
As Data Privacy Day approaches, organizations must prioritize enhancing their data privacy compliance. The article titled "10 Essential Steps for Data Privacy Day: Strengthen Your Compliance" underscores critical actions that should be taken to fortify this compliance. Key strategies include:
Each of these steps is essential for maintaining compliance with evolving regulations and fostering a robust culture of data protection. By taking these actions, organizations not only comply with legal standards but also build trust with their stakeholders.
Data Privacy Day serves as a critical reminder of the importance of safeguarding personal information in an increasingly digital world. As organizations navigate the complexities of compliance with evolving regulations, this day presents a unique opportunity to enhance their data protection strategies.
However, how can businesses effectively strengthen their compliance and foster a culture of data privacy amidst growing cyber threats? By exploring essential steps and best practices, organizations can not only meet regulatory requirements but also build trust with their customers, ensuring a robust framework for data security that extends well beyond January 28.
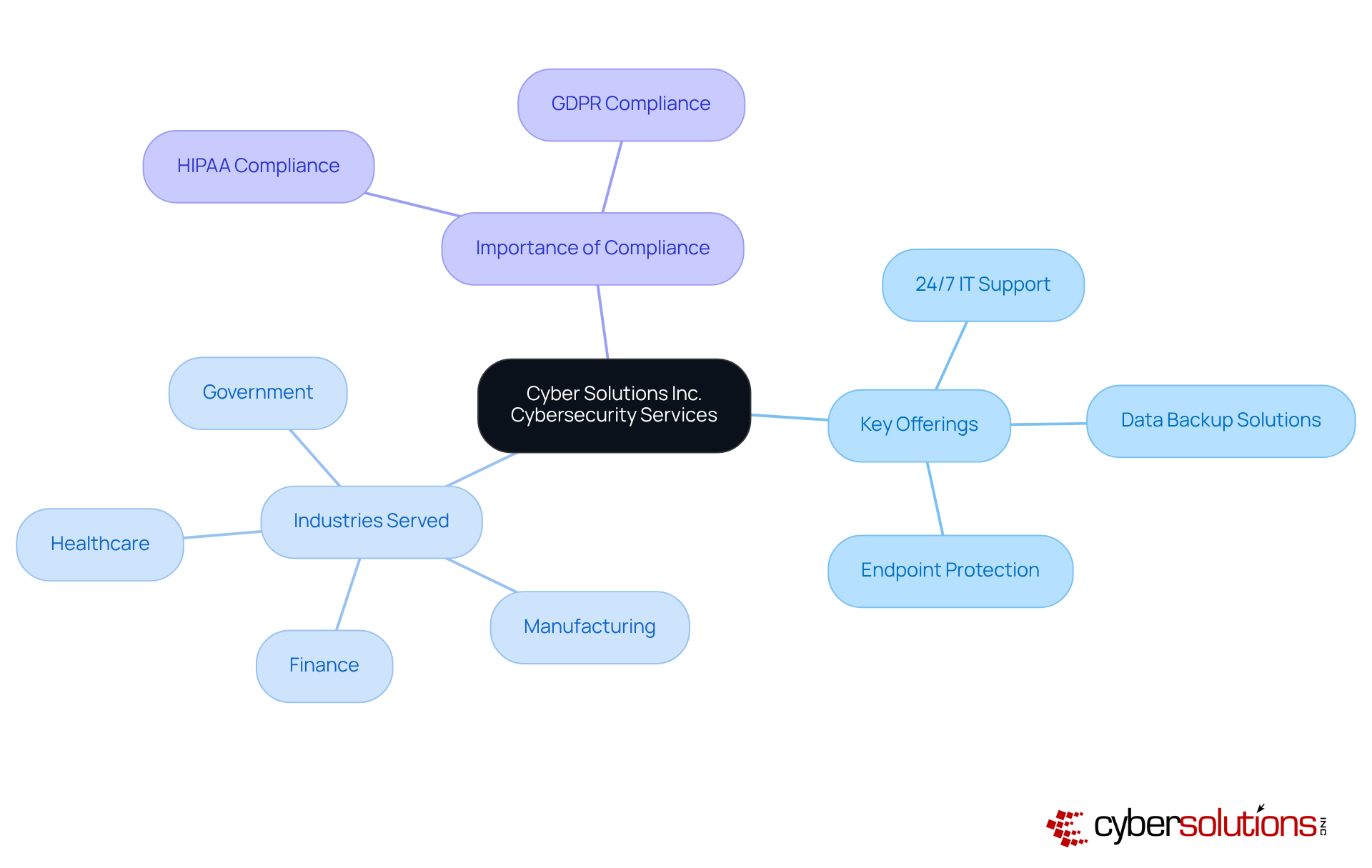
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially within the healthcare sector. Cyber Solutions Inc. offers an extensive range of managed IT and cybersecurity services designed to significantly enhance information privacy for businesses. Our Compliance as a Service (CaaS) solutions simplify the complexities of regulatory requirements, ensuring your entity meets critical standards such as HIPAA and GDPR.
