
CMMC Level 2 compliance is vital for organizations, especially within the defense sector. This compliance involves the implementation of 110 protective measures designed to safeguard Controlled Unclassified Information (CUI) and mandates an external evaluation for certification.
C-suite leaders must prioritize understanding these requirements. They should engage in strategic planning that includes:
By doing so, they can enhance their cybersecurity posture and mitigate the significant penalties associated with non-compliance.
In an era where cybersecurity threats loom larger than ever, organizations are confronted with the pressing challenge of adhering to stringent CMMC Level 2 requirements. For C-Suite leaders, comprehending these regulations transcends mere compliance; it embodies a pivotal opportunity to bolster their organization’s security posture and competitive edge within the defense contracting sector. As the compliance deadline approaches, executives must ask themselves: how can they ensure their organizations not only meet these requirements but also leverage them to cultivate resilience against the ever-evolving landscape of cyber threats?
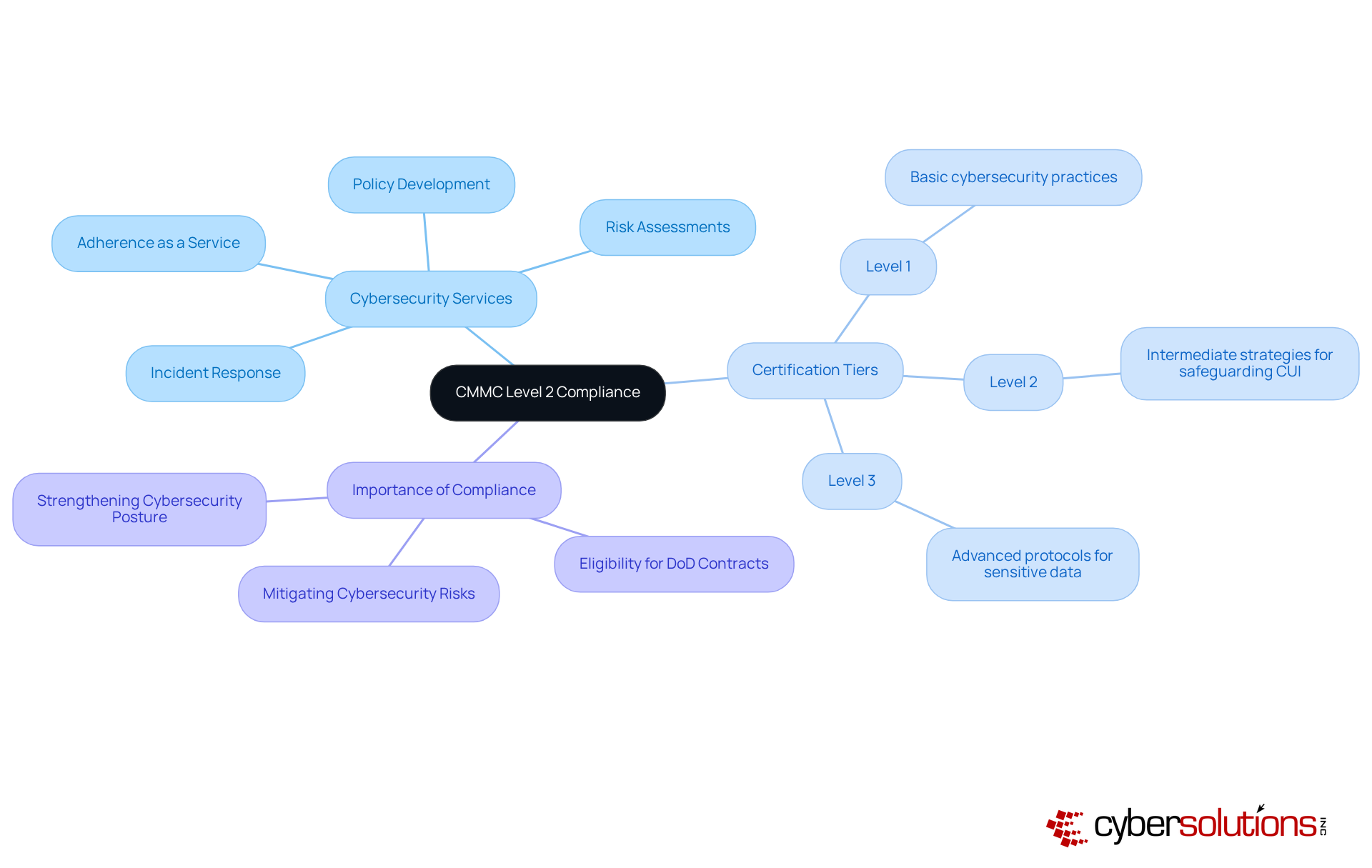
In today's digital landscape, the importance of cybersecurity cannot be overstated, particularly for organizations striving to meet the CMMC Level 2 requirements. Cyber Solutions Inc. offers an extensive range of cybersecurity services specifically tailored to assist these organizations. Their Adherence as a Service (CaaS) solutions simplify the navigation of regulatory requirements, providing risk assessments, policy development, and ongoing adherence monitoring that cater to the unique needs of various industries. This customized strategy ensures that clients can effectively manage the complexities of regulations while maintaining operational efficiency.
