
In today's rapidly evolving digital landscape, the significance of cybersecurity cannot be overstated, particularly for C-suite leaders. As organizations face increasingly sophisticated threats, the need for robust security solutions becomes paramount. Security as a Service (SECaaS) offers a compelling response, providing tailored solutions that enhance cybersecurity through cost-effectiveness and expert support.
By leveraging advanced technologies and continuous updates, SECaaS empowers organizations to significantly bolster their security posture. Collaborative partnerships further enhance operational efficiency while ensuring compliance with regulatory standards. This approach not only addresses immediate security concerns but also maximizes return on investment, making it an essential strategy for forward-thinking leaders.
As the cybersecurity landscape continues to evolve, the implications for organizations are profound. C-suite leaders must navigate these challenges with confidence, knowing that SECaaS can provide the necessary tools and expertise to safeguard their operations. By adopting this innovative model, organizations position themselves to thrive in an increasingly complex environment, ultimately securing their future against potential threats.
In an era where cyber threats are evolving at an unprecedented pace, the importance of robust cybersecurity measures cannot be overstated. For C-suite leaders, understanding the myriad benefits of Security as a Service (SECaaS) is crucial—not only for safeguarding their organizations but also for driving operational efficiency and financial success. This article delves into ten compelling advantages of SECaaS, revealing how tailored cloud solutions can enhance security, streamline compliance, and ultimately empower businesses to thrive in a digital-first world. As organizations navigate the complexities of modern cybersecurity, one must consider: how can embracing SECaaS transform their approach to risk management and resilience?
In today's digital landscape, cybersecurity is not just an option; it’s a necessity for healthcare organizations. excels in delivering customized tailored to the specific needs of contemporary businesses. By leveraging advanced technologies and extensive industry knowledge, the company empowers organizations to concentrate on their core operations while ensuring robust protective measures are firmly in place. This personalized approach not only strengthens security protocols but also aligns seamlessly with the financial objectives of businesses, facilitating in an increasingly regulated environment.
Central to Cyber Solutions' offerings is , a critical feature that ensures suspicious activities are detected and neutralized before they escalate into serious threats. This safeguards businesses from ransomware, phishing, and various malware attacks, significantly and data protection. Organizations that have embraced security as a service cloud, particularly in the healthcare and finance sectors, report against cyberattacks, enabling them to maintain trust with clients and stakeholders.
Industry leaders emphasize the vital importance of . As Ronak Massand, CEO of Adaptive, aptly states, "Data is the most critical asset that must be protected," highlighting that tailored solutions are essential for . By focusing on specific vulnerabilities and compliance requirements, customized protective services not only enhance safety but also streamline business processes, empowering companies to thrive in a digital-first environment.
A fundamental advantage of is its inherent scalability, which is crucial for organizations experiencing growth. As companies expand, their security requirements become increasingly complex, necessitating a . Security-as-a-Service solutions are designed to evolve alongside business operations, allowing organizations to adjust their protective measures seamlessly in response to emerging threats. This adaptability not only safeguards sensitive data but also removes the necessity for , rendering it a financially prudent option.
Data reveals that the global is anticipated to surge from $12.4 billion in 2021 to $23.8 billion by 2026, reflecting a compound annual growth rate (CAGR) of 13.8%. This expansion is driven by the , particularly among small and medium-sized enterprises (SMEs) that are modernizing their operations. For example, organizations utilizing SECaaS have reported with regulatory standards, illustrating the effectiveness of these solutions in adapting to shifting security needs.
Experts emphasize that as companies grow, integrating advanced risk detection and response capabilities becomes imperative. Continuous monitoring guarantees that suspicious activities are identified and mitigated before they escalate into threats, thereby protecting businesses against ransomware, phishing, and other forms of malware attacks. A (vCISO) can provide strategic oversight without the expense of a full-time employee, further showcasing how security as a service cloud can meet the evolving demands of expanding organizations. Additionally, the encompasses vital components such as endpoint isolation, malware eradication, and user education, which are essential for maintaining robust security frameworks. By adopting a security as a service cloud, organizations can ensure that their protective systems remain resilient and agile, shielding their operations from the challenges posed by contemporary cyber threats.
