
In today's digital landscape, the significance of robust cybersecurity management services cannot be overstated. This article delves into ten essential services that bolster business resilience against the ever-evolving threat of cyber attacks. By implementing continuous monitoring, incident response, and compliance management, organizations not only shield themselves from emerging risks but also enhance their operational efficiency and regulatory compliance. As cyber threats become increasingly sophisticated, the necessity for proactive cybersecurity measures grows ever more critical.
The current landscape of cybersecurity threats presents unique challenges for businesses across all sectors. Organizations must navigate a complex web of risks that can jeopardize sensitive data and disrupt operations. This reality underscores the imperative for comprehensive cybersecurity strategies that address these vulnerabilities head-on.
Cyber Solutions offers a suite of services designed to tackle these challenges effectively. By prioritizing proactive measures, businesses can safeguard their assets while fostering a culture of security awareness. The integration of advanced technologies and expert guidance ensures that organizations remain resilient in the face of adversity, ultimately leading to improved outcomes and sustained growth.
In conclusion, the adoption of essential cybersecurity management services is not merely a defensive tactic; it is a strategic imperative for modern organizations. By embracing these proactive measures, businesses can not only protect themselves from cyber threats but also position themselves for success in an increasingly digital world.
In an era where digital threats are more pronounced than ever, the resilience of a business is fundamentally tied to its cybersecurity strategies. The increasing frequency of cyberattacks has driven organizations to pursue comprehensive management services that not only safeguard their data but also ensure compliance with a landscape of evolving regulations. This article explores ten essential cybersecurity management services that can empower businesses to strengthen their defenses, improve operational efficiency, and adeptly navigate the intricate terrain of contemporary threats.
How can organizations effectively balance the imperative for robust security measures with the escalating sophistication of cyber threats?
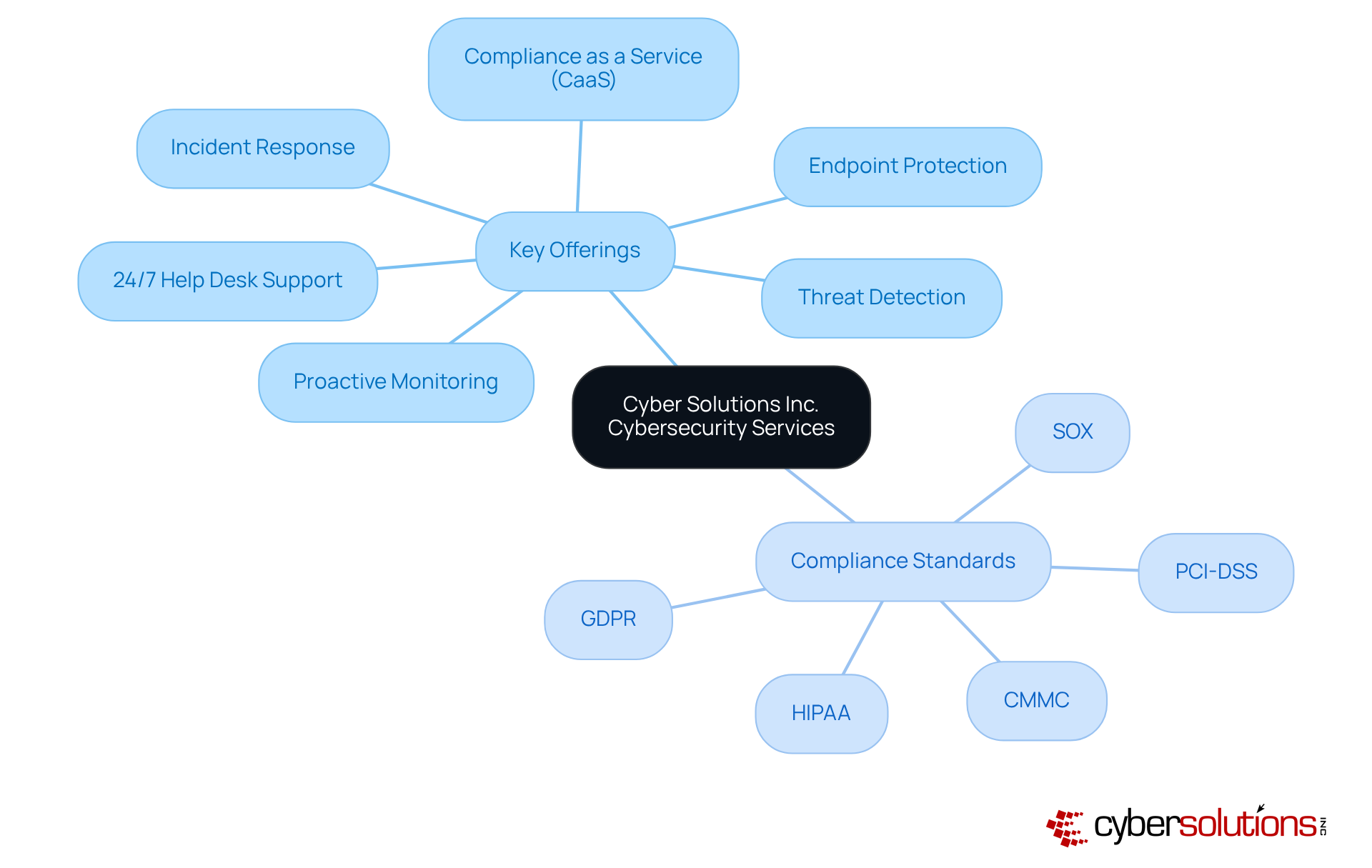
In today's digital landscape, the importance of cybersecurity cannot be overstated. Cyber Solutions Inc. provides an extensive range of designed to protect businesses from the ever-evolving risks associated with the digital environment. Key offerings include:
24/7 help desk support
threat detection
incident response
Our CaaS solutions simplify the navigation of regulatory requirements, providing , policy development, and to ensure adherence to standards such as:
This customized approach enables organizations to focus on their core operations while maintaining a robust protective stance.
By integrating these services, Cyber Solutions not only enhances protection but also boosts operational efficiency and ensures compliance with industry regulations. As more companies recognize the critical significance of cybersecurity, the demand for cyber security management services continues to rise, reflecting a broader trend toward proactive risk management and resilience in the face of . Notably, organizations allocate an average of 12% of their IT budgets