alarming statistics reveal that 37% of medical institutions lack a cyberattack contingency strategy, exacerbating the effects of such incidents. Frequent software updates are a vital cyber security measure that not only bolster protection but also assist organizations in maintaining compliance with regulations like HIPAA, which mandates periodic audits and adherence to safety standards.
By automating updates, healthcare facilities can minimize human error and ensure that critical patches are applied swiftly. This proactive approach not only enhances their overall security posture but also safeguards sensitive patient information, fostering trust and reliability in an increasingly digital world. The question remains: can your institution afford to overlook these vital updates?
In today's healthcare landscape, implementing regular cyber security measure training sessions is not just beneficial; it is essential. These sessions equip employees with the knowledge necessary to identify potential threats and adhere to best practices. Training must encompass critical topics such as:
By enabling employees through customized training, organizations not only foster a culture of awareness but also adopt a cyber security measure that significantly reduces the risk of breaches stemming from human error.
Moreover, integrating this training with extensive support and regulatory reporting services, like those provided by Cyber Solutions, enhances the overall cybersecurity strategy. A well-informed workforce is pivotal for maintaining operational integrity and safeguarding sensitive patient data. This proactive approach ultimately contributes to a , acting as an essential cyber security measure that ensures healthcare organizations can navigate the complexities of cybersecurity with confidence and resilience.
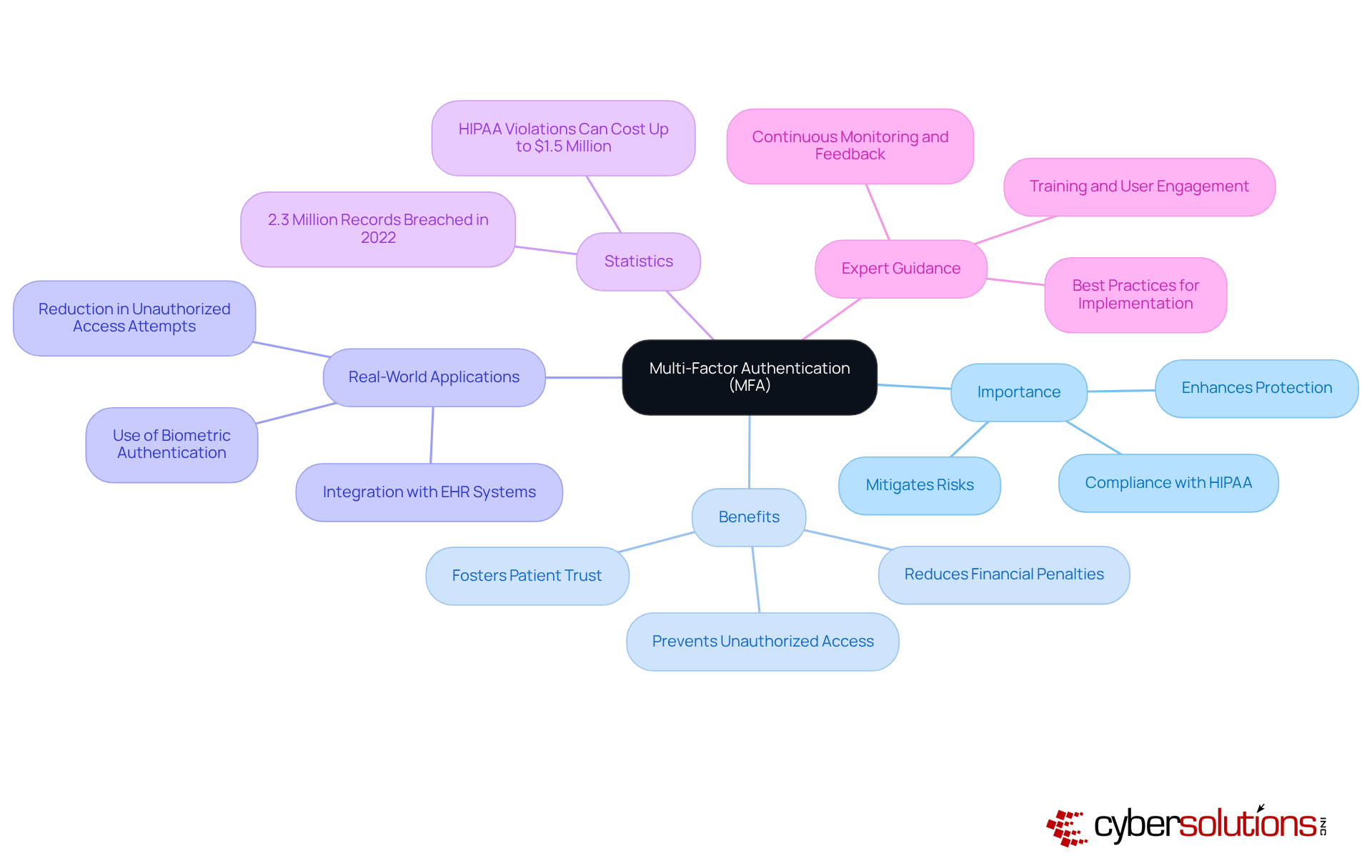