Key offerings, including:
are meticulously tailored to address the unique requirements of various industries, notably healthcare, finance, manufacturing, and government. For instance, a recent case study demonstrated how our rapid incident response team effectively contained a cyber threat within 24 hours, minimizing damage and ensuring business continuity. This proactive approach underscores the necessity for , particularly as small and mid-sized businesses increasingly become prime targets for cyberattacks.
By leveraging cutting-edge technologies and specialized knowledge, Cyber Solutions empowers entities to safeguard confidential information while ensuring adherence to stringent regulatory structures. This holistic approach not only mitigates risks associated with cyber threats but also enhances operational efficiency, allowing businesses to focus on their core functions without the burdens of IT management. As we look ahead to 2025, organizations that invest in managed IT services will be better prepared to navigate the evolving landscape of information protection and regulations, ultimately leading to enhanced business resilience and success.
Conducting regular staff training sessions on information protection is paramount for fostering a culture of awareness and accountability. Training should encompass critical subjects such as:
By equipping employees with the knowledge necessary to protect sensitive information, organizations can substantially reduce the risk of breaches and enhance their overall security posture. Furthermore, leadership involvement in training initiatives is vital, as it demonstrates the organization’s commitment to information confidentiality at every level.
Integrating Compliance as a Service (CaaS) into your training strategy can significantly reinforce these efforts. CaaS offers businesses comprehensive solutions to meet regulatory requirements, including audit preparation and ongoing monitoring. This means that while staff are educated on information protection, the organization can also ensure compliance through expert guidance and proactive risk assessments. CaaS is particularly beneficial for small and medium-sized enterprises, as it provides access to enterprise-level regulatory expertise without the substantial costs associated with hiring in-house personnel.
Continuous training and refresher courses are essential to keep employees informed about the latest developments in information security, while thorough information mapping helps identify personal data collection and usage, ensuring compliance. As global privacy standards continue to evolve, organizations must adapt their training programs in preparation for data privacy day. The potential financial implications of data breaches highlight the necessity of effective training initiatives. Ultimately, cultivating a among employees is crucial for enhancing an organization’s security posture and maintaining consumer trust.

