
In today's digital landscape, the security of an organization is paramount, particularly for C-suite leaders who must navigate an array of cyber threats. The essential IT Managed Service Provider (MSP) services are crucial in bolstering an organization's defenses. Services such as:
play a vital role in mitigating risks and ensuring business continuity. These components underscore the necessity of a proactive and comprehensive cybersecurity strategy, which is essential for fostering organizational resilience in the face of evolving threats.
In an era where cyber threats loom larger than ever, the necessity for organizations to enhance their security measures is paramount. C-suite leaders find themselves increasingly charged with navigating a complex digital landscape, where effective IT management transcends mere technical necessity to become a strategic advantage.
This article explores ten essential IT Managed Service Provider (MSP) services that empower executive leadership to fortify their organization’s security posture. Yet, amidst the vast array of options available, how can leaders identify which services are truly indispensable for safeguarding their operations against evolving threats?
Cyber Solutions Inc. offers a comprehensive suite of IT MSP services that significantly enhance protection across diverse sectors. In today's digital landscape, our 24/7 network monitoring and alert services are critical, ensuring that potential vulnerabilities are identified in real-time. This proactive strategy not only mitigates operational disruptions but also against the ever-evolving cyber threats.
Organizations that adopt continuous support frequently report a substantial decrease in operational interruptions, allowing them to concentrate on strategic initiatives rather than IT challenges. C-suite leaders understand that effective IT management through IT MSP services is vital for safeguarding sensitive data and ensuring compliance, making Cyber Solutions' offerings essential.
As exemplified by Whitehorse City Council's mandate for 24/7/365 security monitoring, ongoing support is crucial for risk mitigation. Furthermore, our rapid incident response strategies, which include on-site assistance within 24 hours, ensure that risks are managed effectively, promoting a faster and more comprehensive recovery.
Regular communications, such as monthly reports and quarterly account management meetings, keep organizations informed and proactive in their IT strategies. Industry leaders consistently underscore the importance of 24/7 help desk support in cultivating a resilient operational framework.
Endpoint protection is paramount for securing devices such as laptops, desktops, and mobile devices against an ever-evolving landscape of cyber threats. Cyber Solutions Inc. implements a comprehensive suite of advanced security measures, including:
A cornerstone of our strategy is application allowlisting, widely regarded as the gold standard in cybersecurity. This proactive approach effectively prevents malware and unauthorized software from executing, significantly and minimizing vulnerabilities. By ensuring that only approved applications can run, we empower organizations to meet stringent compliance requirements such as HIPAA, PCI-DSS, and GDPR. Application allowlisting features centralized management for effortless updates and ongoing monitoring to identify unauthorized software attempts, ensuring prompt detection and blocking of potential threats.
These proactive strategies are crafted to mitigate risks associated with data breaches, which have become increasingly prevalent. In fact, 73% of small and medium-sized businesses reported experiencing cyberattacks in the past year alone. Additionally, the FBI reported 800,944 cyber complaints in 2022, culminating in USD 10.3 billion in reported losses, underscoring the urgent need for robust endpoint protection measures.
By adopting these advanced endpoint security measures, organizations can significantly bolster their security posture and safeguard sensitive information. Features such as automated rollback and extended detection and response (EDR) are essential for effectively addressing emerging threats. This investment not only strengthens defenses but also enhances overall business resilience, enabling companies to maintain operational continuity even amid relentless cyber threats. As organizations navigate the complexities of modern IT environments, embracing IT MSP services and best practices in endpoint security, including application allowlisting, is crucial for protecting critical assets and ensuring compliance with regulatory standards.
Backup and disaster recovery services are vital for ensuring business continuity and protecting data integrity. Cyber Solutions Inc. delivers robust backup solutions that consistently secure critical data, enabling organizations to swiftly recover from cyberattacks or system failures. Consider this: ransomware attacks occur every 11 seconds, and a staggering 90% of businesses lacking recovery plans fail within five days of a disaster. By implementing a well-structured disaster recovery plan, businesses can significantly reduce downtime and safeguard their financial investments while maintaining customer trust.