Implementing multi-factor authentication (MFA) across all systems that handle sensitive medical information is a crucial cyber security measure for enhancing protection and ensuring compliance with HIPAA standards. By requiring users to provide two or more verification factors—such as a password combined with a one-time code sent to their mobile device—organizations can significantly strengthen their defenses against unauthorized access. This additional layer of protection is paramount in the healthcare sector, where can lead to severe repercussions, including compromised patient safety and substantial financial penalties.
Moreover, MFA serves as an essential cyber security measure in proactive risk management and incident response planning. By incorporating MFA as a cyber security measure into their protective protocols, organizations can enhance their preparedness for potential incidents and mitigate risks associated with unauthorized access to patient health information (PHI). Virtual CISO services can further enhance this strategy by providing expert guidance on implementing MFA effectively and ensuring ongoing compliance with regulatory requirements.
Statistics show that more than 2.3 million patient records were taken in the 2022 Shields Healthcare breach, highlighting the pressing requirement for strong protective measures. Experts agree that MFA is a crucial cyber security measure for safeguarding sensitive patient information, with many considering it a 'reasonable safeguard' as defined by HIPAA regulations.
Real-world applications of MFA have demonstrated its effectiveness in improving safety. For example, medical organizations that have integrated MFA into their electronic health record (EHR) systems report a significant reduction in unauthorized access attempts. Additionally, the use of modern MFA tools, such as biometric authentication and push notifications, has streamlined the user experience, making it less intrusive while maintaining high security standards.