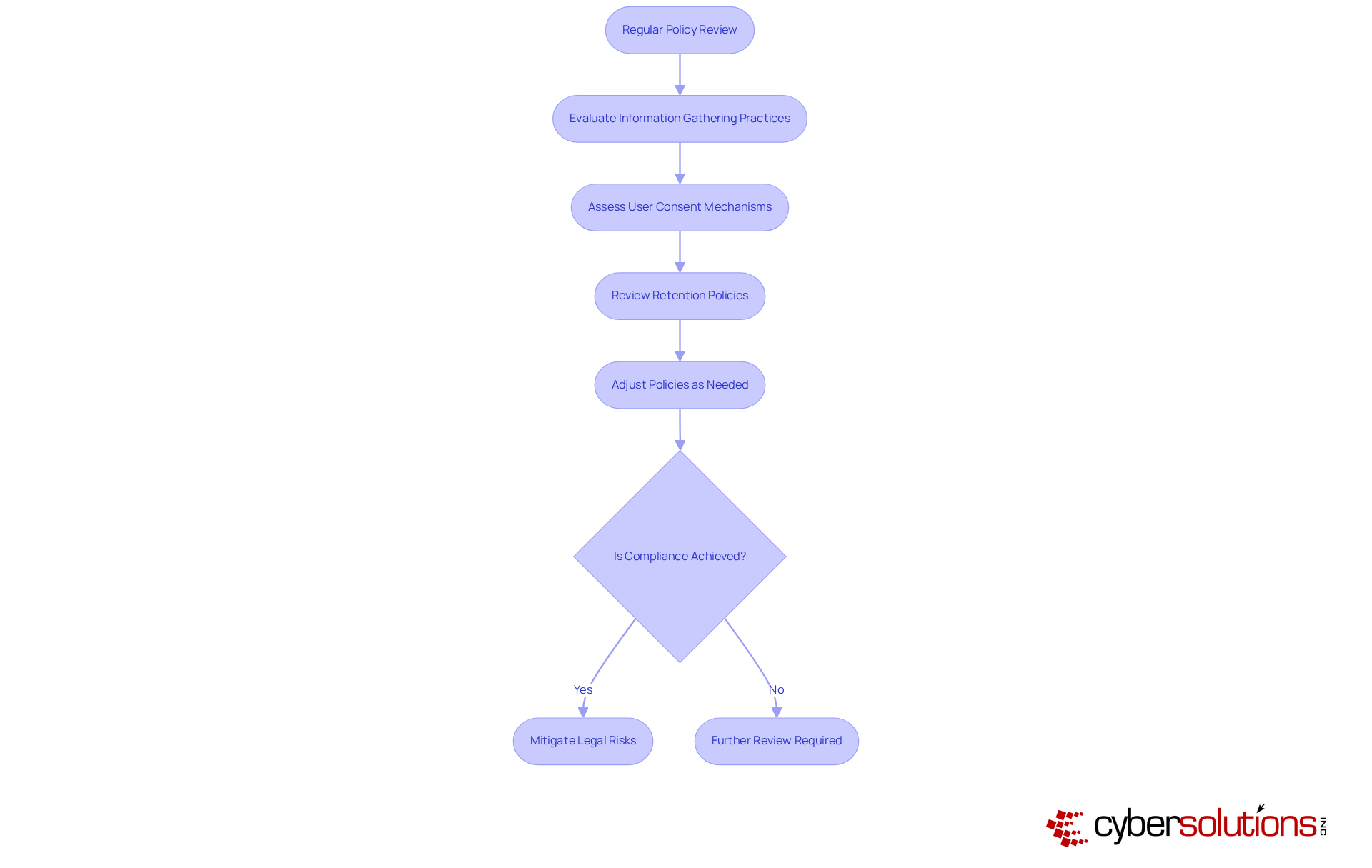
Organizations must prioritize regular reviews of their privacy policies to ensure compliance with evolving regulations such as GDPR, HIPAA, and CCPA. This process involves a comprehensive evaluation of , user consent mechanisms, and retention policies.
For instance, GDPR mandates that entities inform authorities and affected individuals within 72 hours of a breach, underscoring the necessity for robust incident response strategies. By remaining vigilant about regulatory changes and adjusting policies accordingly, businesses can mitigate legal risks and demonstrate their commitment to safeguarding customer information.
Current trends indicate that entities are increasingly adopting governance frameworks to bolster compliance initiatives, reflecting a proactive approach to information management. Legal experts assert that maintaining an up-to-date data protection policy is not merely a legal obligation but a vital practice that fosters trust and transparency with stakeholders.
As privacy regulations continue to evolve, the importance of these evaluations cannot be overstated, enabling organizations to navigate the complexities of information protection effectively.
Implementing information encryption is paramount in safeguarding sensitive details from breaches, particularly in relation to adhering to CMMC certification tiers. Encryption transforms readable information into an unreadable format, ensuring that even if intercepted, it remains secure. Organizations must prioritize encrypting information both at rest and in transit, employing robust encryption standards like AES-256. This approach not only protects customer information but also aids organizations in complying with protection regulations, including those outlined in NIST 800-171 for securing Controlled Unclassified Information (CUI).
Furthermore, secure key management practices are essential for maintaining the integrity of encryption efforts. The failure to encrypt information can result in significant legal penalties and reputational damage, highlighting the urgent need for robust encryption strategies. Additionally, implementing advanced security measures, such as multi-factor authentication (MFA) and access control protocols, is vital for preventing unauthorized access and ensuring compliance with HIPAA regulations.