to , underscoring the essential need for . Furthermore, with 56% of businesses planning to leverage AI to train their cybersecurity professionals, the integration of advanced technologies is becoming vital for sustaining a competitive edge in security management.
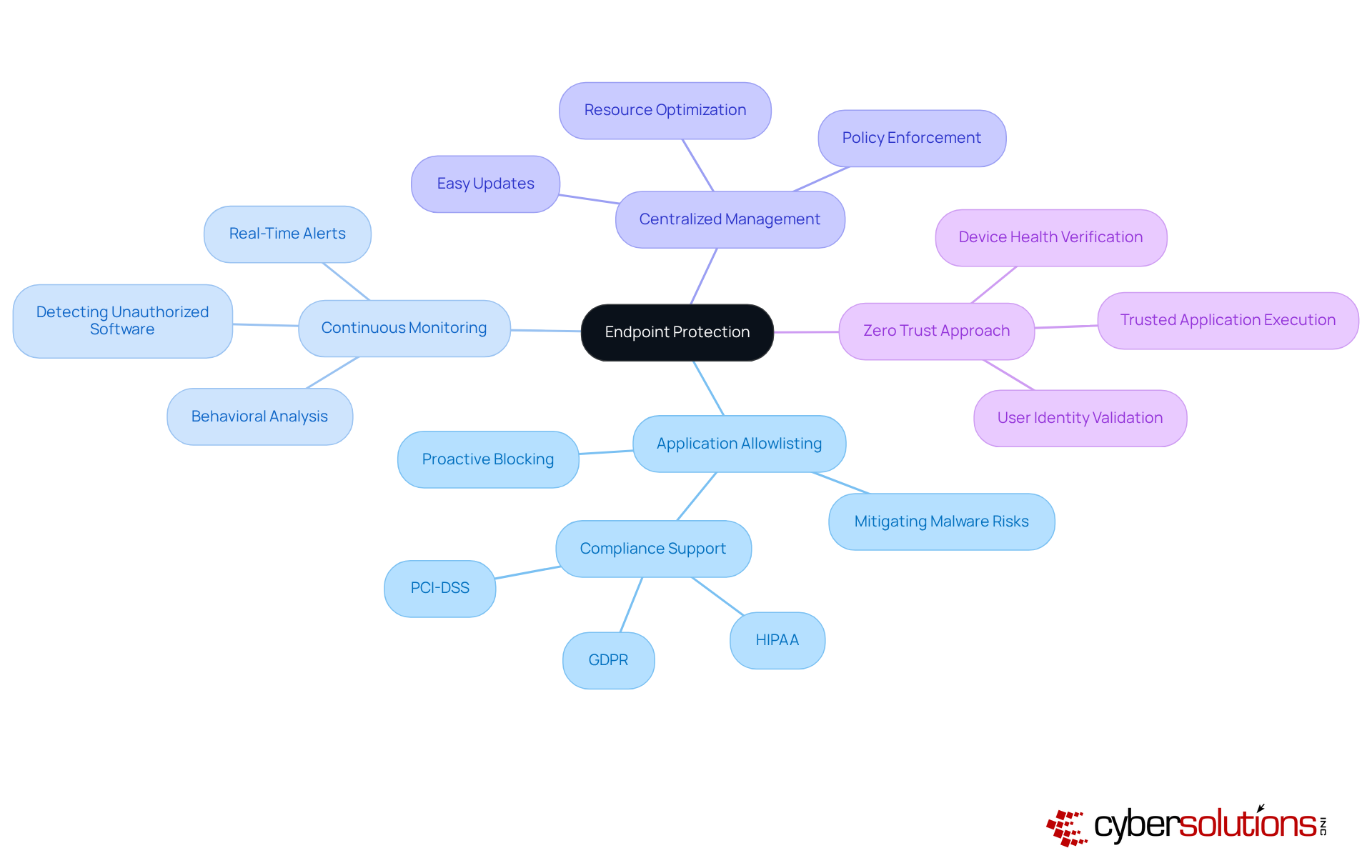
Endpoint protection is essential for safeguarding devices such as laptops, desktops, and mobile devices against a wide array of cyber risks. This comprehensive service encompasses not only but also that leverage next-generation technologies. A pivotal element of endpoint protection is , which proactively blocks unauthorized or malicious applications from executing on devices. By permitting only pre-approved software to run, organizations can significantly mitigate the risks of malware, ransomware, and , thereby ensuring the security of sensitive information.
is crucial for detecting any attempts to execute unauthorized software, while centralized management facilitates easy updates and policy enforcement across all devices. Regular updates and vigilant monitoring are imperative to adapt to the ever-evolving threat landscape, ensuring that defenses remain robust against sophisticated attacks such as ransomware and zero-day exploits. Additionally, application allowlisting aids enterprises in meeting , thereby reinforcing their overall security posture.
Moreover, adopting a zero-trust approach enhances protection by consistently verifying device health and user identity, ensuring that only trusted applications are allowed to run. In this landscape of increasing cyber threats, it is vital for organizations to implement that allow them to take , ensuring their defenses are not only effective but also adaptable to emerging challenges.
