September 10, 2025
.png)
In today's healthcare landscape, the importance of cybersecurity cannot be overstated. As regulatory demands grow increasingly complex, healthcare CFOs face unique challenges in safeguarding sensitive data while ensuring compliance. This article outlines seven key IT strategies that CFOs can implement to enhance compliance and protect sensitive data.
By focusing on proactive cybersecurity measures—such as:
CFOs can effectively align financial and compliance goals. These strategies not only mitigate cyber threats but also ensure adherence to critical regulations like HIPAA. In doing so, CFOs can foster a secure environment that prioritizes patient trust and organizational integrity.
In today's rapidly evolving healthcare landscape, the stakes for compliance and cybersecurity have never been higher. Medical organizations are under increased scrutiny and regulatory pressures, compelling CFOs to navigate a complex web of challenges while safeguarding sensitive patient data. This article delves into seven essential IT strategies that healthcare CFOs can adopt to enhance compliance and protect their organizations from emerging cyber threats. As the digital environment becomes fraught with risks, how can CFOs effectively align financial goals with robust cybersecurity measures to ensure resilience and trust in their institutions?
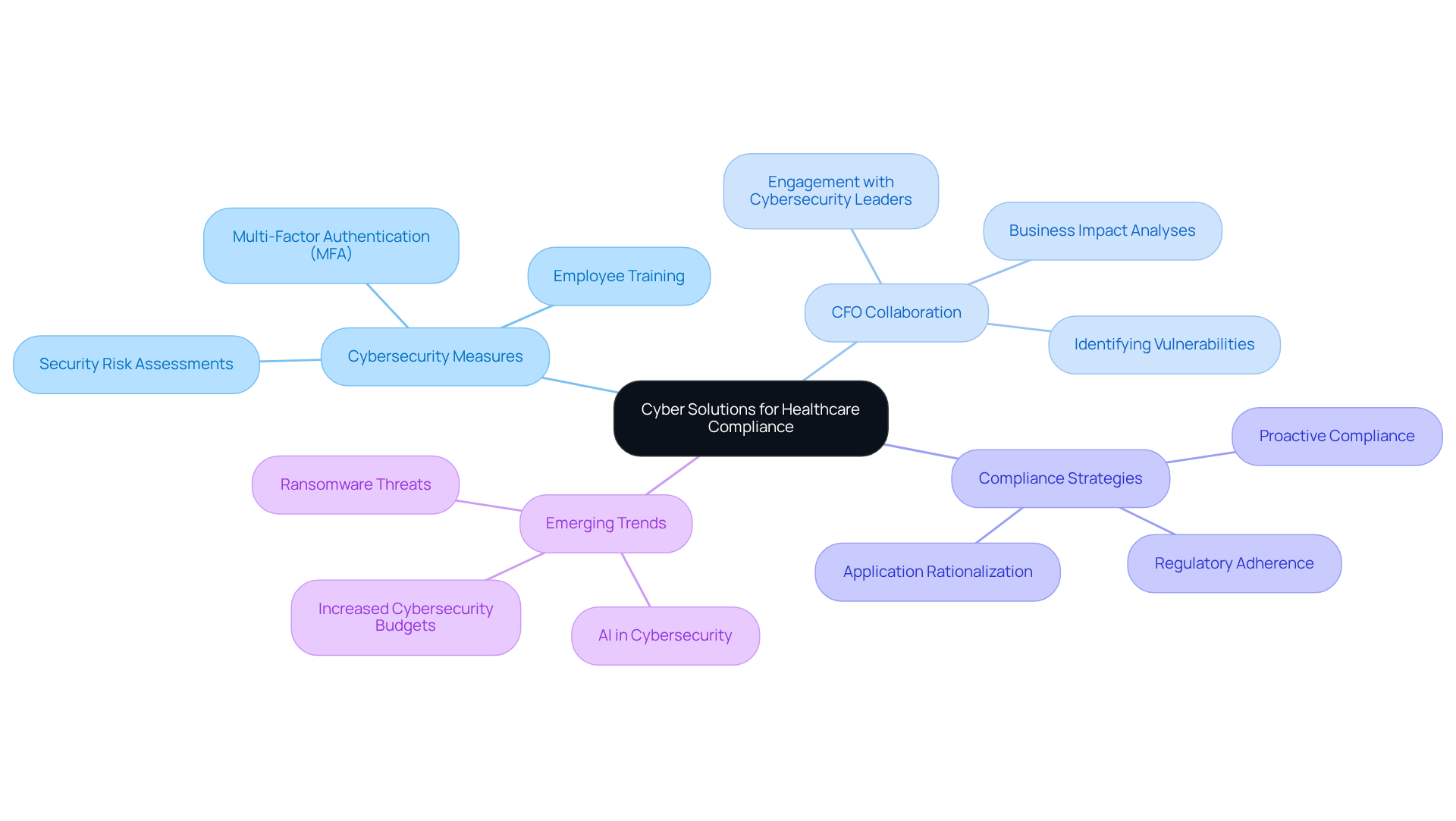
In today's healthcare landscape, the significance of robust cybersecurity measures cannot be overstated. Cyber Solutions Inc. excels in delivering tailored IT and cybersecurity services specifically crafted to fulfill the regulatory requirements of medical organizations. By maneuvering through the intricate regulatory environment, including HIPAA and other relevant standards, Cyber Solutions enables medical CFOs to oversee adherence effectively while focusing on their primary financial responsibilities. This thorough approach combines , incident response, and regulatory support as a service (CaaS), creating a robust framework that aligns effortlessly with financial goals.
