
In today's digital landscape, the importance of robust cybersecurity measures cannot be overstated, particularly for C-suite leaders who are tasked with safeguarding their organizations. The article outlines seven key benefits of SIEM (Security Information and Event Management) technology, emphasizing its critical role in enhancing cybersecurity measures and driving organizational efficiency.
SIEM technology significantly improves threat detection and incident response, streamlining compliance management and operational efficiency. By implementing SIEM, organizations can proactively safeguard sensitive data and effectively reduce the financial impact of cyber incidents. This technology not only addresses the immediate challenges posed by increasing cybersecurity threats but also positions organizations to thrive in a rapidly evolving digital environment.
In an era where cyber threats loom larger than ever, the need for sophisticated security measures is paramount for organizational leaders. Cybersecurity is not just a technical requirement; it is a critical component of operational integrity and trust. As the digital landscape evolves, C-suite leaders face the pressing challenge of selecting the right solutions that not only protect sensitive data but also drive operational efficiency.
SIEM technology emerges as a vital tool, offering a suite of benefits that enhance threat detection, streamline compliance, and bolster overall security operations. What are the key advantages of adopting SIEM technology, and how can it transform the security posture of an organization? By understanding these elements, leaders can make informed decisions that safeguard their organizations against the ever-evolving threat landscape.