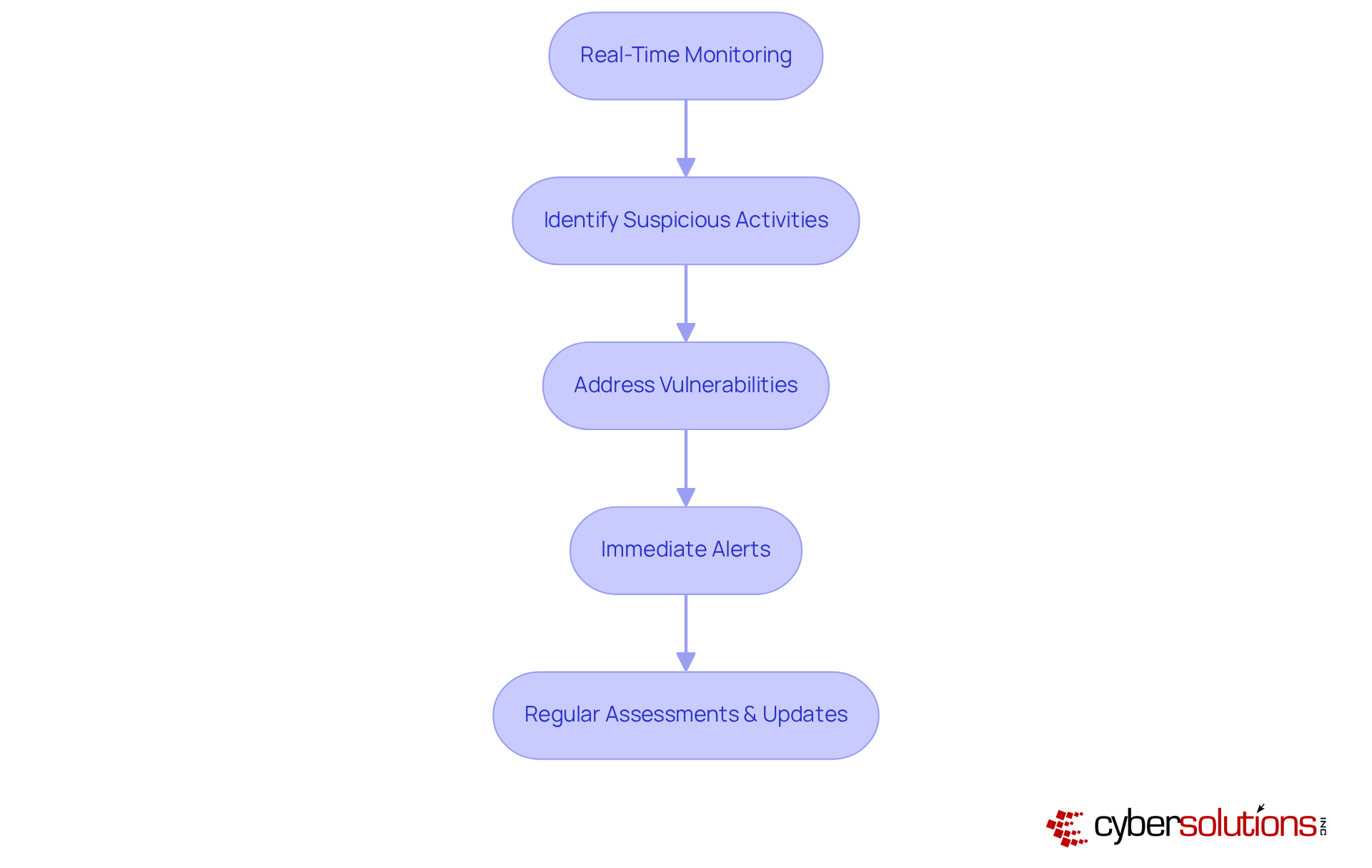
In today's digital landscape, the importance of cybersecurity cannot be overstated. leverage to monitor network traffic and identify suspicious activities in real-time, ensuring that organizations remain vigilant against ever-evolving threats. By employing machine learning and behavioral analytics, organizations can effectively detect anomalies that may signify a security breach, and maintaining operational integrity.
