
In today's digital landscape, the importance of selecting a reliable data backup service cannot be overstated. Businesses must prioritize:
These criteria are not merely recommendations; they are essential for ensuring robust protection against data loss and maintaining operational continuity. By adhering to these best practices, organizations can effectively manage the risks associated with cyber threats and data breaches, safeguarding their critical information and ensuring seamless operations.
In an age where data breaches and cyber threats loom larger than ever, the significance of a reliable data backup service is paramount. Businesses face staggering risks; statistics reveal that a considerable percentage of companies experiencing data loss may not survive the aftermath. This article explores best practices for selecting a data backup service, offering insights into essential criteria that ensure robust protection and operational continuity. As organizations navigate an increasingly complex digital landscape, the pressing question remains: how can they effectively safeguard their critical information against unforeseen disasters and cyberattacks?
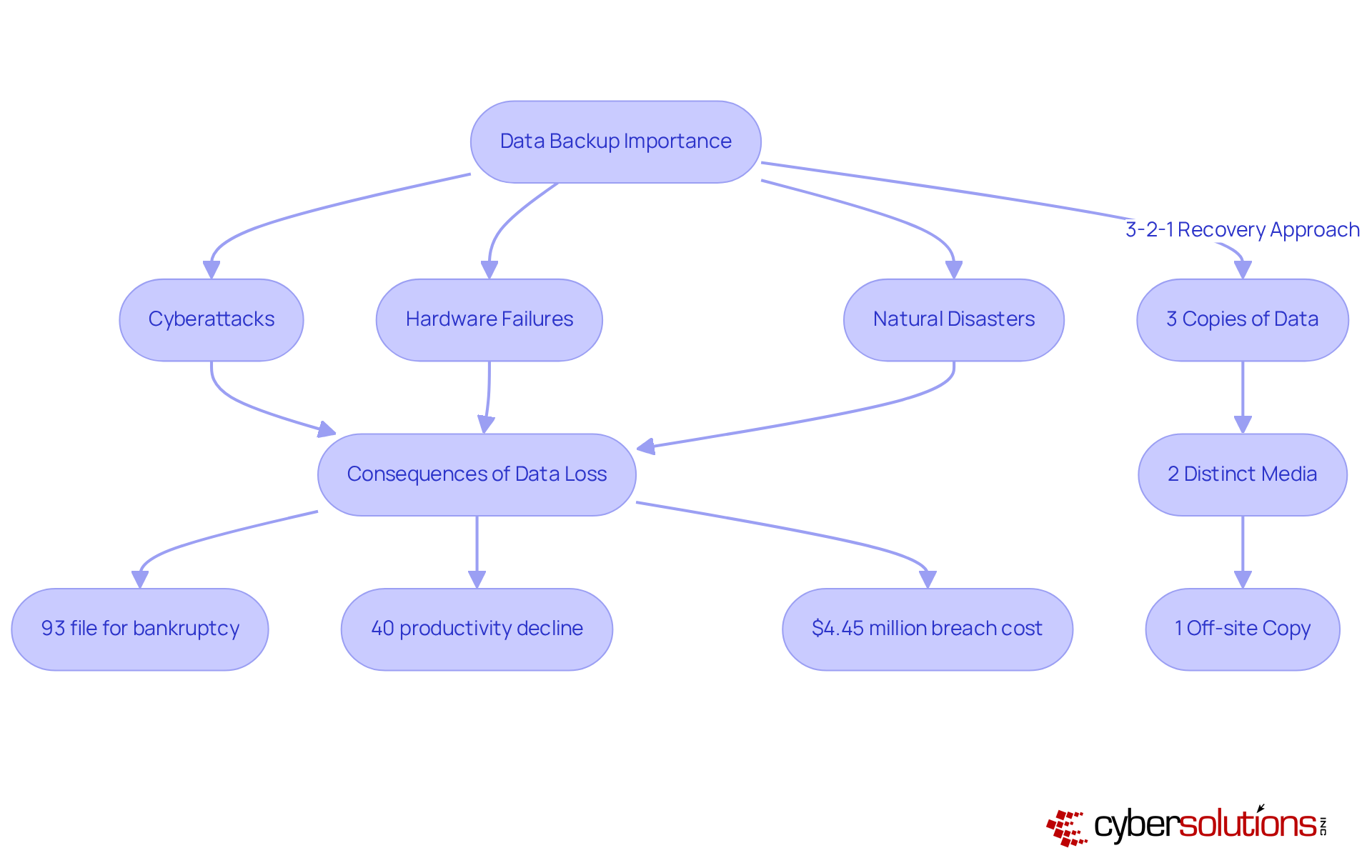
The stands as a pivotal component of any business's IT strategy, serving as a safeguard against losses stemming from cyberattacks, hardware failures, and natural disasters. Alarmingly, 93% of companies that experience prolonged information loss exceeding ten days file for bankruptcy within a year. This statistic underscores the severe repercussions of inadequate information protection. Furthermore, organizations facing significant information loss may suffer productivity declines of up to 40% during recovery phases, a factor that can severely impact operational effectiveness and financial stability. In 2023, the average cost of a data breach reached $4.45 million, illuminating the financial risks associated with information loss.