Real-world examples underscore the effectiveness of these strategies. Organizations that have adopted comprehensive report enhanced resilience against cyber risks, allowing them to recover quickly and minimize operational interruptions. Key features of effective backup solutions include:
These elements are crucial for ensuring that backup data remains protected and recoverable, even amidst escalating cyber threats.
Industry leaders stress the importance of business continuity planning, asserting that the worst time to discover an inadequate backup process is during a crisis. By prioritizing it msp services that include backup and disaster recovery, organizations can bolster their operational resilience and ensure they are prepared for any unforeseen challenges.
Co-managed IT support represents a powerful synergy between a company's internal IT team and the specialized expertise of Cyber Solutions Inc., forging a robust partnership that significantly enhances protective measures. This collaborative model empowers internal personnel to concentrate on strategic initiatives while leveraging external resources for advanced protective measures and proactive monitoring.
By integrating these two layers of expertise, organizations not only bolster their protective stance through a comprehensive strategy—including endpoint isolation, malware removal, and user training—but also achieve improved operational efficiency and a substantial reduction in risk. Companies utilizing IT MSP services have reported notable gains in efficiency and enhanced protection through shared responsibilities, enabling them to focus on core competencies while ensuring a formidable defense against evolving cyber threats.
It is essential to define clear roles and establish effective communication within this partnership to sustain operational efficiency and protection. To fully capitalize on the , C-Suite leaders must prioritize ongoing training for internal teams and ensure that communication channels with Cyber Solutions Inc. are well-articulated.
In today's digital landscape, the significance of managed protection services cannot be overstated. Organizations are increasingly vulnerable to cybersecurity threats, making ongoing monitoring and management of their systems essential. Cyber Solutions Inc. stands out by offering a comprehensive suite of services, including:
