
The article emphasizes the critical importance of disaster recovery and backup strategies, outlining ten essential approaches for achieving success in this domain. Comprehensive planning, the integration of cybersecurity measures, and adherence to regulatory requirements are paramount. Evidence supports the assertion that effective disaster recovery plans not only enhance organizational resilience but also significantly reduce downtime and ensure compliance with industry standards. Ultimately, these strategies protect sensitive data and maintain operational continuity, underscoring the necessity for organizations to prioritize robust disaster recovery frameworks.
In a time when data breaches and operational disruptions can devastate organizations in an instant, the significance of effective disaster recovery and backup strategies has reached an unprecedented level. This article explores ten essential strategies that not only protect sensitive information but also bolster organizational resilience against unexpected crises. As businesses confront evolving threats and increasing regulatory demands, the pressing question emerges: how can they ensure their disaster recovery plans are both robust and compliant? By examining these strategies, readers will gain valuable insights into navigating the complexities of disaster management in today’s digital landscape.
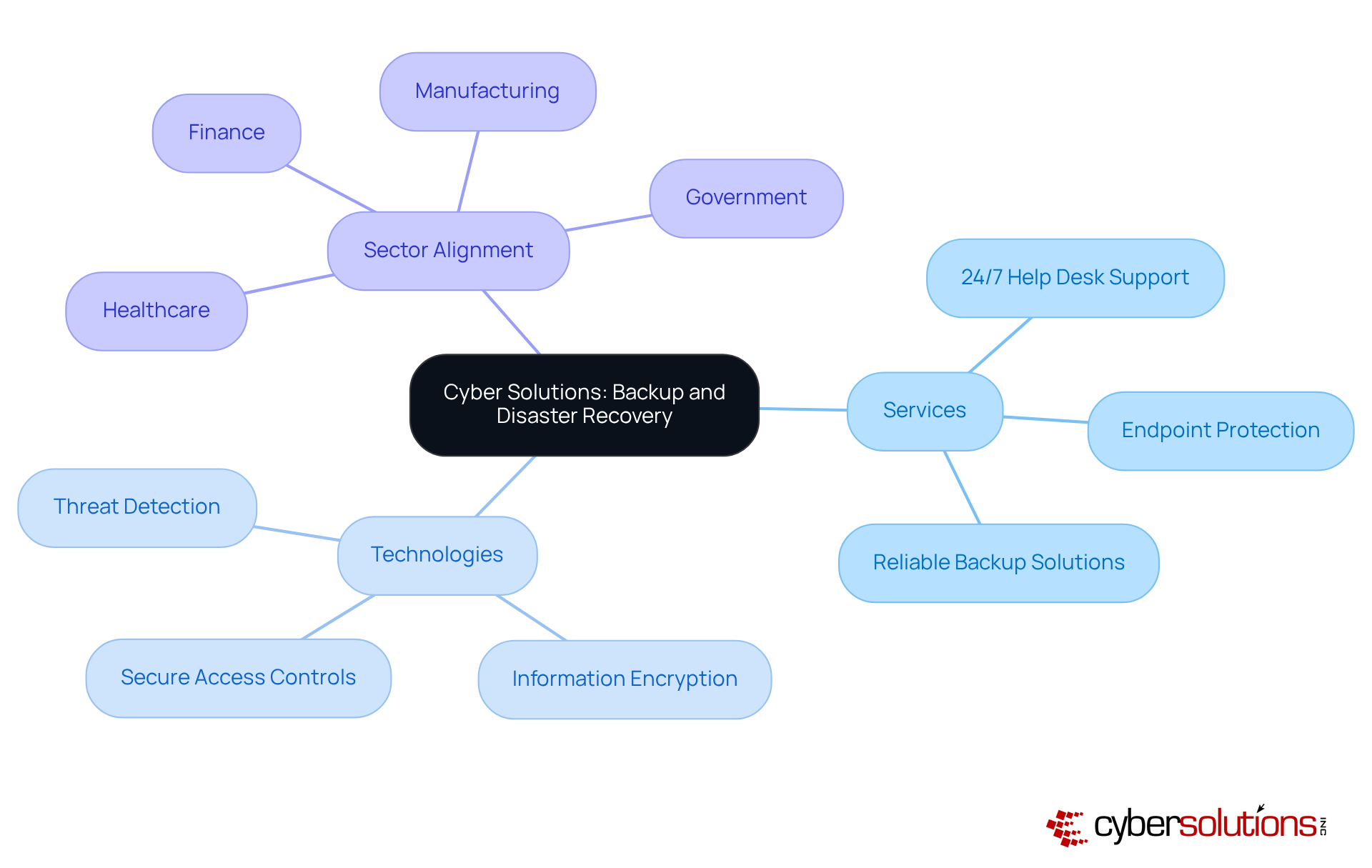
In today's digital landscape, the significance of cybersecurity cannot be overstated, particularly in the healthcare sector where sensitive information is at stake. Cyber Solutions Inc. provides a robust suite of services for disaster recovery and backup, designed to protect against information loss and operational disruptions. This is crucial for healthcare organizations, which face unique challenges such as regulatory compliance and the safeguarding of patient data.
Their comprehensive services encompass:
By implementing advanced technologies like threat detection, information encryption, and secure access controls, Cyber Solutions enhances disaster recovery and backup capabilities, enabling organizations to recover swiftly from incidents, thereby minimizing downtime and mitigating financial repercussions.
