
In today's healthcare landscape, the significance of cybersecurity cannot be overstated. C-suite leaders must prioritize essential HIPAA technical safeguards to ensure compliance and protect sensitive health information. Measures such as:
are not merely regulatory requirements; they are vital strategies that mitigate the risks of data breaches. Moreover, these safeguards enhance patient trust and ensure adherence to regulations within the healthcare sector. By implementing these measures, healthcare organizations can not only safeguard their data but also foster a culture of security that resonates with patients and stakeholders alike.
In an era marked by an alarming rise in cyber threats, the significance of adhering to HIPAA technical safeguards is paramount. C-suite leaders are instrumental in implementing robust cybersecurity measures that not only shield sensitive patient information but also bolster overall organizational trust. This article explores ten essential HIPAA technical safeguards that executives must prioritize to effectively navigate the intricate landscape of compliance and protect their institutions against potential breaches.
How can leaders ensure that their organizations are not only compliant but also resilient in the face of the ever-evolving cybersecurity risks?
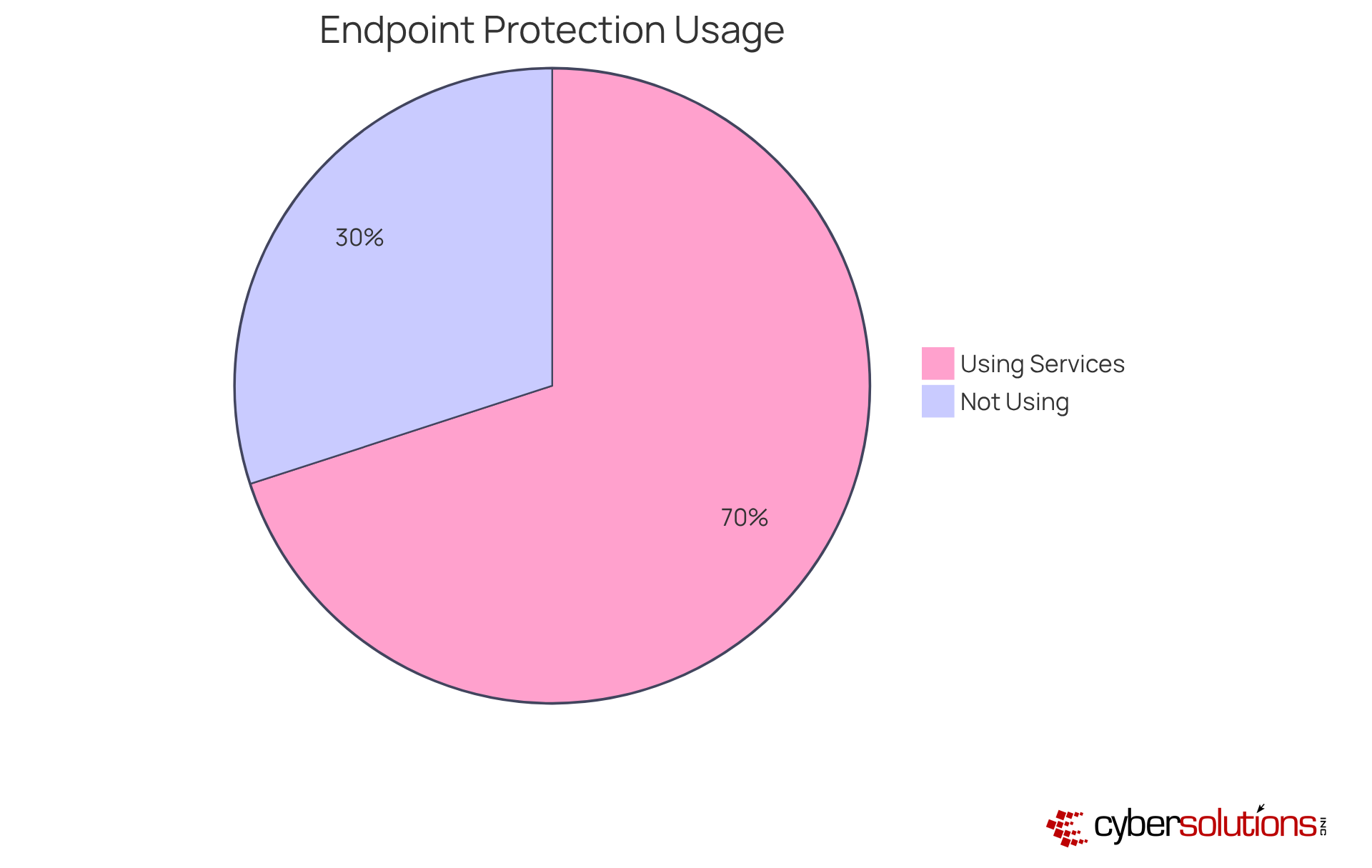
In today's digital age, the importance of cybersecurity in healthcare cannot be overstated. Cyber Solutions Inc. provides essential endpoint protection services that are crucial for maintaining HIPAA compliance. These services encompass advanced threat detection and response capabilities, ensuring that all devices accessing sensitive health information are secure. A key component of these services is application allowlisting, which proactively prevents unauthorized software from executing, thereby reducing the risk of malware, ransomware, and zero-day attacks.