In today's digital landscape, cybersecurity is not just a necessity; it is a aiming to safeguard their assets and reputation. Protection as a Service presents a financially prudent approach for companies seeking to bolster their cybersecurity measures without incurring the substantial costs typical of traditional safety frameworks. By adopting , organizations can benefit from , facilitating more effective budget management.
This strategic transition not only enhances financial planning but also maximizes through reduced downtime and improved operational efficiency. Statistics reveal that businesses utilizing security as a service cloud can achieve significant cost savings while accessing expert protective resources. For instance, firms that have embraced this model report an average ROI of 4.1 times their investment, underscoring the .
Moreover, organizations can swiftly scale their security measures, adapting to emerging threats without the additional costs associated with on-premises solutions. Real-world examples illustrate the efficacy of Security as a Service in optimizing ROI. Companies like SCA Security have successfully collaborated with sales development firms to enhance operational efficiency, leading to a and a steady pipeline of opportunities. This collaboration not only refined their sales processes but also empowered their Account Executives (AEs) to concentrate on closing deals rather than prospecting, thereby optimizing resource allocation.
In conclusion, security as a service cloud not only delivers but also enables enterprises to reap . This makes it an essential consideration for C-suite executives focused on and ensuring long-term operational success.
Proactive risk detection is not just beneficial; it is essential to Service as a Solution (SECaaS). This approach empowers providers to leverage , enabling them to recognize and address potential threats before they escalate into serious safety incidents. The advantages of this proactive stance are twofold: it not only fortifies a company's overall defense posture but also significantly reduces the . For instance, entities utilizing report a remarkable 62% reduction in incidents annually, underscoring the tangible benefits of early threat identification.
Experts in the field stress the critical role of real-time monitoring. Cybersecurity professionals assert that constant vigilance allows organizations to swiftly detect anomalies and unauthorized access attempts, thereby bolstering operational resilience. The statistics speak volumes: the average response time for MDR services is approximately three hours, in stark contrast to the 66 hours typically required by in-house security teams. This discrepancy highlights the efficiency gained through outsourcing.
Recent trends in cybersecurity further underscore the necessity of real-time monitoring. With the , organizations are increasingly recognizing the significance of . This shift is driven by the urgent need for effective , especially as cyber threats continue to evolve.
