
The article underscores the paramount importance of data backup for businesses, particularly for C-suite leaders. It highlights essential strategies to safeguard against data loss stemming from various threats. By detailing best practices such as:
The article not only enhances operational resilience but also ensures business continuity in the face of potential data loss events.
In an era where data breaches and cyber threats are more prevalent than ever, the significance of robust data backup strategies is paramount. For C-suite leaders, the challenge extends beyond merely recognizing the critical nature of data preservation; it encompasses the implementation of effective solutions that guarantee operational continuity and adherence to regulatory standards. As organizations confront the staggering financial consequences of data loss, one pressing question emerges: how can leaders construct a resilient data backup framework that not only safeguards their assets but also prepares them for unexpected disruptions?
Information duplication is a critical process that involves creating copies of information to ensure its availability in the event of loss, corruption, or disaster. For C-suite leaders, understanding the significance of backup is not just beneficial—it's essential. This practice of safeguards against the loss of information due to cyberattacks, hardware failures, or natural disasters, while also ensuring compliance with regulatory requirements. In 2023, the global average cost of a breach was a staggering $4.45 million, underscoring the financial repercussions of inadequate information protection measures.
Efficient information preservation methods, such as the widely adopted 3-2-1 strategy—maintaining three copies of information on two different media with one stored off-site—can significantly reduce restoration time and costs associated with information breaches. This approach is not merely a precaution; it is a fundamental component of an organization's risk management framework. By safeguarding against data loss, it enhances operational resilience, enabling businesses to maintain continuity even in adverse conditions. A notable example is the prolonged recovery of a company in Hong Kong from a ransomware attack, which highlighted the critical need for a robust and regularly tested data restoration plan to ensure business continuity. Additionally, the disruption of the Toyota system for over 36 hours in August 2023 serves as a stark reminder of the consequences of insufficient recovery plans.
Leaders must prioritize information preservation as a cornerstone of their overall IT strategy, recognizing its vital role in protecting both financial and operational integrity. As Chad Quarles, a CISO/Security Advisor, aptly states, 'Data backup for business refers to the procedure of generating and preserving copies of information that can be utilized to safeguard organizations against information loss.' Furthermore, organizations need to select the most suitable restoration and recovery methods tailored to their specific needs, as a variety of approaches are available. By investing in comprehensive recovery solutions and regularly conducting drill tests, organizations can enhance their preparedness for potential information loss events, ensuring they possess a robust plan that adapts to their evolving requirements.
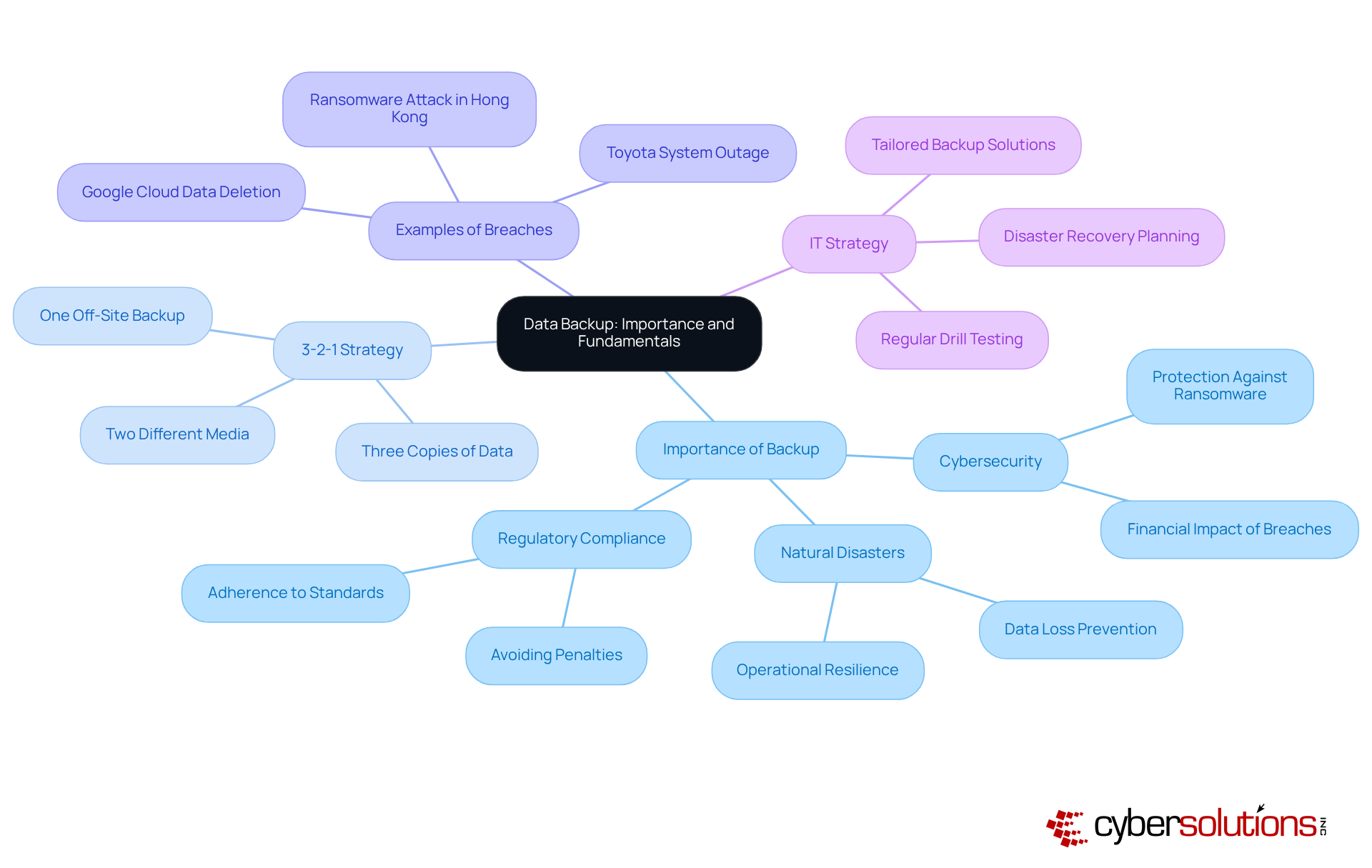