By embedding cybersecurity into every aspect of their offerings, Cyber Solutions ensures compliance with industry standards while enhancing operational efficiency.
The implications for organizations are profound. Cyber Solutions’ proactive strategy for managing risks empowers companies to mitigate dangers before they escalate into major problems. This approach not only fosters a but also safeguards profits. Their 24-hour on-site response capability exemplifies a commitment to swift incident response, enabling entities to manage risks effectively and recover promptly.
In conclusion, the integration of robust cybersecurity measures is crucial for organizations navigating the complexities of today's threat landscape. By partnering with Cyber Solutions, organizations can address these challenges head-on, ensuring their systems are secure and resilient against evolving threats.
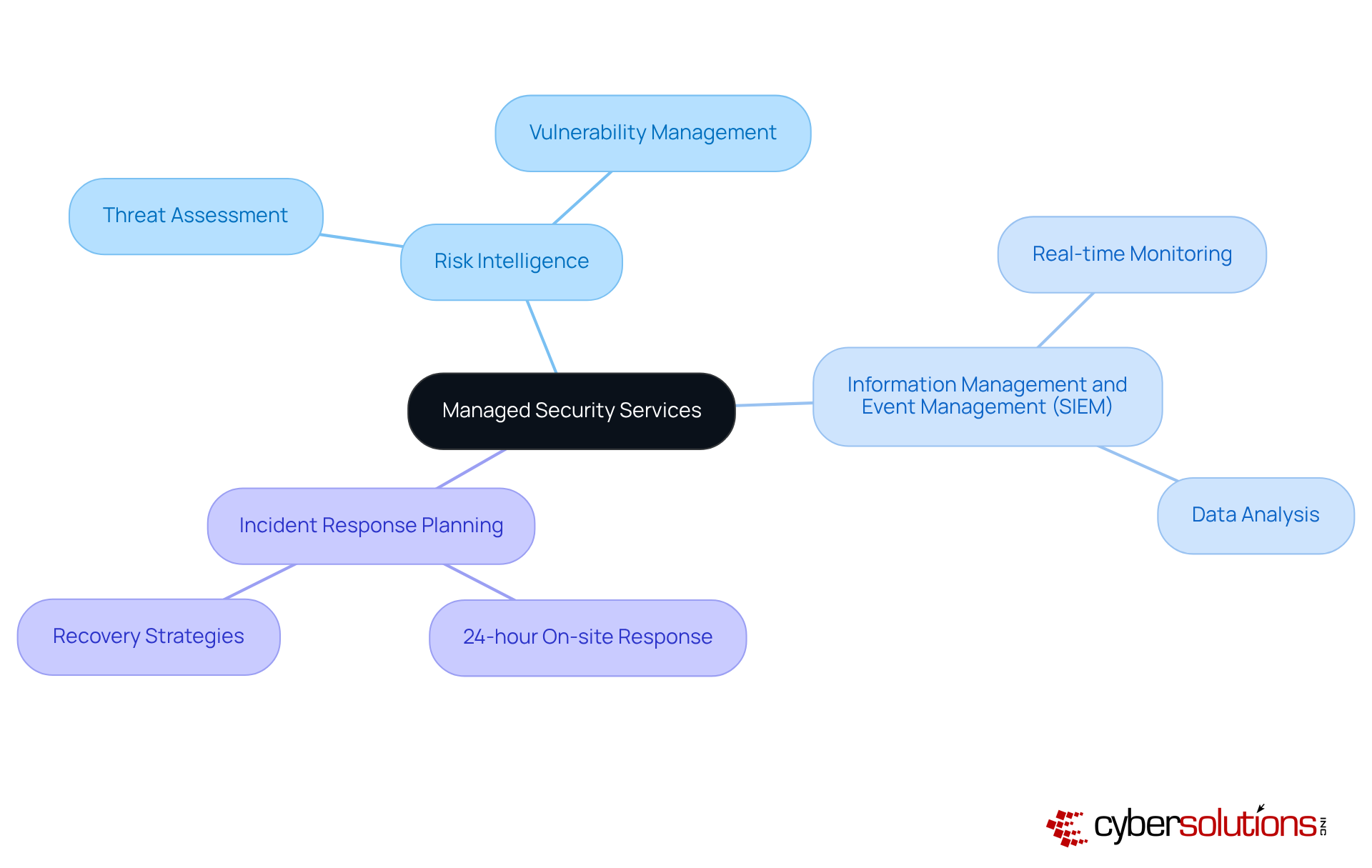
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. is crucial for recognizing potential risks through advanced monitoring tools and techniques. Cyber Solutions Inc. employs sophisticated intrusion detection systems and behavioral analytics to meticulously assess network traffic and user activity. This proactive approach enables organizations to identify anomalies that may indicate a risk, ensuring they remain one step ahead of potential threats.
Our 24/7 network monitoring services deliver instant alerts and real-time insights, facilitating swift action to prevent downtime or breaches. For example, a recent case study highlighted how our vigilant monitoring enabled a healthcare provider to identify and mitigate a ransomware attack before it escalated, showcasing the effectiveness of our services. By implementing robust threat detection measures, businesses can respond rapidly to potential breaches, minimizing damage and safeguarding sensitive information.
Moreover, achieving CMMC Level 3 compliance not only reflects a commitment to cybersecurity but also enhances your organization's overall protective stance. This compliance is vital for safeguarding sensitive federal information and ensuring eligibility for lucrative government contracts. In an era where cyber threats are increasingly sophisticated, partnering with Cyber Solutions can empower your organization to navigate these challenges effectively, fortifying your defenses and securing your operations.