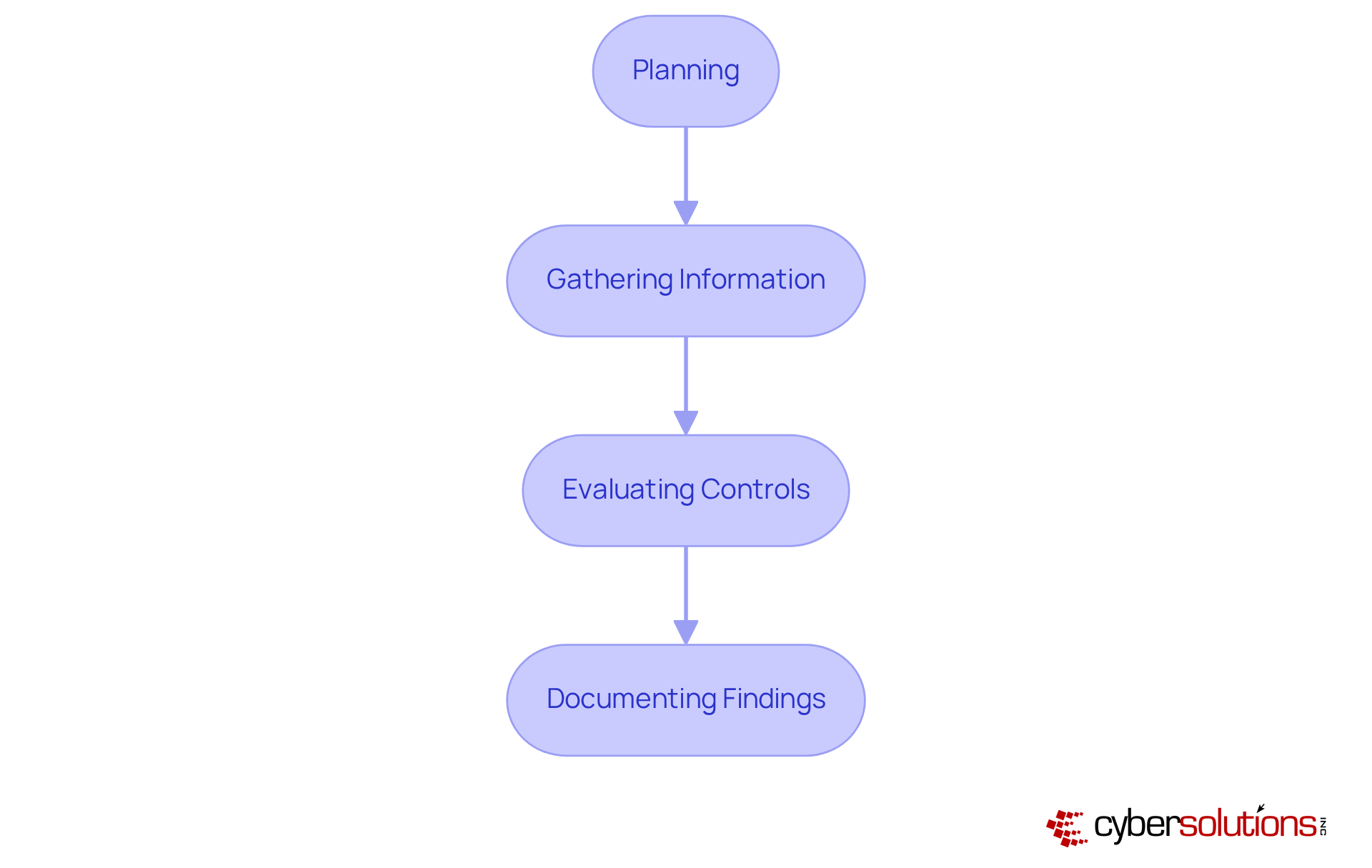
Regular assessments of information protection practices are not just essential; they are imperative for identifying weaknesses and ensuring integrity. These audits must rigorously assess adherence to privacy policies, evaluate information handling procedures, and pinpoint potential security gaps. By implementing a structured audit process that encompasses planning, gathering information, evaluating controls, and documenting findings, organizations can proactively address vulnerabilities and enhance their overall information protection strategies. Notably, only 52% of companies conduct security audits; however, those that do experience a 40% lower risk of data breaches, underscoring the critical role these assessments play in safeguarding sensitive information.