With around 70% of healthcare entities now employing , the execution of thorough protective measures, including allowlisting, is more crucial than ever. By efficiently reducing risks linked to information breaches, entities not only adhere to HIPAA regulations but also utilize HIPAA technical safeguards to protect patient information, thereby improving trust in healthcare services. Industry experts emphasize that robust endpoint security, complemented by application allowlisting, is a foundational element in safeguarding electronic protected health information (ePHI) and adhering to HIPAA technical safeguards. This makes it imperative for healthcare leaders to prioritize these measures in their cybersecurity strategies.
As the landscape of cybersecurity threats evolves, healthcare organizations must adapt to protect sensitive information effectively. Cyber Solutions Inc. stands ready to assist in addressing these pressing challenges, ensuring that healthcare providers can focus on what they do best—caring for patients.
Data encryption is crucial for safeguarding patient information against unauthorized access. By applying encryption for electronic Protected Health Information (ePHI) both at rest and in transit, healthcare organizations can uphold the confidentiality of sensitive information.
In 2025, it is anticipated that hacking and IT incidents will represent over 79% of healthcare information breaches, underscoring the necessity for robust encryption practices. Cyber Solutions employs industry-standard encryption methods, such as AES-256, to protect patient information, ensuring [compliance with HIPAA standards](https://discovercybersolutions.com/compliance-as-a-service) and significantly reducing the risk of breaches.
Notably, entities that implement AES-256 encryption have reported enhanced protective measures and fewer occurrences of compromise, demonstrating the effectiveness of this encryption standard in safeguarding patient information. Moreover, application allowlisting acts as a vital layer of defense, proactively preventing unauthorized applications from executing and thereby diminishing the attack surface.
This dual approach of encryption and allowlisting, which includes features like continuous monitoring and centralized management, not only fortifies information protection but also guarantees compliance with stringent regulations, including HIPAA technical safeguards.
With the reaching $7.42 million, it is imperative for organizations to regularly review their encryption protocols and application allowlists to ensure compliance and security.
Access controls, as part of HIPAA technical safeguards, are paramount for compliance, safeguarding sensitive health information by ensuring that only authorized personnel can access it. Cyber Solutions employs role-based access controls (RBAC), which restrict access based on specific user roles. This focused approach guarantees that employees receive only the information essential for their job functions, significantly reducing the risk of security breaches. Statistics reveal that inadequate access controls have contributed to numerous security incidents, including the 585,621 individuals affected by Comstar, LLC's ransomware attack.
Implementing RBAC not only enhances data protection but also aligns with best practices in the healthcare sector. Organizations adopting RBAC report improved compliance with HIPAA requirements and a reduction in unauthorized access incidents, supported by HIPAA technical safeguards. Real-world examples underscore the effectiveness of RBAC: healthcare providers that implemented these controls experienced a marked decline in security incidents, reinforcing the critical importance of access management in protecting electronic protected health information (ePHI).
In a recent case study, a healthcare provider fell victim to a ransomware attack that compromised their systems. In the aftermath, staff underwent immediate training on identifying suspicious emails and maintaining proper cybersecurity hygiene. Remarkably, the provider's 4,500 endpoints were restored within two weeks, far quicker than initial projections, enabling essential operations to resume with minimal downtime. This incident underscored the necessity of , highlighting a proactive stance against future threats.
Industry leaders stress the importance of robust access controls, asserting that they are vital for preserving the integrity and confidentiality of health data. A designated Protection Official must be appointed to formulate and implement safety policies, ensuring compliance and overseeing risk assessments. By prioritizing access controls and conducting regular risk evaluations, healthcare organizations can adeptly navigate the complexities of HIPAA adherence while ensuring the implementation of HIPAA technical safeguards to protect sensitive information. Cyber Solutions offers expert guidance and proactive risk management to bolster these initiatives.