As the landscape of cyber threats evolves, the significance of using a cyber security measure such as MFA in medical settings cannot be overstated. It not only protects sensitive data but also fosters patient trust and compliance with regulatory requirements, making it a vital component of any comprehensive cybersecurity strategy.
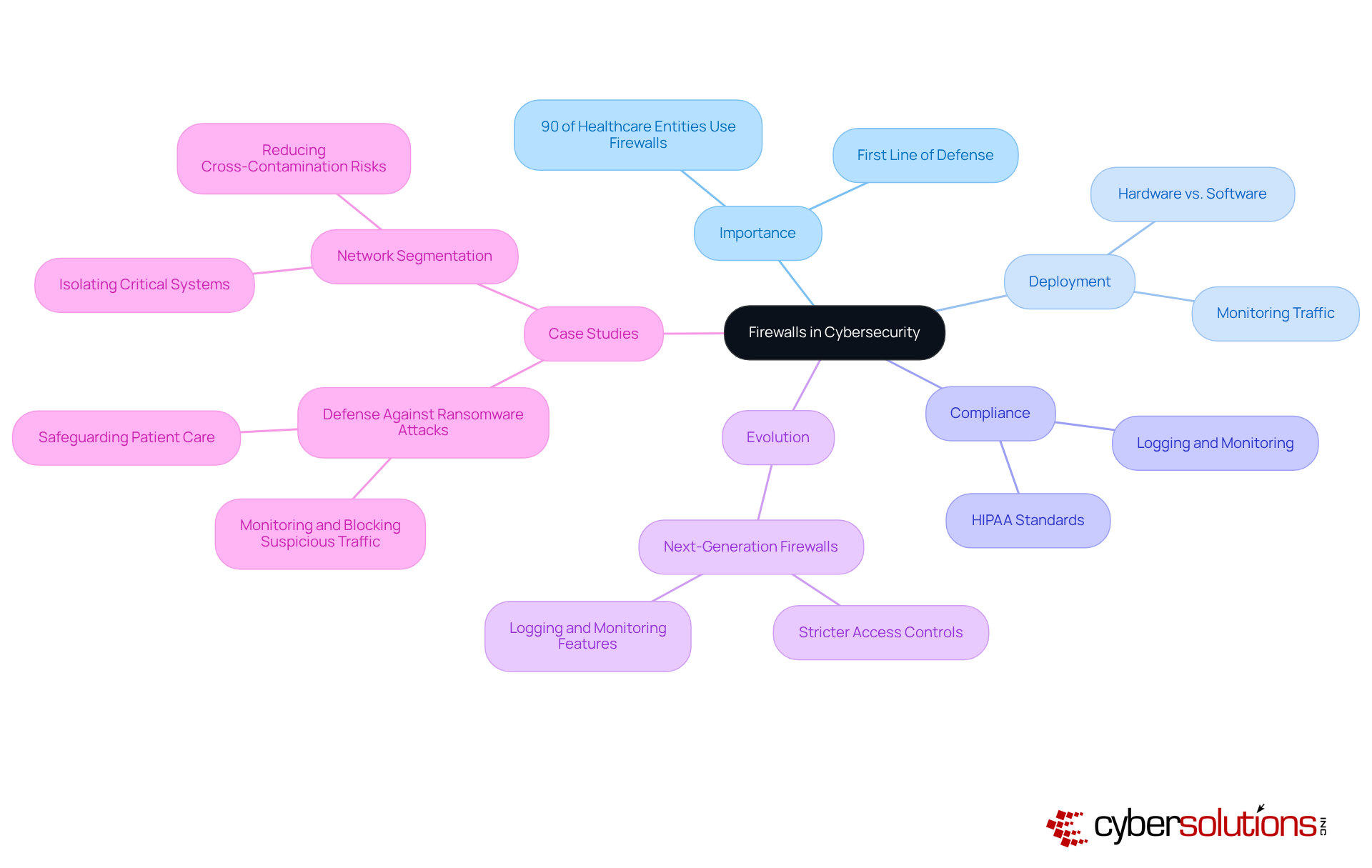
Firewalls represent a cornerstone of cybersecurity within medical networks and are an essential cyber security measure against unauthorized access and cyber threats. With approximately 90% of healthcare entities employing firewalls to protect their systems, their is undeniable. To effectively monitor incoming and outgoing traffic, both hardware and software firewalls should be deployed, blocking potentially harmful connections that could jeopardize sensitive patient data.
Regularly assessing and revising firewall rules is essential to adapt to the ever-evolving threat landscape and ensure compliance with industry standards such as HIPAA. Next-generation firewalls exemplify this evolution, not only enforcing stricter access controls but also providing logging and monitoring features that assist organizations in tracking access attempts and documenting security incidents for compliance purposes.
Case studies further illustrate the effectiveness of firewalls in thwarting cyber threats. A notable instance involved a healthcare entity that successfully mitigated a ransomware attack by leveraging advanced firewall technologies to monitor and block suspicious traffic. This proactive strategy not only safeguarded patient care but also preserved the integrity of their systems.
Expert insights indicate that firewalls should be integrated throughout a company's internal systems rather than solely at the perimeter. This comprehensive approach enhances protection by segregating critical systems from general-purpose networks, thereby reducing the risk of cross-contamination during incidents. By implementing robust cyber security measures, medical facilities can significantly bolster their security posture and protect sensitive patient information from unauthorized access.