A well-structured recovery plan, such as the 3-2-1 Data Recovery Approach—which involves maintaining three copies of data on two distinct media, with one copy stored off-site—not only minimizes downtime and facilitates swift restoration but also enhances compliance with industry standards, thereby shielding the organization from potential legal ramifications.
At Cyber Solutions, we provide comprehensive managed IT and cybersecurity services tailored specifically for small to medium enterprises, including:
By prioritizing a data backup service and implementing robust information protection strategies, organizations can ensure operational continuity and safeguard their financial health in an increasingly volatile digital landscape.
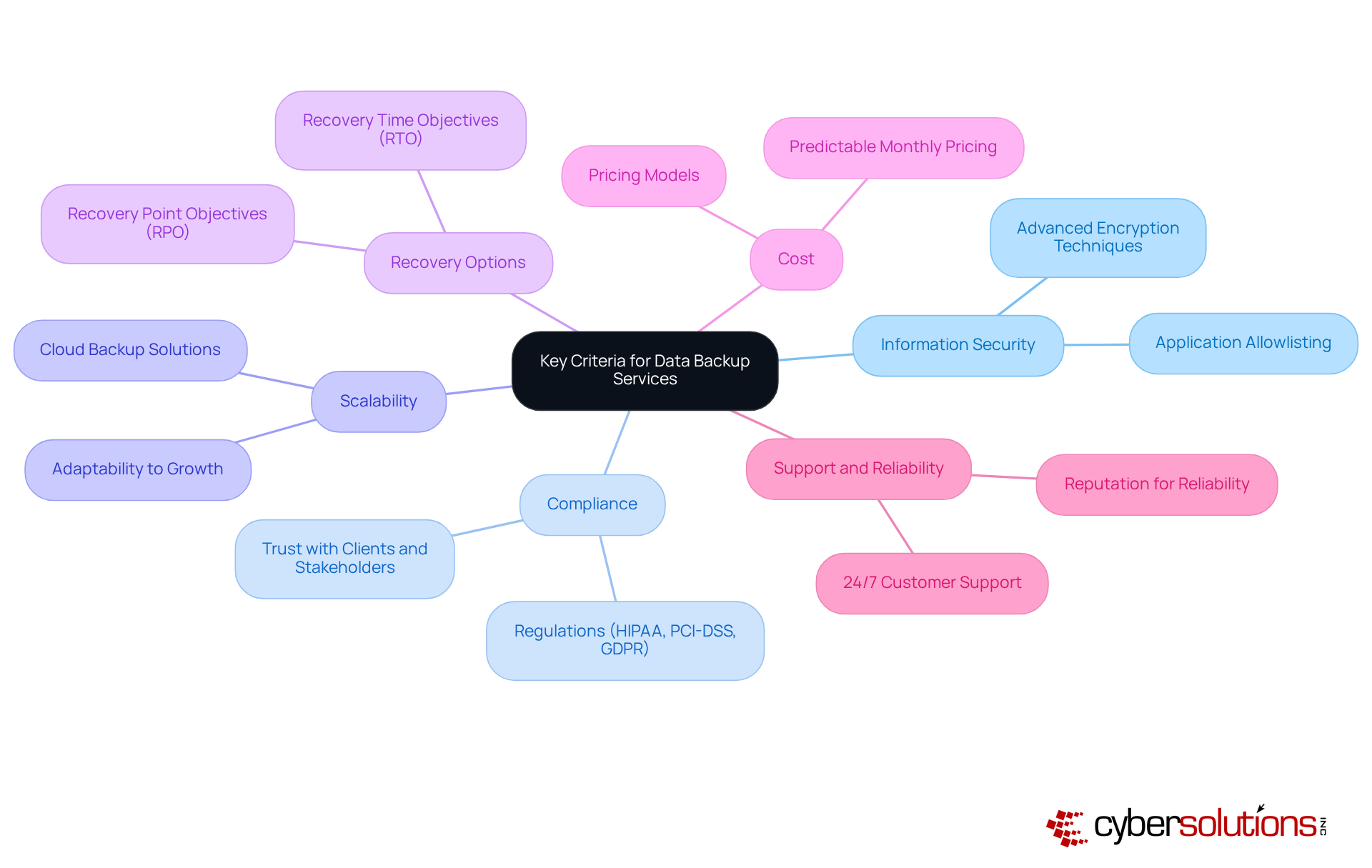
In today's digital landscape, choosing a data backup service is crucial for businesses seeking to guarantee robust protection and compliance. The stakes are high; with 91% of involving data theft and 88% of SMB breaches linked to extortion malware, a strong defense is non-negotiable. Therefore, prioritizing the following essential criteria is critical.
By focusing on these criteria, organizations can significantly enhance their information protection strategies, positioning themselves to effectively confront the evolving landscape of cyber threats.