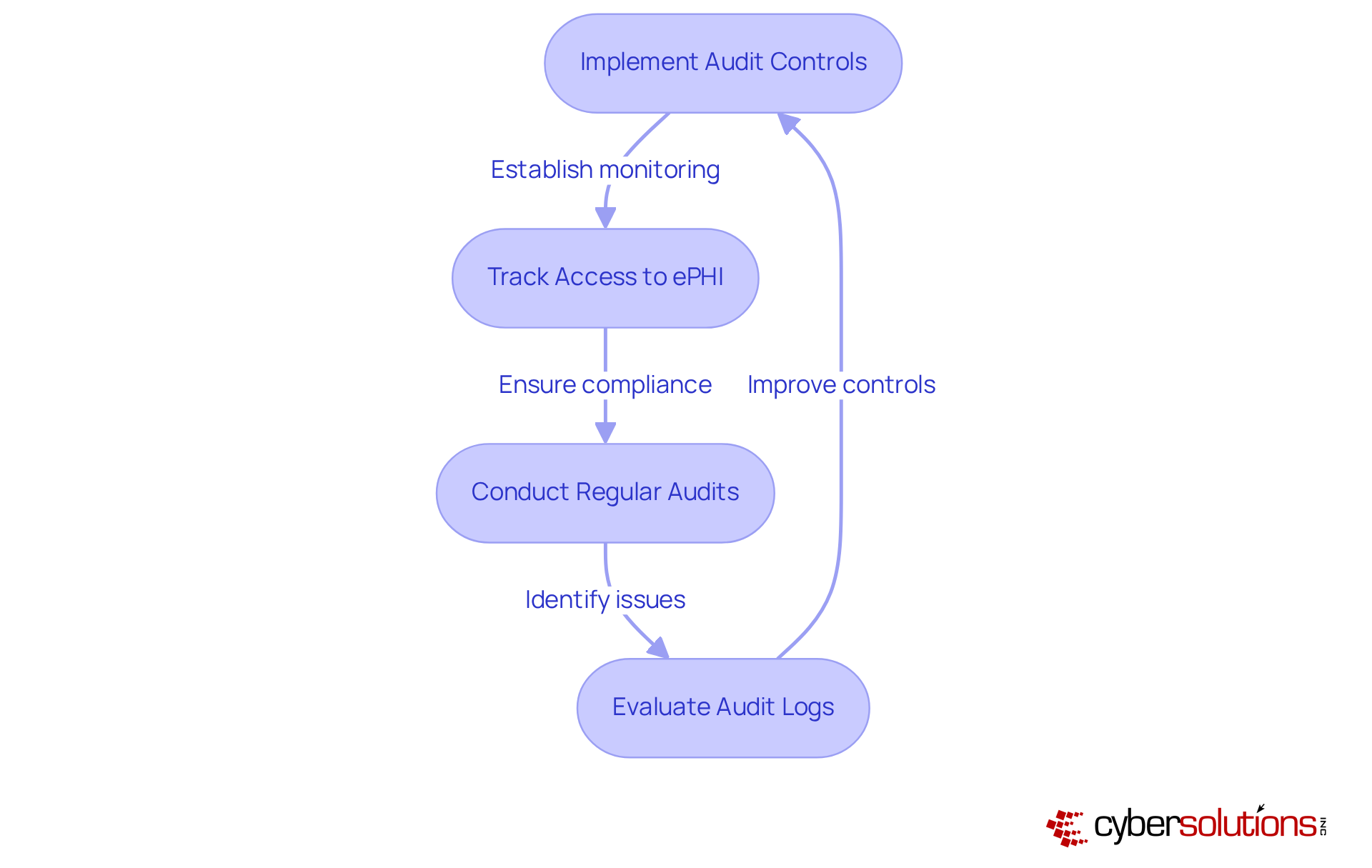
In the rapidly evolving landscape of healthcare, the importance of cybersecurity cannot be overstated. Audit controls are essential for effectively monitoring access to electronic Protected Health Information (ePHI). Cyber Solutions Inc. offers advanced logging and monitoring solutions that meticulously track who accesses sensitive data and when. This capability empowers healthcare entities to conduct regular audits, which are crucial for detecting unauthorized access and ensuring compliance with HIPAA technical safeguards.
Consider the significance of audit logs—they serve as a vital record of access, detailing who accessed what information, when, and for how long. This level of scrutiny not only aids in but also plays a pivotal role in protecting patient privacy. Regular evaluations of these logs are indispensable, as they provide proof of adherence during audits and investigations.
Moreover, organizations that implement robust audit controls can significantly enhance their security posture by adhering to HIPAA technical safeguards. A notable example is the University of Pittsburgh Medical Center, where remote patient monitoring initiatives led to a remarkable 76% reduction in readmission rates and increased patient satisfaction scores. As the healthcare landscape continues to evolve, integrating effective logging and monitoring solutions will remain a cornerstone of safeguarding sensitive information and maintaining regulatory compliance.
In today's healthcare landscape, the integrity of electronic Protected Health Information (ePHI) is paramount. Integrity controls are essential to ensure that ePHI remains accurate and unaltered. Cyber Solutions Inc. implements robust mechanisms, including:
to verify the integrity of health information. Furthermore, our application allowlisting strategy is crucial in this endeavor, as it prevents unauthorized or malicious applications from executing, thereby safeguarding the integrity of patient information. This proactive strategy not only mitigates the risk of malware and ransomware attacks but also aids organizations in , ensuring that patient information is both reliable and trustworthy.