As we look toward 2025, the importance of HIPAA adherence continues to escalate, with medical organizations facing intensified scrutiny and regulatory pressures. Successful compliance strategies involve:
How can CFOs ensure their organizations remain resilient in the face of evolving cyber threats? As noted by industry experts, fostering collaboration between CFOs and cybersecurity leaders is crucial for identifying vulnerabilities and enhancing organizational resilience against cyber threats.
Emerging trends in IT cybersecurity indicate that CFOs in the medical sector must prioritize application rationalization within their business IT strategies to optimize technology portfolios and address outdated systems that may not comply with current regulations. By utilizing advanced cybersecurity frameworks and collaborating with external specialists, entities can strengthen their defenses against increasingly sophisticated cyberattacks.
As CFOs in the medical sector navigate these challenges, insights from cybersecurity specialists highlight the significance of a proactive strategy for compliance. By aligning financial strategies with strong cybersecurity measures, medical institutions can enhance their business IT strategies to protect sensitive patient data and uphold trust in a changing digital environment.
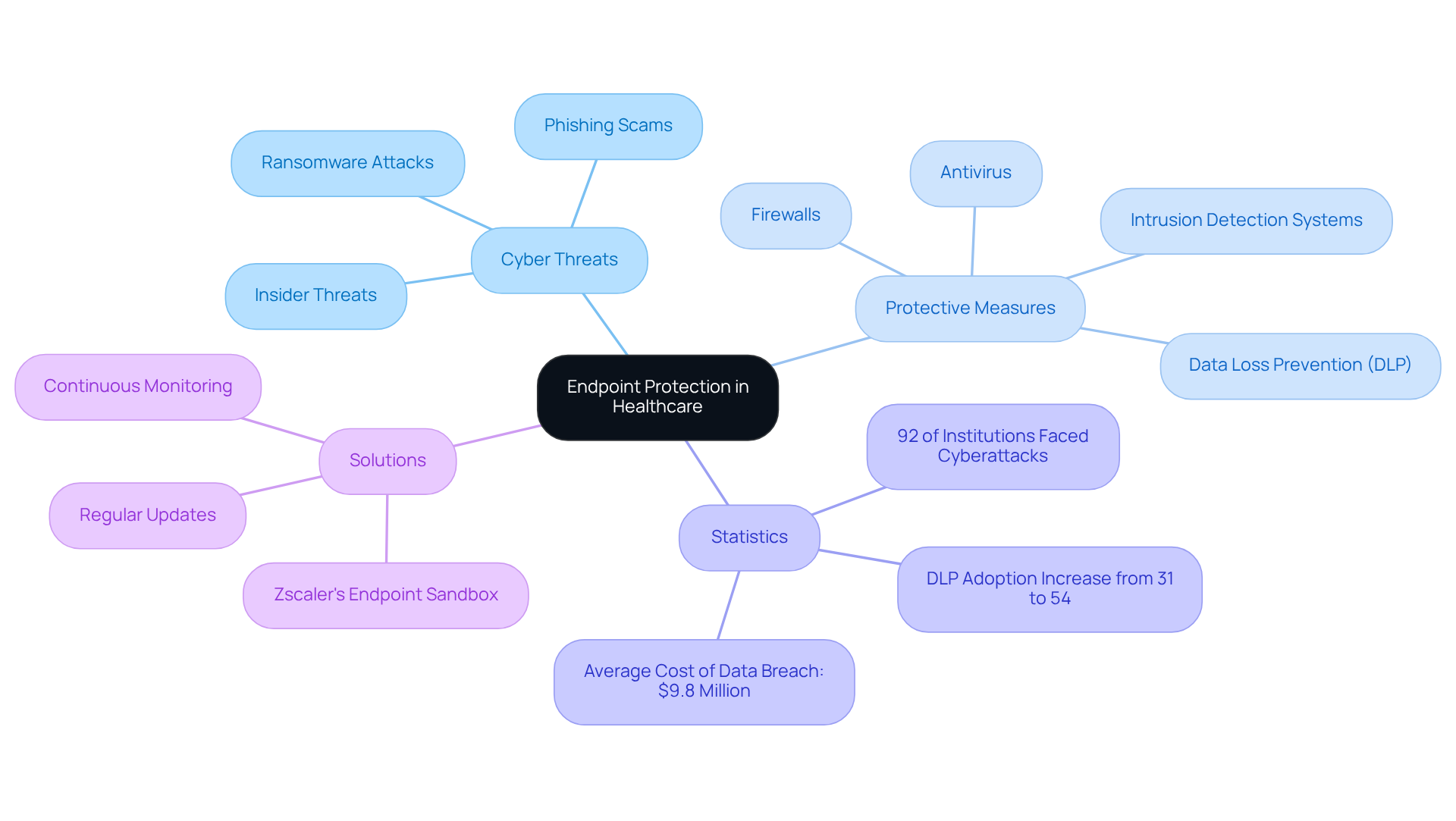
Endpoint protection solutions are paramount in safeguarding sensitive medical data against the ever-evolving landscape of cyber threats. As healthcare organizations face unprecedented challenges, the implementation of sophisticated protective measures—such as antivirus programs, firewalls, and intrusion detection systems—becomes essential. Medical institutions must efficiently secure endpoints, including computers, mobile devices, and medical apparatus, from unauthorized access and malware assaults. In 2025, the focus on endpoint protection has intensified, with a staggering 92% of medical institutions experiencing cyberattacks in the previous year. This alarming statistic underscores the urgent need for robust defenses.