What sets Cyber Solutions apart is their tailored approach, which aligns each service with the distinct security and compliance requirements of various sectors, including finance, manufacturing, and government. This strategic alignment enhances overall resilience against potential threats, making it imperative for healthcare CFOs to consider such solutions. With Cyber Solutions, organizations can with confidence, ensuring their operations remain uninterrupted and secure.
In today's digital landscape, the importance of robust cybersecurity measures cannot be overstated, particularly for organizations relying on data integrity. IBM's advanced solutions for disaster recovery and backup leverage artificial intelligence and cloud technologies to deliver exceptional performance. Key services such as IBM Cloud Backup and IBM Resiliency Orchestration automate restoration processes, ensuring that information is consistently backed up across various environments. This automation significantly and simplifies restoration efforts, making these solutions especially advantageous for entities that demand high availability and strong information protection.
Integrating IBM's solutions into IT strategies enables businesses to realize substantial cost savings while enhancing operational efficiency. As industry experts highlight, the integration of AI in procedures for disaster recovery and backup is revolutionizing how organizations manage information resilience. By 2025, forecasts suggest that AI-driven solutions will greatly enhance recuperation times and mitigate operational risks. Moreover, with 93 percent of attacks targeting backup repositories, the impact of IBM Cloud Backup on operational efficiency is profound, allowing enterprises to maintain continuity and compliance while effectively safeguarding essential information.
In conclusion, as organizations face increasing cybersecurity threats, the adoption of IBM's innovative solutions becomes a strategic imperative. By prioritizing disaster recovery and backup, businesses can not only protect their data but also position themselves for success in an ever-evolving threat landscape.

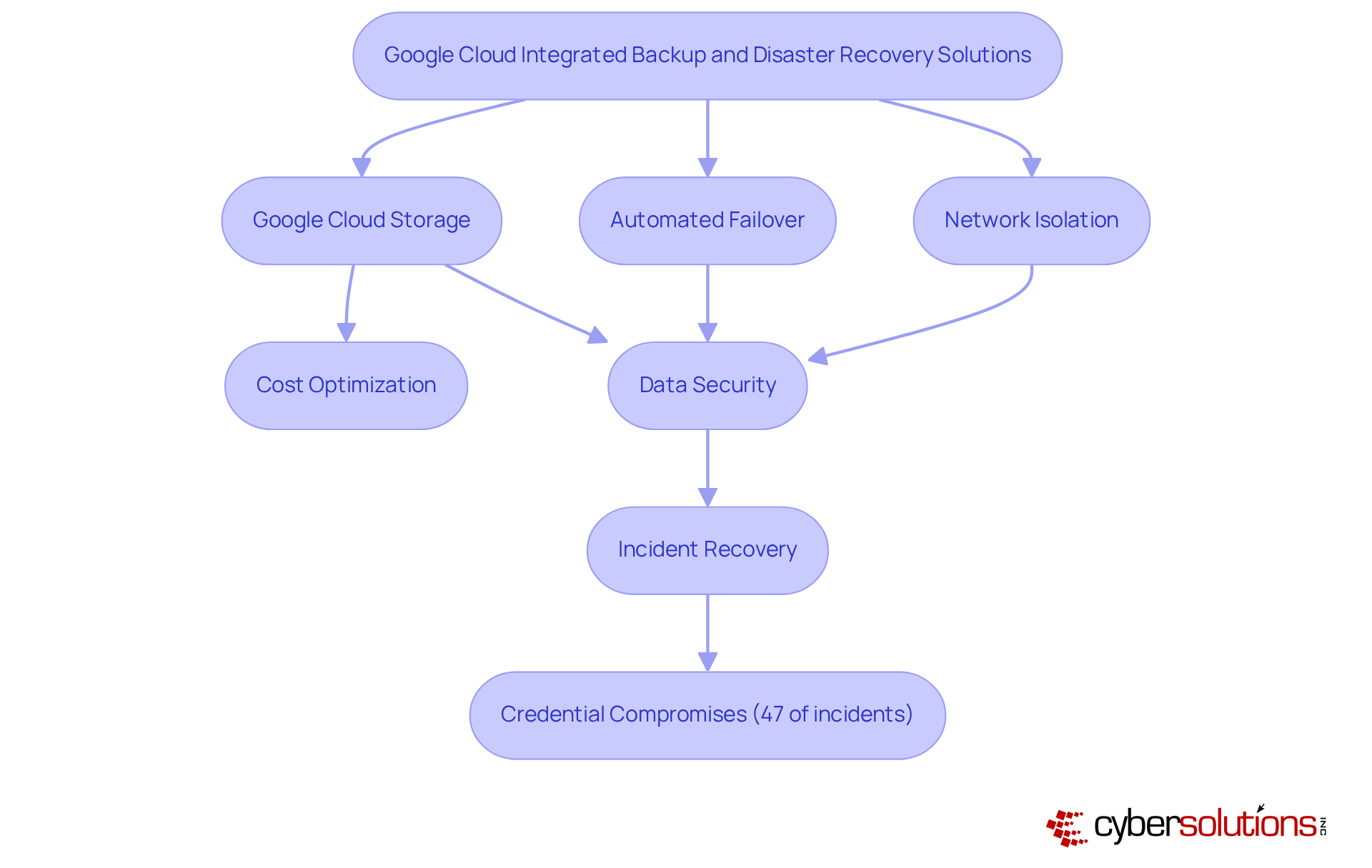
Google Cloud provides robust integrated solutions for disaster recovery and backup, which are essential for safeguarding information across diverse platforms. With tools such as Google Cloud Storage for disaster recovery and backup and Google Cloud Disaster Recovery, organizations can leverage , significantly reducing downtime during disruptions. As we look ahead to 2025, the anticipated increase in cloud storage utilization for backup underscores a growing reliance on cloud technology for information protection.