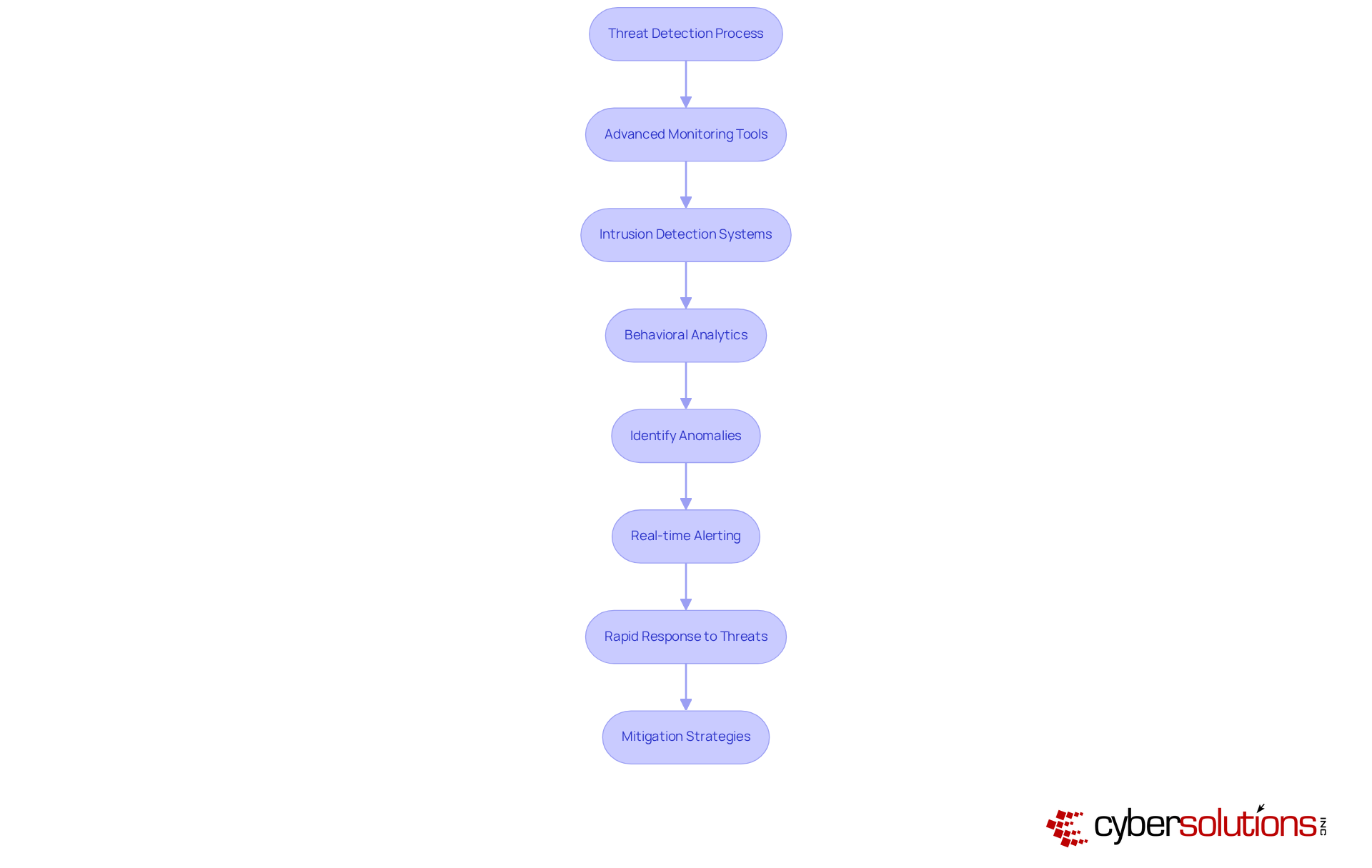
Incident response stands as a pivotal element of cybersecurity, embodying a systematic approach to managing and recovering from security incidents. Cyber Solutions Inc. equips organizations with a robust incident response plan that delineates critical steps to undertake during a breach, including immediate containment, thorough investigation, and effective recovery processes. This proactive strategy is indispensable; research indicates that organizations with a can drastically reduce recovery times and minimize operational disruptions.