In today's digital landscape, the significance of robust cybersecurity measures cannot be overstated. Cyber Solutions Inc. harnesses the power of SIEM technology to dramatically enhance threat detection capabilities. By collecting and analyzing safety-related data across the organization, SIEM systems can identify potential threats in real-time, empowering proactive responses to incidents before they escalate. This capability is critical, especially considering that 77% of companies encountered at least one cybersecurity incident in 2023, underscoring the urgent need for effective protective measures.
To further bolster security, Cyber Solutions provides comprehensive designed to detect anomalies and potential vulnerabilities. This continuous vigilance ensures that suspicious activities are identified and addressed before they evolve into serious risks, specifically shielding your organization from ransomware, phishing, and other malware attacks through real-time alerts and advanced security intelligence.
Organizations that have adopted SIEM technology report marked improvements in their security posture. The latest advancements in this field incorporate artificial intelligence and machine learning capabilities, which enhance threat detection and incident response. These innovations allow organizations to process vast volumes of data—averaging 3.7TB daily—more efficiently, thereby strengthening their capacity to counter sophisticated cyber threats.
Cybersecurity experts emphasize the transformative impact of SIEM technology. Tim de Groot, General Manager at Kaspersky, notes that modern monitoring solutions not only bolster security but also ensure business resilience in an increasingly digital world. By accelerating risk identification and response, organizations can avert costly data breaches and maintain compliance with industry regulations.