Practical examples illustrate the effectiveness of real-time monitoring in enhancing safety. Healthcare organizations, for instance, have fortified the protection of electronic health records through continuous monitoring. This not only safeguards sensitive information but also ensures . As entities navigate the complexities of modern cyber threats, is crucial for protecting their assets and maintaining operational integrity. and consider to strengthen their security posture.
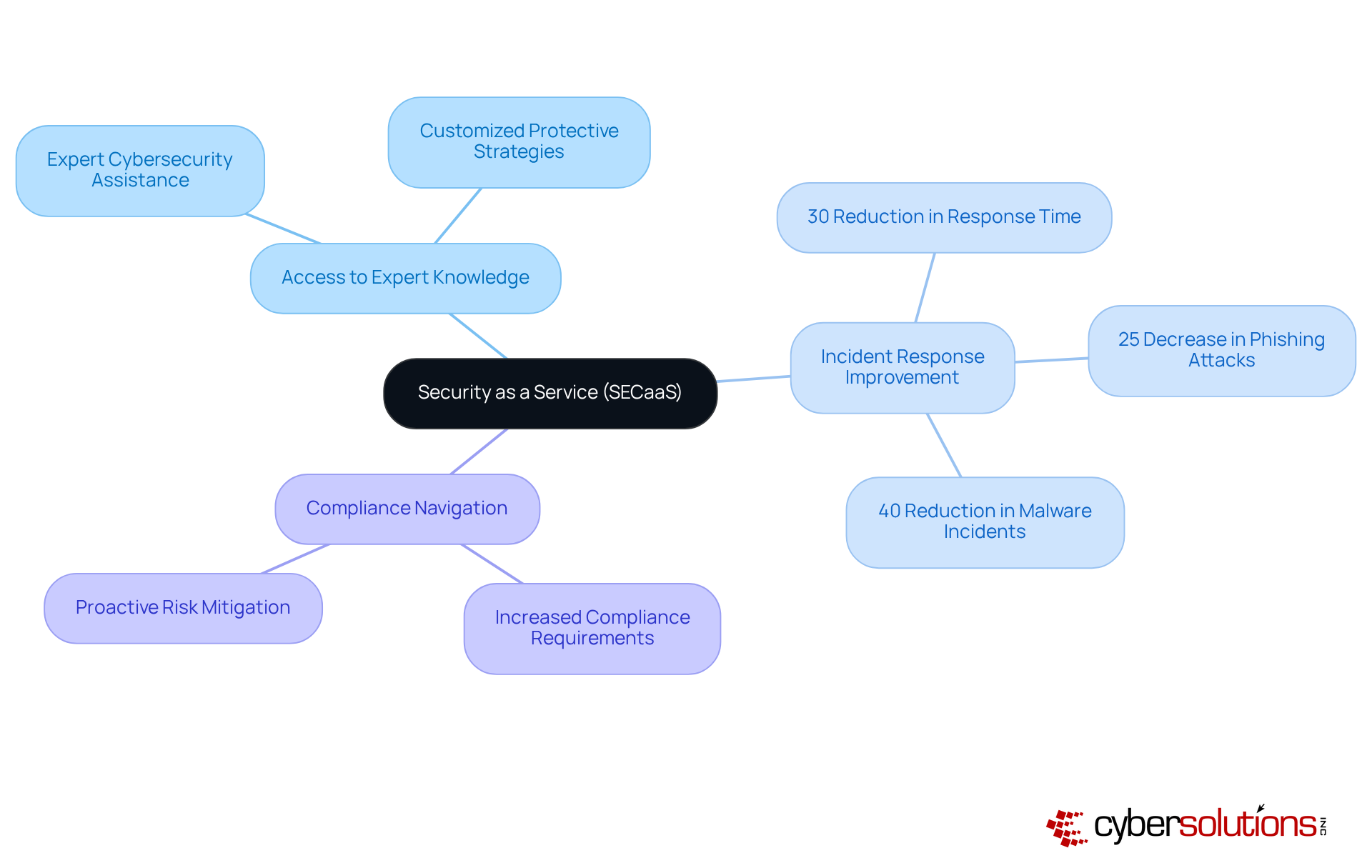
Security as a Service significantly streamlines compliance management, equipping businesses with essential tools and knowledge to meet various . Many providers of Security as a Service incorporate (CaaS) into their offerings, which is crucial for helping businesses navigate complex regulations such as , , and GDPR. This strategy alleviates the burden on internal teams, enabling them to concentrate on core operations while and reducing the risk of .
Entities utilizing CaaS have reported , with 71% noting improvements in their security and compliance posture. Moreover, 89% of users experienced a quicker time-to-compliance across different frameworks, underscoring the effectiveness of Security as a Service solutions.
Experts stress the significance of . Rick Stevenson, Manager of Compliance Advisory Services, asserts that organizations can substantially diminish risks by identifying vulnerabilities before they escalate into compliance issues. This proactive stance is vital, particularly given that 54% of data breaches involve human factors, highlighting the necessity for comprehensive training and awareness programs.
The are considerable, with the global average cost of a data breach projected to reach $4.88 million in 2024. By adopting , companies not only enhance their compliance initiatives but also protect themselves from the severe financial consequences associated with regulatory failures.
In conclusion, security as a service cloud, particularly through Compliance as a Service, empowers organizations to effectively manage the complexities of regulatory adherence, ensuring compliance while minimizing operational disruptions.

In today's digital landscape, the cannot be overstated. A major benefit of lies in its built-in adaptability, allowing providers to to the distinctive needs of each organization. This customization ensures that businesses receive essential safeguarding without the burden of unnecessary features, enhancing the relevance and overall effectiveness of their protective measures. For instance, healthcare entities can implement to meet stringent regulations like HIPAA, integrating robust cybersecurity measures that encompass , comprehensive audit support, and virtual CISO services. This strategic approach (PHI) against unauthorized access and breaches.