In addition to regular audits, it is crucial to address regulatory gaps through tailored remediation strategies. This process involves revising policies, enhancing systems, and refining procedures, all of which must be meticulously documented to demonstrate adherence during audits. Key documentation categories, such as security policies, procedures, and evidence of compliance, are vital for successful audits. For instance, a case study illustrated how a mid-sized nonprofit organization identified specific vulnerabilities in their data handling processes, including inadequate access controls and outdated encryption methods, ultimately leading to improved compliance with regulatory standards through targeted remediation efforts.
Moreover, cybersecurity audits offer a systematic examination of IT systems, enabling businesses to effectively identify and mitigate risks. Proactive network hardening strategies—such as updating security configurations and optimizing endpoint protections—can significantly bolster a company's security posture. Training staff to recognize suspicious emails and uphold proper is equally crucial in cultivating a culture of security awareness. As industry experts emphasize, a well-structured cybersecurity audit program empowers organizations to stay ahead of emerging risks and maintain regulatory alignment, ultimately fostering trust and operational resilience.
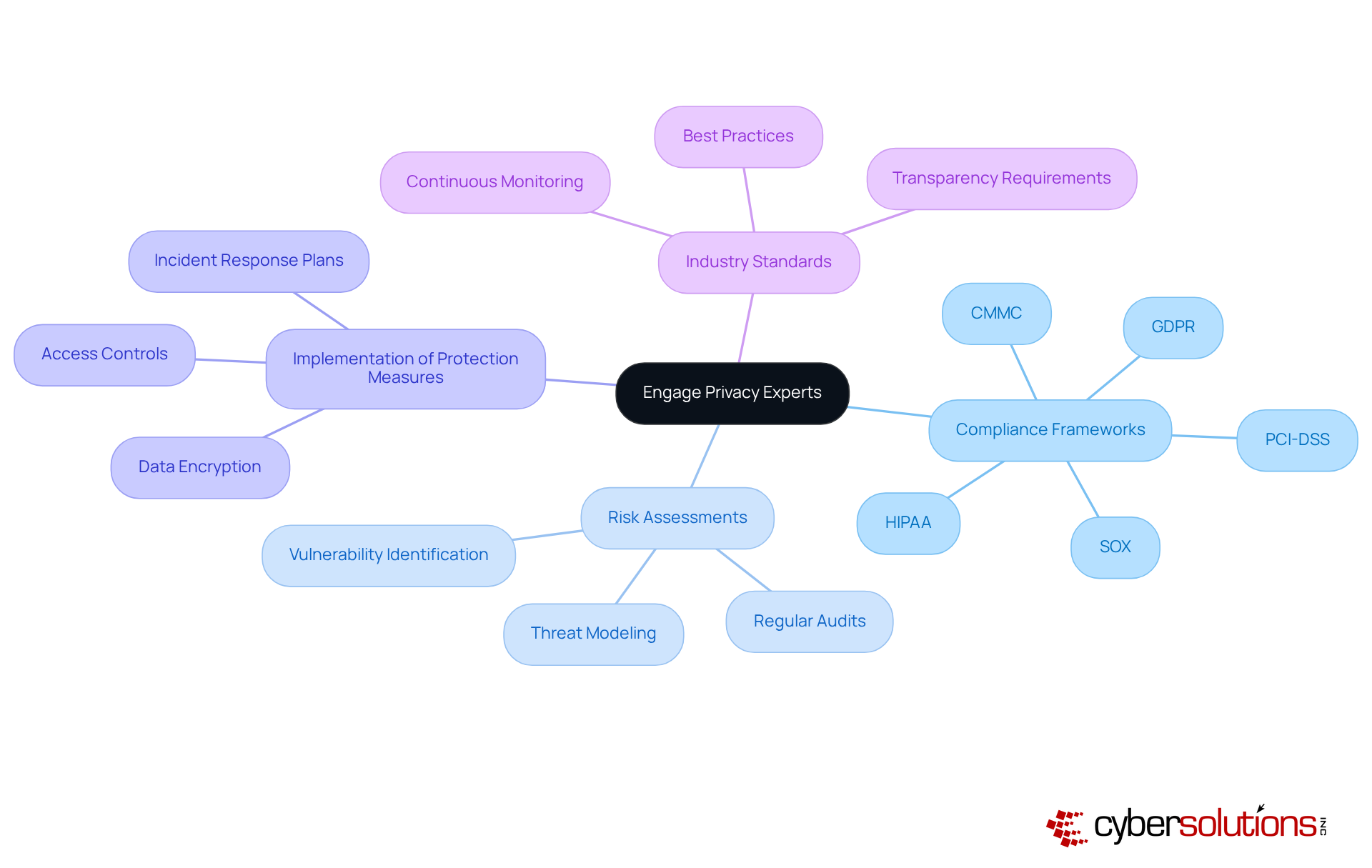
In today's digital landscape, the involvement of information security specialists is paramount for organizations aiming to enhance their protection strategies. These experts offer critical insights into compliance frameworks, risk assessments, and the implementation of robust information protection measures. By collaborating with consultants on confidentiality, businesses can align their practices with industry standards and regulations, ensuring a comprehensive approach to data protection. As organizations increasingly acknowledge the necessity of expert guidance, the hiring of privacy consultants has emerged as a growing trend, demonstrating a proactive stance towards safeguarding sensitive information and navigating the complexities of regulations in an ever-evolving legal environment.
Cyber Solutions' Compliance as a Service (CaaS) streamlines this process by offering essential services such as risk assessments, policy development, and ongoing compliance monitoring to meet standards like HIPAA, PCI-DSS, CMMC, SOX, and GDPR. Industry leaders emphasize that leveraging the expertise of privacy specialists not only strengthens privacy frameworks but also fosters a culture of responsibility and transparency within organizations. This shift not only addresses immediate cybersecurity threats but also cultivates a resilient organizational ethos that prioritizes .