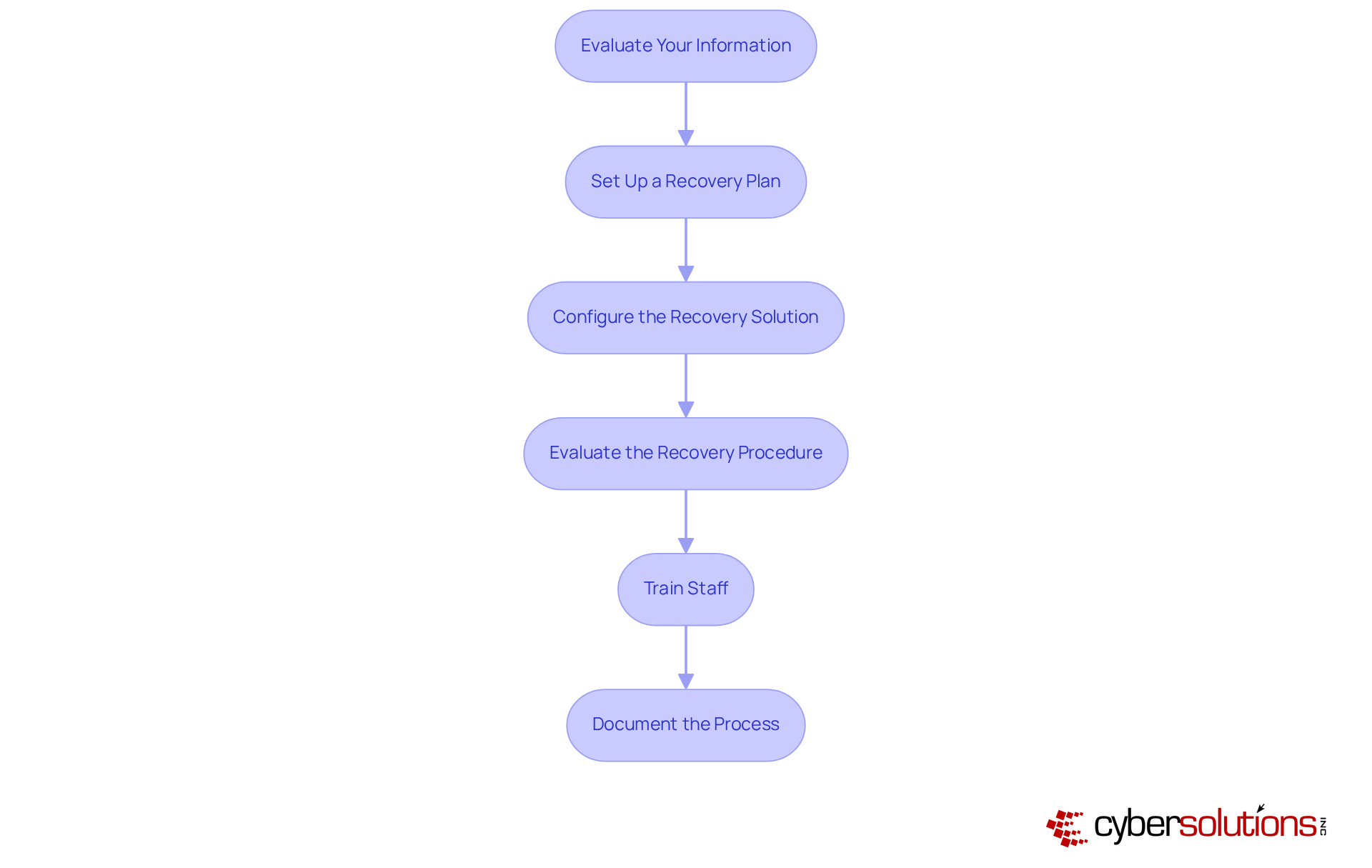
To effectively implement your chosen data backup solution, consider the following steps:
By adhering to these steps, organizations can establish a robust recovery plan that incorporates a data backup service to safeguard essential information and enhance overall operational resilience. As Kyle Andrise points out, "A successful information preservation strategy requires careful planning," and integrating these best practices will ensure your organization is well-prepared.
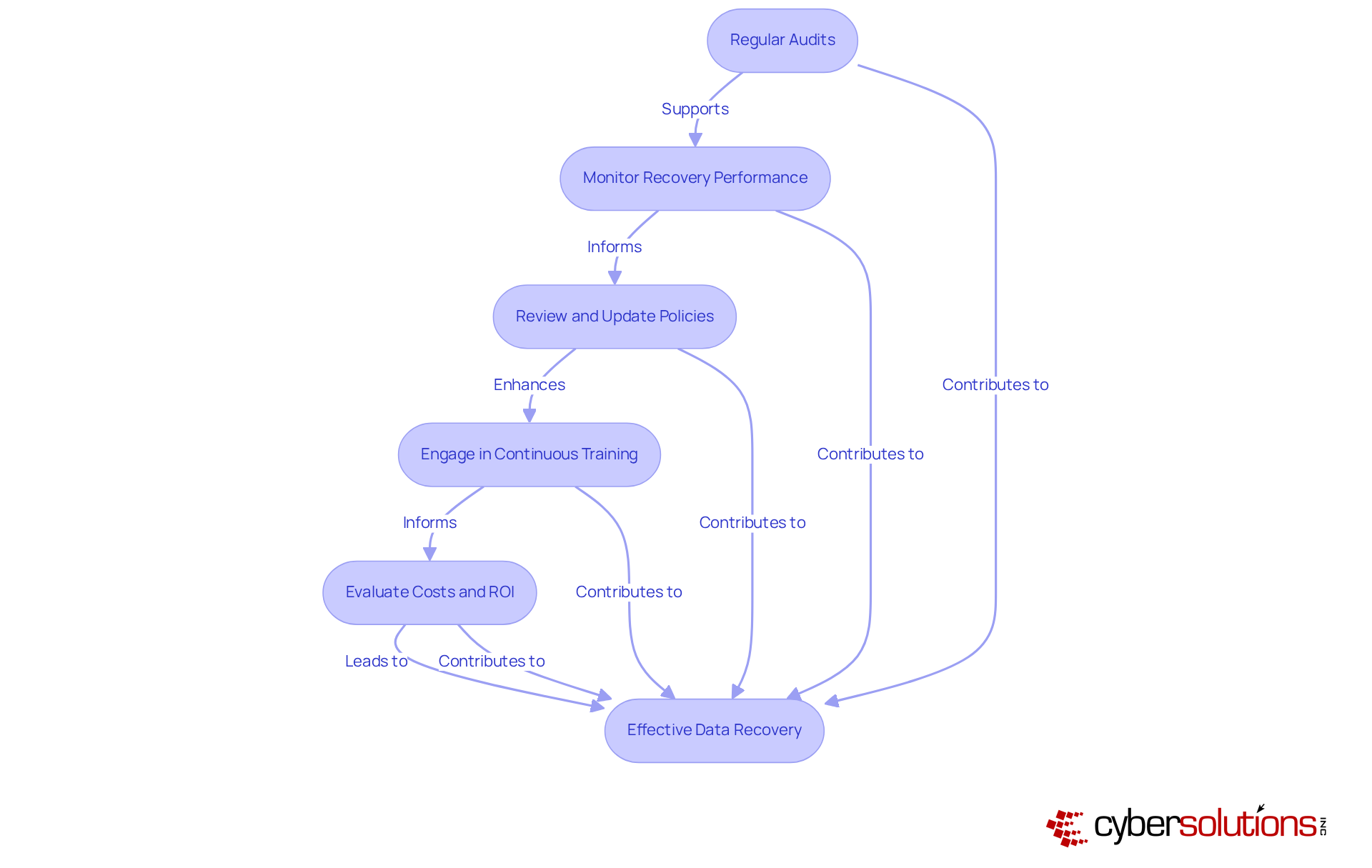
Managing and monitoring your data backup strategy is critical in today’s digital landscape, and it involves several essential practices:
Choosing the right data backup service is not merely a decision; it is a critical imperative for any business intent on safeguarding its vital information and ensuring operational continuity. A robust backup strategy not only mitigates the risks associated with data loss but also fortifies the organization against potential financial repercussions. By prioritizing data backup, businesses can effectively safeguard their assets and maintain trust with clients and stakeholders in an increasingly digital world.