In conclusion, this SIEM technology, augmented by Cyber Solutions' extensive 24/7 network monitoring and alert services, serves as a powerful catalyst for organizations aiming to fortify their security frameworks. By leveraging these systems, C-suite leaders can enhance their enterprises' risk detection capabilities, ultimately safeguarding sensitive data and ensuring operational continuity.
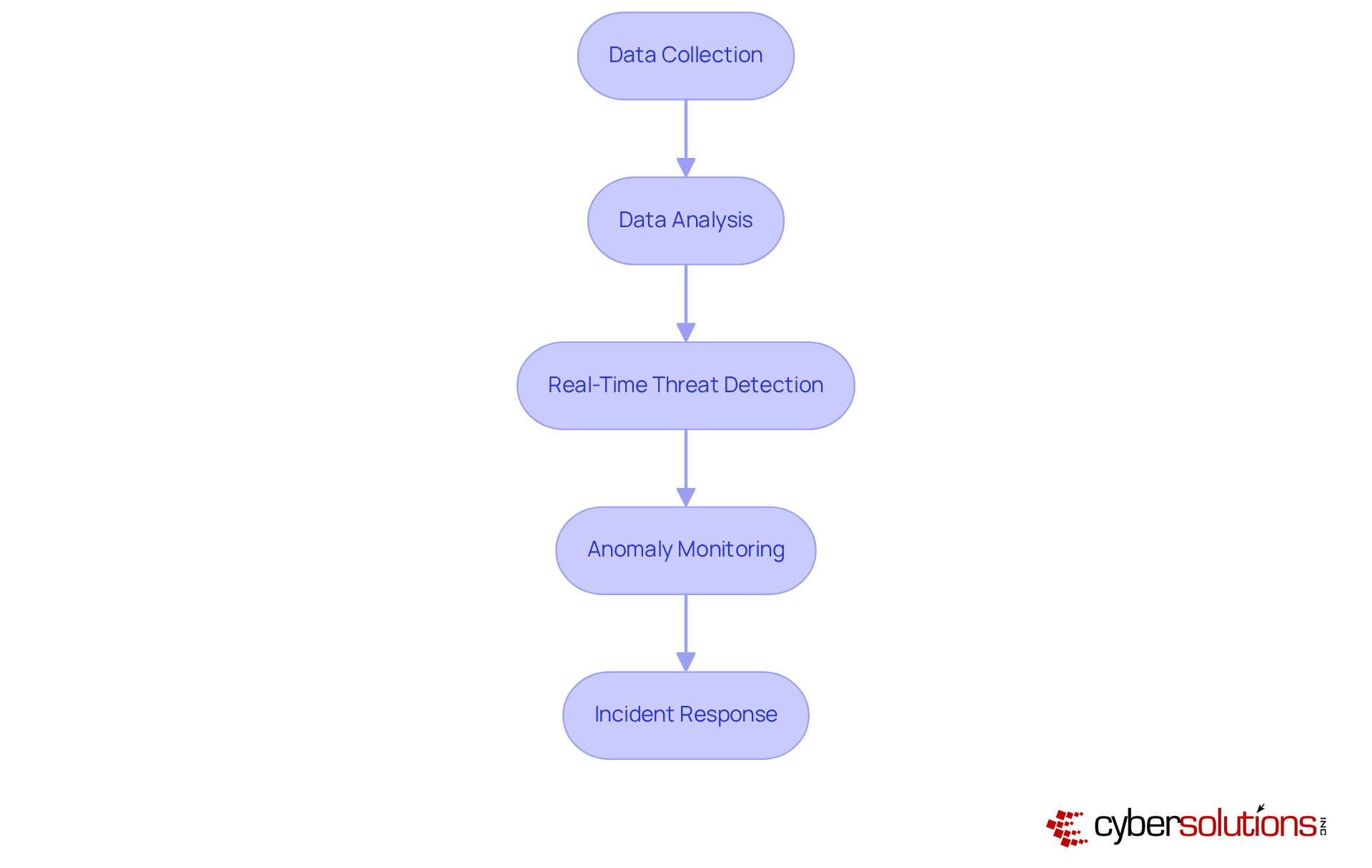
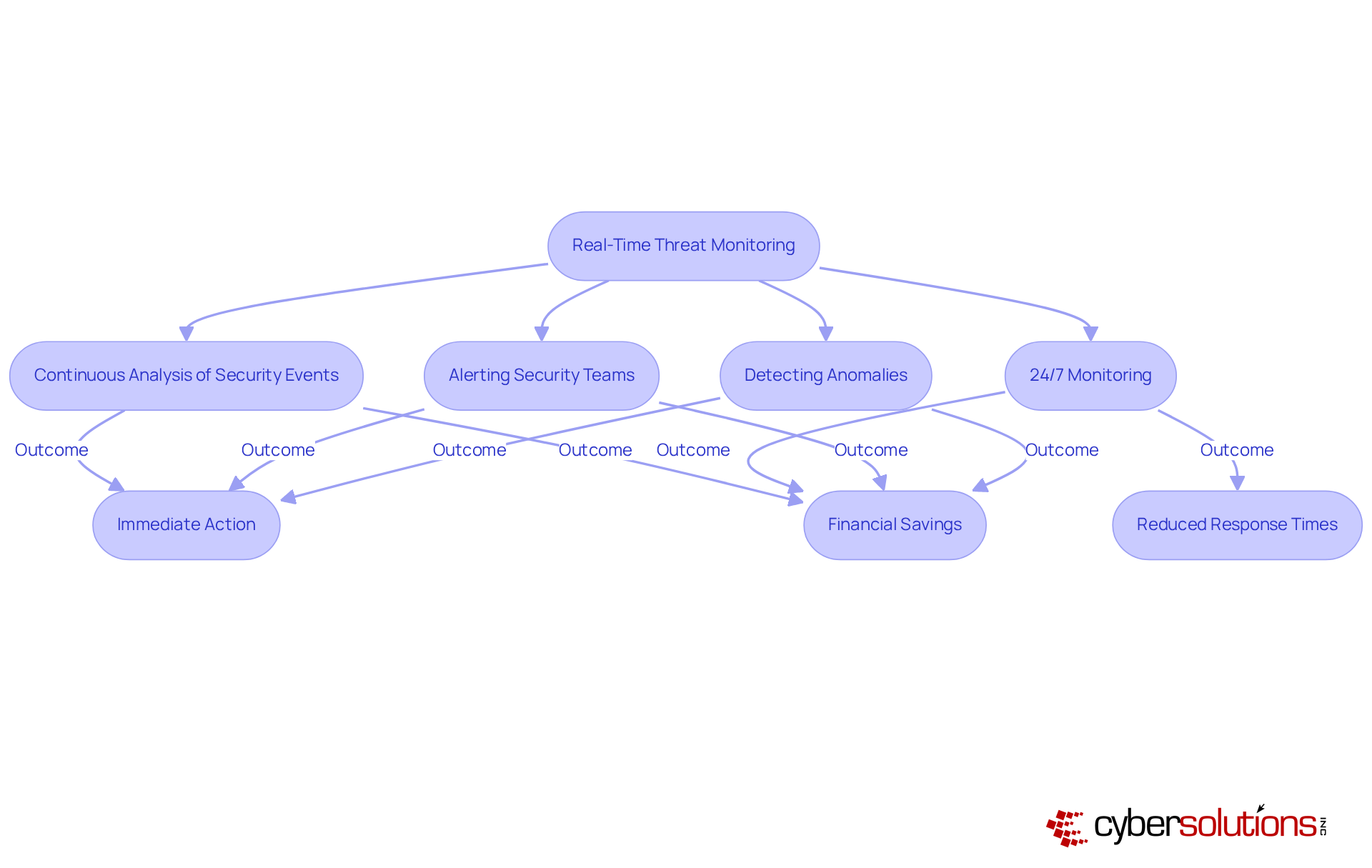
Real-time threat observation is crucial for SIEM technology, empowering organizations to respond instantly to incidents. By continuously analyzing security events, security information and event management systems can swiftly alert security teams to suspicious activities, significantly reducing average response times.
With , organizations can detect anomalies and potential vulnerabilities in real-time, facilitating immediate action to avert downtime or breaches. Notably, entities leveraging AI-enhanced security information and event management solutions have reported average savings of USD 1.76 million in data breach containment, underscoring the financial advantages of prompt response capabilities.
C-suite executives must prioritize investments in monitoring solutions that feature robust real-time tracking and customized access controls, as these elements are vital for mitigating the impact of potential breaches and maintaining a proactive defense posture.
Importantly, organizations that have effectively integrated SIEM technology have demonstrated improved incident response times, emphasizing the critical need for swift action in today’s evolving threat landscape. The necessity of having an incident response team prepared to act within 24 hours cannot be overstated; this readiness significantly bolsters recovery efforts and enhances overall cybersecurity confidence.