To implement effective data backup for business strategies, C-suite leaders must recognize the critical importance of . Consider the following best practices that not only protect data but also ensure operational continuity in the face of potential threats:
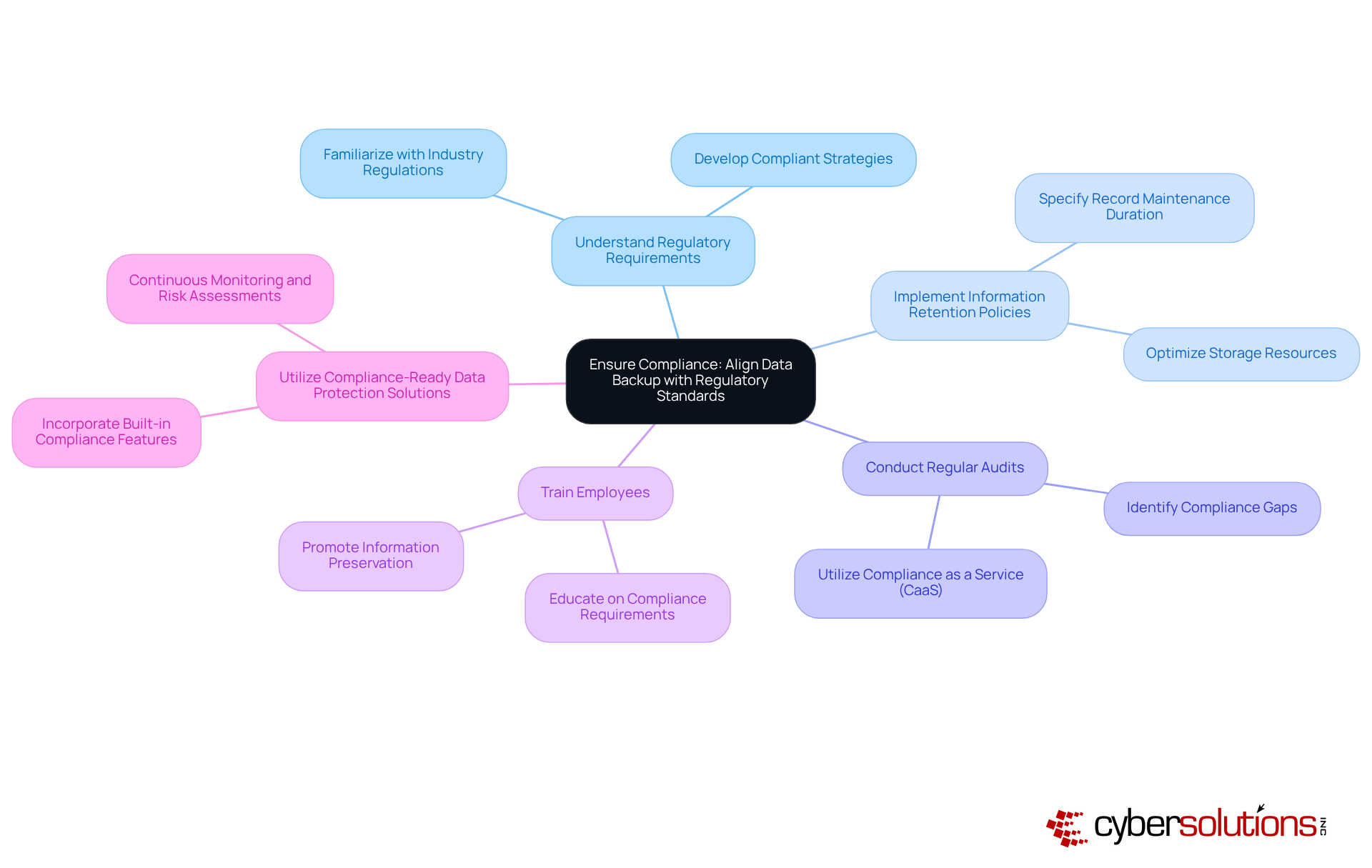
C-suite executives must ensure that their information recovery plans adhere to critical regulatory benchmarks, including GDPR, HIPAA, and PCI-DSS. Compliance is not merely a legal obligation; it cultivates trust with customers and stakeholders, which is essential for business sustainability. Consider the following key aspects:
In 2023, 62% of organizations reported significant improvements in their information safeguarding practices after implementing GDPR-compliant recovery solutions, underscoring the effectiveness of aligning recovery practices with regulatory obligations. Moreover, 80% of companies prioritize cybersecurity in their recovery plans, reflecting the increasing focus on safety in information management. As we move toward 2025, understanding and integrating these regulatory standards into information recovery strategies will be crucial for organizational resilience and trust.
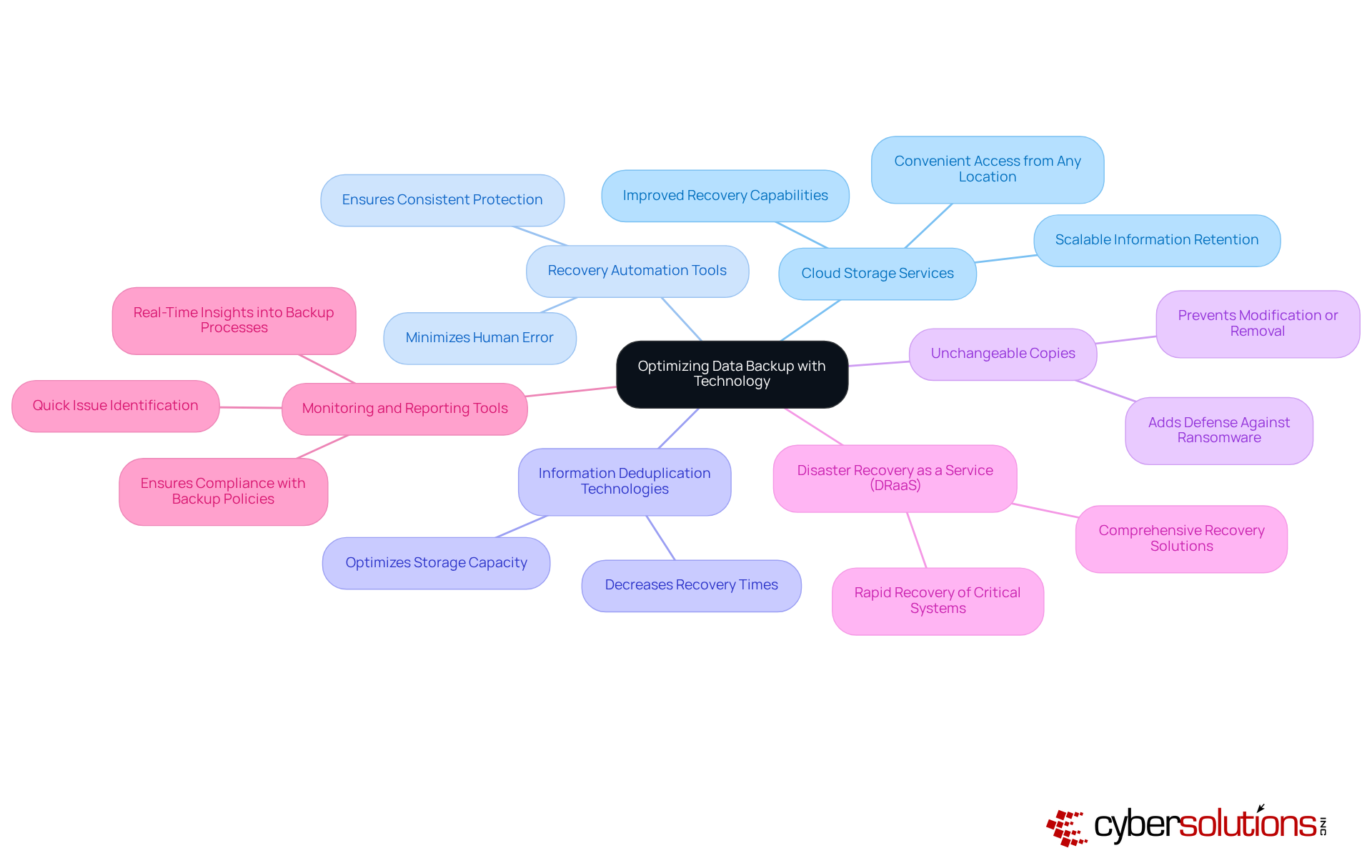
To optimize for business processes, C-suite leaders must recognize the critical role of leveraging advanced technologies. The following solutions are essential for enhancing data protection and recovery capabilities:
By adopting these technologies, C-suite leaders can fortify their organizations against evolving cybersecurity threats, ensuring robust data backup for business and recovery strategies.