Establishing robust information retention policies is essential for the responsible management of personal information. These policies must explicitly outline the , the specific criteria that dictate information deletion, and the secure methods for disposing of data. By implementing comprehensive retention policies, organizations not only ensure compliance with stringent protection regulations, such as GDPR and HIPAA, but also significantly mitigate the risks associated with retaining unnecessary personal information.
Companies that have adopted thorough information retention strategies have reported enhanced operational efficiency and reduced compliance risks. Regular evaluations and updates to these policies are crucial to adapt to evolving legal requirements and technological advancements, ensuring that organizations remain vigilant against potential data breaches and regulatory penalties.
Furthermore, integrating information security best practices within these policies can help diminish risks related to data leaks and unauthorized access, ultimately fostering a culture of accountability and trust.
Clear communication regarding information practices is essential for organizations aiming to establish trust with their customers, particularly on data privacy day. By clearly outlining how customer information is collected, utilized, and safeguarded, especially on data privacy day, businesses foster a sense of security and confidence. Openly sharing information handling practices on data privacy day not only demonstrates a commitment to privacy but also .
Looking ahead to 2025, effective communication will be pivotal on data privacy day in shaping customer perceptions of privacy, as consumers increasingly seek transparency and accountability from the entities they engage with. On data privacy day, organizations that emphasize transparency are likely to experience heightened customer loyalty; indeed, a significant 94% of surveyed entities found that clients would refrain from purchasing if they did not adequately protect their information.
Furthermore, companies like Zendesk exemplify how empowering customers with knowledge about information usage, especially on data privacy day, can significantly bolster trust and enhance the overall customer experience. For instance, Zendesk's initiatives have led to increased customer satisfaction and loyalty, underscoring the effectiveness of their transparency practices.
However, organizations also face challenges in achieving transparency, such as navigating complex regulations and ensuring consistent communication across departments. By adopting a proactive approach to information transparency, especially on data privacy day, businesses can effectively navigate these complexities while cultivating stronger relationships with their customers.