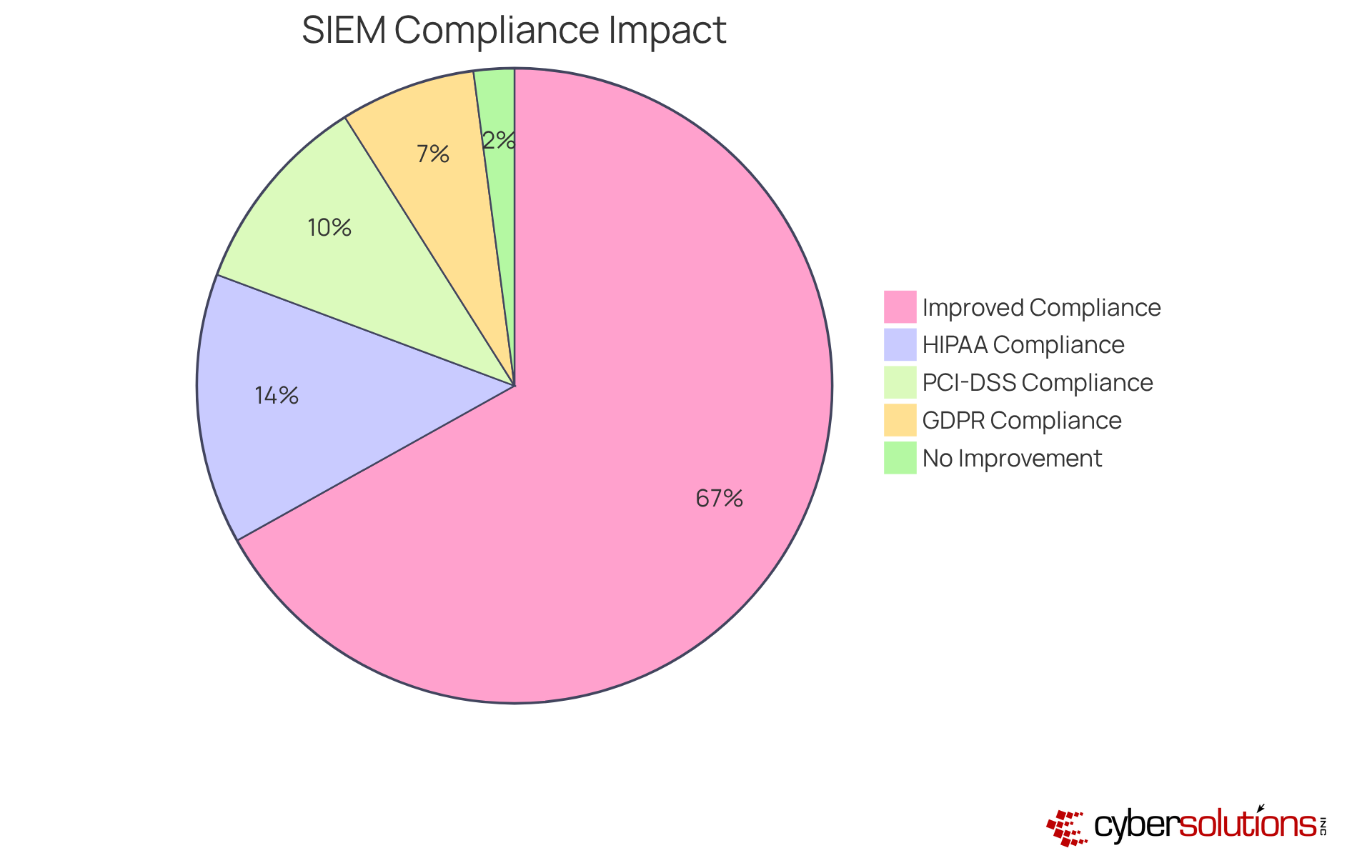
SIEM technology is paramount for effective compliance administration, automating the collection and analysis of security data necessary for regulatory reporting. By leveraging these solutions, companies can streamline their compliance processes, ensuring adherence to industry standards such as HIPAA, PCI-DSS, and GDPR. This automation significantly alleviates the , empowering C-suite leaders to allocate resources more efficiently and concentrate on core business operations while fulfilling regulatory obligations.
Industry leaders underscore the critical role of SIEM technology in automating regulatory compliance. Notably, entities utilizing these systems have reported a remarkable enhancement in their compliance posture, with 97% of users indicating improved security and compliance strategies. Furthermore, a substantial number of organizations have achieved compliance standards through SIEM technology, illustrating its effectiveness in meeting regulatory requirements.
Real-world examples illustrate how organizations have adeptly optimized their compliance with regulations through security information and event management. By centralizing logs and automating reporting processes, these entities not only bolster their compliance capabilities but also mitigate risks associated with non-compliance, which can lead to significant financial penalties. As cyber risks evolve, the ability of SIEM technology to provide real-time monitoring and automated alerts becomes increasingly vital for maintaining compliance and protecting sensitive information.