Regular updates and continuous monitoring are vital in adapting to these evolving threats, ensuring compliance with regulatory standards like HIPAA. Notably, the adoption of Data Loss Prevention (DLP) policies within medical organizations has surged from 31% to 54%, reflecting a proactive approach to data protection. Such measures are not merely regulatory checkboxes; they signify a commitment to safeguarding patient information.
Successful implementations of endpoint security solutions, such as Zscaler's Endpoint Sandbox, empower IT teams in the medical sector to analyze files offline. This capability significantly introduced through common vectors like USB drives and external hard disks. These advancements not only bolster compliance but also contribute to a more resilient IT landscape in the medical field, reinforcing the imperative for healthcare organizations to prioritize cybersecurity.
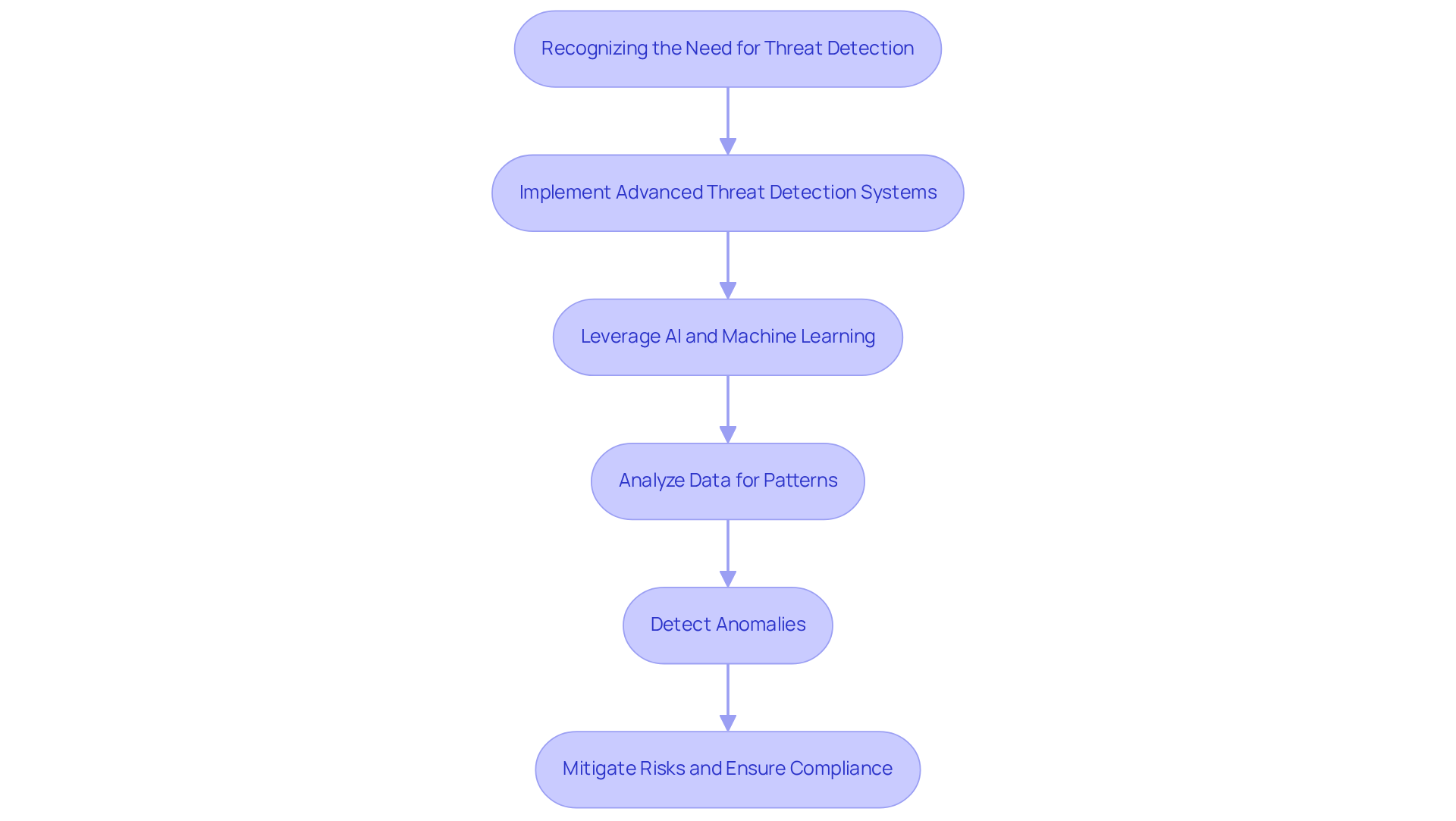
Implementing advanced threat detection systems is not just beneficial but essential for medical organizations aiming to identify and respond to cyber threats in real-time. The landscape of cybersecurity threats is evolving rapidly, with reaching a staggering 1,160 incidents in 2024 alone. This alarming statistic underscores the urgent need for proactive measures. By leveraging artificial intelligence and machine learning, these systems can analyze vast amounts of data, recognizing patterns and detecting anomalies that may signal a security breach.
