
Artificial intelligence significantly enhances cybersecurity solutions, particularly through its improved threat detection and response capabilities. This advancement allows organizations to proactively identify and mitigate risks, a necessity in today's rapidly evolving threat landscape.
For instance, companies such as Cyber Solutions Inc. and Darktrace are effectively leveraging AI-driven analytics to scrutinize vast datasets in real-time. This capability not only accelerates the identification of potential threats but also reduces incident response times, thereby fortifying overall security measures.
In an era where cybersecurity is paramount, the integration of AI is not just beneficial; it is essential for organizations aiming to safeguard their assets and data.
In an era marked by increasingly sophisticated cyber threats, the integration of artificial intelligence into cybersecurity solutions stands as a pivotal advancement for organizations across diverse sectors. This article delves into ten innovative ways AI bolsters cybersecurity measures, ranging from proactive threat detection to streamlined incident response, equipping businesses with a formidable defense against ever-evolving risks.
As these technologies continue to evolve, organizations must confront essential challenges and considerations to fully harness the potential of AI within their cybersecurity strategies.
In today's digital landscape, the significance of robust cybersecurity measures cannot be overstated, particularly within the healthcare sector. Cyber Solutions Inc. harnesses the power of artificial intelligence and cybersecurity to significantly enhance its risk detection and response capabilities. By employing sophisticated machine learning algorithms, the firm can swiftly analyze vast datasets in real-time, enabling the identification of potential risks before they escalate into serious incidents. This proactive strategy not only mitigates the risk of data breaches but also bolsters such as HIPAA, PCI-DSS, and GDPR, thereby protecting clients' financial investments in digital security.
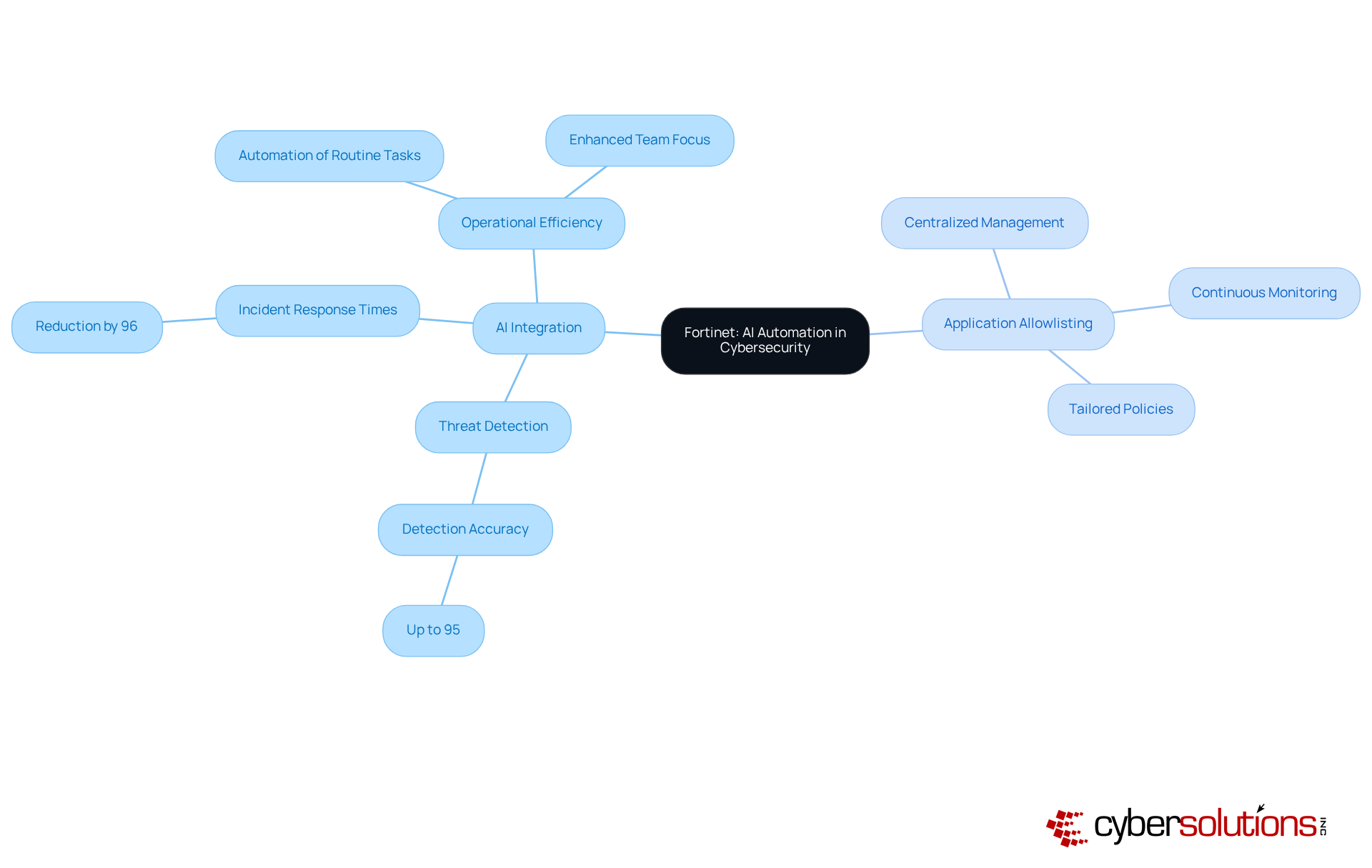
Application allowlisting is integral to this framework, proactively preventing unauthorized software from executing and thereby reducing the attack surface and minimizing vulnerabilities. For instance, AI-powered attack detection systems can identify cyber intrusions up to 60% faster than traditional methods, facilitating rapid responses such as isolating compromised systems or blocking malicious traffic. Moreover, the integration of artificial intelligence and cybersecurity into security solutions empowers organizations to implement preventive measures based on predictive analytics, effectively anticipating potential vulnerabilities before they can be exploited.