For instance, a recent study revealed that organizations employing comprehensive incident response strategies achieved an average recovery time of merely a few days, in stark contrast to weeks for those lacking such plans. This efficiency not only alleviates the financial repercussions of breaches but also safeguards customer trust and brand reputation.
The importance of incident response is underscored by the fact that 52% of organizations identify human error as their most significant vulnerability in IT protection. This reality emphasizes the necessity for ongoing training and awareness programs alongside incident response planning. Cyber Solutions Inc. asserts that a well-prepared organization can adeptly navigate the complexities of a breach, ensuring a swift return to normal operations with minimal fallout.
As Ranjit Bhaskar, a Senior Security Architect, notes, "Cybersecurity awareness is not merely about training; it’s about cultivating a culture that emphasizes protection at every level." This cultural transformation, coupled with a comprehensive incident response strategy, empowers organizations to effectively manage security incidents and recover swiftly, thereby reinforcing their resilience against future threats. Furthermore, Cyber Solutions Inc. provides continuous Threat Monitoring, along with extensive risk assessments and gap analyses, to identify compliance deficiencies and vulnerabilities, ensuring that organizations meet HIPAA standards and enhance their overall cybersecurity posture.
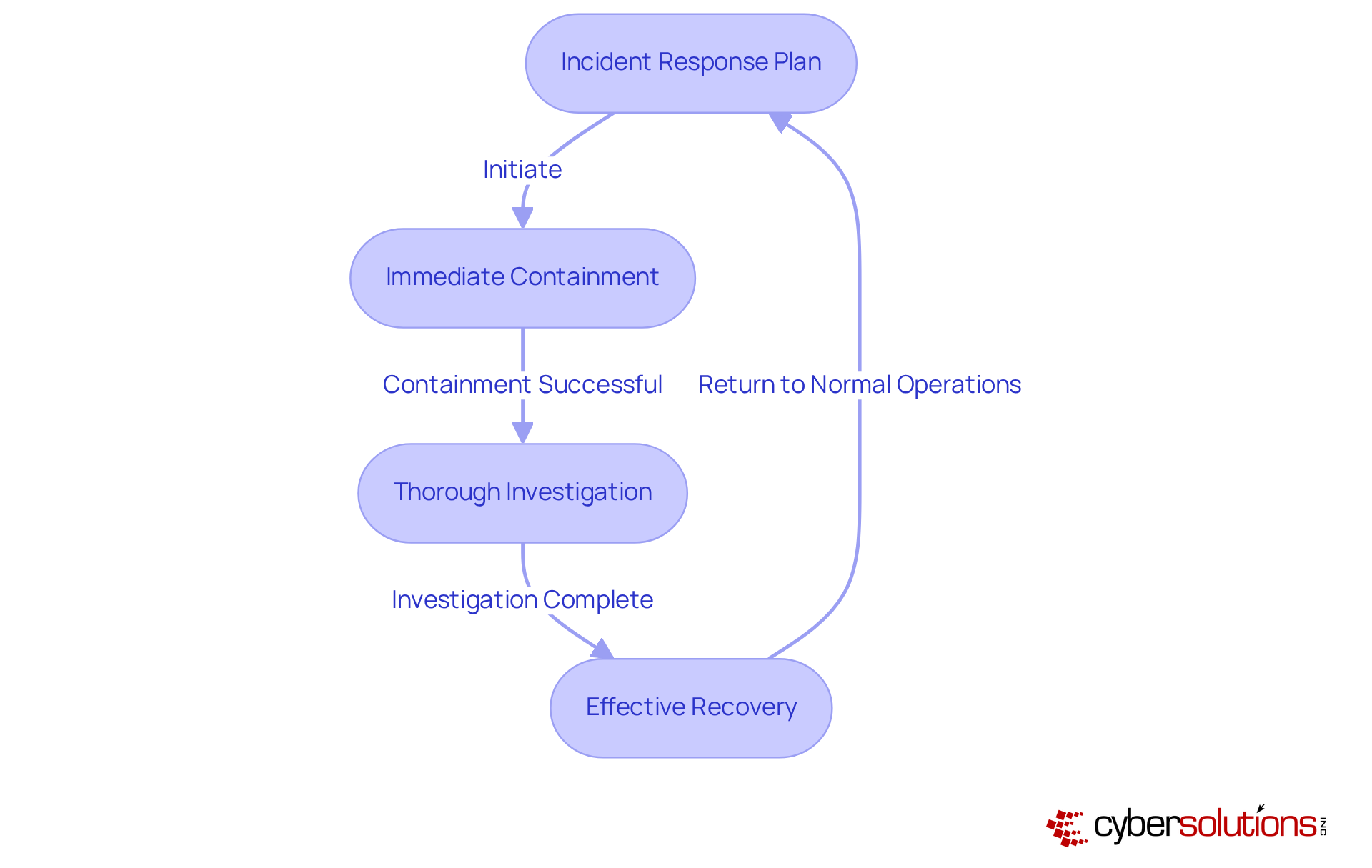
are vital for evaluating a company's IT infrastructure, and it msp services can help reveal potential weaknesses that cybercriminals might exploit. These assessments encompass a thorough examination of systems, applications, and networks, identifying vulnerabilities such as unpatched software, weak access controls, and misconfigurations. Notably, 60% of data breaches arise from unpatched vulnerabilities, highlighting the urgent need for regular evaluations.
Cyber Solutions Inc. employs advanced methodologies to conduct comprehensive evaluations, enabling organizations to proactively address identified vulnerabilities. By establishing a structured assessment schedule—beginning with an in-depth evaluation, followed by monthly quick scans and quarterly reviews—businesses can significantly mitigate their risk of successful cyberattacks by utilizing it msp services. This proactive approach not only protects assets but also enhances compliance with industry standards, particularly for entities in regulated sectors like healthcare and finance when it msp services are implemented. Moreover, integrating audit support and compliance management through it msp services equips organizations for CMMC assessments, further reinforcing their cybersecurity posture.