Investing in these technologies mitigates the risk of costly data breaches—averaging over $9.77 million per incident—while ensuring compliance with stringent regulatory requirements. Cybersecurity leaders emphasize that a proactive approach to threat detection is crucial for protecting sensitive patient information and maintaining trust in medical systems. As the threat landscape continues to evolve, the integration of AI-driven solutions will play a pivotal role in enhancing the security posture of healthcare entities. This enables them to stay ahead of potential risks and safeguard their operational integrity.
In conclusion, the imperative for healthcare organizations is clear: adopting advanced threat detection systems is not merely a technical upgrade but a strategic necessity. By doing so, they can effectively combat the rising tide of cyber threats, ensuring both the safety of patient data and the trust of the communities they serve.
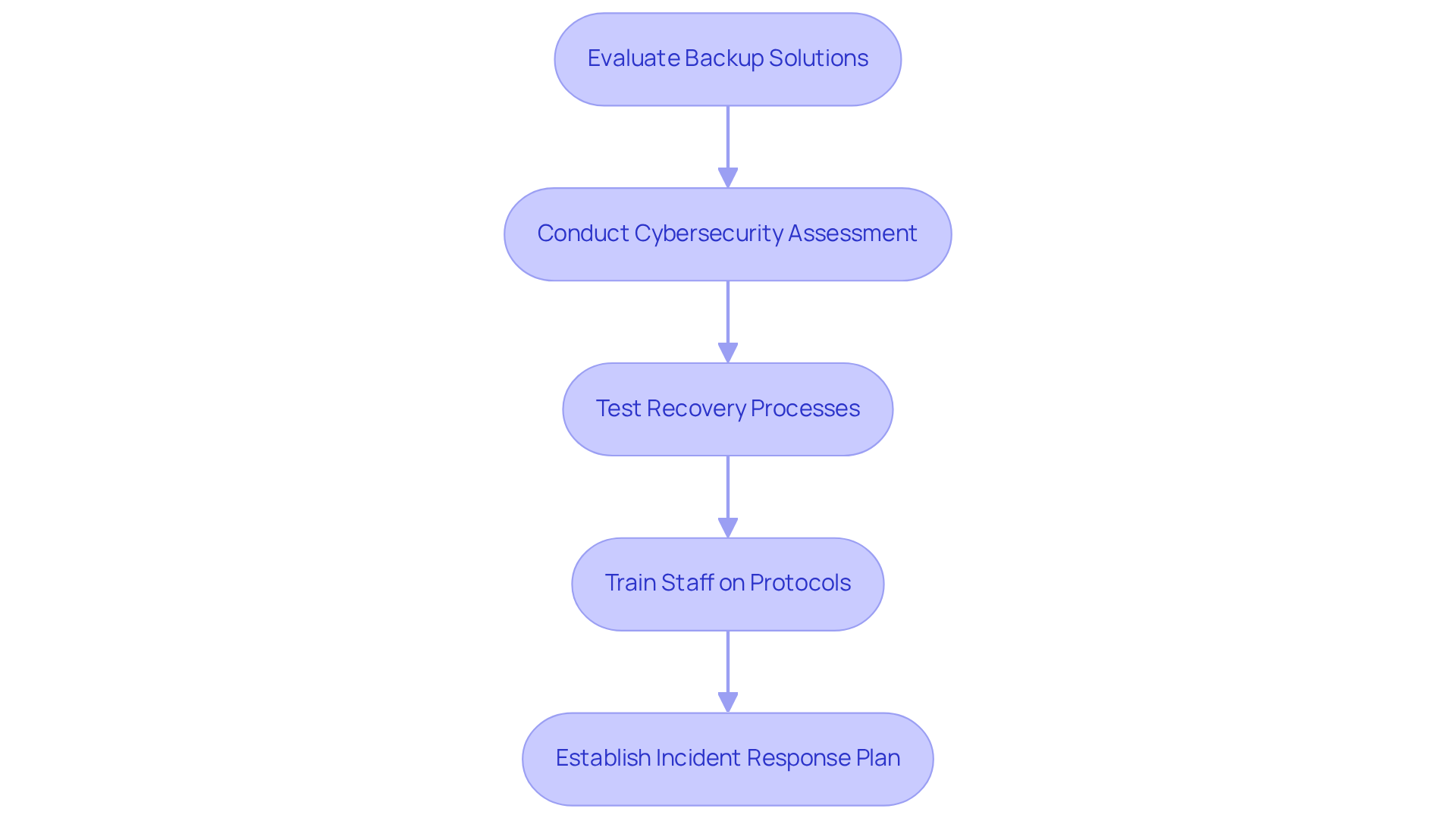
Healthcare institutions must prioritize the implementation of robust backup and disaster recovery plans to safeguard sensitive data against cyberattacks, natural disasters, and system failures. In today's landscape, where threats are ever-evolving, the need for regular backups—both on-site and in secure, HIPAA-compliant cloud environments—is paramount. This proactive approach is essential for ensuring that critical patient information can be swiftly restored following any data loss incident, thereby protecting data integrity and aligning with compliance requirements that mandate effective data protection and recovery protocols. Looking ahead to 2025, adherence to updated regulations will be crucial; non-compliance can result in significant penalties.