With the crucial deadline for set for December 16, 2024, entities must act quickly. The adherence to CMMC Level 2 requirements necessitates third-party evaluation and certification by a C3PAO, highlighting the significance of external validation in the adherence process. By harnessing advanced technologies and expert insights, Cyber Solutions empowers organizations to maintain a secure environment, allowing them to focus on their core business objectives. The incorporation of these services not only enhances regulatory preparedness but also strengthens the overall cybersecurity posture, establishing businesses as trustworthy allies in the Defense Industrial Base.
Moreover, ongoing training and awareness campaigns are vital components of Level 2 compliance, ensuring that the workforce is equipped with the necessary knowledge to effectively mitigate cyber threats. Cyber Solutions also offers robust incident response capabilities, rapidly identifying, containing, and mitigating threats to restore systems and ensure business continuity.
Understanding the certification tiers is essential:
This comprehensive approach not only prepares organizations for compliance but also fortifies their defenses against evolving cyber threats.
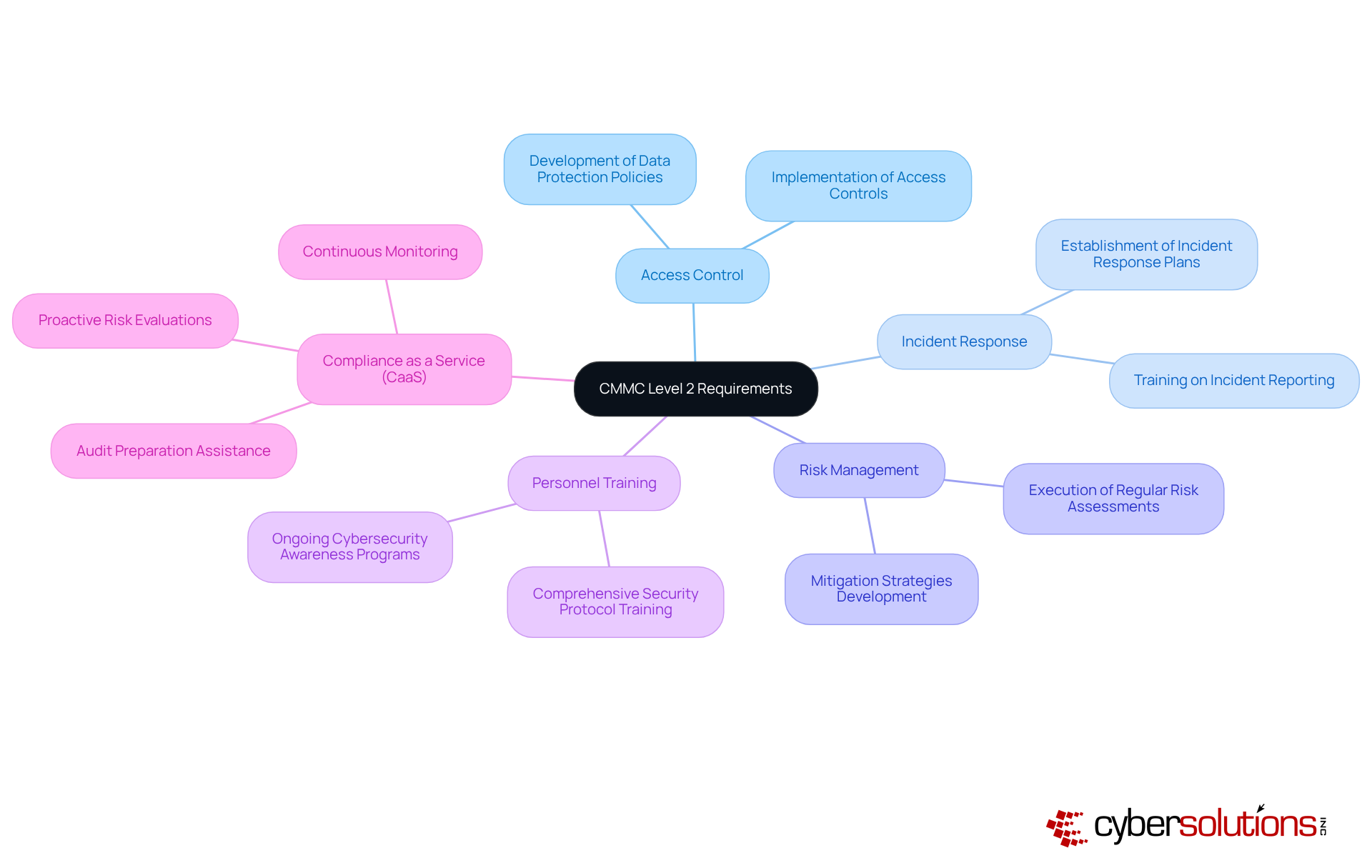
The CMMC Level 2 requirements mandate the implementation of 110 protective measures across various domains, including access control, incident response, and risk management. Key practices encompass:
Notably, entities like Manufacturing Consulting Concepts (MCC) have successfully achieved Level 2 certification, underscoring the effectiveness of these practices. Statistics reveal that organizations with established cybersecurity programs are significantly better equipped to meet these stringent requirements, yet a considerable number of defense contractors remain unprepared for compliance.