This article underscores several key criteria for selecting a data backup service. It emphasizes the importance of:
These factors contribute to a comprehensive data protection strategy. Moreover, the implementation steps outlined ensure that businesses can seamlessly integrate their chosen backup solutions into their existing operations, thereby enhancing resilience against data loss incidents.
Ultimately, a proactive approach to data backup management is essential. Regular audits, performance monitoring, and continuous staff training are vital practices that empower organizations to stay ahead of potential threats. By embracing these best practices and prioritizing data backup, businesses can not only protect their information but also position themselves for long-term success in a rapidly evolving digital landscape. Taking decisive action today to evaluate and enhance backup strategies will ensure that organizations are well-prepared for the challenges of tomorrow.
Why is data backup important for businesses?
Data backup is crucial for businesses as it protects against losses from cyberattacks, hardware failures, and natural disasters. Without proper data protection, organizations face severe consequences, including potential bankruptcy and significant productivity declines during recovery.
What are the risks of inadequate data protection?
Inadequate data protection can lead to severe repercussions, including bankruptcy for 93% of companies that experience prolonged information loss exceeding ten days. Additionally, organizations may suffer productivity declines of up to 40% during recovery phases.
How much did the average cost of a data breach reach in 2023?
In 2023, the average cost of a data breach reached $4.45 million, highlighting the financial risks associated with information loss.
What is the 3-2-1 Data Recovery Approach?
The 3-2-1 Data Recovery Approach involves maintaining three copies of data on two distinct media, with one copy stored off-site. This strategy minimizes downtime, facilitates swift restoration, and enhances compliance with industry standards.
What services does Cyber Solutions provide related to data backup?
Cyber Solutions offers comprehensive managed IT and cybersecurity services tailored for small to medium enterprises, including 24/7 IT support and proactive monitoring.
How can organizations ensure operational continuity and financial health?
By prioritizing a data backup service and implementing robust information protection strategies, organizations can safeguard their operational continuity and financial health in a volatile digital landscape.