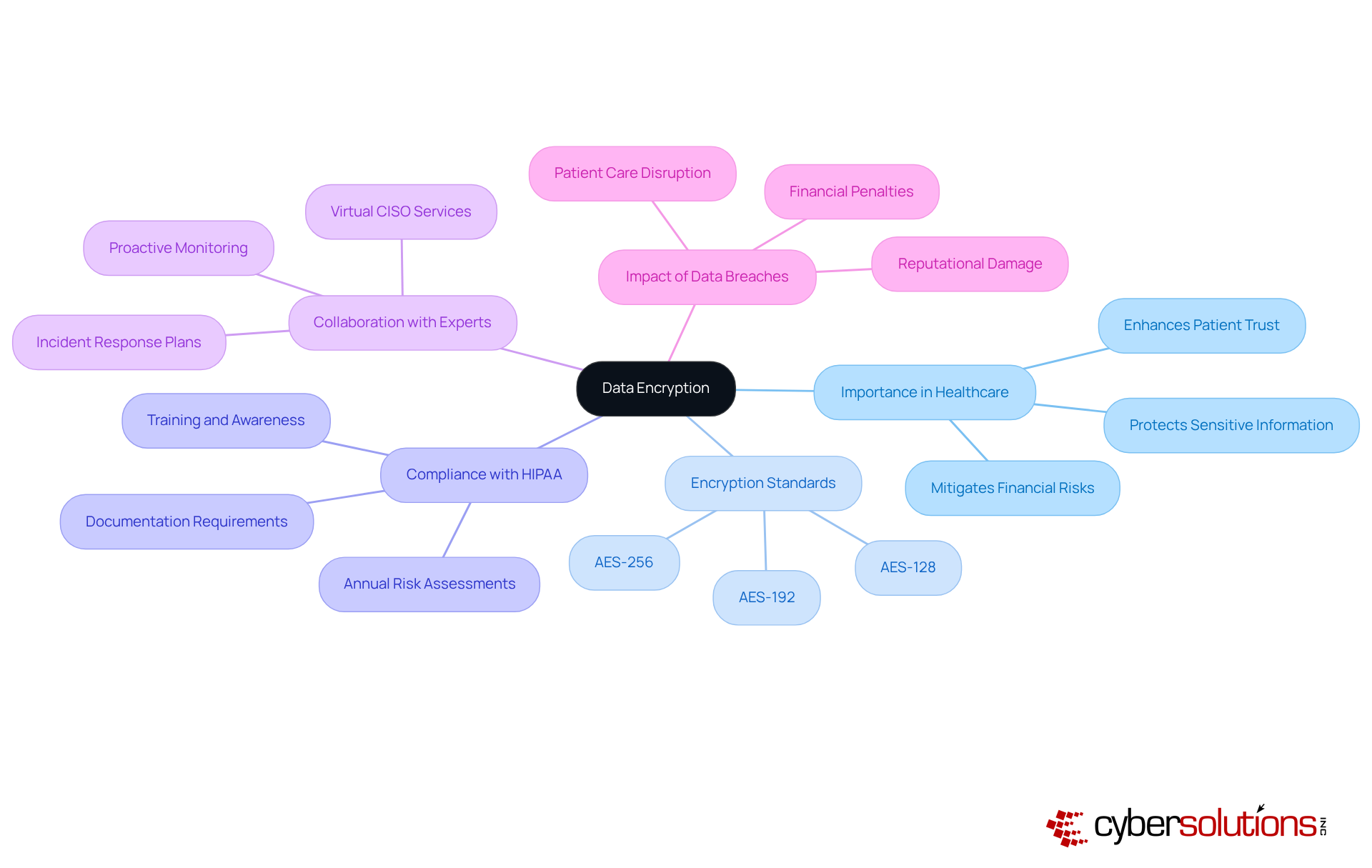
Data encryption stands as a pillar in safeguarding sensitive medical information, encompassing both data stored on servers and that transmitted across networks. The implementation of robust , such as AES-256, ensures that intercepted data remains inaccessible without the correct decryption keys. Notably, 53% of healthcare entities that had their data encrypted still paid ransoms to regain access, underscoring encryption's critical role as a primary defense mechanism and a vital cyber security measure against cyber threats.
Regular evaluations of encryption methods, coupled with annual risk assessments to identify weaknesses, are essential for compliance with regulations such as HIPAA, which mandates that electronic Protected Health Information (ePHI) be shielded from unauthorized access.
Collaborating with experts for comprehensive HIPAA compliance solutions, including virtual CISO services, empowers organizations to not only implement effective encryption but also to develop robust incident response plans. Proactive monitoring and reporting further enhance the effectiveness of a cyber security measure.
As the medical industry faces escalating cyber threats, prioritizing encryption not only protects patient information but also mitigates the risk of substantial financial penalties associated with data breaches.