The advantages of Google Cloud Storage extend beyond mere information retention; it enables companies to optimize costs through efficient resource management while ensuring data security and recoverability. Experts in cloud technology emphasize the critical need for comprehensive information protection strategies, which include the use of automated failover systems to enhance disaster recovery and backup. A recommended practice is to isolate production and backup infrastructures through separate VPC networks, further bolstering information protection.
Real-world applications of Google Cloud Storage demonstrate its efficacy in backup scenarios. Organizations have effectively employed these solutions to recover from incidents involving credential compromises, which represented 47% of cloud security incidents in the latter half of 2025. By adopting Google Cloud's integrated solutions, businesses not only secure their data but also strengthen their overall operational resilience.
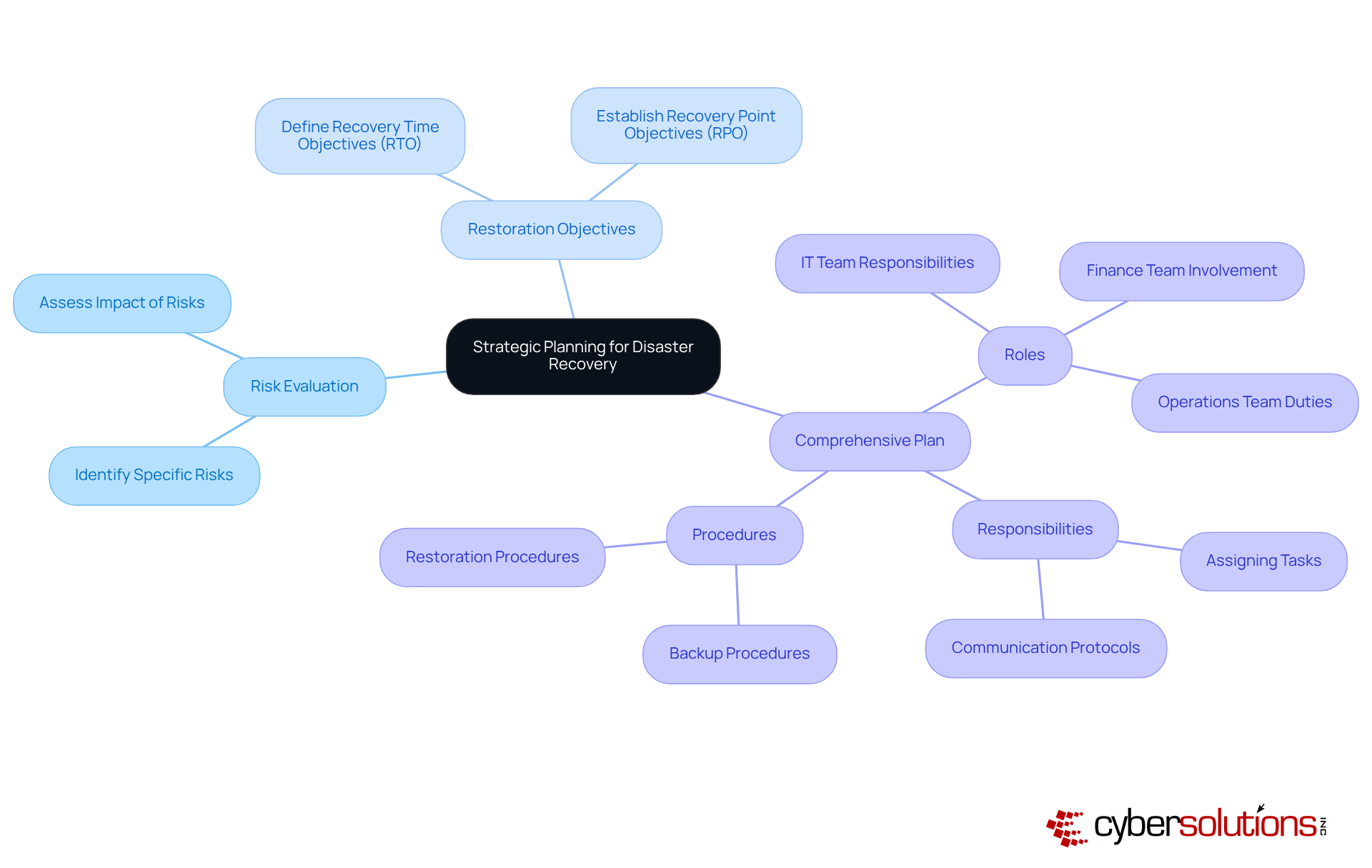
Effective disaster recovery and backup management begins with strategic planning. Organizations must evaluate their specific risks, define restoration objectives, and create a comprehensive plan that details roles, responsibilities, and procedures. This planning process should involve key stakeholders from IT, finance, and operations to ensure . By establishing a clear strategy for disaster recovery and backup, entities can enhance their preparedness for potential disruptions and ensure a swift recovery when incidents occur.