Our commitment to means that potential vulnerabilities are swiftly addressed, allowing for immediate alerts and . This not only prevents downtime but also mitigates the risk of breaches, ensuring that healthcare organizations can focus on their core mission without interruption. Timely empowers organizations to implement prompt measures, minimizing the potential impact of cyber events.
Furthermore, regular assessments and updates to detection protocols are crucial in staying ahead of threats such as ransomware, phishing, and other malware attacks. By continually refining these protocols, organizations can enhance their defenses and foster a culture of . In an era where are increasingly sophisticated, is not just a necessity—it's a strategic imperative.
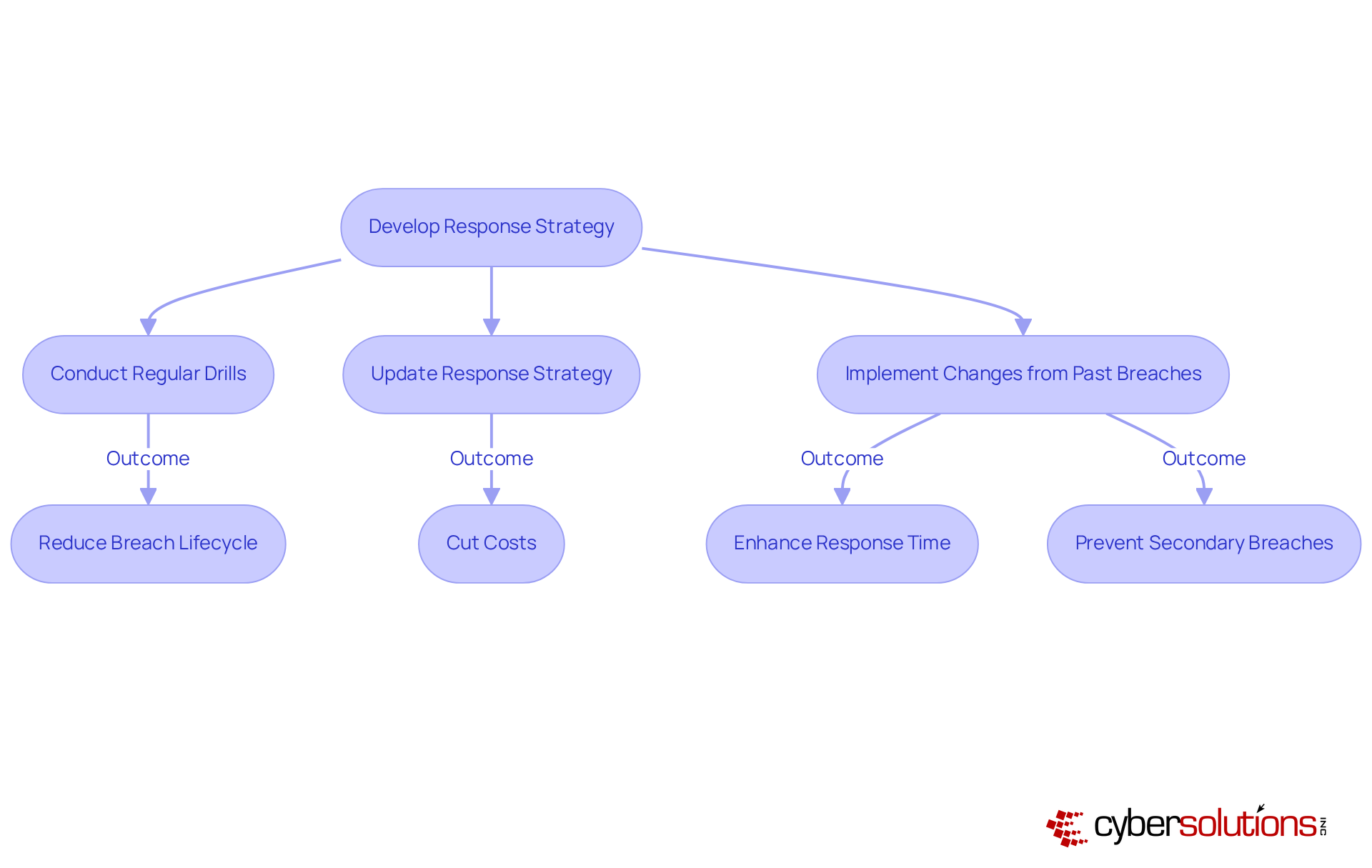
Response services are crucial for managing and mitigating the impact of cyber events, particularly in the healthcare sector. The initial step in this process involves developing a comprehensive that outlines the necessary actions when a breach occurs. Organizations lacking a formal response plan face an , resulting in costs that are 58% higher per incident compared to those with a documented strategy. Regularly conducting drills and updating the response strategy are vital activities that prepare teams to react swiftly and effectively during an incident.