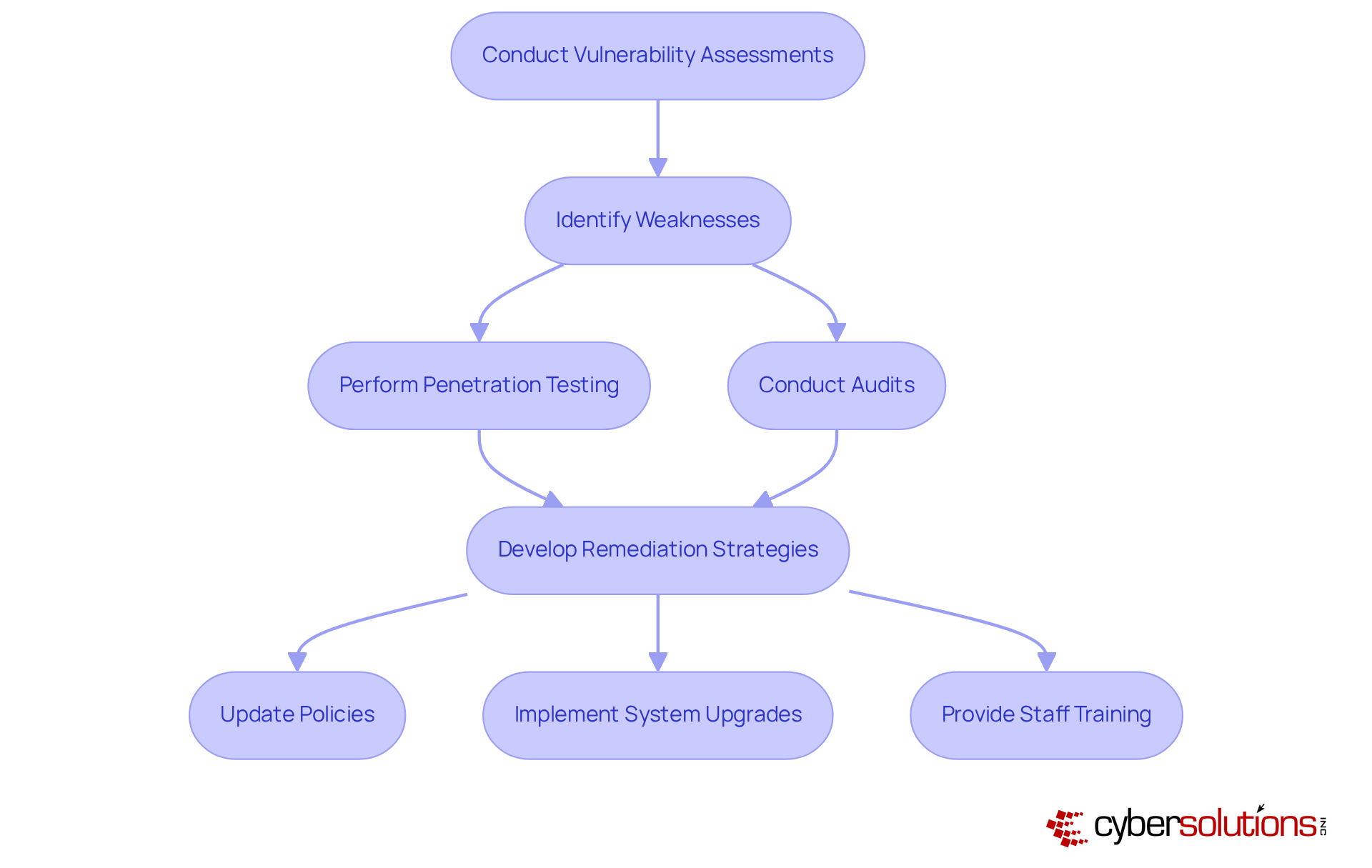
In today's rapidly evolving digital landscape, conducting regular vulnerability evaluations is not just advisable; it is essential for identifying and addressing weaknesses within healthcare IT systems. With the increasing frequency of cyber threats, healthcare organizations must prioritize these evaluations, which should include comprehensive and audits as a vital cyber security measure to assess the effectiveness of current protective measures.
Tailored remediation strategies must be implemented based on the findings of these assessments. This includes critical updates to policies and necessary system upgrades. By preparing thorough documentation, including robust security policies and procedures, entities can demonstrate their adherence to best practices during audits.