Conducting a comprehensive cybersecurity assessment and gap analysis allows entities to identify vulnerabilities and implement tailored remediation strategies, including policy updates and system upgrades. Specific steps may include:
Establishing comprehensive disaster recovery strategies not only enhances operational resilience but also ensures continuity of care, thereby maintaining trust with patients.
Moreover, having a swift incident response plan in place can greatly enhance recovery times and mitigate damage in the event of a ransomware attack. This underscores the significance of specialized expertise and in protecting medical operations. In a world where data breaches are increasingly common, the time to act is now.
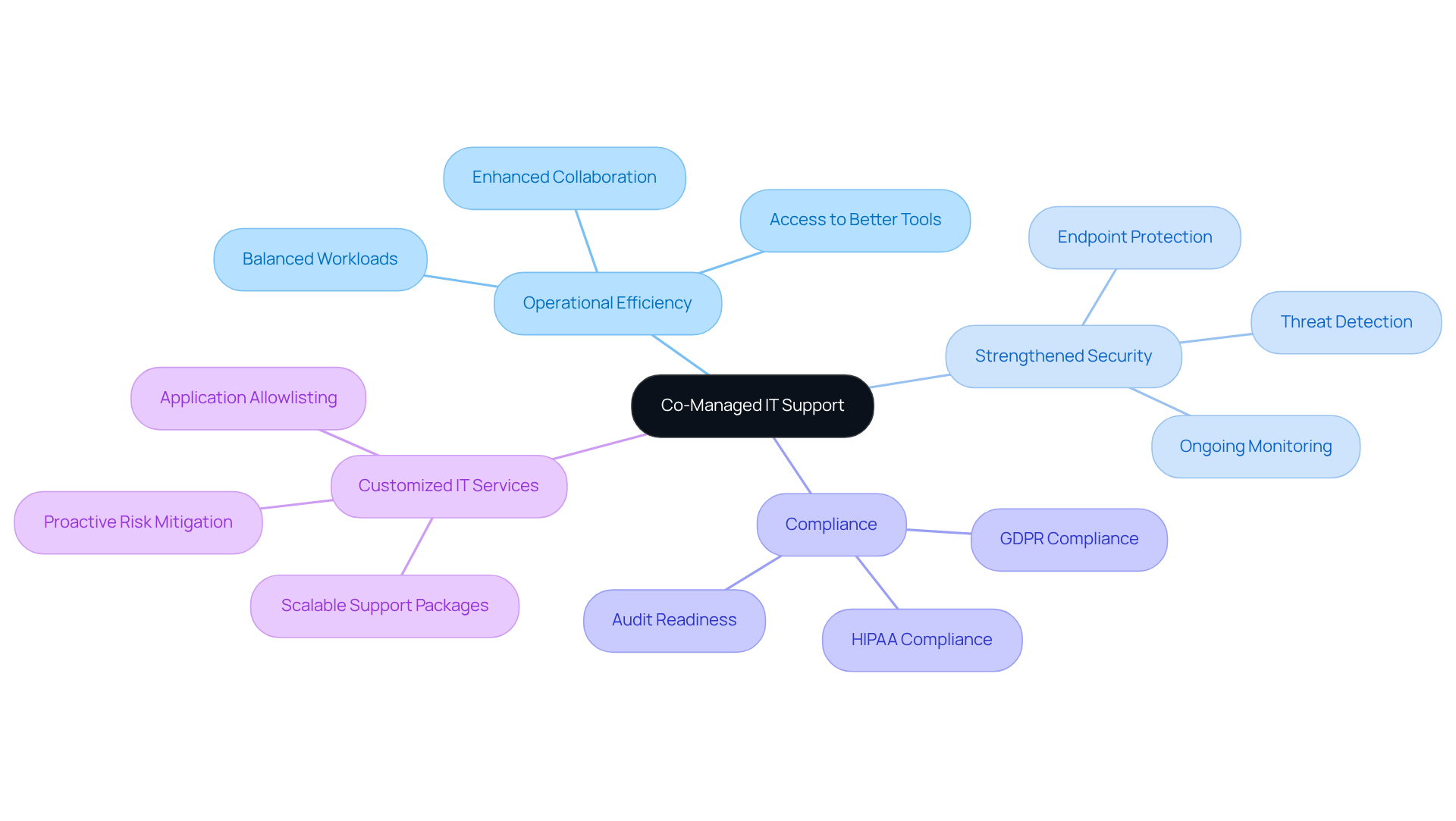
Co-managed IT support is crucial for empowering medical organizations, as it merges the expertise of internal IT teams with the specialized knowledge of external managed service providers. This collaboration not only enhances operational efficiency but also strengthens security measures and ensures compliance with industry regulations. By distributing responsibilities, financial executives in the medical sector can concentrate on strategic financial planning while maintaining a robust IT infrastructure.
Customized IT services—such as application allowlisting, endpoint protection, and threat detection—proactively mitigate risks by preventing malware and unauthorized software from executing. This significantly reduces vulnerabilities and aids organizations in adhering to stringent like HIPAA and GDPR.
Successful collaborations demonstrate that shared objectives and transparent communication yield improved outcomes, ultimately benefiting patient care and operational stability. In an era where cybersecurity threats are pervasive, leveraging co-managed IT support is not just an option; it is a necessity for healthcare organizations aiming to protect their data and ensure compliance.