Consider this: organizations that implement changes based on past breaches can . Additionally, firms that conduct response testing at least biannually can save, on average, $1.49 million for each breach. This proactive stance not only shortens recovery time but also significantly diminishes the , which currently average $4.88 million globally.
Looking ahead to 2025, effective response planning strategies will include:
Organizations that provide can reduce breaches by 60%, addressing the human element that contributes to 68% of violations. By prioritizing these strategies, especially in the healthcare sector, businesses can bolster their resilience against and ensure a more effective response to incidents through .
, which are a cornerstone of a robust cybersecurity strategy, are often conducted as part of to systematically evaluate an entity's IT infrastructure and identify vulnerabilities. This critical process includes scanning for outdated software, misconfigurations, and other weaknesses that attackers may exploit. By regularly conducting these assessments as part of their cyber security management services, businesses can effectively prioritize remediation efforts, thereby and ensuring such as HIPAA, PCI-DSS, and GDPR.
In 2024, a significant 24% of entities reported conducting more than four times a year, a notable increase from 15% in 2023. This trend underscores a growing awareness of the need for continuous monitoring and rapid response to emerging threats. For instance, organizations that have adopted ongoing scanning practices have substantially reduced the time required to detect and address vulnerabilities, effectively closing gaps before they can be exploited.
The impact of regular vulnerability evaluations on an organization's defensive stance cannot be overstated. These assessments not only aid in identifying potential weak points but also foster a . As cyber risks evolve rapidly, maintaining a vigilant stance through cyber security management services. Experts assert that vulnerability assessments must be an ongoing process—both manual and automated—to ensure that newly discovered vulnerabilities are promptly patched or remediated.
Current trends in vulnerability management for 2025 indicate a shift towards integrating automated tools that streamline the scanning process and enhance visibility into security risks. Organizations are increasingly investing in solutions that provide comprehensive insights into their vulnerabilities, facilitating quicker action when new threats are identified. This proactive approach is vital for minimizing incident costs and through effective cyber security management services.
In addition to vulnerability assessments, application allowlisting serves as a critical strategy in preventing unauthorized software execution, thereby . By ensuring that only approved applications can operate, entities significantly diminish the risk of malware and ransomware attacks. Coupled with , which deliver real-time insights and instant alerts for suspicious activities, businesses can strengthen their proactive cybersecurity measures. Practical implementation of application allowlisting includes regularly updating allowlists and utilizing centralized management tools to streamline control and policy enforcement.
In today's , emerges as a vital solution for organizations striving to navigate the intricate , , and GDPR. This service offers comprehensive solutions, encompassing regular audits, policy development, and targeted training. By doing so, it not only ensures that businesses but also fosters a culture of accountability.
Outsourcing compliance management allows companies to concentrate on their core operations, significantly lowering the risk of non-compliance penalties. The empowers businesses to stay ahead of regulatory changes, enabling them to adapt swiftly to evolving requirements. A critical element of this proactive approach is application allowlisting, which acts as a gold standard in cybersecurity by preventing unauthorized software from executing. This strategy not only but also assists organizations in meeting stringent compliance mandates.