Moreover, addressing identified vulnerabilities promptly is vital. Providing staff training on recognizing suspicious emails and maintaining proper cybersecurity hygiene can significantly reduce the risk of a successful cyberattack. In an era where the stakes are high, proactive measures, including a strong cyber security measure, are the key to safeguarding sensitive information and ensuring the integrity of healthcare systems.
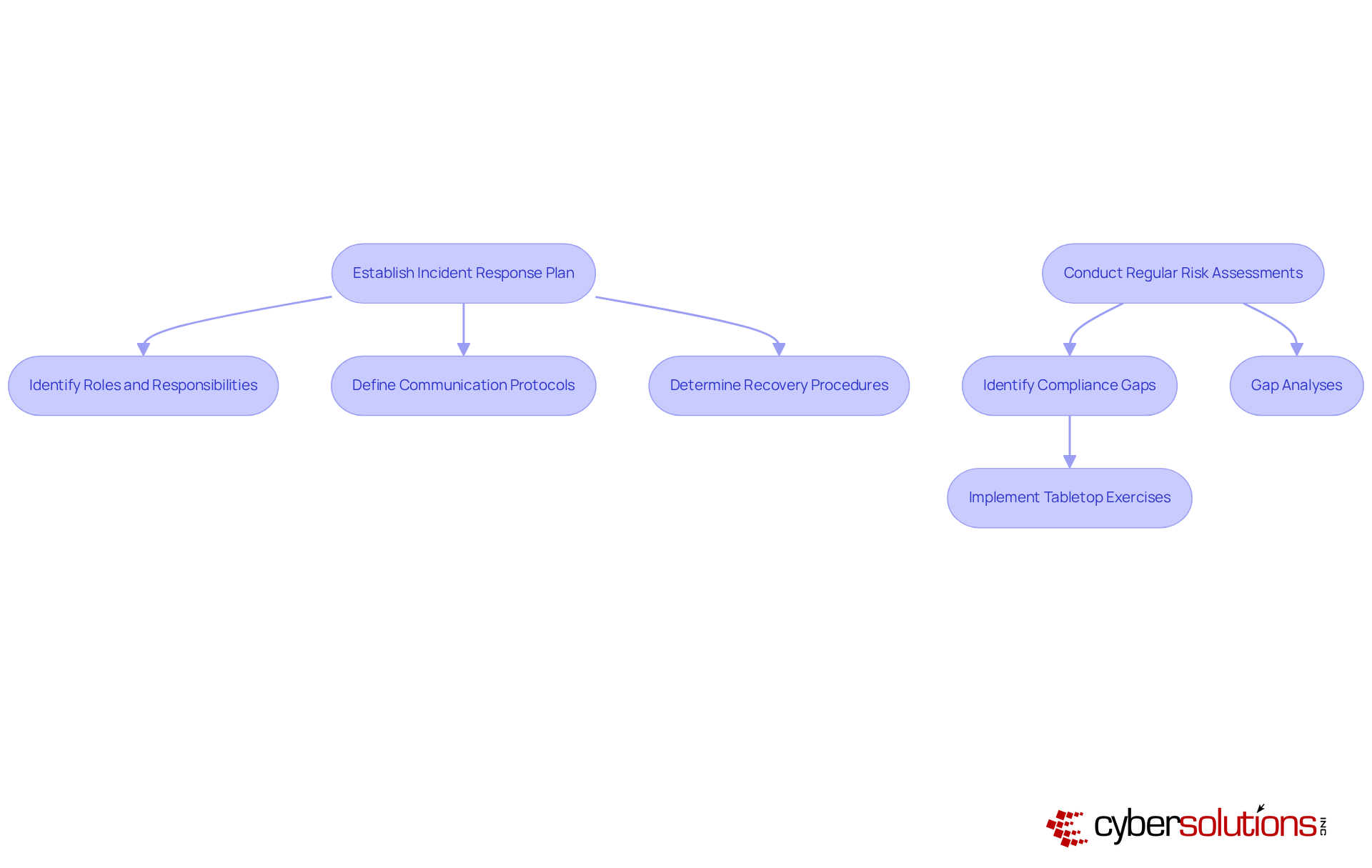
In today's healthcare landscape, the necessity of a robust incident response plan cannot be overstated. Every healthcare entity must establish and maintain a comprehensive plan that aligns with HIPAA standards. This plan should delineate the steps to follow in the event of a cybersecurity incident, including a cyber security measure that encompasses roles and responsibilities, communication protocols, and recovery procedures.