C-Suite executives must prioritize understanding the CMMC Level 2 requirements in order to allocate resources effectively and ensure organizational compliance, as certification in this framework is increasingly regarded as a competitive advantage in the defense contracting sector.
To facilitate this, leveraging Compliance as a Service (CaaS) can provide businesses with:
This approach streamlines the regulatory process while mitigating potential fines and ensuring eligibility for lucrative government contracts.
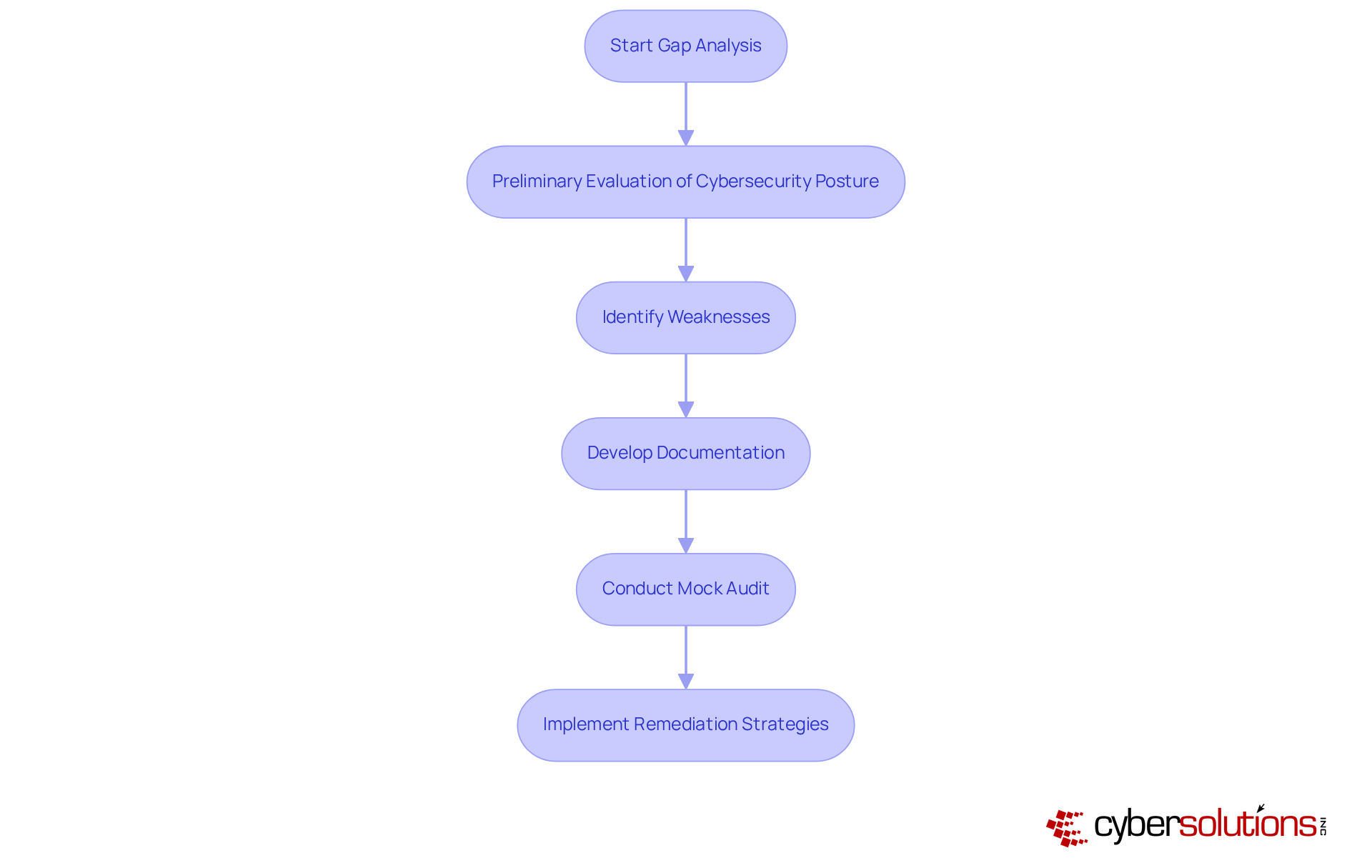
Performing a gap analysis is essential for organizations aiming to achieve Level 2 compliance. This process involves a thorough assessment of existing policies, procedures, and controls against the specific requirements outlined in Level 2. By pinpointing areas of non-compliance, organizations can effectively prioritize their remediation efforts.