As the risk landscape continues to evolve, the adoption of artificial intelligence and cybersecurity technologies, along with application allowlisting, becomes increasingly essential for maintaining robust security frameworks and ensuring operational resilience. Notably, companies that leverage AI and automation in digital security realize an average savings of $2.2 million compared to those that do not, underscoring the financial benefits of these technologies. The escalating complexity of digital threats, including the rise of AI-driven malware, underscores the urgent need for advanced solutions in artificial intelligence and cybersecurity.
As Stephen Kines, COO of Cyber Solutions Inc., aptly states, "To combat these intelligent risks, businesses must embrace a multilayered strategy that integrates artificial intelligence and cybersecurity with proactive risk mitigation techniques, such as application allowlisting." This comprehensive approach not only addresses current challenges but also positions organizations to thrive in an increasingly perilous digital environment.

Darktrace harnesses the power of autonomous AI, which is a key component of artificial intelligence and cybersecurity, to deliver robust real-time risk response capabilities. By continuously analyzing the typical behavior patterns within an organization, this self-learning technology can autonomously identify and mitigate anomalies, effectively minimizing risks before they escalate. This not only strengthens protective measures but also lessens the necessity for constant human oversight, enabling teams to concentrate on strategic initiatives.
Notably, 78% of Chief Information Security Officers recognize the significant influence of risks related to artificial intelligence and cybersecurity, underscoring the increasing acknowledgment of the effectiveness of such autonomous systems within the industry. As organizations face a surge in advanced cyber threats, Darktrace's AI, which operates at the capacity of 30 additional security analysts, underscores its critical role in enhancing operational efficiency and resilience in the context of artificial intelligence and cybersecurity against evolving cyber dangers.

In today's digital landscape, the importance of robust cybersecurity cannot be overstated, particularly within the realm of healthcare. CrowdStrike leverages artificial intelligence to significantly bolster its endpoint security and intelligence capabilities. By meticulously analyzing patterns and behaviors, the platform identifies and responds to threats in real-time—an essential strategy for minimizing breach risks. This proactive approach not only protects sensitive data but also ensures compliance with regulatory standards, thereby enhancing organizational integrity.