In today's complex regulatory landscape, Compliance as a Service (CaaS) emerges as a vital solution for medical institutions navigating intricate compliance requirements. By outsourcing regulatory tasks to specialized providers like Cyber Solutions, organizations can effectively manage evolving regulations such as HIPAA and GDPR. CaaS encompasses a range of services including:
This empowers healthcare CFOs to concentrate on financial management while ensuring robust regulatory adherence.
The necessity for regular privacy audits, supported by advanced technology, cannot be overstated. Continuous adherence monitoring and real-time notifications are essential components of CaaS, significantly mitigating risks associated with non-conformity. This systematic approach involves a thorough evaluation of a client's regulatory environment, identifying deficiencies, and enabling firms to allocate resources more effectively.
As the demand for clarity and protection intensifies, CaaS stands out as a strategic solution for healthcare organizations striving to streamline their compliance processes and maintain a competitive edge in a rapidly changing environment. Moreover, with the added benefit of , CaaS ensures that healthcare entities are well-equipped for any upcoming audits, reinforcing their commitment to compliance and safety.

In today’s healthcare landscape, cybersecurity is not just an option; it is a necessity. Healthcare organizations must prioritize the development and implementation of robust incident response plans to effectively address cyber incidents. These plans should outline explicit procedures for:
Ensuring a swift and coordinated response is crucial. Training all staff in is essential; this not only minimizes the operational impact of cyber incidents but also helps maintain compliance with regulatory requirements.
As cyber threats evolve, organizations are urged to adopt a zero trust architecture (ZTA) to enhance security measures. This approach requires verifying every user and device before granting access, thereby strengthening defenses against potential breaches. Regular incident response training, including tabletop exercises that simulate multi-vector attacks, can significantly bolster preparedness and response capabilities. Such proactive measures are not merely best practices; they are vital to safeguarding sensitive patient information and ensuring operational continuity.
Successful strategies implemented in hospitals have demonstrated that proactive planning and continuous staff education are key to mitigating risks. By fostering a culture of awareness and preparedness, healthcare organizations can navigate the increasingly complex threat landscape while ensuring patient safety. The time to act is now—prioritize cybersecurity to protect what matters most.
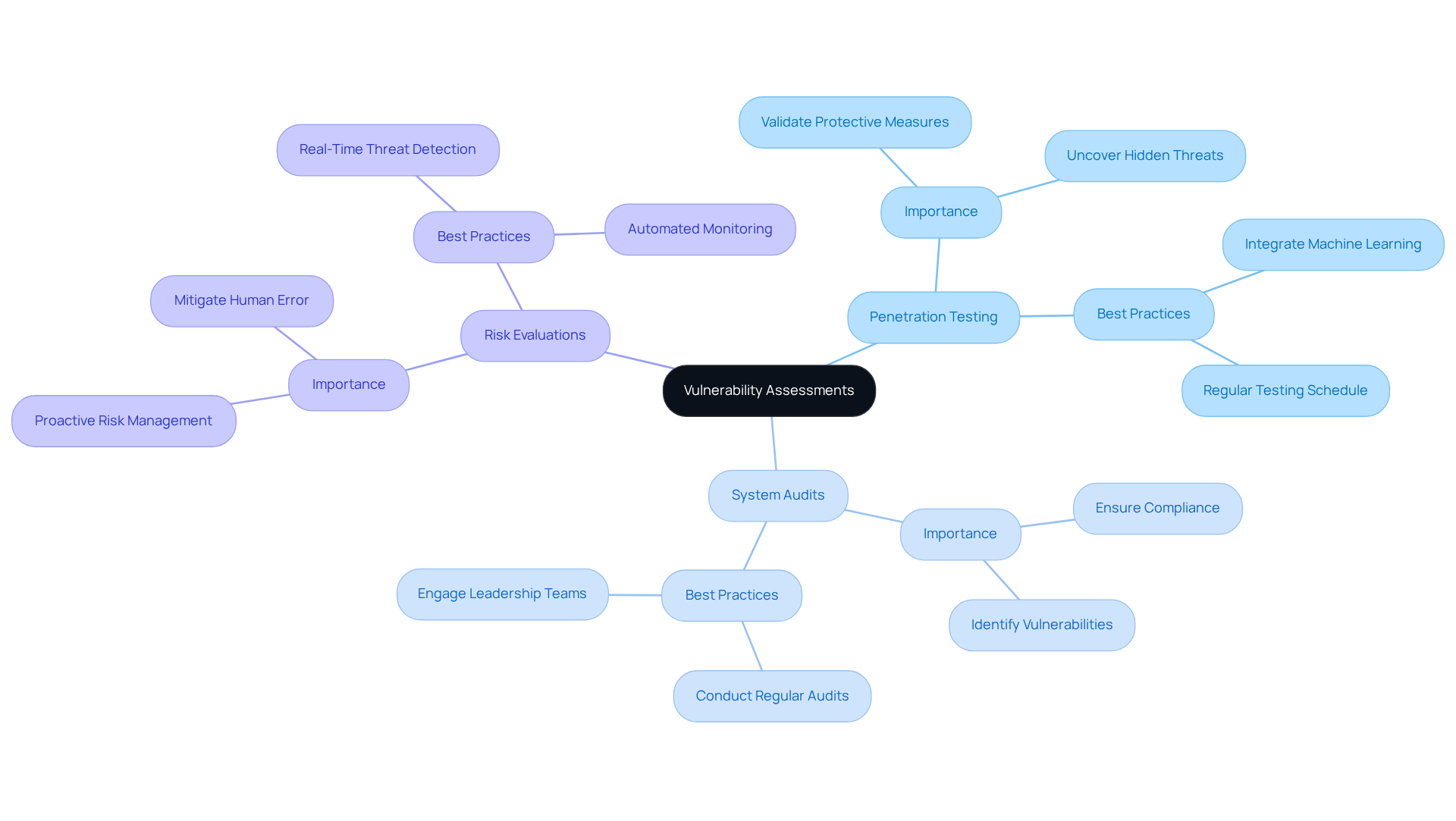
In today's digital age, routine vulnerability evaluations are not just beneficial but essential for medical institutions aiming to proactively identify and mitigate weaknesses before cybercriminals exploit them. These assessments must encompass:
Ensuring that all potential vulnerabilities are rigorously examined and addressed. As we look ahead to 2025, the emphasis on penetration testing has intensified, with medical entities recognizing its critical role in uncovering hidden threats and validating protective measures.