Cyber Solutions initiates the process with a preliminary evaluation of your current cybersecurity posture, identifying weaknesses within your systems and providing a roadmap to meet regulatory standards. This includes the development of comprehensive documentation, such as security policies and procedures, to demonstrate compliance during audits. Conducting a mock audit is also vital to ensure your organization is fully prepared for the official CMMC assessment, addressing any outstanding issues.
Understanding their empowers leaders to make informed decisions regarding resource allocation and necessary investments in cybersecurity initiatives. Tailored remediation strategies, including policy updates and system improvements, are crucial for effectively addressing regulatory gaps. Continuous oversight of CMMC changes ensures that organizations remain compliant and ready for future audits.
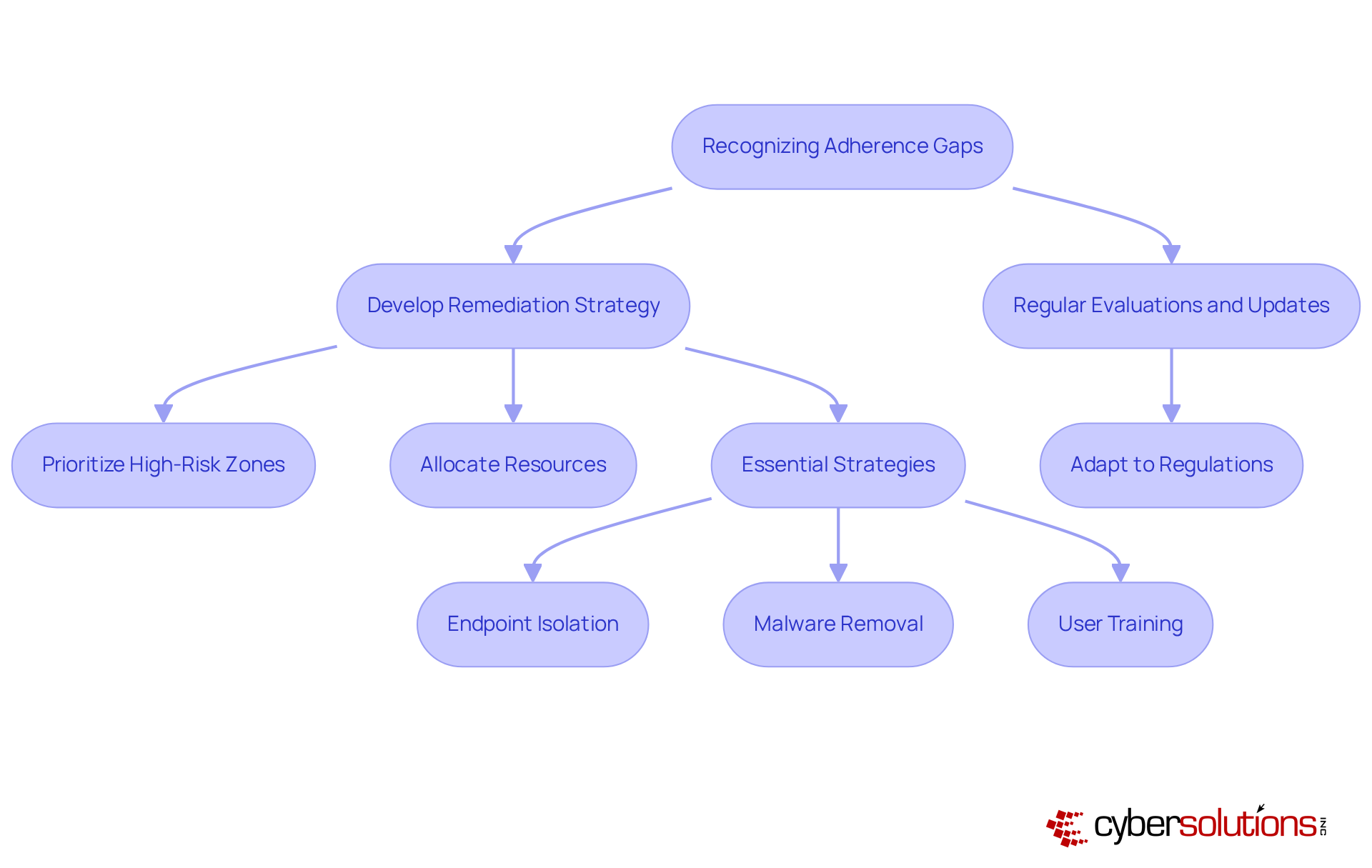
Recognizing adherence gaps is critical; therefore, entities must develop a comprehensive remediation strategy that outlines specific actions, timelines, and assigned responsibilities. This strategy should prioritize , ensuring that resources are allocated efficiently to meet established standards.