Industry leaders emphasize the critical nature of this customization. As one expert aptly noted, 'Cybersecurity isn’t just about avoiding risk — it’s about .' This statement underscores the necessity for tailored strategies that resonate with specific business contexts. Furthermore, evidence suggests that organizations utilizing tailored security as a service cloud solutions experience a notable enhancement in their protective stance, with numerous reports indicating and improved adherence to regulatory standards. The further fortifies this approach by proactively preventing malware and unauthorized software from executing, thereby minimizing vulnerabilities and ensuring compliance with regulations like HIPAA.
This flexibility not only empowers organizations to address their immediate protection challenges but also equips them for enduring resilience in a constantly evolving risk environment.

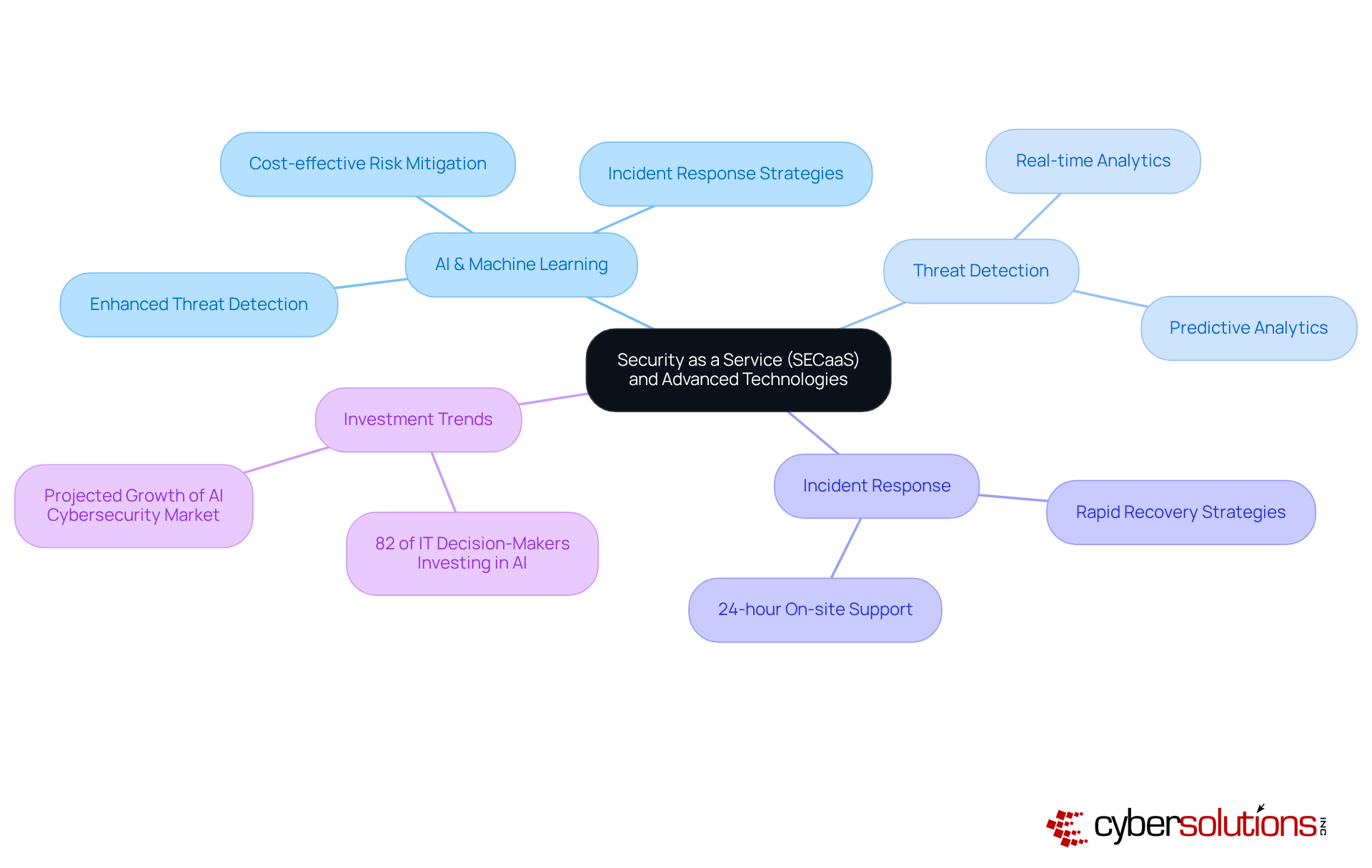
Security as a Service (SECaaS) leverages advanced technologies to deliver tailored for modern enterprises. By integrating artificial intelligence (AI) and machine learning, SECaaS providers significantly enhance threat detection capabilities, streamline processes, and elevate overall security efficiency. For example, AI-driven analytics can dramatically shorten detection windows, potentially saving organizations millions in breach costs. Looking ahead to 2025, those organizations that effectively incorporate AI into their cybersecurity strategies will secure a competitive advantage in managing emerging risks, especially as AI-powered attacks grow increasingly sophisticated.