Looking ahead to 2025, the integration of AI in risk intelligence is projected to evolve further, introducing innovations that improve detection accuracy and response times. Experts highlight that the intersection of artificial intelligence and cybersecurity is revolutionizing how organizations spot anomalies and anticipate potential threats in digital security. Additionally, the critical role of application allowlisting cannot be overlooked; it stands as a gold standard in cybersecurity by preemptively blocking malware and unauthorized software from executing. This strategy effectively and aids organizations in adhering to stringent compliance standards, ensuring that only authorized applications are permitted to operate.
Key features of application allowlisting include:
As organizations navigate an ever-evolving risk landscape, investing in platforms that utilize artificial intelligence and cybersecurity, such as CrowdStrike's solution combined with robust application allowlisting strategies, is increasingly recognized as essential for maintaining strong protective measures.
In today's rapidly evolving digital landscape, the significance of robust cybersecurity cannot be overstated. IBM Security's Watson AI is at the forefront of this transformation, revolutionizing risk management through advanced analytics and insights. By leveraging natural language processing and machine learning, Watson meticulously analyzes vast amounts of security information. This enables the detection of potential risks with remarkable speed and precision, far surpassing traditional methods. As a result, incident response times are significantly accelerated, empowering organizations to effectively mitigate the impact of cyberattacks.
Ongoing surveillance is a critical component of this strategy, ensuring that suspicious activities are swiftly identified and neutralized before they escalate into serious threats. This protects companies from ransomware, phishing, and various malware attacks. Organizations that harness Watson's capabilities have reported a notable decrease in response times, allowing them to address issues before they spiral out of control. As cyber threats continue to evolve, the integration of AI-powered solutions like Watson is essential for maintaining robust security measures.
Moreover, adopting layered recovery strategies, such as endpoint isolation and comprehensive user training, is vital for effective recovery. The importance of rapid incident response strategies cannot be overlooked; having an on-site team ready to act within 24 hours is crucial for minimizing damage and ensuring a thorough recovery. By prioritizing these strategies, organizations can safeguard their assets and fortify their defenses against the ever-present threat of cyber risks.
In today's digital landscape, the integration of artificial intelligence and cybersecurity is not merely advantageous; it is essential for robust protection. Palo Alto Networks exemplifies this by incorporating artificial intelligence and cybersecurity into its AI-driven analytics, significantly enhancing threat prevention capabilities. By identifying and blocking threats in real-time, organizations can fortify their defenses against increasingly sophisticated attacks. This proactive approach not only bolsters safety but also , including CMMC certification tiers. Aligning with these standards is crucial for safeguarding sensitive federal data and maintaining eligibility for government contracts.
Furthermore, Cyber Solutions Inc. underscores the critical importance of network hardening techniques. These techniques involve not only enhancing protection setups but also educating personnel on cybersecurity practices. Such measures are vital for strengthening defenses against potential risks. By prioritizing these strategies, organizations can effectively mitigate threats and ensure a secure operational environment.
Microsoft Azure Sentinel stands at the forefront of cybersecurity innovation, harnessing the power of artificial intelligence to significantly enhance analytics. This advancement empowers organizations to identify and address threats with greater efficacy. By automating data collection and analysis, Sentinel allows teams to concentrate on high-priority tasks, thereby boosting operational efficiency and minimizing the risk of human error. The integration of artificial intelligence and cybersecurity not only fortifies protective measures but also aids in meeting compliance obligations, ensuring that organizations remain vigilant in an increasingly regulated landscape.
The recent launch of the Sentinel data lake exemplifies this evolution in cybersecurity. It equips teams with the ability to uncover attacker behaviors and conduct retrospective searches through historical data, effectively transitioning cybersecurity from a reactive to a predictive paradigm. Additionally, the collaboration between Microsoft and industry leaders such as Accenture and ServiceNow enhances the protective ecosystem, providing extensive visibility and improved security measures across various platforms.
The practical applications of AI in threat detection are evident in the advancements made by Microsoft Sentinel. Its capability to ingest both structured and semi-structured signals enables the creation of detailed contextual representations of digital environments, facilitating superior pattern detection and signal correlation. This functionality is crucial, as organizations often operate with an average of 45 different protective tools, leading to fragmented defensive strategies.