Regular evaluations and updates to the remediation plan are vital, allowing organizations to adapt to evolving regulations and emerging cybersecurity threats. Not only do effective remediation plans address regulatory gaps, but they also enhance the overall protective posture through essential strategies such as:
These are fundamental components of a layered security approach. This proactive stance fosters resilience against future risks and strengthens partnerships with cybersecurity providers like Cyber Solutions.
In the realm of healthcare, achieving the CMMC Level 2 requirements is paramount. Entities must deploy a comprehensive suite of protective measures, including access controls, encryption, and incident response protocols. Among these, application allowlisting emerges as a pivotal strategy, proactively thwarting unauthorized or malicious software from executing. This not only reduces the attack surface but also minimizes vulnerabilities, thereby enhancing compliance with standards such as HIPAA, PCI-DSS, and GDPR. Notably, recent assessments reveal high scores in access controls (4.4 ± 0.3) and data integrity measures (4.3 ± 0.3), underscoring the efficacy of these strategies in safeguarding sensitive information and contributing to an overall EHR assessment score of 22 ± 1.5.
To maintain resilience against the ever-evolving landscape of , regular updates and rigorous testing of these controls are essential. A phased approach to compliance with CMMC Level 2 requirements enables organizations to implement necessary measures gradually. The Department of Defense estimates that by the fourth year, approximately 229,818 small entities will be subject to CMMC requirements, highlighting the urgency for organizations to act swiftly to mitigate potential non-compliance risks.
Cybersecurity experts assert that establishing effective security measures is crucial. As Casey Crane aptly stated, "Without trying to be compliant with industry standards, you leave yourself and your sensitive data exposed to potential theft, manipulation, and other forms of compromise." This perspective reinforces the necessity for entities to prioritize robust access controls, encryption methods, and application allowlisting as foundational components of their cybersecurity strategy.
To implement these controls effectively, organizations should concentrate on integrating advanced encryption techniques and establishing clear access protocols tailored to their specific operational needs. This proactive strategy not only ensures adherence but also cultivates trust with stakeholders, positioning the entity as a resilient participant in the defense marketplace.
In today's rapidly evolving landscape of cybersecurity threats, frequent security evaluations—including vulnerability scans and penetration testing—are essential for identifying weaknesses within a business's security framework. These assessments should be conducted at least annually, with an increase in frequency in response to significant organizational changes or emerging threats. As we approach 2025, the shifting environment of cyber threats necessitates continuous assessment to ensure compliance with CMMC Level 2 requirements.
Statistics reveal that organizations conducting can significantly reduce unresolved vulnerabilities. For instance, a midsized healthcare company that transitioned from annual to quarterly testing experienced a remarkable 42% decrease in unresolved issues within just six months. Moreover, with over 25,000 Common Vulnerabilities and Exposures (CVEs) reported in 2022, the urgency for proactive measures is clear.
Cybersecurity analysts assert that vulnerability assessments not only facilitate adherence to the CMMC level 2 requirements but also enhance an organization’s overall security posture by uncovering critical weaknesses before they can be exploited. By integrating these evaluations into their protection strategies, organizations can more effectively adapt to the evolving threat landscape and maintain robust compliance.