Moreover, the deployment of machine learning algorithms facilitates continuous improvement in threat detection, adapting to new attack vectors in real-time. This proactive methodology not only strengthens security measures but also aligns with the increasing focus on . With a staggering 71% annual increase in , the adoption of these technologies is essential for maintaining robust defenses against evolving cyber threats.
In addition to these technological advancements, Inc. underscores the necessity of through its Lyra Recovery division. Their sophisticated incident response and recovery services ensure that organizations can swiftly recover from cyberattacks and ransomware incidents, managing over 70 incident responses annually with a recovery time of under two weeks. Committed to providing 24-hour on-site support, Cyber Solutions minimizes damage and promotes a layered recovery approach that encompasses endpoint isolation, malware removal, and user training. This comprehensive strategy not only improves recovery outcomes but also cultivates a strong partnership with clients, equipping them to better face future threats.
Tech leaders acknowledge the significance of these innovations; 82% of IT decision-makers plan to invest in within the next two years. This trend underscores the critical role of in enhancing , ensuring that companies can navigate the complexities of contemporary cybersecurity landscapes while effectively safeguarding their assets. As one client aptly stated, "Cyber Solutions has been a game-changer for our company. Their team is responsive, knowledgeable, and genuinely cares about our business.
A significant benefit of security as a service cloud is the access to . SECaaS providers employ with extensive knowledge and experience, enabling organizations to adopt best practices and advanced risk intelligence. This specialized knowledge is crucial for developing customized protective strategies that significantly enhance a firm's overall safety stance.
Organizations that have implemented SECaaS solutions report a remarkable improvement in their ability to respond to threats. In 2023, companies utilizing SECaaS experienced a compared to those relying solely on internal teams. This efficiency is critical, especially considering that the average cost of a data breach in the U.S. reached $9.48 million, highlighting the .
Moreover, the role of cybersecurity experts in SECaaS is paramount. With over 70% of organizations expecting an annually, of regulatory frameworks is invaluable. These specialists not only assist in navigating compliance but also implement proactive measures that mitigate risks before they escalate.
The advantages of extend beyond compliance and . Organizations leveraging expert support report , including:
As cybersecurity threats evolve, the necessity for specialized knowledge becomes increasingly vital.
Cybersecurity experts underscore the importance of professional assistance, with one stating, "Organizations that invest in specialized cybersecurity expertise are better equipped to protect against contemporary dangers and ensure adherence to changing regulations." This sentiment reflects a growing consensus among industry leaders that expert guidance is essential for maintaining robust protection frameworks in today's complex digital landscape.
is essential for organizations aiming to proactively combat through continuous enhancements to their protective measures. SECaaS providers implement regular updates to systems and protocols, effectively addressing new vulnerabilities and ensuring robust protection against the latest . This is crucial, particularly as 85% of cybersecurity professionals attribute the rise in cyberattacks to the increasing sophistication of threats, including those driven by generative AI.
Data underscores the effectiveness of these ongoing updates; organizations that maintain current protective measures report significantly lower incident rates. For instance, the typical cost of a ransomware incident soared to $4.54 million in 2023, highlighting the . By leveraging security as a service cloud, organizations can mitigate these threats and enhance their overall safety posture.