Expert insights underscore the significant role of AI in efficient risk detection. With the , protection teams can automate routine tasks, allowing analysts to focus on strategic decision-making. Recent enhancements to Azure AI Foundry, including agent task adherence controls and prompt shielding features, further bolster the security of AI applications, ensuring they remain robust against emerging challenges.
In conclusion, Microsoft Azure Sentinel exemplifies how AI can revolutionize protective strategies, equipping organizations with the necessary tools to navigate the complexities of modern threats while enhancing their overall defense posture.

In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. Splunk harnesses the power of artificial intelligence and cybersecurity to significantly enhance data analysis related to safety and incident response capabilities, ensuring compliance with rigorous standards that are vital for protecting Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). By automating the processing of extensive security data, organizations can swiftly identify threats and respond with heightened efficiency—an essential factor for maintaining eligibility for lucrative government contracts.
This capability not only but also supports adherence to regulatory requirements, making it an invaluable asset for enterprises, particularly in the healthcare sector where rapid incident response is crucial for continuity of care and compliance. For instance, during a recent ransomware attack, a healthcare organization leveraged Splunk's risk-based alerting and automated workflows to gain real-time visibility into suspicious activities, resulting in enhanced response times and operational uptime.
The integration of artificial intelligence and cybersecurity into incident response procedures is not merely beneficial; it is essential for bolstering overall safety and operational resilience. As cybersecurity threats continue to evolve, healthcare organizations must prioritize advanced solutions like Splunk that integrate artificial intelligence and cybersecurity to navigate these challenges effectively and safeguard their critical data.
In an era where sophisticated threats challenge cybersecurity, the integration of artificial intelligence and cybersecurity by Fortinet emerges as a pivotal enhancement to [risk detection and response capabilities](http://discovercybersolutions.com/blog-posts/10-managed-it-services-and-support-for-healthcare-cf-os). By automating routine protection tasks, the platform empowers teams to concentrate on more complex threats, thereby significantly boosting overall operational efficiency. This proactive methodology not only strengthens security measures but also , rendering it a strategic investment for organizations.
Notably, AI-driven solutions can reduce incident response times by up to 96%, enabling teams to react swiftly to potential breaches. Furthermore, AI enhances detection accuracy by up to 95%, ensuring that even the most subtle anomalies are promptly identified and addressed. As cyber risks continue to evolve, incorporating artificial intelligence and cybersecurity into security operations becomes essential for maintaining robust defenses and enhancing team efficiency.