Enhancing employee training programs is not just beneficial; it is essential for cultivating a security-conscious culture within organizations. In today's landscape, where cybersecurity threats are ever-evolving, offering regular training sessions on:
is paramount. By empowering employees with the necessary knowledge, companies can significantly reduce the risk of human error and bolster their overall security posture. This proactive approach not only but also instills a sense of responsibility among staff, ultimately leading to a more resilient organization.
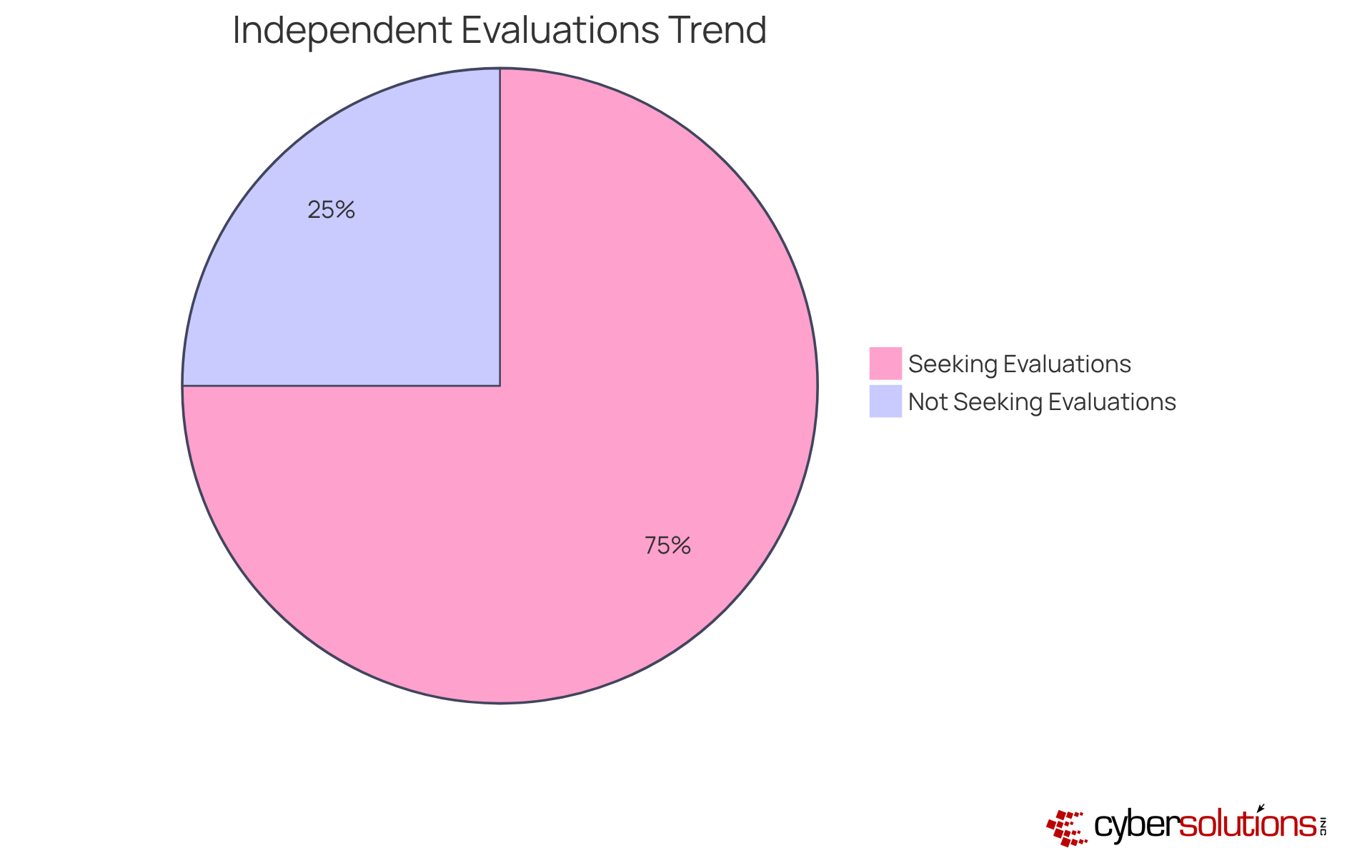
Securing an external evaluation is crucial for validating compliance with the . Engaging an external evaluator delivers an unbiased review of a company's adherence to these standards, pinpointing areas ripe for enhancement while simultaneously serving as a robust demonstration of conformity to clients and regulatory authorities.
It is projected that approximately 70-75% of entities managing Controlled Unclassified Information (CUI) will enlist independent evaluators for their compliance verification, signaling a growing trend toward external validation. Independent evaluations not only bolster adherence but also elevate the overall cybersecurity posture, as organizations receive tailored recommendations that address specific vulnerabilities.