Data backup is an indispensable element for modern businesses, particularly for C-suite leaders tasked with safeguarding their organization's information assets. The necessity of having a robust data backup strategy cannot be overstated; it serves as a shield against data loss stemming from cyber threats, hardware failures, and natural disasters. By prioritizing data backup, organizations not only protect their operational integrity but also enhance their resilience in the face of unexpected challenges.
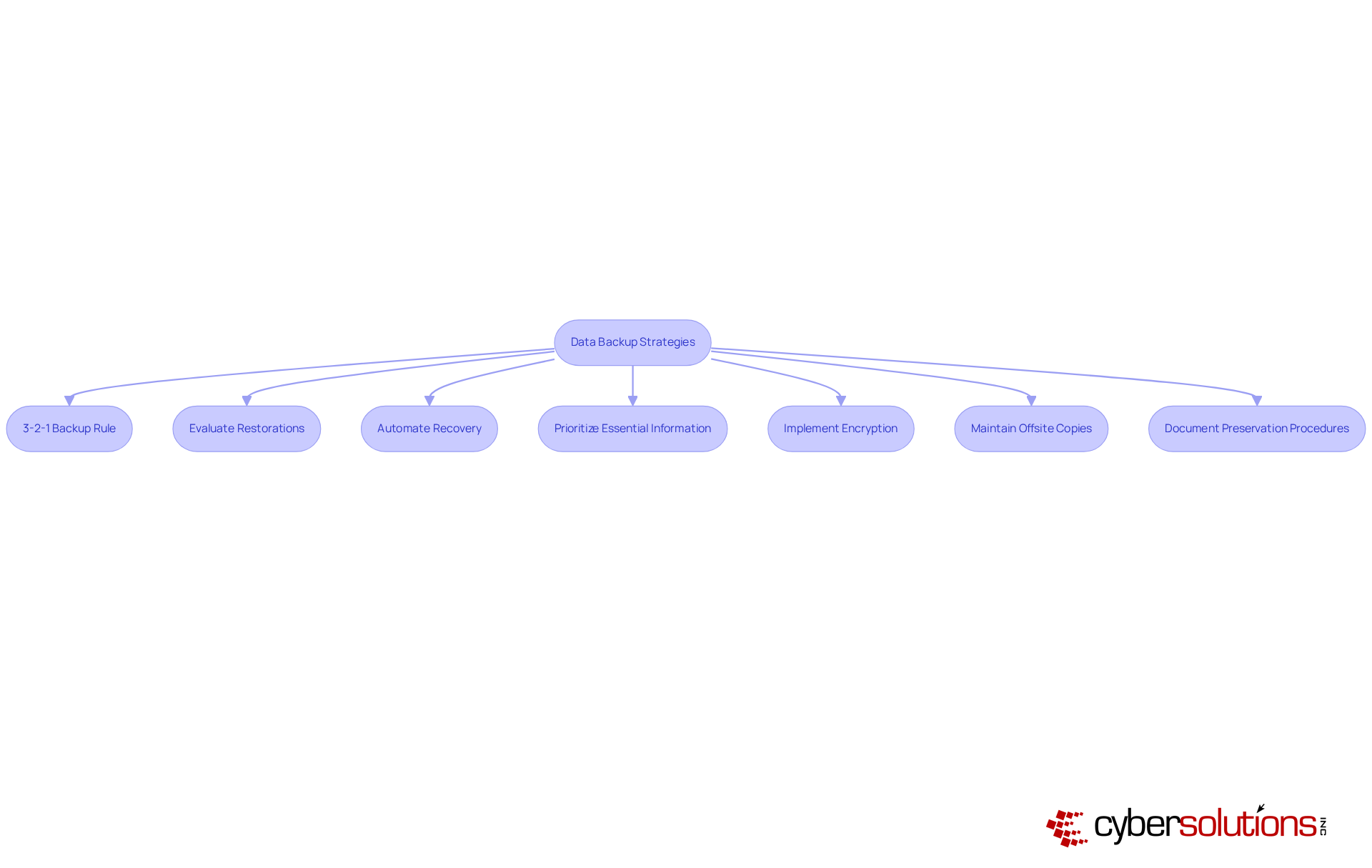
Key strategies that leaders should implement to ensure effective data backup practices include:
Additionally, leveraging advanced technologies such as cloud storage and disaster recovery services further optimizes data protection and recovery capabilities. Each of these strategies contributes to a comprehensive approach that minimizes risks associated with data loss and enhances business continuity.
Ultimately, the significance of data backup transcends mere compliance; it is a vital investment in the future of any organization. C-suite leaders are urged to take proactive steps in developing and implementing robust data backup strategies that align with regulatory requirements and leverage modern technologies. By doing so, they not only protect their organization's valuable information but also build trust with customers and stakeholders, ensuring long-term success and sustainability in an increasingly data-driven world.
What is data backup and why is it important?
Data backup is the process of creating copies of information to ensure its availability in case of loss, corruption, or disaster. It is essential for businesses to safeguard against data loss due to cyberattacks, hardware failures, or natural disasters, and to comply with regulatory requirements.
What is the financial impact of inadequate data protection measures?
In 2023, the global average cost of a data breach was approximately $4.45 million, highlighting the significant financial repercussions of insufficient information protection.
What is the 3-2-1 backup strategy?
The 3-2-1 backup strategy involves maintaining three copies of data on two different media types, with one copy stored off-site. This method helps reduce restoration time and costs associated with data breaches.
How does data backup enhance operational resilience?
By safeguarding against data loss, data backup enhances operational resilience, allowing businesses to maintain continuity during adverse conditions and recover more effectively from incidents.
Can you provide examples of the consequences of poor data recovery plans?
A notable example is a company in Hong Kong that experienced prolonged recovery from a ransomware attack, demonstrating the need for a robust data restoration plan. Additionally, the disruption of the Toyota system for over 36 hours in August 2023 serves as a reminder of the risks associated with insufficient recovery plans.
How should leaders prioritize data backup in their IT strategy?
Leaders must view information preservation as a cornerstone of their overall IT strategy, recognizing its crucial role in protecting both financial and operational integrity.
What should organizations consider when selecting recovery methods?
Organizations need to choose the most suitable restoration and recovery methods based on their specific needs, as various approaches are available. Regularly conducting drill tests can also enhance preparedness for potential information loss events.