Moreover, the critical role of application allowlisting cannot be overstated; it proactively prevents unauthorized software from executing, thereby minimizing vulnerabilities and ensuring adherence to regulations such as HIPAA and GDPR. Key features of application allowlisting include:
C-Suite executives should seriously consider evaluating solutions that integrate artificial intelligence and cybersecurity to align with their security strategies and remain proactive against emerging risks. Additionally, adopting application allowlisting should be viewed as an indispensable component of their protection framework.
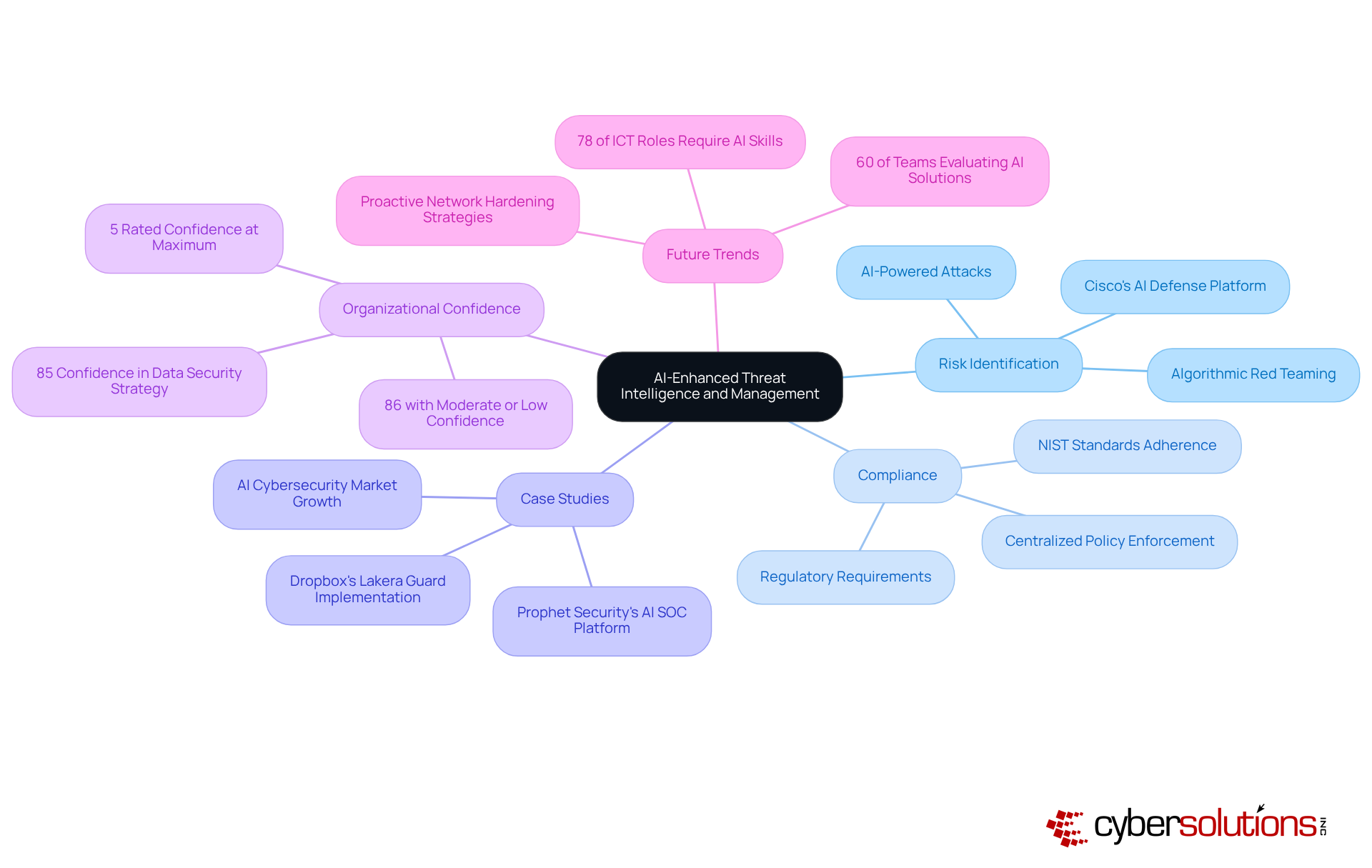
The integration of artificial intelligence and cybersecurity into management significantly enhances intelligence on risks and response capabilities, particularly in the context of protecting federal data and ensuring compliance with stringent regulatory standards. By leveraging AI-driven analytics, organizations can rapidly identify and mitigate risks related to artificial intelligence and cybersecurity, adapting to the fast-changing landscape of cyber threats. This proactive strategy not only fortifies protective measures but also aids in maintaining adherence to essential requirements, such as those established by NIST standards.
For example, Cisco's AI Defense platform exemplifies this trend by automating the stress-testing of AI models through algorithmic red teaming, simulating billions of potential attack scenarios to reveal vulnerabilities before exploitation occurs. Cisco's protective solutions utilize threat intelligence derived from over 50 billion daily events, providing a robust foundation for effective threat management. As a result, protection teams can focus on strategic decision-making rather than being overwhelmed by alert fatigue, ultimately improving operational efficiency and reducing response times.
While 85% of organizations express confidence in their keeping pace with AI advancements, it is noteworthy that only 5% rated their confidence in current protective measures at five out of five, indicating a considerable gap in perceived effectiveness. Practical applications, such as Dropbox's implementation of Lakera Guard to enhance the security of its LLM-powered applications, demonstrate the efficacy of artificial intelligence and cybersecurity in safeguarding sensitive data and ensuring robust protection frameworks.
Furthermore, proactive network hardening strategies, including staff training on online safety practices, are vital for bolstering overall security posture. As we approach 2025, the impact of artificial intelligence and cybersecurity on risk management efficiency will continue to grow, with 60% of teams not currently utilizing artificial intelligence and cybersecurity planning to evaluate AI-enhanced SOC solutions within the year, solidifying its role as an essential component of modern security strategies.