In today's complex regulatory landscape, employing technology solutions is not just beneficial; it is essential for improving regulatory processes. Automation of routine tasks ensures adherence to regulations while significantly enhancing overall regulatory efficiency. Compliance management software empowers entities to efficiently monitor regulatory changes, handle data subject requests, and maintain accurate records. By automating these critical functions, businesses mitigate the risk of human error and streamline their operations. Notably, entities utilizing have reported not only improved workflows but also enhanced precision in their compliance efforts. Experts assert that integrating such software can transform compliance from a reactive obligation into a proactive strategy, ultimately bolstering organizational resilience in a challenging regulatory environment.
Observing Data Privacy Day presents a vital opportunity for institutions to bolster awareness surrounding information protection and reaffirm their commitment to safeguarding personal details. Engaging activities—such as hosting workshops, distributing educational materials, and facilitating discussions on information security—can significantly elevate employee understanding and involvement.
Industry leaders emphasize that these initiatives not only demonstrate a company's dedication to protecting customer information but also foster a culture of privacy that permeates the organization. Gagan Gulati, General Manager for Information Services at NetApp, aptly states, "Privacy Day reminds us that safeguarding information goes beyond compliance—it's about embracing a mindset of ensuring that your customer's information remains confidential and you uphold their trust."
By actively participating in Data Privacy Day, businesses can enhance their compliance efforts and cultivate trust with stakeholders, ultimately reinforcing their reputation in an increasingly regulated environment. This day serves as a crucial reminder that prioritizing is essential for maintaining customer trust and ensuring long-term organizational success.
Notably, with only 25% of websites halting tracking technologies when users opt-out, the necessity for proactive measures is evident. Organizations should also contemplate employing digital checklists to monitor workplace events and data privacy initiatives, ensuring thorough engagement in this critical endeavor.
Data Privacy Day, celebrated annually on January 28, serves as a timely occasion for reflection and action.
Observing Data Privacy Day presents a crucial opportunity for organizations to reaffirm their commitment to safeguarding personal information and enhancing awareness of data protection practices. This day serves as a reminder of the growing importance of data privacy in our increasingly digital world. By implementing the ten essential steps outlined, businesses can significantly strengthen their compliance with evolving regulations and foster a culture of privacy that prioritizes the protection of sensitive data.
Key strategies include:
These proactive measures not only mitigate risks associated with data breaches but also cultivate trust and transparency with customers.
As organizations prepare for Data Privacy Day, recognizing the importance of a comprehensive approach to data protection is essential. By actively participating in initiatives that promote privacy awareness and implementing best practices, businesses can enhance their reputations and ensure long-term success in an increasingly regulated environment. Embracing a strong commitment to data privacy transcends mere legal obligation; it is a vital component of maintaining customer trust and fostering a secure digital landscape.
What services does Cyber Solutions Inc. offer to enhance data privacy?
Cyber Solutions Inc. offers a range of managed IT and cybersecurity services, including Compliance as a Service (CaaS), 24/7 IT support, data backup solutions, and endpoint protection, specifically tailored for industries like healthcare, finance, manufacturing, and government.
How does Compliance as a Service (CaaS) help organizations?
CaaS simplifies regulatory compliance by providing comprehensive solutions to meet standards such as HIPAA and GDPR, including audit preparation and ongoing monitoring, which is especially beneficial for small and medium-sized enterprises.
Why is employee training important for data privacy?
Regular staff training on information protection is crucial for fostering awareness and accountability, helping employees identify phishing attempts, understand information handling protocols, and recognize compliance regulations, thereby reducing the risk of data breaches.
What should organizations focus on during their employee training sessions?
Training should cover identifying phishing attempts, understanding information handling protocols, and recognizing the significance of compliance regulations like GDPR, CCPA, and HIPAA.
How often should organizations review their privacy policies?
Organizations should prioritize regular reviews of their privacy policies to ensure compliance with evolving regulations such as GDPR, HIPAA, and CCPA.
What are the consequences of not having robust incident response strategies?
Without robust incident response strategies, organizations may face legal risks, as regulations like GDPR require entities to inform authorities and affected individuals within 72 hours of a breach.
What trends are organizations following to bolster compliance initiatives?
Organizations are increasingly adopting governance frameworks to enhance their compliance initiatives, reflecting a proactive approach to information management.
What is the significance of maintaining an up-to-date data protection policy?
Maintaining an up-to-date data protection policy is vital not only for legal compliance but also for fostering trust and transparency with stakeholders.