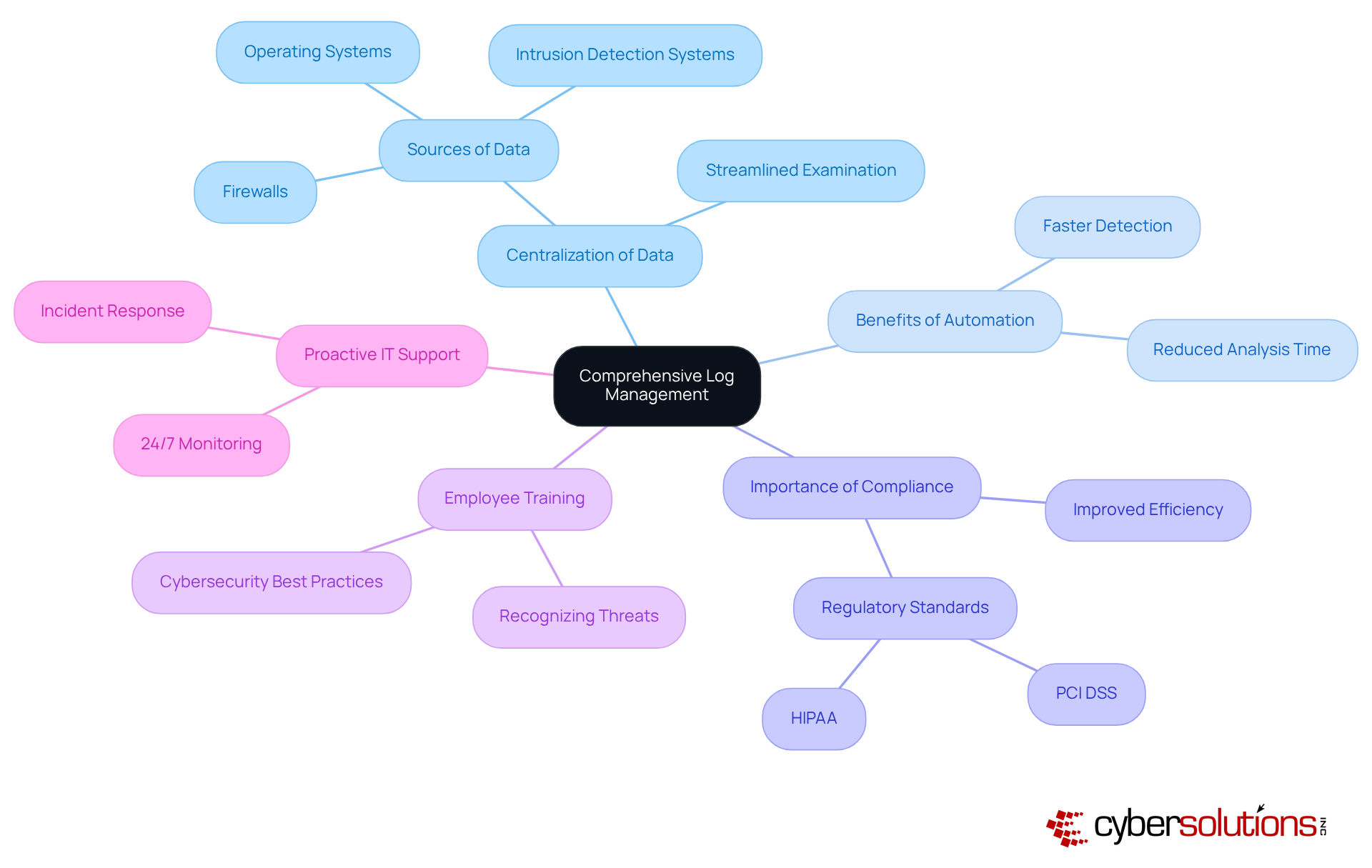
In today's digital landscape, thorough log management is a cornerstone of SIEM technology for effective security information and event management. It empowers organizations to centralize data from diverse sources, including operating systems, firewalls, and intrusion detection systems. This centralization not only streamlines the examination and correlation of incidents but also enables teams to swiftly identify and respond effectively. For C-suite executives, investing in SIEM technology equipped with robust log management features is crucial for enhancing operational safety and achieving comprehensive insights into the organization’s security posture.
By automating log reviews and leveraging advanced analytics, companies can significantly decrease the time spent on security data analysis, leading to faster detection and response to incidents. Notably, organizations that embrace centralized log management report improved efficiency in threat detection and compliance with regulatory requirements, ultimately safeguarding sensitive data and mitigating operational risks. Daily log analysis is essential for maintaining compliance with PCI DSS and HIPAA standards, particularly for entities in regulated industries.
Given that nearly every corporation in the U.S. faces daily threats from malicious attacks, prioritizing SIEM technology for security information and event management solutions has never been more vital. Furthermore, investing in IT services that bolster operational efficiency and minimize costly downtime—such as 24/7 IT Support and Proactive Monitoring—is critical for maximizing ROI, especially for small to medium-sized businesses.
Regular log reviews are indispensable for identifying errors, anomalies, or suspicious activities, underscoring the continuous nature of effective log management. Additionally, equipping personnel with the skills to recognize questionable emails and adhere to cybersecurity best practices is essential for strengthening overall security measures. As organizations navigate the complexities of cybersecurity, a strategic focus on log management and proactive IT support will pave the way for a more secure future.
Event correlation is a pivotal element of SIEM technology, empowering organizations to discern patterns and connections among incidents. By meticulously analyzing these correlations, security teams can uncover sophisticated risks that may remain hidden when reviewing isolated data points. Continuous monitoring is vital in this endeavor, ensuring that suspicious activities are detected and mitigated before they escalate into threats.