Best practices now advocate for the integration of advanced machine learning tools to analyze user behaviors and detect anomalies, significantly enhancing the effectiveness of vulnerability testing. By prioritizing these assessments, financial leaders in the medical field can substantially bolster their entity's security posture, ensure compliance with industry regulations, and ultimately protect sensitive patient information amidst an increasingly perilous threat landscape. The time to act is now—are you prepared to against emerging cyber threats?
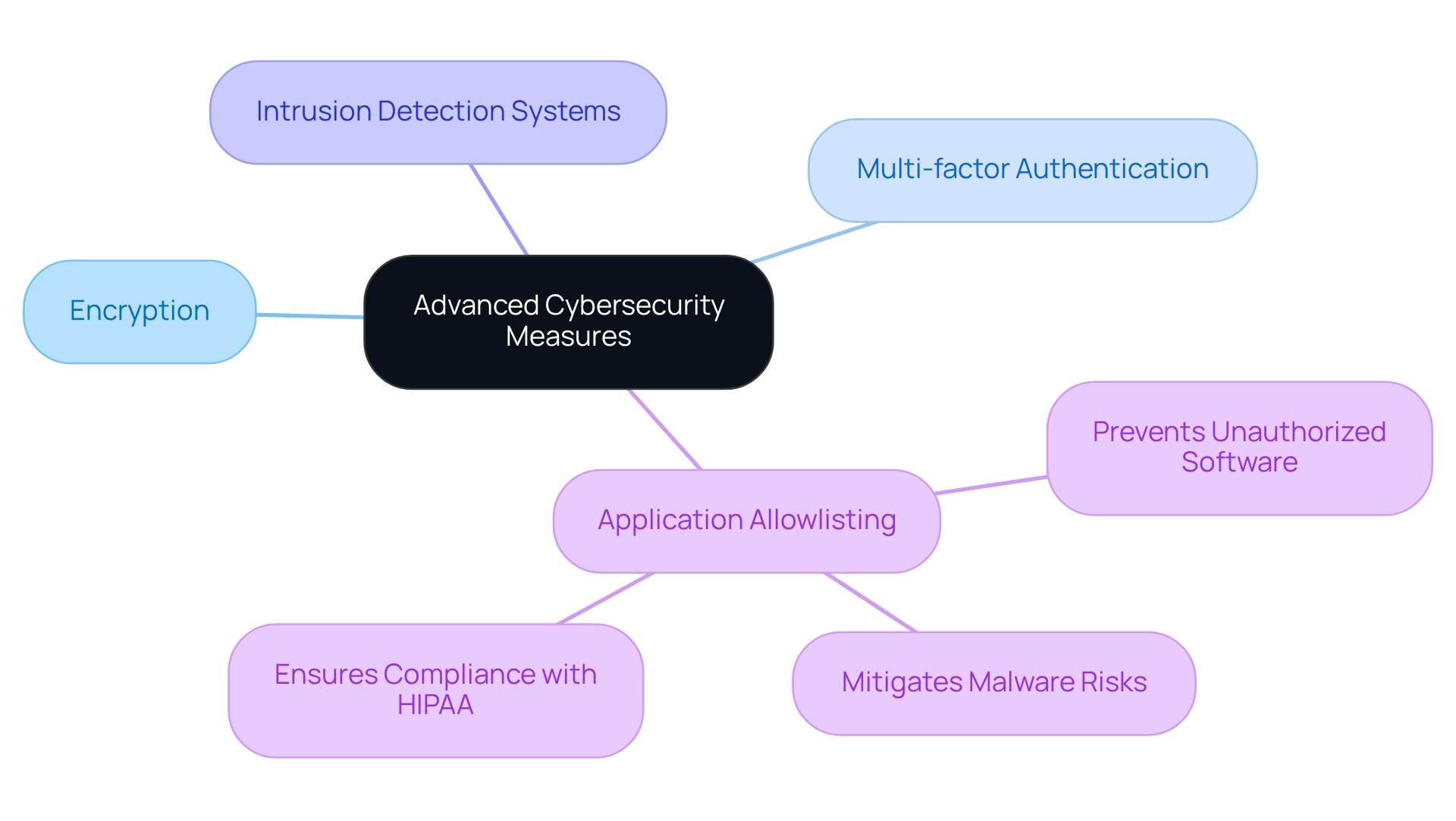
In today's digital landscape, safeguarding sensitive healthcare data is paramount. Entities must implement advanced cybersecurity measures, including:
Among these, application allowlisting stands out as a critical strategy, proactively preventing unauthorized or malicious software from executing. This significantly , ransomware, and zero-day attacks, thereby reducing vulnerabilities.