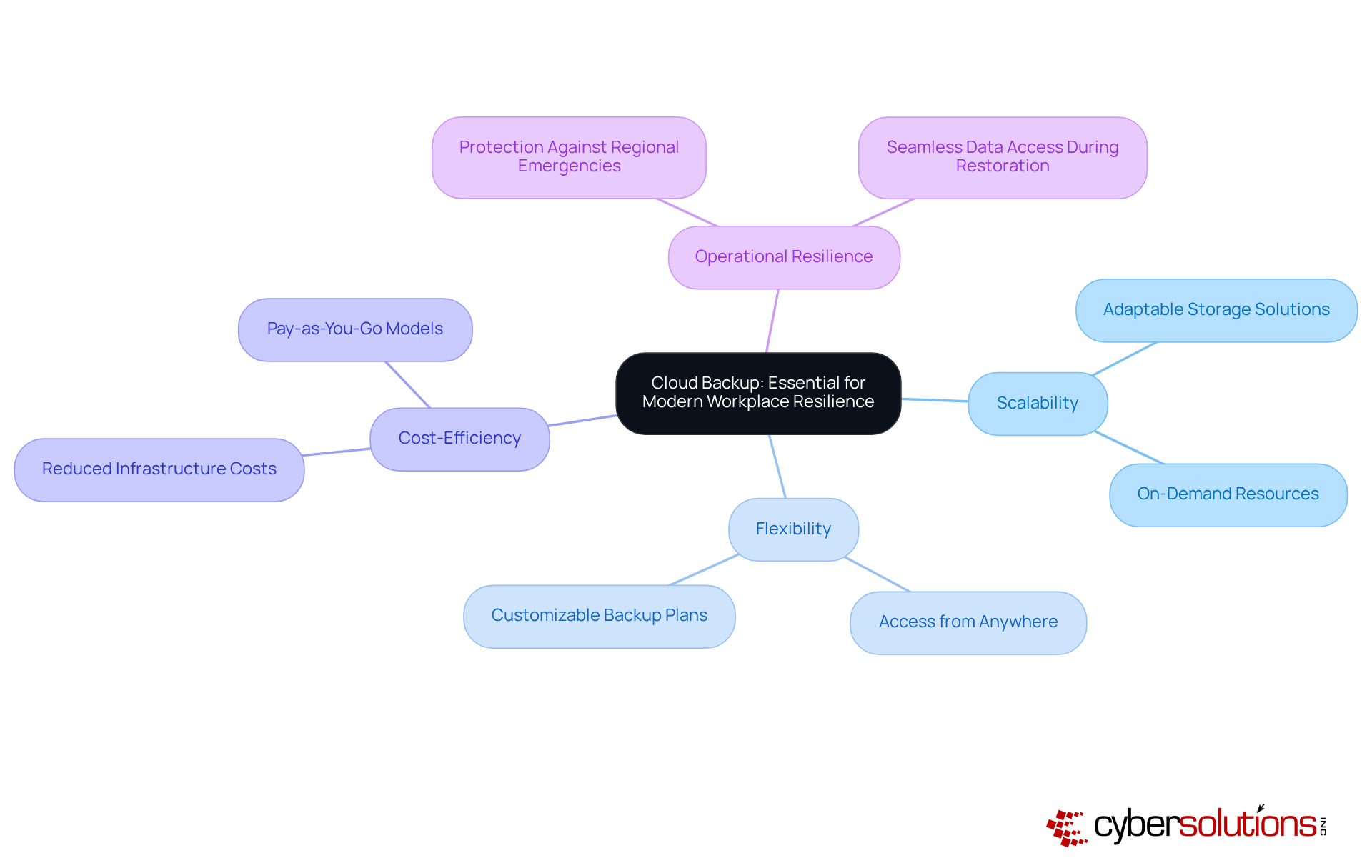
In today's digital landscape, disaster recovery and backup are essential for ensuring information resilience, rather than being merely an option. Organizations must recognize that cloud-based solutions offer unparalleled scalability, flexibility, and cost-efficiency, which enable them to implement effective disaster recovery and backup for their information offsite. This approach not only protects against regional emergencies but also by ensuring seamless access to data during restoration efforts.
By leveraging cloud backup solutions, companies can enhance their operational resilience and ensure effective disaster recovery and backup of critical information, making it accessible no matter the circumstances. Investing in disaster recovery and backup is not just prudent; it is a strategic imperative for any organization aiming to thrive in an increasingly unpredictable environment.