Research reveals that a substantial portion of advanced risks is uncovered through , which highlights the significance of SIEM technology in contemporary cybersecurity strategies. For C-suite leaders, grasping the value of event correlation is crucial for making informed decisions regarding security investments and resource allocation.
Cybersecurity professionals emphasize that leveraging SIEM technology for event correlation not only enhances vulnerability detection capabilities but also streamlines incident response processes, enabling organizations to react swiftly to potential breaches.
Real-world examples demonstrate how entities have successfully identified advanced threats through event correlation, reinforcing SIEM technology as a cornerstone of proactive cybersecurity measures.
AI-driven automation is revolutionizing operational processes within SIEM technology, enhancing efficiency by streamlining routine tasks such as log analysis and incident response. This transformative automation from hours to mere minutes, empowering security teams to focus on more complex challenges. For C-suite leaders, the integration of AI not only optimizes resource allocation but also leads to substantial cost savings, as organizations can effectively minimize downtime and operational disruptions.
Moreover, automated workflows enable teams to act swiftly, often initiating immediate alerts and responses within seconds of detecting an issue. This rapid response not only accelerates the Mean Time to Recovery (MTTR) but also minimizes errors by performing consistently without the drawbacks of human fatigue or bias. Continuous monitoring of networks ensures that dubious activities are identified and halted before they escalate into significant threats, thereby safeguarding businesses from ransomware, phishing, and other malware attacks.
As organizations increasingly adopt AI-powered dashboards, they gain real-time insights into vulnerabilities and risk trends, facilitating quicker decision-making and a proactive defense posture. Industry leaders emphasize that SIEM technology and intelligent automation are transforming cybersecurity from a reactive to a proactive strategy, ensuring that organizations remain resilient against evolving threats. By leveraging advanced technologies, including Cyber Solutions' comprehensive monitoring and layered recovery strategies, companies can significantly enhance their overall protection framework while optimizing operational efficiency.
However, it is crucial to acknowledge the challenges organizations face when implementing AI in cybersecurity. Ongoing training and human oversight are essential to mitigate potential biases and ensure effective collaboration between analysts and automated systems. Furthermore, access controls tailored to business requirements enhance protection, ensuring that only authorized users have entry.
Forensic investigations are a cornerstone of SIEM technology, enabling organizations to conduct comprehensive analyses of incidents. By pinpointing root causes, these entities can implement proactive strategies to mitigate the risk of recurrence. Notably, around 90% of organizations report engaging in after incidents, underscoring its pivotal role in fortifying security posture.
C-suite executives must prioritize the integration of forensic capabilities into their SIEM technology solutions, thereby cultivating a culture of continuous improvement and resilience against the ever-evolving landscape of cyber threats.
For instance, a prominent retail firm adeptly utilized SIEM technology to scrutinize a phishing attack, leading to strengthened defenses and a marked reduction in similar incidents. By harnessing these insights, organizations can not only respond adeptly to breaches but also bolster their overall security framework.
(UEBA) represents a significant advancement in SIEM technology, specifically designed to detect anomalies in user activity. By establishing behavioral baselines, organizations can swiftly detect unusual activities that may signal internal risks or compromised accounts. This proactive strategy is vital, particularly in sectors like healthcare, where minimizing operational disruption is essential. Studies reveal that a notable percentage of insider threats—often estimated at around 30%—are effectively identified through UEBA solutions.
For C-suite leaders, integrating UEBA into defense frameworks transcends mere technical enhancement; it emerges as a strategic imperative. As cybercriminals increasingly leverage sophisticated tactics, including AI-driven phishing schemes and deepfake social engineering, the capability to monitor and analyze user behavior becomes indispensable. Experts assert that SIEM technology, including UEBA tools, provides invaluable insights, enabling organizations to manage user activity data and discern unusual patterns that may indicate potential threats. This is particularly critical for healthcare providers, who must balance operational continuity with a robust protective posture.
Real-world applications of UEBA underscore its efficacy. For instance:
These instances illustrate the transformative impact of UEBA and SIEM technology in enhancing protective strategies, safeguarding sensitive information, and ultimately preserving organizational integrity in an increasingly complex cyber landscape. Furthermore, the global UEBA market is projected to expand at a CAGR of 33.4%, highlighting the growing significance of UEBA in cybersecurity strategies.
Incorporating incident response functions within monitoring technology is crucial for efficiently coordinating actions during threat events. This integration empowers protection teams to react promptly and effectively, significantly minimizing the potential impact of incidents on the organization.
