
Understanding the Cybersecurity Maturity Model Certification (CMMC) 2.0 is crucial for any organization looking to excel in the defense contracting sector. This framework is not just a set of guidelines; it signifies a significant shift towards strengthening cybersecurity practices that safeguard sensitive Federal Contract Information (FCI).
As businesses grapple with the complexities of compliance, a pressing question emerges: how can organizations effectively implement CMMC 2.0 Level 1 requirements to not only adhere to regulations but also enhance their operational success?
The Cybersecurity Maturity Model Certification 2.0 is not just a framework; it’s a crucial initiative by the Department of Defense (DoD) aimed at elevating the cybersecurity posture of organizations managing Federal Contract Information (FCI). With a tiered adherence approach, the CMMC 2.0 Level 1 requirements focus on essential safeguarding practices that must be grasped by every business leader. Why is this important? Understanding the implications of the CMMC 2.0 framework is vital, as it ensures compliance with federal regulations while enhancing your organization’s reliability and trust within the defense sector.
By aligning with these standards, businesses can significantly mitigate risks associated with cyber threats, positioning themselves favorably for government contracts. This proactive approach not only fosters operational efficiency but also contributes to improved financial performance. Organizations that fulfill the CMMC 2.0 level 1 requirements can expect a strengthened cybersecurity stance, which includes ongoing maintenance, annual self-evaluations, and periodic third-party assessments.
A pivotal aspect of this enhanced security is application allowlisting, which effectively prevents unauthorized software from executing, thereby reducing vulnerabilities and ensuring compliance with stringent regulations like HIPAA, PCI-DSS, and GDPR. As the DoD enforces these standards, the urgency for compliance escalates, impacting over 300,000 organizations worldwide. The phased rollout of CMMC 2.0 underscores the necessity for companies to prepare in advance, ensuring they meet the evolving requirements of federal contracting and maintain a competitive edge in the marketplace.

Cybersecurity is not just a necessity; it's a critical component of operational success in today's digital landscape. The CMMC 2.0 Level 1 requirements encompass 17 fundamental practices designed to protect Federal Contract Information (FCI), categorized into six essential areas:
Organizations that effectively implement these practices can significantly enhance their cybersecurity posture, ensuring compliance with CMMC 2.0 Level 1 requirements. Alarmingly, a recent survey revealed that only 30% of entities currently meet all CMMC 2.0 Level 1 requirements, underscoring the urgent need for focused efforts in this area. Successful case studies demonstrate that companies adopting these practices not only comply with regulations but also fortify their overall security frameworks, mitigating risks associated with cyber threats. By prioritizing these essential practices, organizations can establish a robust digital security framework that not only protects sensitive information but also drives operational success.

The Importance of Cybersecurity Compliance
In today’s digital landscape, ensuring compliance with cybersecurity standards is not just a regulatory requirement; it’s a critical necessity for organizations handling Federal Contract Information (FCI). The assessment process for meeting the CMMC 2.0 Level 1 requirements consists of several essential steps designed to help organizations comply with these standards effectively.
Determine Applicability: First, confirm that your entity manages FCI and is subject to cybersecurity maturity model certification standards. This foundational step sets the stage for your compliance journey.
Scope Your Assessment: Next, identify the systems and assets that process, store, or transmit FCI. A comprehensive understanding of your operational landscape is crucial for effective compliance.
Conduct a Gap Analysis: Evaluate your current practices against the 17 CMMC Level 1 requirements. This analysis is vital; organizations that efficiently recognize regulatory gaps can significantly enhance their security posture, minimizing weaknesses and preparing for assessments. Cyber Solutions offers tailored remediation strategies to address these gaps, ensuring your organization is on the right path to compliance.
Implement Required Controls: Address the identified gaps by implementing necessary cybersecurity practices. This may include enhancing access controls, improving system integrity, and ensuring proper media protection, all supported by Cyber Solutions' expert guidance and documentation preparation.
Perform Self-Assessment: Conduct an annual self-evaluation to assess adherence to CMMC Level 1 practices. Document your findings in the Supplier Performance Risk System (SPRS), which serves as an official record of your adherence efforts. Cyber Solutions assists in this process, ensuring thorough documentation and readiness for audits.
Confirm Adherence: Finally, a senior company official must confirm adherence based on the self-assessment results. This step reinforces accountability and commitment to security standards. Cyber Solutions provides ongoing support to navigate any remaining issues.
By diligently following these steps and leveraging the extensive support from Cyber Solutions, organizations can effectively prepare for the CMMC 2.0 Level 1 requirements while demonstrating their robust security stance. This not only instills confidence in government sponsors and prime contractors but also positions your organization as a leader in cybersecurity compliance.