As Tony Giles, Director of Information Security at NSF-ISR, articulates, "We are passionate about this work and proud to take part in it," highlighting the dedication of independent assessors to maintaining stringent standards. By harnessing these evaluations, organizations can adeptly navigate the complexities of CMMC compliance, ensuring they meet the CMMC level 2 requirements while enhancing their operational integrity.
Upon receiving assessment results, entities must swiftly prioritize and address any identified findings. This imperative process often entails:
Timely corrective actions not only bolster a company's protective posture but also ensure with the CMMC Level 2 requirements. As Paul Koziarz emphasizes, without a robust regulatory framework, companies may overlook vital protective measures until it is too late. Richard Clarke further notes the severe consequences of neglecting protection, stating, "If you allocate more for coffee than for IT defense, you will be hacked."
Moreover, the typical duration required to resolve assessment findings can significantly impact a company's overall protection strategy, making prompt responses crucial. By cultivating a culture of continuous improvement and education, entities can effectively mitigate risks and strengthen their resilience against evolving cyber threats.
C-Suite executives should consider:
to ensure their organizations remain proactive in their security initiatives. Additionally, maintaining a specialized incident response team on standby can further enhance recovery efforts, as evidenced by recent case studies where rapid deployment and layered recovery strategies resulted in successful outcomes in the face of ransomware threats.
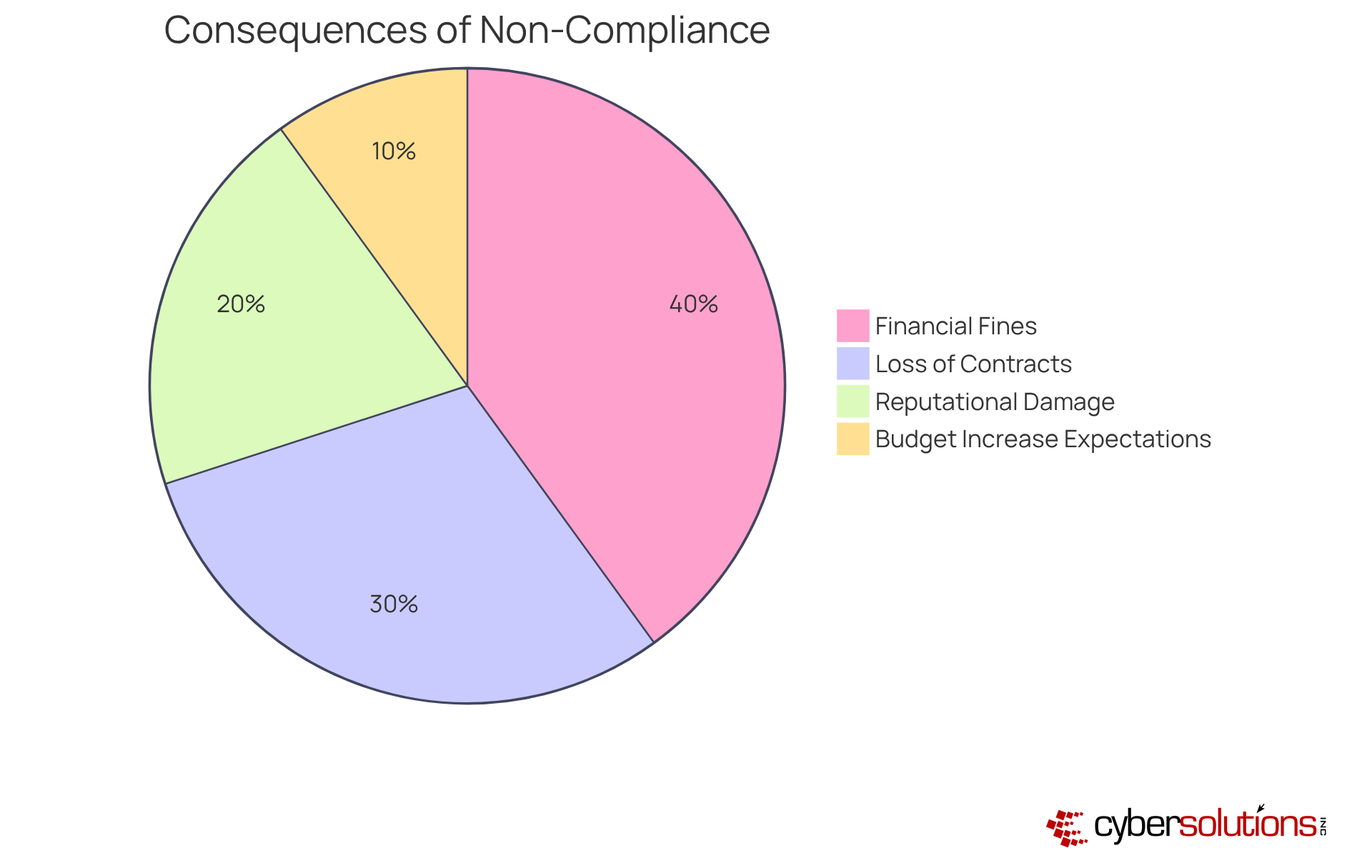
Organizations must recognize the substantial penalties associated with non-compliance with CMMC Level 2 requirements. These penalties can take the form of , loss of eligibility for critical contracts, and severe reputational damage. Notably, around 34% of entities anticipate a lasting budget increase to meet regulatory demands, underscoring the financial repercussions of non-adherence. The risks extend beyond immediate financial consequences; entities that fail to meet CMMC Level 2 requirements may find themselves excluded from lucrative Department of Defense contracts, which jeopardizes their market position and future growth.