Studies indicate that companies leveraging SIEM technology can by as much as 60%, facilitating quicker risk management. C-suite executives must prioritize monitoring solutions that seamlessly integrate incident response capabilities; this not only enhances the organization’s defensive posture but also fosters a proactive approach to threat management.
For instance, organizations that have successfully implemented unified threat monitoring systems report improved coordination during incidents, leading to more effective event management and reduced operational disruptions.
Expert insights underscore the importance of this integration, emphasizing that a well-coordinated response can conserve valuable time and resources, ultimately safeguarding the organization’s assets and reputation.

Adopting monitoring technology is essential for significantly improving organizational efficiency through refined protective measures. By providing thorough insight into threat events and automating vital processes, monitoring solutions empower entities to operate more efficiently while upholding stringent protective standards. For C-suite leaders, grasping the impact of siem technology on operational efficiency is crucial for making informed decisions regarding cybersecurity investments and strategies.
Studies indicate that organizations utilizing event management systems can substantially reduce operational expenses related to incidents. By automating manual tasks and enhancing incident response times, businesses can save an average of USD 1.76 million compared to those that do not leverage such technologies. Furthermore, siem technology solutions play a pivotal role in fulfilling regulatory obligations, particularly in sectors like healthcare and finance, where compliance with standards is paramount.
Numerous organizations have effectively strengthened their protective posture and operational efficiency through the implementation of siem technology. A recent case study in the healthcare sector exemplifies this; a provider not only recovered from a ransomware attack more quickly than anticipated but also improved its protective measures through a systematic response plan and a layered recovery strategy. This underscores the critical importance of specialized knowledge and teamwork in combating cyber threats.
Industry leaders emphasize the importance of siem technology in enhancing security frameworks. Experts note that siem technology not only improves visibility into network activities but also facilitates rapid responses to unusual behaviors and potential attacks. This proactive approach is vital for associated with the ever-evolving landscape of cyber threats.
In summary, strategically adopting siem technology is crucial for C-suite leaders seeking to strengthen their organization's security posture while maximizing operational efficiency, particularly through effective incident response strategies and proactive security measures.
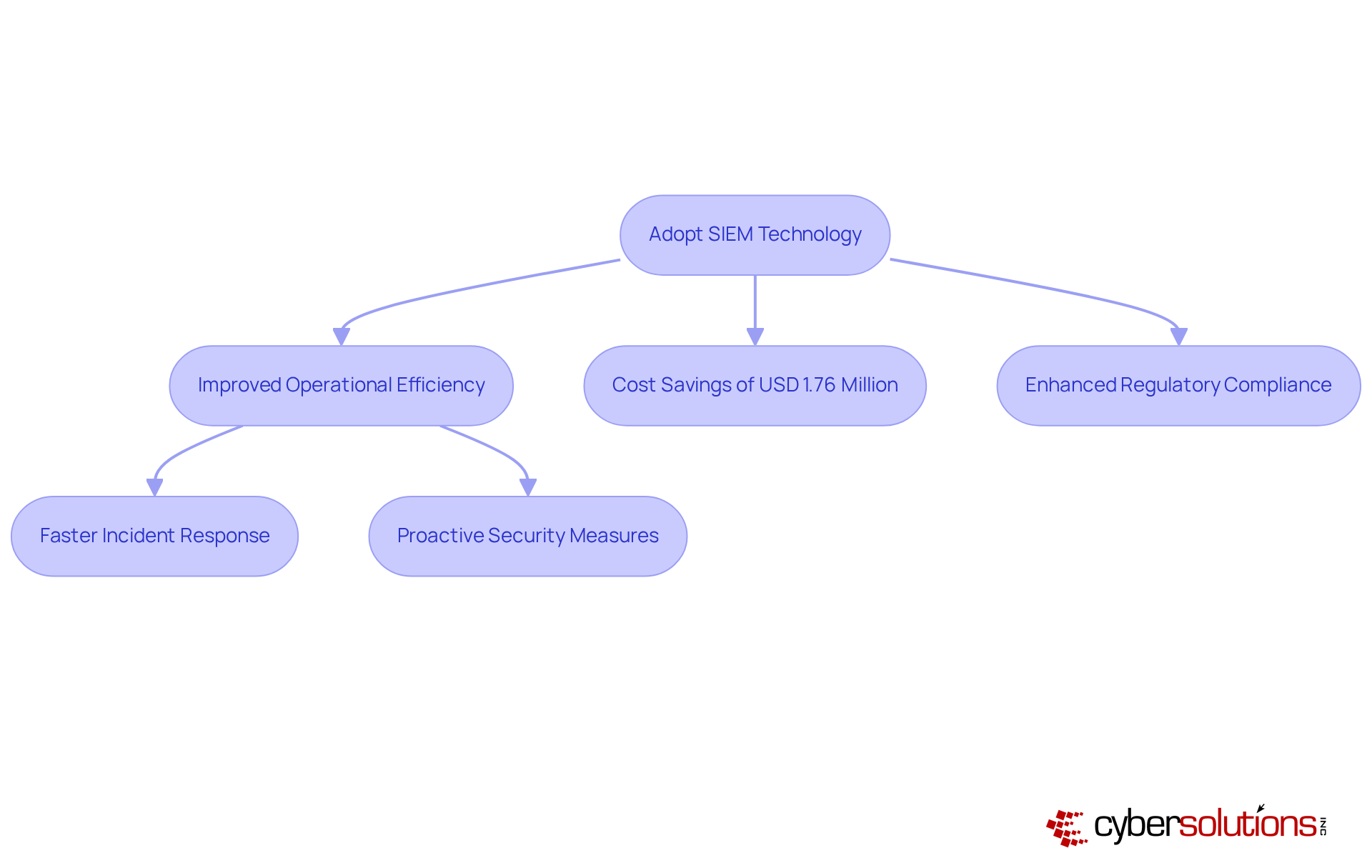
The integration of SIEM technology stands as a crucial advancement for C-suite leaders committed to fortifying their organizations' cybersecurity frameworks. By harnessing the capabilities of Security Information and Event Management systems, executives can significantly enhance threat detection, streamline compliance processes, and cultivate a proactive approach to incident response. This technology not only strengthens defenses against cyber threats but also ensures that businesses remain resilient in an increasingly intricate digital landscape.