Moreover, application allowlisting aids organizations in meeting stringent compliance standards, such as those mandated by HIPAA. By continuously monitoring application activity and permitting only approved software to operate, it not only enhances security but also streamlines management through centralized control. For CFOs in the medical sector, investing in advanced cybersecurity solutions—especially application allowlisting—is essential. It not only protects their entities from potential breaches but also demonstrates a commitment to regulatory compliance, reinforcing their credibility in a challenging environment.
As cybersecurity threats evolve, the implications for healthcare organizations become increasingly severe. The stakes are high, and the cost of inaction could be catastrophic. By prioritizing robust cybersecurity measures, healthcare leaders can fortify their defenses and ensure the integrity of sensitive data, ultimately fostering trust and reliability within their organizations.
In today's healthcare landscape, continuous staff training and awareness initiatives are paramount for equipping employees with the skills necessary to recognize and effectively address cybersecurity threats. Essential topics such as:
must be integral components of these training programs. By fostering a culture of safety awareness, medical institutions can significantly mitigate the risk of cyber incidents and bolster their compliance posture.
Successful awareness campaigns in 2025 have clearly demonstrated a marked reduction in cyber incidents within hospitals, underscoring the critical role of ongoing education and engagement. As cyber threats continue to evolve, healthcare organizations must adapt their training programs to reflect current trends and challenges. This ensures that all employees remain well-informed and prepared to protect sensitive patient information.
This not only enhances security but also builds trust with patients, showcasing a steadfast commitment to safeguarding their data. The implications are clear: investing in continuous training is not merely a regulatory requirement but a strategic imperative that can lead to substantial improvements in both security and patient confidence.

In today's increasingly complex healthcare environment, the imperative for effective IT strategies that enhance compliance and protect sensitive data has reached unprecedented levels. This article delineates essential strategies for healthcare CFOs, underscoring the necessity of integrating robust cybersecurity measures with financial management. By prioritizing compliance, organizations not only meet regulatory standards but also cultivate trust with patients, thus ensuring a secure operational framework.
Key insights include:
Moreover, the collaboration between CFOs and cybersecurity experts emerges as a vital element in identifying vulnerabilities and strengthening defenses. The adoption of advanced technologies, such as artificial intelligence for threat detection and Compliance as a Service (CaaS) for streamlined regulatory adherence, exemplifies the proactive measures essential for navigating the evolving landscape of healthcare compliance.
Ultimately, the message is unequivocal: healthcare organizations must take decisive action to enhance their cybersecurity posture. By investing in comprehensive IT strategies, including incident response plans and vulnerability assessments, CFOs can safeguard sensitive patient information and ensure adherence to industry standards. The time to prioritize cybersecurity is now; it transcends a mere technical necessity and stands as a strategic imperative that will shape the future of healthcare operations.
What services does Cyber Solutions Inc. provide for healthcare organizations?
Cyber Solutions Inc. offers tailored IT and cybersecurity services designed to meet the regulatory requirements of medical organizations, including proactive monitoring, incident response, and regulatory support as a service (CaaS).
Why is HIPAA adherence important for medical organizations?
HIPAA adherence is crucial as it ensures the protection of sensitive patient data and helps medical organizations comply with regulatory standards, especially in a landscape facing increased scrutiny and regulatory pressures.
What strategies can CFOs implement to enhance cybersecurity in their organizations?
CFOs can enhance cybersecurity by enforcing Multi-Factor Authentication (MFA), conducting regular security risk assessments, and providing ongoing employee cybersecurity training to mitigate risks.
What is the significance of collaboration between CFOs and cybersecurity leaders?
Collaboration between CFOs and cybersecurity leaders is essential for identifying vulnerabilities and enhancing organizational resilience against evolving cyber threats.
What emerging trends should CFOs in the medical sector prioritize?
CFOs should prioritize application rationalization within their IT strategies to optimize technology portfolios and address outdated systems that may not comply with current regulations.
What role does endpoint protection play in healthcare cybersecurity?
Endpoint protection is vital for safeguarding sensitive medical data by securing endpoints like computers, mobile devices, and medical apparatus from unauthorized access and malware attacks.
How has the adoption of Data Loss Prevention (DLP) policies changed in medical organizations?
The adoption of DLP policies in medical organizations has increased from 31% to 54%, reflecting a proactive approach to data protection.
What are the benefits of implementing advanced threat detection systems in healthcare?
Advanced threat detection systems help medical organizations identify and respond to cyber threats in real-time, mitigating the risk of costly data breaches and ensuring compliance with regulatory requirements.
How can artificial intelligence and machine learning enhance threat detection in healthcare?
AI and machine learning can analyze vast amounts of data to recognize patterns and detect anomalies, which helps identify potential security breaches and enhances the overall security posture of healthcare entities.
What is the financial impact of data breaches on medical organizations?
The average cost of a data breach for medical organizations exceeds $9.77 million per incident, highlighting the importance of investing in cybersecurity measures to protect sensitive patient information.