Real-world examples demonstrate the efficacy of these assessments. Organizations that have integrated regular vulnerability assessments through it msp services into their security programs have successfully diminished risks associated with emerging threats. For instance, a company that adopted automated scanning tools reported a substantial improvement in its protective measures, effectively uncovering vulnerabilities that manual evaluations might overlook. By prioritizing vulnerabilities based on their potential impact and likelihood of exploitation, organizations can focus their remediation efforts on it msp services to address the most critical issues, ensuring a robust defense against cyber threats while aligning with CMMC compliance requirements. Additionally, implementing network hardening strategies, such as closing potential attack vectors and optimizing endpoint protections, can significantly bolster overall security.
Compliance as a Service (CaaS) is crucial for organizations aiming to navigate the complex regulatory landscape shaped by frameworks such as HIPAA, PCI-DSS, and GDPR. In an era where regulatory scrutiny is intensifying, utilizing tailored solutions from Cyber Solutions allows businesses to not only meet these demands but also mitigate associated risks. Our CaaS offerings, which include:
empower organizations to concentrate on their core operations without the burden of regulatory challenges. This strategic focus ultimately safeguards their reputation and financial integrity.
The significance of compliance is underscored by increased scrutiny from regulatory agencies and the potential repercussions of non-compliance, which can lead to hefty fines and reputational damage. Organizations that effectively implement it msp services report enhanced operational efficiency and a stronger regulatory posture, illustrating the tangible advantages of investing in these services. Furthermore, application allowlisting is pivotal in proactively thwarting malware and unauthorized software, thereby reducing vulnerabilities and ensuring adherence to stringent data protection standards.
As we look ahead to 2025, the regulatory landscape is poised for evolution, with new requirements on the horizon. This will heighten the demand for , solidifying CaaS as an indispensable element of contemporary business operations.