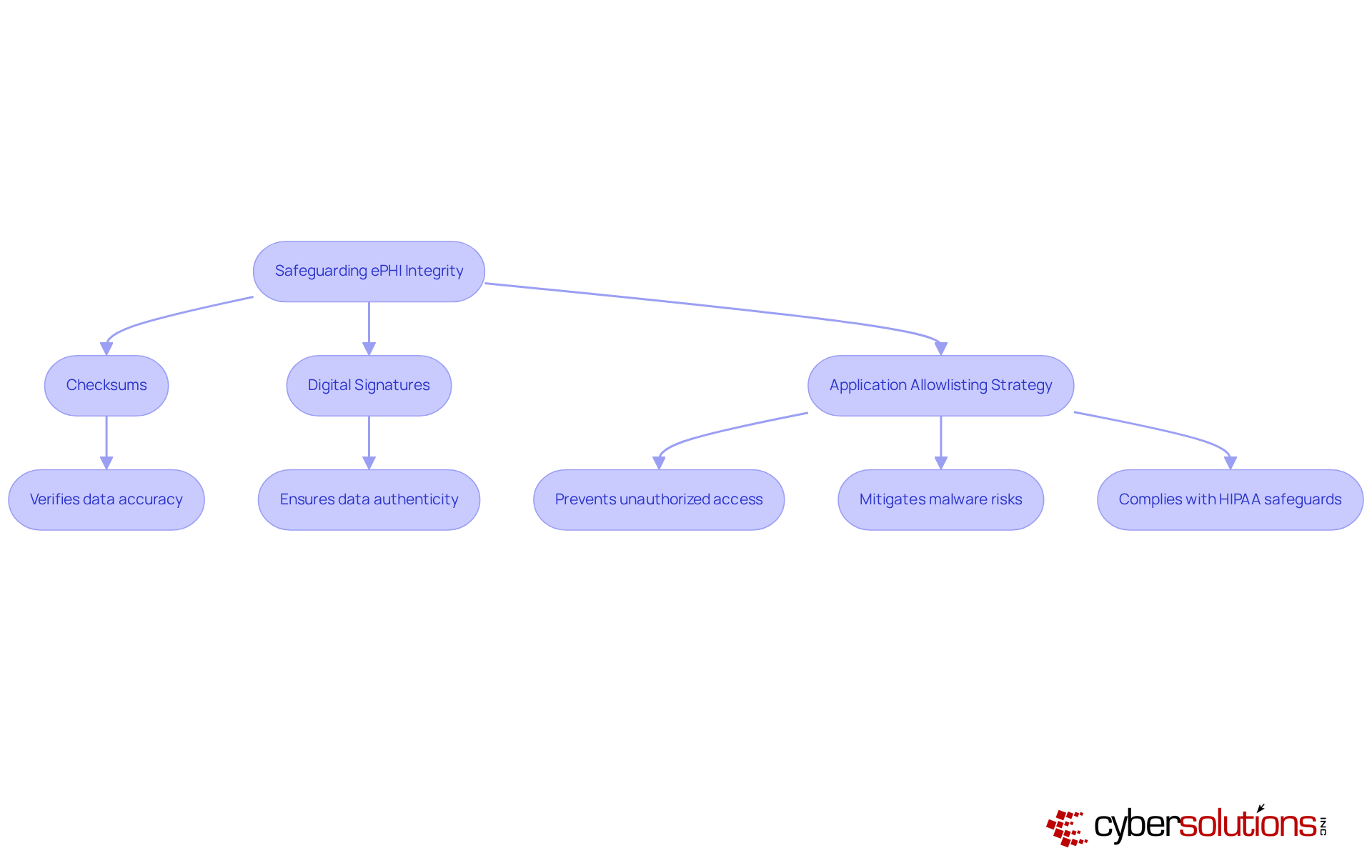
Transmission protection is critical for safeguarding electronic Protected Health Information (ePHI) during information transfers. With a staggering in the past year, the urgent need for robust protective measures cannot be overstated.
Cyber Solutions Inc. employs secure protocols such as HTTPS and Virtual Private Networks (VPNs) to encrypt information in transit, effectively shielding sensitive material from interception. These protocols not only comply with [HIPAA transmission security standards](https://discovercybersolutions.com/compliance-as-a-service/sox-compliance) but also incorporate HIPAA technical safeguards to ensure that patient information remains confidential during electronic communications.
Experts underscore the necessity of encryption; as one cybersecurity authority states, 'ePHI should be encrypted at rest and in transit to prevent unauthorized access.' By implementing these secure protocols, organizations can significantly reduce the risk of information breaches and enhance their overall regulatory compliance.