Achieving CMMC Level 1 compliance is not just a regulatory requirement; it’s a strategic imperative that significantly impacts business operations across several key areas:
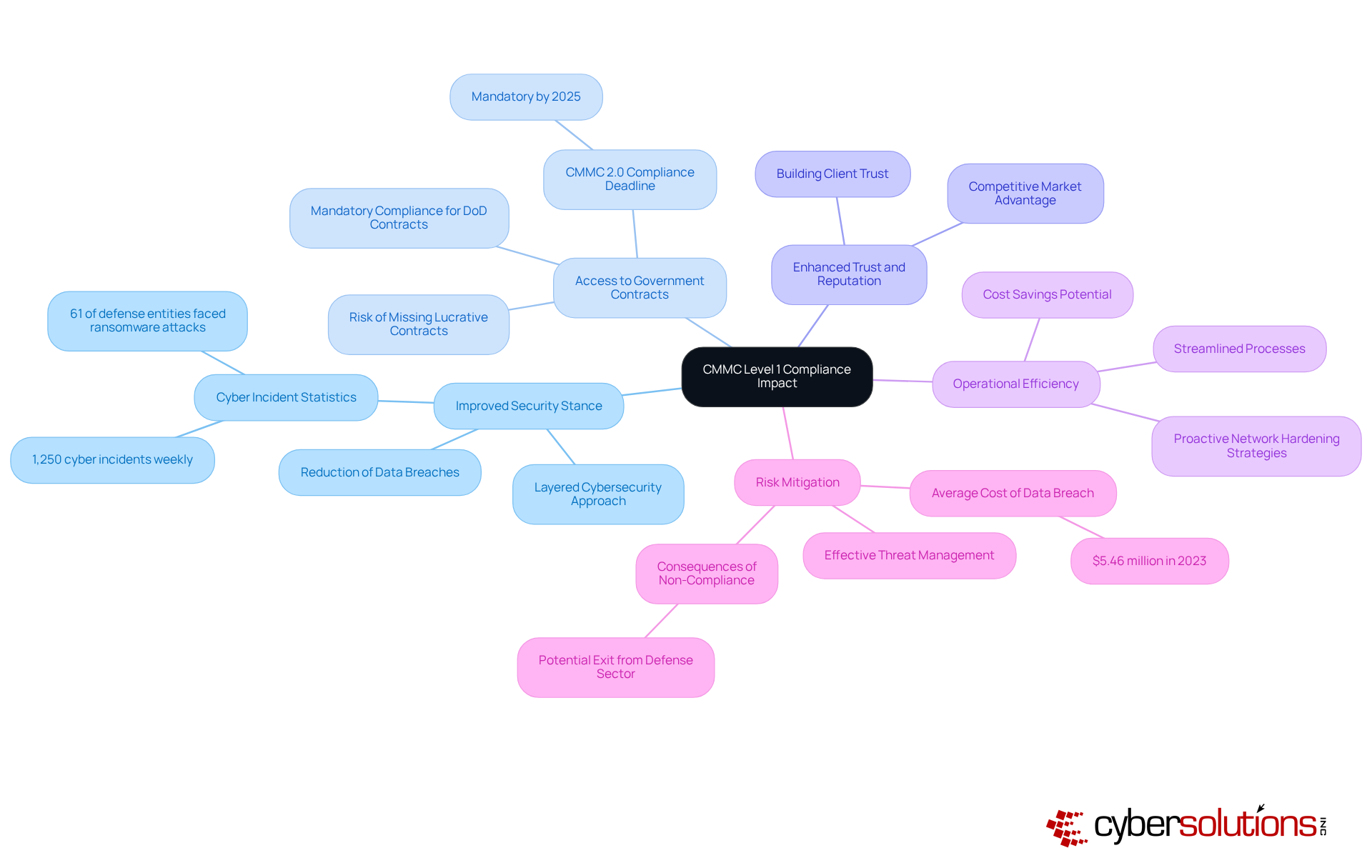
Improved Security Stance: Compliance mandates essential security measures that effectively reduce the risk of data breaches and cyberattacks. This foundational layer of security is crucial, especially as the defense industry faces around 1,250 cyber incidents weekly. With 61% of defense entities reporting ransomware attacks in the past year, the importance of robust digital security cannot be overstated. Cyber Solutions Inc. advocates for a layered approach to cybersecurity, integrating rapid incident management and specialized expertise to enhance recovery efforts and strengthen client partnerships.