In today's digital landscape, the importance of cybersecurity cannot be overstated, particularly for organizations handling sensitive information. Penetration testing simulates cyberattacks to identify vulnerabilities within a company's systems, a critical step in safeguarding assets. Cyber Solutions Inc. performs comprehensive penetration tests to assess the effectiveness of current protective measures and reveal potential vulnerabilities. This proactive approach is essential for entities aiming to attain , which necessitates advanced protective protocols to safeguard sensitive federal information. By identifying vulnerabilities early, organizations can implement necessary changes to enhance their protective stance, ultimately reducing the risk of costly breaches and ensuring eligibility for lucrative government contracts.
Moreover, these assessments contribute significantly to a comprehensive cybersecurity strategy. They include:
In an era where cyber threats are increasingly sophisticated, organizations must prioritize these proactive measures to protect their operations and maintain trust with stakeholders. How prepared is your organization to face these challenges? Taking action now can make all the difference.
In the realm of cybersecurity, the integration of robust IT MSP services is essential for C-suite leaders seeking to enhance their organizations' security posture. Cyber Solutions Inc. provides a comprehensive array of services designed to address the multifaceted challenges posed by today's digital threats. By leveraging continuous support, proactive monitoring, and specialized expertise, organizations can significantly fortify their defenses against cyber risks while ensuring compliance with regulatory standards.
Key services such as:
are critical components of an effective cybersecurity strategy. Each service plays a pivotal role in safeguarding sensitive data while promoting operational efficiency and resilience. The urgency of adopting these measures is underscored by the escalating frequency and sophistication of cyberattacks, highlighted by relevant examples and statistics.
Ultimately, organizations must recognize that investing in IT MSP services is not merely a reactive measure but a proactive strategy for long-term success. As cyber threats evolve, so too must the approaches to mitigate them. Embracing these essential services will protect critical assets and empower businesses to navigate the complexities of the digital landscape with confidence. Taking decisive action now can pave the way for a secure and resilient future.
What services does Cyber Solutions Inc. provide?
Cyber Solutions Inc. offers a comprehensive suite of managed IT support services, including 24/7 network monitoring, incident response strategies, endpoint protection, and backup and disaster recovery services.
How does Cyber Solutions Inc. enhance security for organizations?
The company enhances security through proactive strategies such as continuous support, real-time vulnerability identification, and rapid incident response, which helps mitigate risks and operational disruptions.
What is the significance of 24/7 network monitoring?
24/7 network monitoring is critical for identifying potential vulnerabilities in real-time, which helps organizations fortify their security posture against evolving cyber threats.
What are the benefits of continuous IT support?
Organizations that adopt continuous IT support report a significant decrease in operational interruptions, enabling them to focus on strategic initiatives rather than IT challenges.
What is application allowlisting and why is it important?
Application allowlisting is a cybersecurity measure that prevents unauthorized software from executing. It is important because it reduces the attack surface, minimizes vulnerabilities, and helps organizations comply with regulatory standards like HIPAA, PCI-DSS, and GDPR.
What advanced security measures are included in Cyber Solutions Inc.'s endpoint protection?
The endpoint protection includes next-generation antivirus software, robust firewalls, and sophisticated intrusion detection systems.
Why are backup and disaster recovery services essential?
Backup and disaster recovery services are essential for ensuring business continuity and protecting data integrity, allowing organizations to recover quickly from cyberattacks or system failures.
What key features should effective backup solutions have?
Effective backup solutions should include regular testing of backup systems, adherence to the 3-2-1 rule (three copies of data on two different storage types with one offsite), and robust security measures such as encryption and access controls.
What is the 3-2-1 rule in backup strategies?
The 3-2-1 rule is a backup strategy that involves keeping three copies of data, stored on two different types of storage media, with one copy stored offsite.
How can organizations ensure they are prepared for unforeseen challenges?
By prioritizing managed IT services that include backup and disaster recovery, organizations can enhance their operational resilience and be better prepared for unexpected challenges.