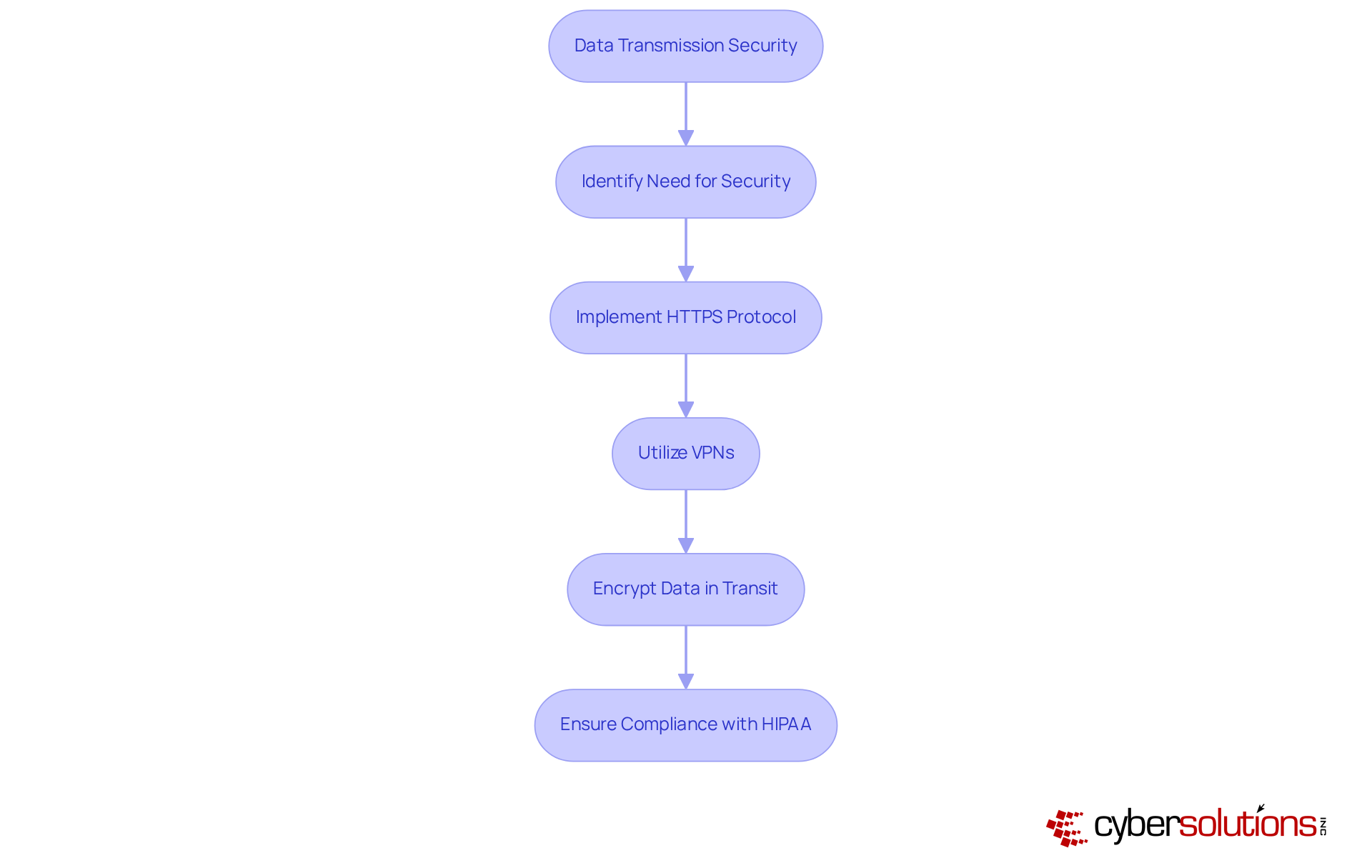
Security awareness training is not just a requirement; it is a cornerstone of HIPAA compliance and vital for the implementation of HIPAA technical safeguards to protect electronic Protected Health Information (ePHI). Cyber Solutions Inc. provides comprehensive training programs designed to equip staff with the skills necessary to identify potential risks and understand their responsibilities in protecting confidential information. By cultivating an environment of awareness, organizations can significantly mitigate the risk of breaches, which are often exacerbated by human errors.
Statistics reveal that over 70% of healthcare organizations are now , recognizing its vital role in compliance and risk management. Effective training programs encompass not only the fundamentals of HIPAA regulations but also practical scenarios that enhance employees' capabilities to respond to real-world threats, particularly through the application of HIPAA technical safeguards.
Industry leaders underscore the importance of continuous training, with many recommending annual refreshers to keep staff informed about evolving cyber threats. As one specialist noted, "Establishing a safety awareness and training initiative for all employees is essential for ensuring adherence and safeguarding patient information." By prioritizing security awareness training, healthcare entities can build a robust defense against breaches, ultimately protecting their operations and reputation.