Legal experts assert that non-compliance is not merely a regulatory oversight but a potentially business-threatening miscalculation. Financial penalties can soar to $250,000 per violation under the False Claims Act. Entities that have faced fines for inaccurate statements highlight the essential need for robust adherence strategies. By proactively addressing compliance requirements and investing in necessary cybersecurity measures, organizations can mitigate these risks and protect their business interests, ensuring they remain competitive in an increasingly regulated environment.
The significance of CMMC Level 2 compliance cannot be overstated, particularly for organizations operating within the Defense Industrial Base. As the deadline for compliance approaches, C-Suite leaders must prioritize understanding the specific requirements and implement necessary measures to ensure their organizations not only meet but exceed these standards. By doing so, they position their businesses as trustworthy partners, ready to tackle the challenges of a complex regulatory landscape.
Throughout this article, key strategies for achieving CMMC Level 2 compliance have been outlined. From conducting thorough gap analyses and developing robust remediation plans to enhancing employee training and obtaining third-party assessments, each step is crucial in building a resilient cybersecurity framework. Additionally, recognizing the potential penalties for non-compliance serves as a vital reminder of the stakes involved, ensuring that organizations remain vigilant and proactive in their efforts.
In an environment where cyber threats are constantly evolving, the call to action is clear: organizations must invest in comprehensive cybersecurity solutions and foster a culture of security awareness among employees. By embracing these practices, C-Suite leaders can not only safeguard their sensitive information but also enhance their competitive edge in the defense contracting sector. The time to act is now—prioritize CMMC Level 2 compliance and secure a safer future for your organization.
What services does Cyber Solutions Inc. offer for CMMC Level 2 compliance?
Cyber Solutions Inc. offers a range of cybersecurity services, including Adherence as a Service (CaaS), risk assessments, policy development, and ongoing adherence monitoring tailored to meet the unique needs of various industries.
What is the deadline for compliance with CMMC Level 2 requirements?
The deadline for compliance with the CMMC Level 2 cybersecurity framework is December 16, 2024.
What is required for CMMC Level 2 compliance?
CMMC Level 2 compliance requires third-party evaluation and certification by a Certified Third Party Assessment Organization (C3PAO) and involves implementing 110 protective measures across various domains.
What are the key practices included in CMMC Level 2 requirements?
Key practices include developing robust data protection policies, conducting regular risk assessments, and providing comprehensive training for all personnel on security protocols.
How can organizations assess their current compliance status for CMMC Level 2?
Organizations can perform a gap analysis, which involves assessing existing policies, procedures, and controls against CMMC Level 2 requirements to identify areas of non-compliance.
What role does ongoing training play in achieving CMMC Level 2 compliance?
Ongoing training and awareness campaigns are vital for ensuring that the workforce is equipped with the necessary knowledge to effectively mitigate cyber threats.
How can Compliance as a Service (CaaS) benefit organizations?
CaaS can provide continuous monitoring, proactive risk evaluations, and audit preparation assistance, streamlining the regulatory process and helping organizations avoid potential fines.
What is the importance of understanding certification tiers in CMMC?
Understanding certification tiers is essential as it helps organizations recognize the different levels of cybersecurity practices required, from basic to advanced protocols, to protect sensitive data.
What happens if an organization is not prepared for CMMC Level 2 compliance?
Organizations that are unprepared for compliance may face challenges in securing government contracts and could incur fines due to non-compliance with regulatory requirements.