Industry experts emphasize the necessity of keeping protective measures updated. Tomer Weingarten, CEO of SentinelOne, asserts that should not solely depend on frequent updates but rather be designed with resilience at their core. This perspective aligns with the growing trend of companies adopting security as a service cloud solutions, which provide a systematic approach to and risk management.
Numerous examples illustrate companies successfully utilizing security as a service cloud to strengthen their defenses. For example, financial institutions utilizing security as a service cloud report a 67% increase in their ability to counter cyber threats, demonstrating the of these services. As we approach 2025, the emphasis on maintaining robust cybersecurity strategies through security as a service cloud will be critical, enabling organizations to navigate the complexities of the digital landscape with confidence.
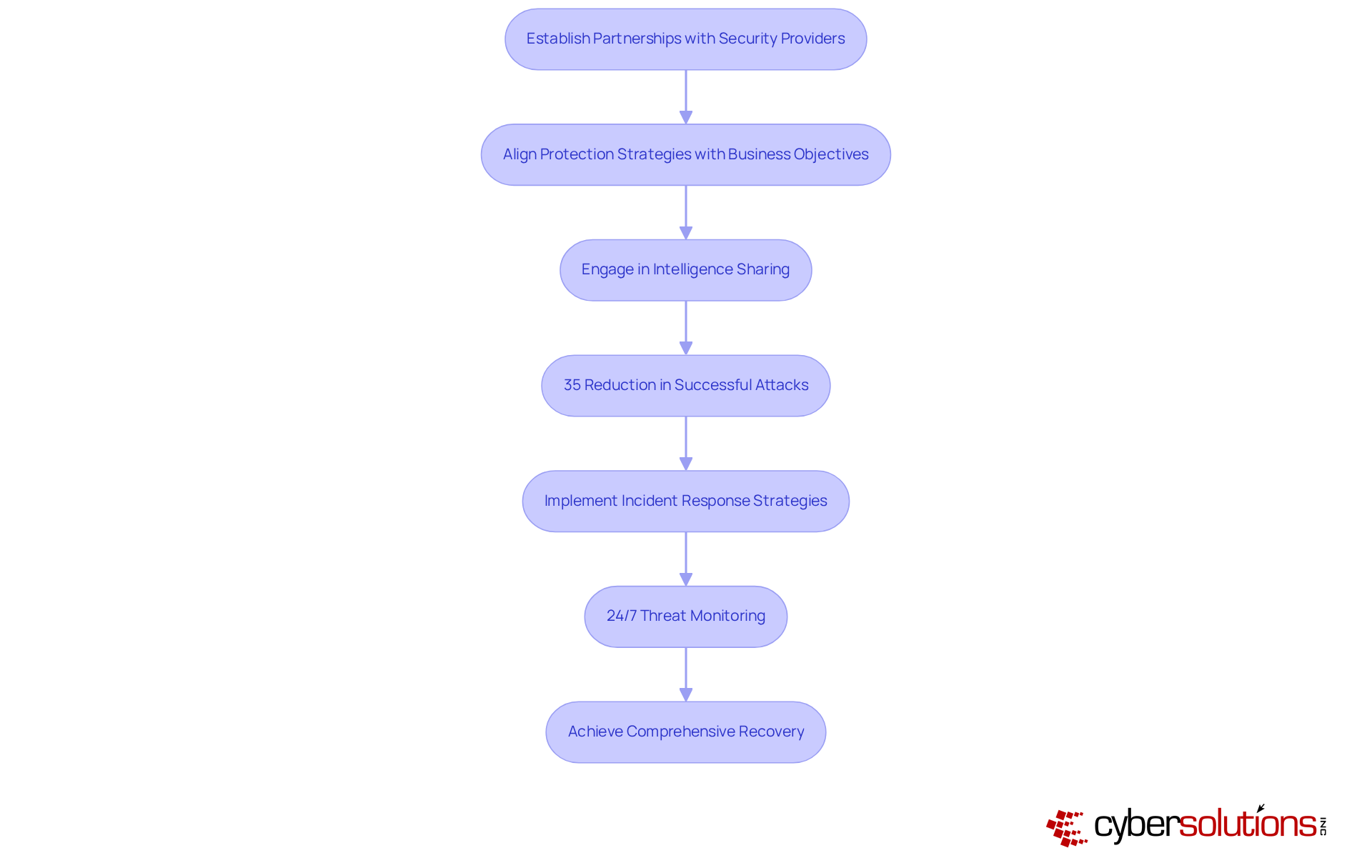
In today's digital landscape, , particularly in healthcare, where the stakes are high. fosters robust collaborations between companies and their protection providers, significantly enhancing overall safety capabilities. By , organizations can align their protection strategies with business objectives, ensuring readiness to tackle evolving challenges. This collaborative approach not only fortifies protective measures but also with financial strategies, as emphasized by industry leaders.