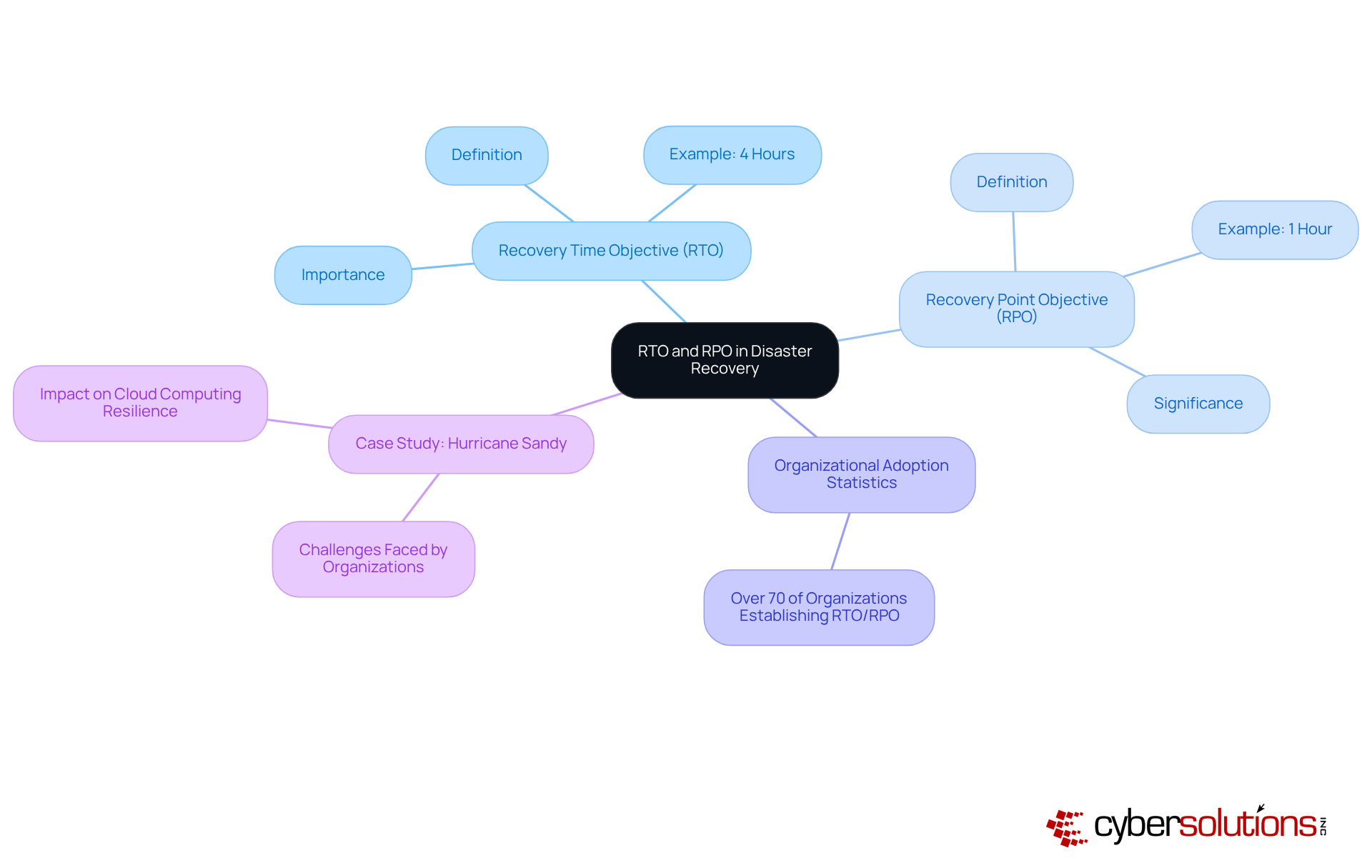
Recovery Time Objective (RTO) and Recovery Point Objective (RPO) are critical metrics in crisis recovery planning that significantly impact a company's resilience. RTO defines the maximum allowable downtime following an incident, while RPO indicates the maximum permissible information loss measured in time. For example, a company with an RTO of four hours must restore operations within that timeframe to avoid substantial disruptions. Similarly, an RPO of one hour signifies that the organization can only .
In 2025, statistics indicate that over 70% of organizations have begun to establish their RTO and RPO metrics, recognizing their essential role in effective disaster management strategies. By setting clear RTO and RPO objectives, businesses can prioritize restoration efforts and allocate resources more efficiently, ensuring a swift return to normal operations. Industry experts stress that understanding these metrics is crucial for aligning recovery strategies with business goals, ultimately enhancing operational resilience and minimizing financial losses during unforeseen events.
Consider the case of Hurricane Sandy, where numerous entities faced significant challenges due to unclear RTO and RPO metrics, resulting in prolonged downtimes and data losses. As highlighted by industry expert Gelbstein, 'The security of information involves the protection of their confidentiality, integrity, and