Throughout this discussion, the key benefits of SIEM technology have been illuminated, including:
The incorporation of AI-driven automation further amplifies the efficiency of security operations, enabling organizations to respond swiftly to incidents and mitigate potential damages. Moreover, the role of user and entity behavior analytics (UEBA) in detecting anomalies underscores the multifaceted capabilities of SIEM solutions in protecting sensitive information.
In a climate where cybersecurity incidents are escalating, the importance of adopting SIEM technology cannot be overstated. C-suite leaders are urged to prioritize investments in these systems, not only to shield their organizations from immediate threats but also to foster a culture of continuous improvement and resilience. By embracing SIEM solutions, businesses can adeptly navigate the evolving threat landscape, ensuring operational continuity and safeguarding their most valuable assets.
What is SIEM technology and how does it enhance threat detection?
SIEM technology collects and analyzes safety-related data across an organization to identify potential threats in real-time, enabling proactive responses to incidents before they escalate.
Why is real-time threat monitoring important?
Real-time threat monitoring allows organizations to respond instantly to security incidents by continuously analyzing security events and swiftly alerting security teams to suspicious activities, significantly reducing response times.
How does Cyber Solutions Inc. utilize SIEM technology?
Cyber Solutions Inc. uses SIEM technology to enhance threat detection capabilities and provides 24/7 network monitoring to detect anomalies and potential vulnerabilities, protecting against ransomware, phishing, and other malware attacks.
What benefits do organizations experience by adopting SIEM technology?
Organizations that adopt SIEM technology report improvements in their security posture, including enhanced threat detection and incident response capabilities, often aided by artificial intelligence and machine learning.
What financial advantages come from using AI-enhanced SIEM solutions?
Entities using AI-enhanced SIEM solutions have reported average savings of USD 1.76 million in data breach containment, highlighting the financial benefits of prompt response capabilities.
How does SIEM technology assist with compliance management?
SIEM technology automates the collection and analysis of security data necessary for regulatory reporting, streamlining compliance processes and helping organizations adhere to standards like HIPAA, PCI-DSS, and GDPR.
What impact does SIEM technology have on compliance posture?
Organizations utilizing SIEM technology have reported significant improvements in their compliance posture, with 97% of users indicating enhanced security and compliance strategies.
How can organizations mitigate risks associated with non-compliance using SIEM technology?
By centralizing logs and automating reporting processes, organizations can bolster their compliance capabilities and reduce risks related to non-compliance, which can result in financial penalties.
What is the importance of having an incident response team prepared to act?
Having an incident response team ready to act within 24 hours is crucial as it significantly bolsters recovery efforts and enhances overall cybersecurity confidence in the face of evolving threats.