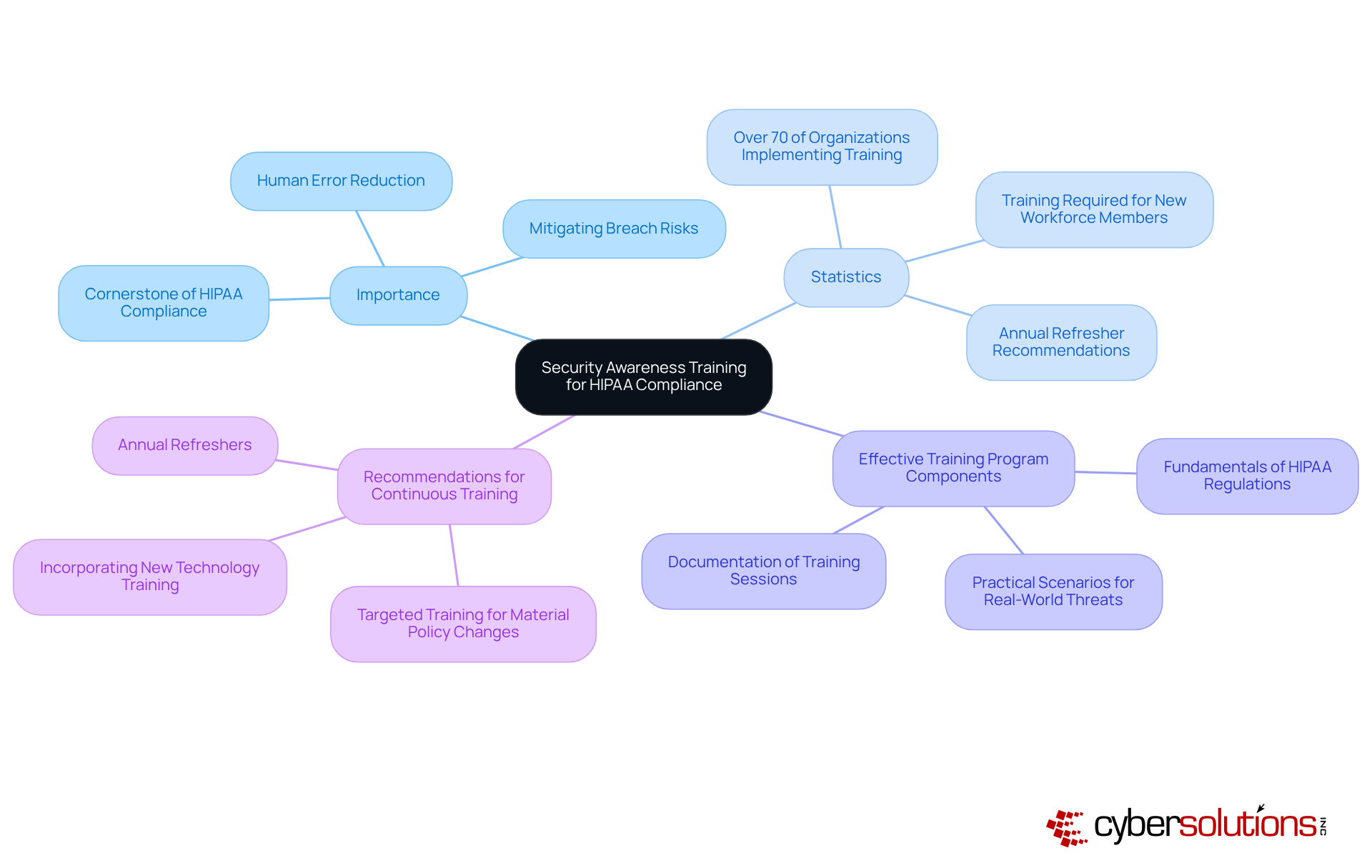
Contingency planning is essential for healthcare entities to effectively prepare for potential data breaches and emergencies. A significant percentage of healthcare organizations have recognized the critical need for robust contingency plans that not only comply with HIPAA regulations but also include HIPAA technical safeguards to ensure the protection of patient care.
Cyber Solutions Inc. plays a pivotal role in assisting these entities in developing comprehensive contingency strategies that encompass:
This proactive approach mitigates the impacts of security incidents, ensuring that organizations can swiftly navigate crises while maintaining compliance. As emphasized by cybersecurity specialists, having a well-defined plan is vital; it enables healthcare entities to respond effectively to incidents, thereby minimizing operational disruptions and enhancing overall resilience.
For instance, organizations that implement structured contingency plans along with HIPAA technical safeguards can significantly reduce risks associated with data breaches, demonstrating a commitment to protecting sensitive patient information and upholding trust within the healthcare community.
Immediate action and specialized expertise are crucial in , as illustrated by successful case studies where rapid deployment and a structured response plan led to effective threat containment and recovery.