availability,' underscoring the necessity of robust metrics. Furthermore, concerns regarding cloud computing's ability to uphold these standards have prompted organizations to reassess their recovery strategies, ensuring they are equipped to tackle both natural and artificial emergencies.
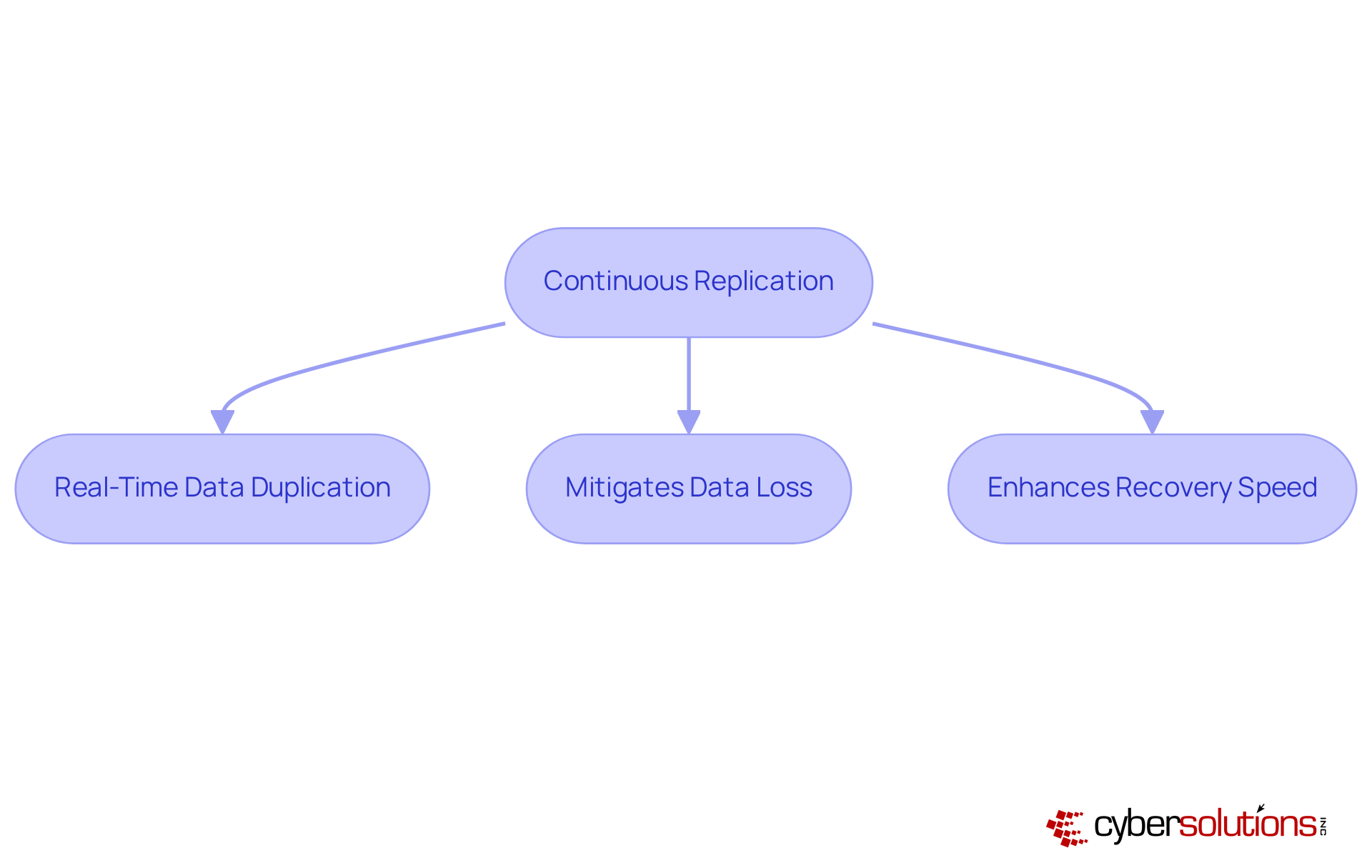
Continuous replication stands as a formidable protection strategy, ensuring real-time duplication of information to a secondary location. This method not only guarantees that data remains consistently current but also significantly mitigates the risk of data loss during emergencies, which is essential for effective disaster recovery and backup. By adopting continuous replication, organizations can markedly decrease restoration times and enhance their overall disaster recovery and backup capabilities. This strategy is especially advantageous for businesses that demand and cannot afford prolonged downtime.
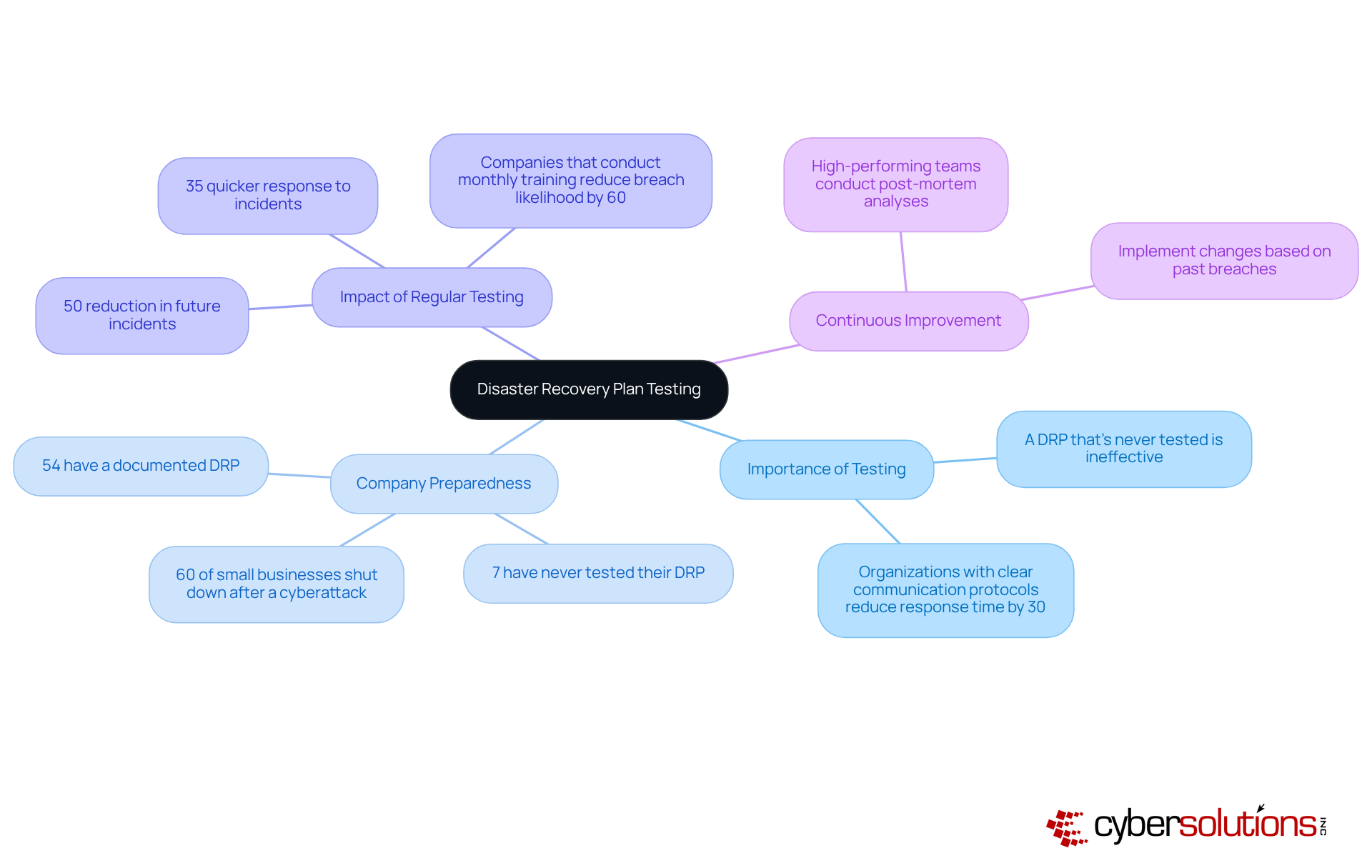
Routine evaluation of emergency response strategies is not just important; it is essential for confirming their efficacy and ensuring organizational durability. Frequent simulations and drills, involving all relevant stakeholders, clarify roles and responsibilities during emergencies. Notably, entities conducting incident response exercises at least quarterly can react 35% quicker to incidents, significantly enhancing restoration results.