Consider the impact of intelligence sharing: organizations that engage in this practice can experience a remarkable 35% reduction in successful attacks, underscoring the tangible benefits of cooperation. Furthermore, 54% of entities reported a within the first year. , including , empower organizations to swiftly contain risks and achieve comprehensive recovery through a layered approach that encompasses endpoint isolation, malware removal, and user training.
Additionally, continuous guarantees that suspicious activities are identified and mitigated before escalating into serious threats, effectively safeguarding businesses from ransomware, phishing, and other malware attacks. As cybersecurity remains a critical business risk, is essential for navigating the complexities of the digital landscape in 2025.
The significance of Security as a Service (SECaaS) for C-suite leaders is paramount. This innovative approach not only addresses the critical need for robust cybersecurity but also aligns seamlessly with the strategic objectives of modern organizations. By embracing tailored security solutions, businesses can enhance their protective measures while optimizing operational efficiency and financial performance.
Throughout this discussion, key benefits of SECaaS have been underscored, including its scalability, cost-effectiveness, and the capacity to leverage advanced technologies. The proactive threat detection capabilities and continuous updates ensure that organizations remain resilient against evolving cyber threats. Moreover, the importance of expert support and collaboration with security providers has emerged as a crucial factor in successfully navigating the complexities of today's digital landscape.
In light of these insights, it is essential for C-suite leaders to recognize the transformative potential of Security as a Service. By investing in these solutions, organizations can not only safeguard their assets but also foster a culture of security that permeates every level of the business. As cybersecurity challenges continue to grow, adopting SECaaS is not merely a strategic advantage; it is a necessary step toward ensuring long-term success and resilience in an increasingly interconnected world.
What is Cyber Solutions Inc.?
Cyber Solutions Inc. is a company that specializes in delivering customized security as a service cloud solutions tailored to the specific needs of modern businesses, particularly in the healthcare and finance sectors.
Why is cybersecurity important for healthcare organizations?
Cybersecurity is crucial for healthcare organizations because it protects sensitive data, ensures compliance with regulations, and helps maintain trust with clients and stakeholders in an increasingly regulated environment.
What are the key features of Cyber Solutions Inc.'s offerings?
Key features include 24/7 threat monitoring, proactive cybersecurity solutions to safeguard against ransomware, phishing, and malware attacks, and customized protective services that align with business financial objectives.
How does security as a service cloud benefit growing organizations?
Security as a service cloud offers scalability, allowing organizations to adjust their security measures as they grow without the need for significant upfront investments in infrastructure, thus ensuring ongoing protection against emerging threats.
What is the projected growth of the Security as a Service market?
The global Security as a Service market is expected to grow from $12.4 billion in 2021 to $23.8 billion by 2026, reflecting a compound annual growth rate (CAGR) of 13.8%.
How does adopting security as a service impact financial planning for organizations?
Adopting security as a service provides predictable monthly pricing structures, enhancing budget management and maximizing return on investment (ROI) through reduced downtime and improved operational efficiency.
What kind of ROI can organizations expect from security as a service?
Organizations utilizing security as a service can achieve an average ROI of 4.1 times their investment, highlighting the financial advantages of this approach.
What additional capabilities does security as a service encompass?
Security as a service includes advanced risk detection and response capabilities, continuous monitoring, endpoint isolation, malware eradication, and user education, all essential for maintaining robust security frameworks.
How does Cyber Solutions Inc. approach risk management for businesses?
Cyber Solutions Inc. focuses on specific vulnerabilities and compliance requirements to enhance safety and streamline business processes, empowering companies to thrive in a digital-first environment.