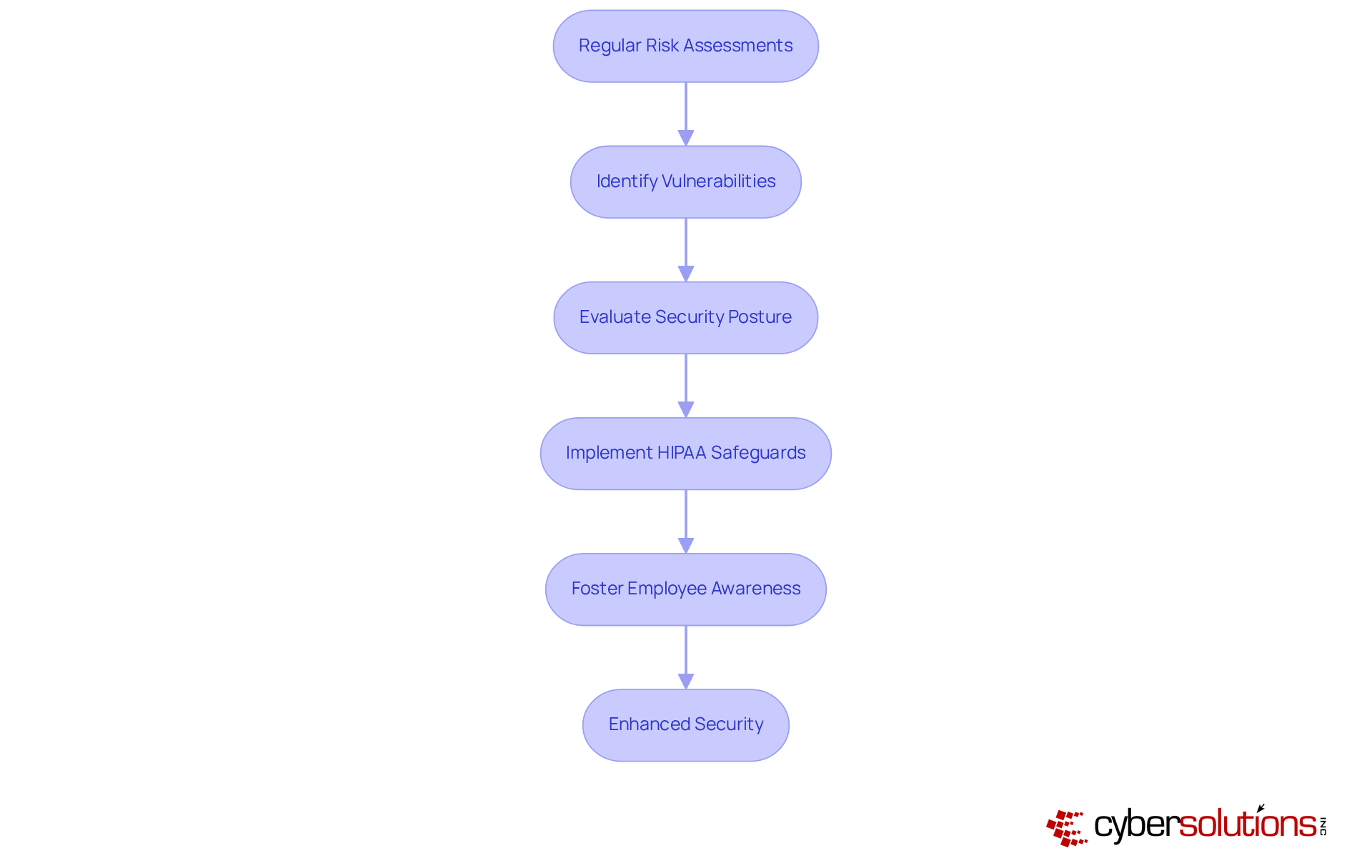
In today's digital landscape, regular risk evaluations are paramount for identifying vulnerabilities in health data protection, particularly regarding HIPAA technical safeguards compliance. Alarmingly, statistics reveal that only a fraction of healthcare entities consistently conduct these evaluations, leaving many exposed to potential breaches. Cyber Solutions Inc. specializes in comprehensive risk assessment services that meticulously evaluate a firm's security posture, pinpointing areas that require improvement. By implementing these assessments, organizations not only achieve compliance with HIPAA regulations but also proactively address security threats using HIPAA technical safeguards.
Industry leaders emphasize that fostering employee awareness and ensuring prompt reporting of phishing attempts are critical components of a robust cybersecurity strategy. As highlighted by CISA, neglecting to report such incidents can severely hinder a company's ability to respond effectively. Furthermore, regular risk assessments act as a foundational element for uncovering vulnerabilities, empowering organizations to adopt a proactive approach in safeguarding sensitive health information with HIPAA technical safeguards.
Organizations that have woven regular risk assessments into their operational protocols have reported substantial enhancements in their overall safety frameworks. This not only underscores the effectiveness of this approach in but also reinforces trust within the healthcare ecosystem. Are you ready to fortify your organization against cybersecurity threats? Embrace the power of regular risk assessments and take the first step towards a more secure future.