For instance, entities that have effectively adopted CaaS, particularly those utilizing customized solutions, have reported and a marked reduction in compliance-related incidents. As we approach 2025, with regulatory scrutiny intensifying, leveraging CaaS will be paramount for maintaining compliance and safeguarding organizational integrity. As KRITIKA SINHA emphasizes, '[Compliance as a Service (CaaS)](https://discovercybersolutions.com/compliance-as-a-service/cmmc-compliance) offers a transformative solution, providing streamlined processes, enhanced security, cost efficiency, and scalability.
services are essential for safeguarding critical business data and ensuring operational continuity. Regular backups, off-site storage, and robust empower organizations to swiftly restore operations after data loss incidents. A well-organized backup strategy not only minimizes downtime but also mitigates financial losses, enabling businesses to remain resilient against and natural disasters through . Alarmingly, 94% of companies that face significant data loss cannot recover, highlighting the necessity of a . Organizations that adopt thorough can significantly reduce , allowing for rapid recovery from disruptions.
Best practices involve conducting regular to identify critical functions and dependencies, which inform recovery priorities and establish key benchmarks such as Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO). Moreover, leveraging modern hybrid cloud solutions can eliminate the need for expensive secondary facilities, optimizing while enhancing recovery capabilities. Hybrid cloud disaster recovery (DR) offers benefits like reduced facility costs, pay-as-you-use pricing, and instant capacity.
In today’s environment, where the average cost of IT downtime exceeds $300,000 per hour for mid-sized enterprises, is not merely prudent—it is vital for survival.
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. (MSSPs) provide essential that include:
Healthcare CFOs face unique challenges as they navigate an environment rife with . By collaborating with , organizations can leverage expert knowledge and advanced technologies to significantly enhance their .
Our are designed to ensure minimal operational disruption, particularly for healthcare entities, by adopting a . With 24/7 network monitoring and instant alerts, we detect anomalies and potential vulnerabilities in real-time, enabling swift action to prevent downtime or breaches. This proactive strategy not only helps businesses stay ahead of but also maximizes their cybersecurity investments, providing robust protection against ransomware, phishing, and other malware attacks.
Are you prepared to safeguard your organization against evolving threats? With Cyber Solutions, you can confidently , ensuring that your and resilient.
stands at the forefront of modern IT strategy, effectively merging the strengths of internal IT teams with the specialized expertise of external providers. This collaborative model empowers enterprises to without the burden of extensive hiring.
By leveraging external expertise through , companies can significantly bolster their security protocols, optimize operations, and against . Organizations that have embraced co-managed IT support have reported a remarkable 40% reduction in support tickets, showcasing .
Furthermore, this approach enables internal teams to concentrate on while external partners manage high-volume tasks, ultimately fostering enhanced operational resilience. As cyber challenges grow increasingly sophisticated, leveraging cyber security management services to integrate external expertise not only mitigates risks but also ensures compliance with , underscoring co-managed IT support as an essential component of contemporary business strategy.
are essential for equipping employees with the knowledge to recognize and respond to potential threats. These initiatives cover critical topics such as phishing awareness, password management, and safe browsing practices. By empowering staff, organizations can significantly reduce the likelihood of cyber incidents stemming from human errors, thereby cultivating a robust culture of safety awareness.
Consider the , successfully restored 4,500 endpoints within two weeks. This achievement was made possible through immediate training on identifying suspicious emails and adhering to proper cybersecurity hygiene. Such an efficient response ensured that critical healthcare operations could continue with minimal downtime. The provider’s commitment to , particularly with a focus on a , underscores the importance of proactive protective strategies.
Moreover, organizations like Franciscan Alliance have implemented monthly phishing simulations and quarterly assessments, fostering continuous education and engagement among staff. This proactive methodology not only enhances awareness but also diminishes the likelihood of successful attacks.