Access to Government Contracts: Many Department of Defense (DoD) contracts now require adherence to specific standards, making compliance essential for entities aiming to engage in government business. As the cybersecurity framework becomes a standard necessity in nearly all DoD bids, firms without certification risk missing out on lucrative contracts. Notably, adherence to CMMC 2.0 level 1 requirements will be mandatory for defense contracts starting in 2025, underscoring the urgency for organizations to act.
Enhanced Trust and Reputation: Demonstrating compliance builds trust with clients and partners, elevating an entity's standing in a competitive market. This trust is vital, particularly as security becomes a top priority for stakeholders. By showcasing a commitment to digital security through adherence to regulations, organizations can distinguish themselves in the marketplace.
Operational Efficiency: Implementing cybersecurity maturity model practices can streamline processes, leading to improved operational efficiency and potential cost savings. Organizations that invest in compliance often discover that a structured approach to digital security enhances overall productivity. Cyber Solutions’ proactive network hardening strategies, including application allowlisting, further strengthen security configurations and promote staff cyber hygiene training, contributing to operational effectiveness.
Risk Mitigation: Adhering to established standards enables entities to manage cybersecurity threats more effectively, safeguarding sensitive data and ensuring compliance with regulatory frameworks. This proactive approach is increasingly crucial, as the average cost of a data breach in the defense sector reached $5.46 million in 2023. Moreover, some companies may exit the defense industrial sector due to their inability to demonstrate compliance with cybersecurity standards, highlighting the severe consequences of non-adherence. Cyber Solutions’ application allowlisting is a vital tool in preventing unauthorized software execution, thereby reducing vulnerabilities and enhancing overall security.
In summary, compliance with the CMMC 2.0 level 1 requirements not only meets regulatory obligations but also strategically positions entities for sustained success in a competitive environment. With over 300,000 businesses affected by CMMC 2.0 enforcement, the scale of compliance requirements is significant, making it imperative for organizations to prioritize their compliance efforts.
Achieving compliance with CMMC 2.0 Level 1 is not just a regulatory obligation; it’s a strategic advantage for businesses in the defense sector. In today’s landscape, understanding and implementing the CMMC 2.0 requirements can significantly bolster your cybersecurity framework. This not only ensures compliance with federal standards but also enhances your reputation and operational efficiency in a competitive market.
This article has outlined the critical components of CMMC 2.0, emphasizing the 17 essential practices that form the foundation of Level 1 compliance. Key areas such as:
have been discussed, showcasing how these practices can effectively mitigate cybersecurity risks. Additionally, the assessment process for compliance has been detailed, illustrating the necessary steps organizations must take to align with these standards and maintain their competitive edge.
The implications of meeting CMMC 2.0 Level 1 requirements extend far beyond mere compliance; they significantly impact overall business operations and success. Organizations that prioritize cybersecurity not only protect sensitive information but also unlock opportunities for lucrative government contracts and foster trust among clients and partners. As the cybersecurity landscape continues to evolve, embracing these standards is essential for organizations aiming to thrive in the defense sector. Taking proactive steps towards compliance is not merely an option; it’s a necessary commitment to securing a successful future in an increasingly digital world.
What is CMMC 2.0?
CMMC 2.0, or Cybersecurity Maturity Model Certification 2.0, is an initiative by the Department of Defense (DoD) designed to enhance the cybersecurity posture of organizations that manage Federal Contract Information (FCI).
Why is CMMC 2.0 important for business leaders?
CMMC 2.0 is important for business leaders because it ensures compliance with federal regulations, enhances organizational reliability and trust within the defense sector, and helps mitigate risks associated with cyber threats.
What are the requirements of CMMC 2.0 Level 1?
CMMC 2.0 Level 1 requirements focus on essential safeguarding practices that every business leader must understand to comply with federal regulations and improve their cybersecurity stance.
How does CMMC 2.0 benefit organizations?
By aligning with CMMC 2.0 standards, organizations can improve operational efficiency, enhance financial performance, and strengthen their cybersecurity posture through ongoing maintenance, annual self-evaluations, and periodic third-party assessments.
What role does application allowlisting play in CMMC 2.0?
Application allowlisting is a key aspect of CMMC 2.0 that prevents unauthorized software from executing, reducing vulnerabilities and ensuring compliance with regulations such as HIPAA, PCI-DSS, and GDPR.
How many organizations are impacted by CMMC 2.0?
CMMC 2.0 impacts over 300,000 organizations worldwide as the DoD enforces these standards for federal contracting.
What is the significance of the phased rollout of CMMC 2.0?
The phased rollout of CMMC 2.0 highlights the necessity for companies to prepare in advance to meet evolving federal contracting requirements and maintain a competitive edge in the marketplace.