Experts assert that a disaster recovery and backup plan (DRP) that is never tested is fundamentally ineffective. Alarmingly, only 54% of companies currently have a documented disaster recovery and backup plan, and a staggering 7% admit they have never tested their disaster recovery and backup procedures. This lack of readiness in disaster recovery and backup can lead to severe consequences; FEMA indicates that 25% of businesses facing a major crisis never resume operations.
Moreover, entities that implement modifications derived from previous breaches can reduce future incident rates by as much as 50%. This underscores the critical need for continuous improvement through regular testing and post-incident reviews. As IBM succinctly states, "A DRP that’s never tested is basically a piece of paper." By fostering a culture of readiness and integrating emergency management into daily operations, businesses can enhance their confidence and capacity to respond efficiently to situations, ultimately safeguarding their operations and reputation. To ensure your entity is prepared, prioritize and actively engage all participants in the process.
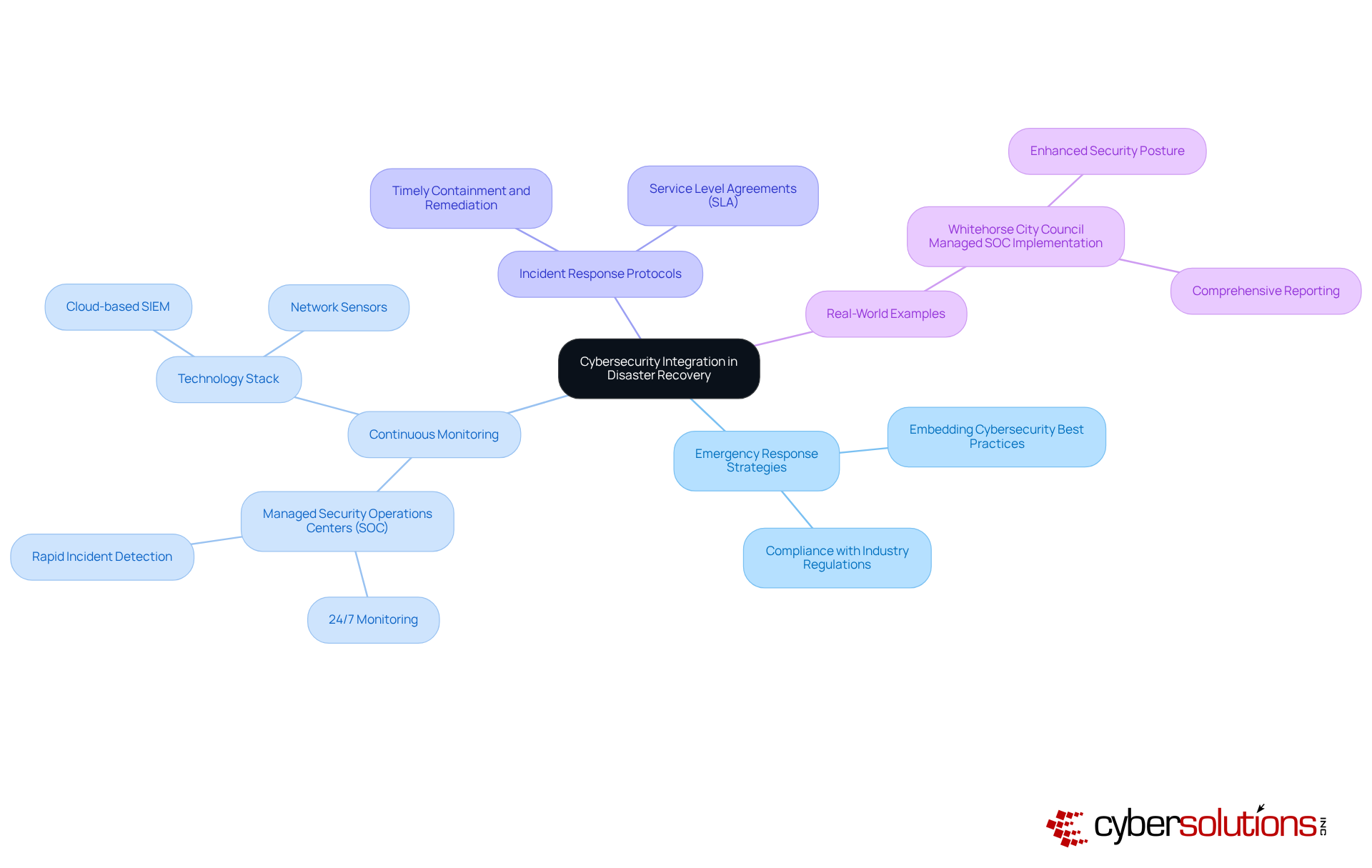
Incorporating cybersecurity measures into emergency response strategies is not just advisable; it is imperative for organizations aiming to safeguard against evolving threats. With cyber incidents, including ransomware attacks and information breaches, becoming increasingly prevalent, it is essential for to explicitly address these challenges. By embedding cybersecurity best practices into restoration strategies, businesses not only enhance their resilience but also ensure compliance with industry regulations. This comprehensive approach safeguards sensitive data and strengthens the overall security posture of the organization.