Proactive risk management strategies are essential; conducting regular risk assessments and gap analyses is crucial for identifying compliance gaps and vulnerabilities. By consistently evaluating and revising the plan, organizations ensure that all personnel are familiar with their responsibilities, enabling effective responses to incidents and minimizing potential harm.
Moreover, leveraging expert guidance through virtual CISO services can significantly enhance your incident response capabilities, ensuring your entity remains audit-ready and compliant with HIPAA requirements. To further fortify your incident response plan, implementing a as a cyber security measure to simulate a cybersecurity incident enables your team to practice their response in a controlled environment, thereby reinforcing their preparedness and confidence.
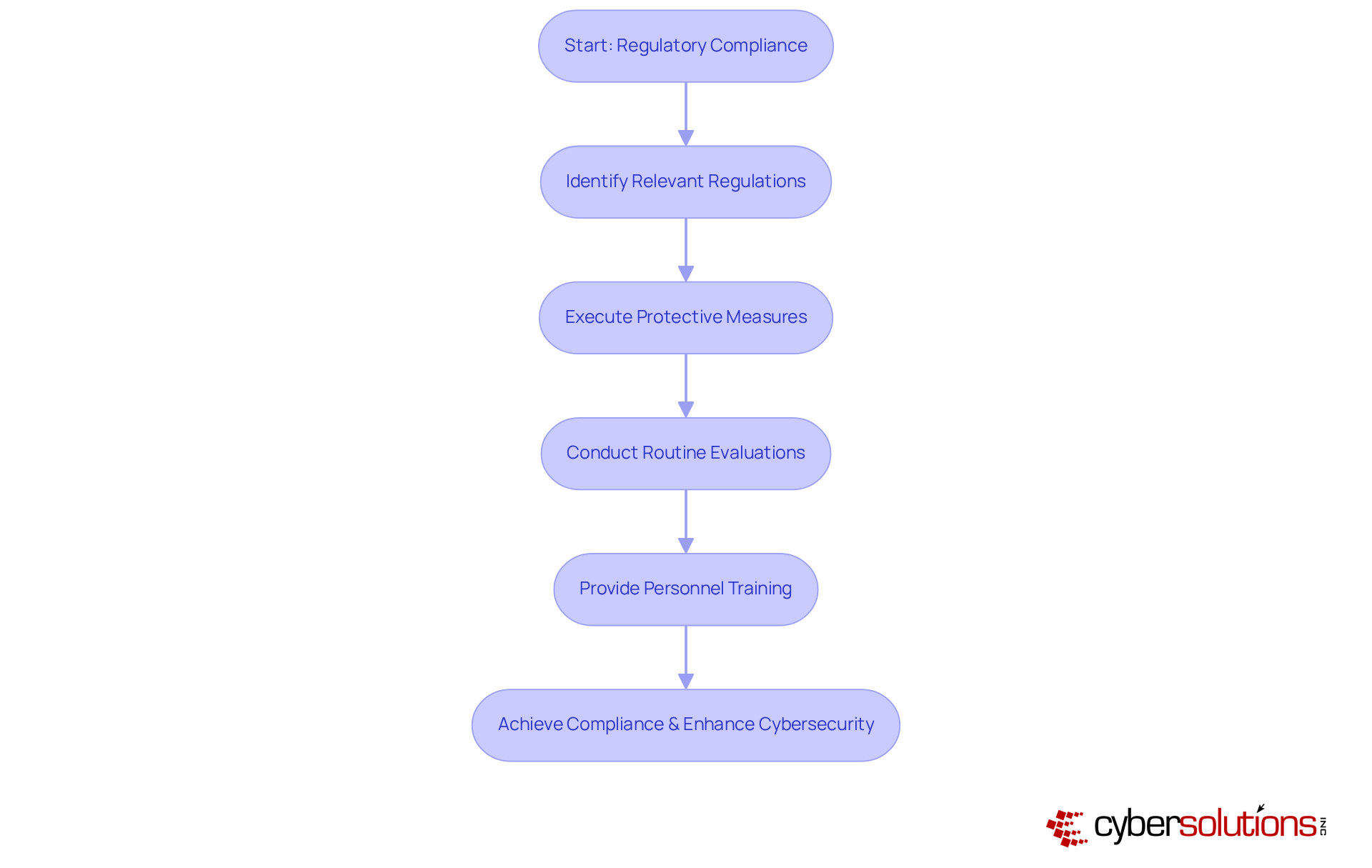
In today's rapidly evolving digital landscape, healthcare entities face unprecedented cybersecurity threats. It is imperative that they guarantee adherence to pertinent regulations, such as HIPAA, to safeguard sensitive patient information. This involves executing , conducting routine evaluations, and providing personnel instruction on regulatory obligations. At Cyber Solutions, we understand the unique challenges faced by CFOs in this environment.