A study from EDUCAUSE indicates that organizations with effective training programs experience a notable reduction in breaches. By measuring engagement and analyzing incident response rates, businesses can refine their training initiatives, ensuring they address the most pressing threats, as exemplified by the healthcare provider's experience.
As we approach , themed 'Building a Cyber Strong America,' the necessity for becomes increasingly evident, especially in sectors like healthcare and finance, where are critical. Organizations must customize their training to align with specific business needs, ensuring employees are adequately prepared to safeguard sensitive information.
Ultimately, not only protects the organization but also empowers employees to actively engage in the protection of digital assets, reinforcing the notion that are a collective responsibility.
In today's increasingly interconnected world, the importance of cybersecurity management services cannot be overstated. These services transcend mere protective measures; they represent essential strategies that empower businesses to adeptly navigate the complex landscape of digital threats. By embracing a comprehensive cybersecurity approach, organizations can bolster their resilience, protect sensitive data, and ensure operational continuity amidst evolving cyber risks.
Key aspects of effective cybersecurity management have been underscored, including:
Each of these components is vital in strengthening an organization's defenses. Regular vulnerability assessments, coupled with the integration of managed security service providers, further enhance security postures, equipping businesses to confront potential breaches and regulatory challenges with confidence.
Ultimately, the journey toward robust cybersecurity is a collective endeavor, necessitating not only advanced technologies but also a culture of awareness and preparedness among employees. Organizations are urged to invest in ongoing training and to leverage external expertise through co-managed IT support. This strategic investment fosters a resilient framework that not only defends against current threats but also adapts to future challenges. The proactive implementation of cybersecurity management services is not merely a safeguard; it is a strategic imperative for any organization aspiring to thrive in today's digital landscape.
What services does Cyber Solutions Inc. offer for cybersecurity management?
Cyber Solutions Inc. provides a range of cybersecurity management services, including 24/7 help desk support, proactive monitoring, endpoint protection, threat detection, incident response, and Compliance as a Service (CaaS).
What is Compliance as a Service (CaaS) and what does it include?
CaaS simplifies the navigation of regulatory requirements by providing risk assessments, policy development, and ongoing compliance monitoring to ensure adherence to standards such as HIPAA, PCI-DSS, CMMC, SOX, and GDPR.
How does Cyber Solutions Inc. enhance operational efficiency?
By integrating various cybersecurity services, Cyber Solutions Inc. enhances protection, boosts operational efficiency, and ensures compliance with industry regulations, allowing organizations to focus on their core operations.
What percentage of IT budgets do organizations typically allocate to cybersecurity measures?
Organizations allocate an average of 12% of their IT budgets to cybersecurity measures, highlighting the essential need for investment in these services.
How is artificial intelligence being utilized in cybersecurity?
56% of businesses plan to leverage AI to train their cybersecurity professionals, indicating the growing importance of advanced technologies in maintaining a competitive edge in security management.
What is endpoint protection and why is it important?
Endpoint protection safeguards devices like laptops, desktops, and mobile devices against cyber risks. It includes traditional antivirus solutions and advanced threat detection capabilities, helping to mitigate risks from malware, ransomware, and zero-day attacks.
What is application allowlisting and how does it contribute to security?
Application allowlisting is a security measure that permits only pre-approved software to run on devices, proactively blocking unauthorized or malicious applications, thus significantly reducing the risk of malware and ransomware attacks.
How does threat detection work and what technologies are involved?
Threat detection services monitor network traffic and identify suspicious activities in real-time using advanced technologies such as machine learning and behavioral analytics to detect anomalies that may indicate a security breach.
Why is continuous monitoring important in cybersecurity?
Continuous monitoring is crucial for detecting unauthorized software activity and addressing potential vulnerabilities swiftly, which helps prevent downtime and mitigates the risk of breaches.
What is a zero-trust approach in cybersecurity?
A zero-trust approach involves consistently verifying device health and user identity to ensure that only trusted applications are allowed to run, thereby enhancing protection against cyber threats.