Current trends indicate a shift towards proactive cybersecurity strategies within emergency management frameworks. Organizations are recognizing the critical need for continuous monitoring and rapid incident response capabilities to mitigate the impact of cyber threats effectively. For example, the implementation of Managed Security Operations Centers (SOC) has demonstrated effectiveness in providing 24/7 monitoring and prompt detection of security incidents, significantly reducing security risks.
The impact of ransomware on disaster recovery and backup planning is profound. As ransomware attacks rise, entities must prioritize strategies that incorporate robust disaster recovery and backup solutions along with incident response protocols. Real-world examples, such as the successful deployment of a Managed SOC for Whitehorse City Council, illustrate how tailored cybersecurity solutions can enhance response strategies. This implementation not only improved incident response times but also delivered comprehensive reporting and actionable insights, ultimately strengthening the security posture and providing greater peace of mind for stakeholders.
By 2025, integrating cybersecurity into emergency response strategies will transcend being a best practice; it will become essential for entities striving to navigate the complexities of contemporary threats efficiently. By adopting a holistic approach that merges IT resilience with cybersecurity measures, businesses can better prepare for and recover from potential cyber incidents.
Adherence factors play a pivotal role in crisis management planning, particularly for organizations operating within regulated sectors such as healthcare and finance. Understanding , including HIPAA, PCI-DSS, and GDPR, is imperative, as these frameworks dictate the necessary protocols for safeguarding sensitive information during recovery efforts.
For instance, HIPAA mandates that healthcare entities develop comprehensive emergency restoration plans to protect patient information, whereas PCI-DSS outlines stringent requirements for financial institutions to secure cardholder data.
By integrating crisis management strategies with these regulations, organizations not only mitigate the risk of penalties but also enhance their overall security posture. This proactive compliance approach cultivates trust among clients and stakeholders, showcasing a commitment to data protection and operational resilience.
Notably, organizations that prioritize regulatory adherence in their disaster recovery plans demonstrate greater success in maintaining business continuity and safeguarding critical information assets.

In the realm of disaster recovery and backup, the necessity for robust strategies cannot be overlooked. Organizations must prioritize comprehensive planning and the integration of advanced technologies to safeguard their critical data and ensure operational continuity. By recognizing the unique challenges posed by cybersecurity threats and regulatory requirements, businesses can effectively navigate the complexities of disaster recovery, positioning themselves for success in an increasingly unpredictable environment.
The article outlines essential strategies for effective disaster recovery, including:
Moreover, it emphasizes the need for regular testing of disaster recovery plans and the integration of cybersecurity measures to enhance resilience against potential threats. Each of these elements contributes to a holistic approach that not only protects sensitive information but also fosters organizational confidence in the face of disruptions.
Ultimately, organizations are urged to adopt a proactive stance towards disaster recovery and backup. By investing in tailored solutions and prioritizing strategic planning, businesses can ensure they are well-equipped to respond swiftly to incidents, thereby minimizing downtime and safeguarding their reputation. Embracing these essential strategies will empower organizations to thrive amidst challenges, reinforcing the significance of disaster recovery as a critical component of operational success.
What is the significance of cybersecurity in the healthcare sector?
Cybersecurity is crucial in the healthcare sector due to the need to protect sensitive information, ensure regulatory compliance, and safeguard patient data.
What services does Cyber Solutions Inc. provide for disaster recovery and backup?
Cyber Solutions Inc. offers 24/7 help desk support, endpoint protection, and reliable backup solutions that ensure data integrity and availability.
How does Cyber Solutions enhance disaster recovery and backup capabilities?
Cyber Solutions uses advanced technologies such as threat detection, information encryption, and secure access controls to enhance disaster recovery and backup capabilities.
What unique approach does Cyber Solutions take in its services?
Cyber Solutions tailors its services to align with the specific security and compliance requirements of various sectors, including finance, manufacturing, and government.
What are the key features of IBM's backup and disaster recovery solutions?
IBM's solutions leverage artificial intelligence and cloud technologies, offering services like IBM Cloud Backup and IBM Resiliency Orchestration that automate restoration processes.
How does the integration of AI impact disaster recovery and backup?
The integration of AI in disaster recovery and backup processes is expected to significantly enhance recuperation times and mitigate operational risks by 2025.
What is the importance of IBM Cloud Backup?
IBM Cloud Backup is crucial for maintaining operational efficiency and continuity, especially since 93 percent of attacks target backup repositories.
What solutions does Google Cloud offer for disaster recovery and backup?
Google Cloud provides integrated solutions like Google Cloud Storage for disaster recovery and backup, and Google Cloud Disaster Recovery with automated failover and recovery capabilities.
How does Google Cloud Storage optimize costs for organizations?
Google Cloud Storage allows companies to manage resources efficiently, which helps optimize costs while ensuring data security and recoverability.
What is a recommended practice for enhancing information protection in disaster recovery?
It is recommended to isolate production and backup infrastructures through separate VPC networks to bolster information protection.
What real-world applications demonstrate the effectiveness of Google Cloud Storage?
Organizations have successfully used Google Cloud Storage to recover from incidents, including credential compromises, which accounted for 47% of cloud security incidents in the latter half of 2025.