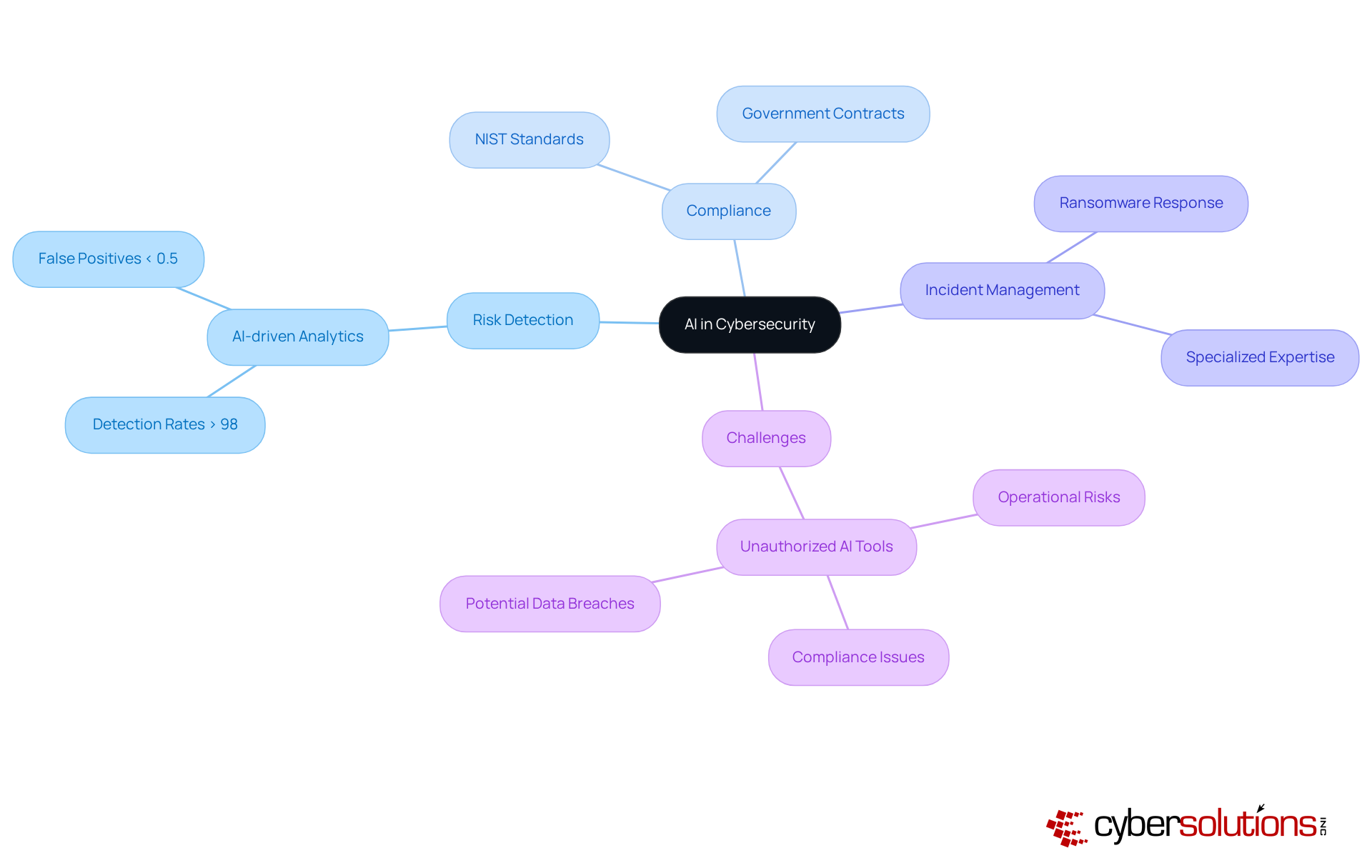
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially for organizations in the healthcare sector. Cyber Solutions leverages artificial intelligence and cybersecurity to provide extensive services that significantly enhance risk detection and response capabilities. By incorporating AI-driven analytics, we can identify and mitigate threats with remarkable efficiency, achieving detection rates exceeding 98 percent while keeping false positives below 0.5 percent. This proactive approach not only fortifies security measures but also aids organizations in complying with stringent industry regulations, including adherence to NIST standards, thereby maintaining eligibility for lucrative government contracts.