Our comprehensive reporting and assistance ensure that businesses remain audit-ready, showcasing compliance with regulations while preserving operational integrity. By prioritizing regulatory compliance and investing in proactive security strategies, organizations not only avoid legal penalties but also enhance their overall cybersecurity posture with effective cyber security measures. Our tailored Managed IT and cybersecurity services offer flat-rate pricing that simplifies budgeting and eliminates unexpected IT expenses.
When organizations choose Cyber Solutions, they are not just investing in compliance; they are implementing a cyber security measure to ensure continuity of care and protect sensitive data. By addressing these critical challenges effectively, we empower healthcare entities to thrive in a secure environment. Are you ready to elevate your cybersecurity strategy and safeguard your organization’s future?
In the healthcare sector, the implementation of essential cybersecurity measures is not merely an option; it is a fundamental necessity for safeguarding sensitive patient information and ensuring compliance with regulations such as HIPAA. The pressing need for effective cybersecurity in healthcare cannot be overstated. As cyber threats continue to evolve, healthcare organizations must prioritize these measures to safeguard their operations and protect patient privacy.
CFOs in healthcare must adopt a comprehensive approach, emphasizing proactive strategies to mitigate cyber threats and enhance operational efficiency. Key strategies include:
Each of these measures plays a critical role in creating a robust cybersecurity framework that not only protects patient data but also fosters trust and reliability in healthcare services. By investing in comprehensive cybersecurity solutions and fostering a culture of awareness, healthcare CFOs can ensure their organizations are well-equipped to face the challenges of today’s digital landscape.
Taking decisive action now will pave the way for a secure future in healthcare, where patient safety and data integrity remain paramount.
What services does Cyber Solutions Inc. provide for the healthcare industry?
Cyber Solutions Inc. offers a comprehensive array of managed IT and cybersecurity services tailored for the medical industry, including 24/7 help desk support, endpoint protection, backup and disaster recovery, and advanced cybersecurity measures such as threat detection and incident response.
How does Cyber Solutions Inc. help healthcare organizations with compliance?
Cyber Solutions empowers medical institutions to ensure strict security and compliance with essential regulations like HIPAA through proactive risk management, audit support, and access to virtual CISO services, helping facilities remain audit-ready.
Why are strong password policies important in healthcare?
Strong password policies are essential for safeguarding sensitive medical data and ensuring HIPAA compliance. They help prevent cyber threats, such as credential stuffing, by enforcing the use of unique passwords that are complex and regularly updated.
What are the recommended practices for password management in medical institutions?
Organizations should enforce the use of unique passwords that are at least 12 characters long, utilize password managers to generate and securely store complex passwords, and train personnel on effective password management practices, including avoiding common passwords and regularly updating credentials.
Why are regular software updates crucial for cybersecurity in healthcare?
Regular software updates are vital to protect against cyberattacks, as they patch vulnerabilities in operating systems, applications, and security software. Automated update schedules help ensure timely patching, reducing the risk of exploitation by cybercriminals.
What consequences can arise from neglecting software updates in medical institutions?
Neglecting software updates can lead to serious consequences, such as data breaches, as seen in the incident at Northwest Medical Specialties. Additionally, many medical institutions lack a cyberattack contingency strategy, which can exacerbate the effects of cyber incidents.
How do software updates assist in maintaining compliance with regulations like HIPAA?
Frequent software updates help organizations maintain compliance with HIPAA by ensuring that they adhere to safety standards and are prepared for periodic audits, thereby protecting sensitive patient information and enhancing overall security posture.