Effective third-party vendor management is paramount for ensuring HIPAA compliance across all partners. Organizations must establish thorough assessment and oversight procedures to guarantee that vendors adhere to stringent safety standards. Notably, 72% of healthcare entities recognize that comprehensive third-party due diligence significantly reduces legal, financial, and reputational risks. By implementing best practices such as regular security assessments and mandating Business Associate Agreements (BAAs), entities can effectively mitigate risks associated with third-party access to electronic Protected Health Information (ePHI).
Cyber Solutions plays a pivotal role in assisting companies with these assessments, ensuring that vendors are not only compliant but also capable of safeguarding sensitive data. With a robust array of that include endpoint protection and threat detection, Cyber Solutions facilitates adherence through integrated policies and tools, aiding entities in remaining audit-ready. Continuous monitoring and periodic audits are essential, given that 60% of companies lack a comprehensive list of all third parties with whom they share sensitive information, revealing a critical gap in vendor oversight.
Cybersecurity specialists emphasize that managing vendor connections has become a fundamental aspect of HIPAA compliance, particularly in relation to HIPAA technical safeguards, as healthcare entities increasingly rely on third parties for essential services. As Kevin Henry aptly notes, "Managing vendor relationships is now a fundamental aspect of HIPAA adherence, as healthcare entities increasingly depend on third parties for essential services." By prioritizing proactive vendor management and utilizing automated risk assessment tools, organizations can bolster their security posture and ensure compliance with HIPAA technical safeguards, ultimately safeguarding patient data and maintaining trust. Moreover, the significance of rapid incident response strategies, including 24-hour on-site support, cannot be overstated in minimizing damage and ensuring a swift recovery from potential breaches.

In the realm of healthcare, safeguarding sensitive patient information transcends mere regulatory compliance; it is a fundamental responsibility that C-suite leaders must prioritize. The implementation of HIPAA technical safeguards is crucial for ensuring compliance and protecting electronic Protected Health Information (ePHI). By understanding and employing these vital measures, healthcare executives can significantly bolster their organization’s cybersecurity posture, ultimately fostering trust and integrity within the healthcare system.
This article outlines ten essential HIPAA technical safeguards that every healthcare leader should consider:
These safeguards collectively form a defense against the ever-evolving landscape of cyber threats. Each safeguard not only fulfills regulatory obligations but also contributes to a culture of safety and accountability within healthcare organizations.
As cyber threats continue to rise, the urgency for healthcare leaders to adopt a proactive approach to HIPAA compliance cannot be overstated. Embracing these technical safeguards is not merely about avoiding penalties; it is about safeguarding patient privacy, enhancing operational resilience, and maintaining the trust of the communities served. By prioritizing cybersecurity measures and fostering a culture of awareness, healthcare executives can lead their organizations toward a more secure and compliant future, ultimately ensuring that patient care remains at the forefront of their mission.
What is the primary focus of Cyber Solutions Inc. in relation to healthcare cybersecurity?
Cyber Solutions Inc. focuses on providing comprehensive endpoint protection services essential for maintaining HIPAA compliance, including advanced threat detection, application allowlisting, and securing devices that access sensitive health information.
Why is application allowlisting important for healthcare organizations?
Application allowlisting is crucial as it proactively prevents unauthorized software from executing, thereby reducing the risk of malware, ransomware, and zero-day attacks, which helps in maintaining the security of electronic protected health information (ePHI).
What percentage of healthcare entities are employing endpoint protection services?
Approximately 70% of healthcare entities are now utilizing endpoint protection services to enhance their cybersecurity measures.
How does data encryption contribute to patient information security?
Data encryption safeguards electronic Protected Health Information (ePHI) both at rest and in transit, ensuring confidentiality and compliance with HIPAA standards, thus significantly reducing the risk of unauthorized access.
What encryption standard does Cyber Solutions employ to protect patient information?
Cyber Solutions employs industry-standard AES-256 encryption methods to protect patient information, which has been shown to enhance protective measures and reduce breaches.
What are role-based access controls (RBAC) and why are they important?
Role-based access controls (RBAC) are a method of restricting access based on specific user roles, ensuring that only authorized personnel can access sensitive health information, which reduces the risk of security breaches and enhances HIPAA compliance.
What are the consequences of inadequate access controls in healthcare?
Inadequate access controls can lead to significant security incidents, such as the ransomware attack affecting 585,621 individuals, highlighting the necessity for robust access management.
How can healthcare organizations improve their compliance with HIPAA requirements?
By implementing RBAC, conducting regular risk evaluations, and appointing a designated Protection Official to oversee safety policies and compliance, healthcare organizations can improve their adherence to HIPAA requirements.
What is the average cost of a healthcare breach, and why is this significant?
The average cost of a healthcare breach is approximately $7.42 million, making it imperative for organizations to regularly review their encryption protocols and application allowlists to ensure compliance and security.
How does Cyber Solutions assist healthcare organizations in cybersecurity?
Cyber Solutions provides expert guidance, proactive risk management, and comprehensive cybersecurity services to help healthcare organizations navigate HIPAA compliance and effectively protect sensitive information.