Moreover, our commitment to a layered cybersecurity strategy ensures that organizations are well-prepared to respond effectively to incidents, such as ransomware attacks, through swift incident management and specialized expertise. As cyber threats continue to evolve, integrating artificial intelligence and cybersecurity becomes essential for maintaining strong defenses and ensuring operational resilience. However, it is crucial for organizations to remain vigilant about the challenges posed by unauthorized AI tools, which can introduce operational risks, compliance issues, and potential data breaches. By addressing these challenges head-on, Cyber Solutions positions itself as a trusted partner in navigating the complex cybersecurity landscape.
The integration of artificial intelligence into cybersecurity solutions signifies a transformative leap in how organizations detect, respond to, and manage threats within an increasingly complex digital landscape. By harnessing AI technologies, companies can not only enhance their risk detection capabilities but also streamline incident response processes, ensuring a proactive stance against evolving cyber threats.
Various industry leaders, including Cyber Solutions Inc., Darktrace, CrowdStrike, and IBM Security, have showcased the multifaceted benefits of AI in cybersecurity. These advancements—from real-time threat detection and autonomous risk management to improved compliance with industry regulations—underscore the necessity for organizations to adopt AI-driven solutions. The effectiveness of application allowlisting, predictive analytics, and continuous monitoring further illustrates how AI can significantly reduce vulnerabilities and enhance operational resilience.
As the cybersecurity landscape continues to evolve, the imperative for organizations to invest in AI-enhanced solutions cannot be overstated. Embracing these technologies not only fortifies defenses but also positions businesses to thrive amid the challenges posed by increasingly sophisticated cyber threats. The future of cybersecurity is undeniably intertwined with artificial intelligence, making it essential for organizations to prioritize these innovations in their security strategies to safeguard their assets and maintain compliance in a rapidly changing environment.
What is the role of Cyber Solutions Inc. in cybersecurity?
Cyber Solutions Inc. utilizes artificial intelligence and sophisticated machine learning algorithms to enhance risk detection and response capabilities in cybersecurity, particularly in the healthcare sector.
How does Cyber Solutions Inc. improve risk detection?
The firm analyzes vast datasets in real-time to identify potential risks before they escalate, which helps mitigate data breaches and ensures compliance with industry regulations such as HIPAA, PCI-DSS, and GDPR.
What is application allowlisting and why is it important?
Application allowlisting is a security measure that prevents unauthorized software from executing, thereby reducing vulnerabilities and the attack surface.
How much faster can AI-powered attack detection systems identify cyber intrusions compared to traditional methods?
AI-powered attack detection systems can identify cyber intrusions up to 60% faster than traditional methods.
What financial benefits do companies experience by leveraging AI and automation in digital security?
Companies that utilize AI and automation in digital security save an average of $2.2 million compared to those that do not.
What is Darktrace and how does it enhance cybersecurity?
Darktrace is a cybersecurity solution that uses autonomous AI to analyze typical behavior patterns within an organization, allowing it to autonomously identify and mitigate anomalies in real-time.
What percentage of Chief Information Security Officers acknowledges the risks associated with AI and cybersecurity?
78% of Chief Information Security Officers recognize the significant influence of risks related to artificial intelligence and cybersecurity.
How does CrowdStrike utilize artificial intelligence in cybersecurity?
CrowdStrike leverages AI to enhance endpoint security and intelligence by analyzing patterns and behaviors to identify and respond to threats in real-time.
What is the significance of application allowlisting in CrowdStrike's approach?
Application allowlisting helps preemptively block malware and unauthorized software, reducing the attack surface and ensuring compliance with regulatory standards.
What key features are associated with application allowlisting?
Key features include continuous monitoring of application activity and centralized management of allowlists across devices to streamline control and policy enforcement.