
In today's rapidly evolving healthcare landscape, cybersecurity is not just a necessity; it is a critical priority for CFOs. With the increasing frequency of cyber threats, healthcare organizations face unique challenges that can jeopardize patient data and operational integrity. This article outlines ten essential managed IT solutions provider services that are crucial for healthcare CFOs, focusing on cybersecurity, operational efficiency, and compliance with regulations like HIPAA.
These services, including 24/7 help desk support, endpoint protection, and incident response, are vital for safeguarding patient data and ensuring continuous business operations. As cyber threats become more sophisticated, the implications for healthcare organizations are profound. How can CFOs navigate these challenges effectively? The answer lies in leveraging specialized managed IT solutions that not only protect sensitive information but also enhance operational resilience.
By investing in these essential services, healthcare CFOs can fortify their organizations against potential breaches and ensure compliance with regulatory requirements. The importance of having a robust IT infrastructure cannot be overstated, as it serves as the backbone of a secure healthcare environment. In an era where patient trust is paramount, these solutions are not merely beneficial; they are indispensable for maintaining the integrity of healthcare delivery.
In the complex and ever-evolving world of healthcare, the stakes are higher than ever for CFOs tasked with safeguarding sensitive patient data while ensuring operational efficiency. As cyber threats grow increasingly sophisticated, the need for comprehensive managed IT solutions has become critical. This article explores ten essential services offered by managed IT providers, specifically designed to empower healthcare CFOs in navigating the intricate landscape of cybersecurity and compliance.
How can these solutions not only protect organizations from potential breaches but also enhance overall business performance in a sector where every second counts?
In today's healthcare landscape, cybersecurity is not just an option; it is a necessity. Cyber Solutions Inc. serves as a managed IT solutions provider, offering an extensive range of services tailored specifically for medical facilities to address the unique challenges they face. With operational efficiency and robust cybersecurity measures at the forefront, the company empowers CFOs to allocate resources effectively while ensuring such as HIPAA.
The threats posed by cybercriminals are ever-evolving, and healthcare organizations are prime targets. CFOs must navigate these challenges while maintaining the integrity of patient data and ensuring operational continuity. Cyber Solutions operates as a managed IT solutions provider, delivering essential services such as:
These offerings are meticulously designed to streamline IT operations and mitigate risks associated with cyber threats.
By adopting a security-first strategy, Cyber Solutions guarantees that medical entities can effortlessly manage intricate regulatory standards. This enables healthcare organizations to focus on what truly matters: expansion and patient care. Are you ready to fortify your organization against cyber threats and ensure compliance? Partner with Cyber Solutions Inc. to safeguard your future.
24/7 help desk assistance is essential for medical entities, ensuring rapid resolution of IT issues and minimizing disruptions in patient care and administrative functions. This service guarantees that technical problems are addressed swiftly, allowing medical personnel to concentrate on their primary responsibilities without the distraction of IT-related challenges. By investing in continuous support, CFOs can significantly bolster operational resilience, culminating in enhanced service delivery and improved patient outcomes.
Research indicates that organizations with effective IT support enjoy higher patient satisfaction rates, as the timely resolution of issues directly correlates with superior care experiences. Furthermore, 24/7 support can avert potential revenue losses tied to downtime, positioning it as a strategic investment for healthcare leaders seeking to optimize both patient care and operational efficiency.
For example, Cyber Solutions has successfully implemented rapid incident response strategies that not only tackle immediate IT challenges but also strengthen overall cybersecurity posture. This layered approach to IT support, combined with proactive cybersecurity services, ensures compliance with HIPAA regulations and fortifies the entity against cyber threats.
To implement or evaluate 24/7 help desk support, CFOs should assess their current IT support capabilities and consider forming partnerships with a .
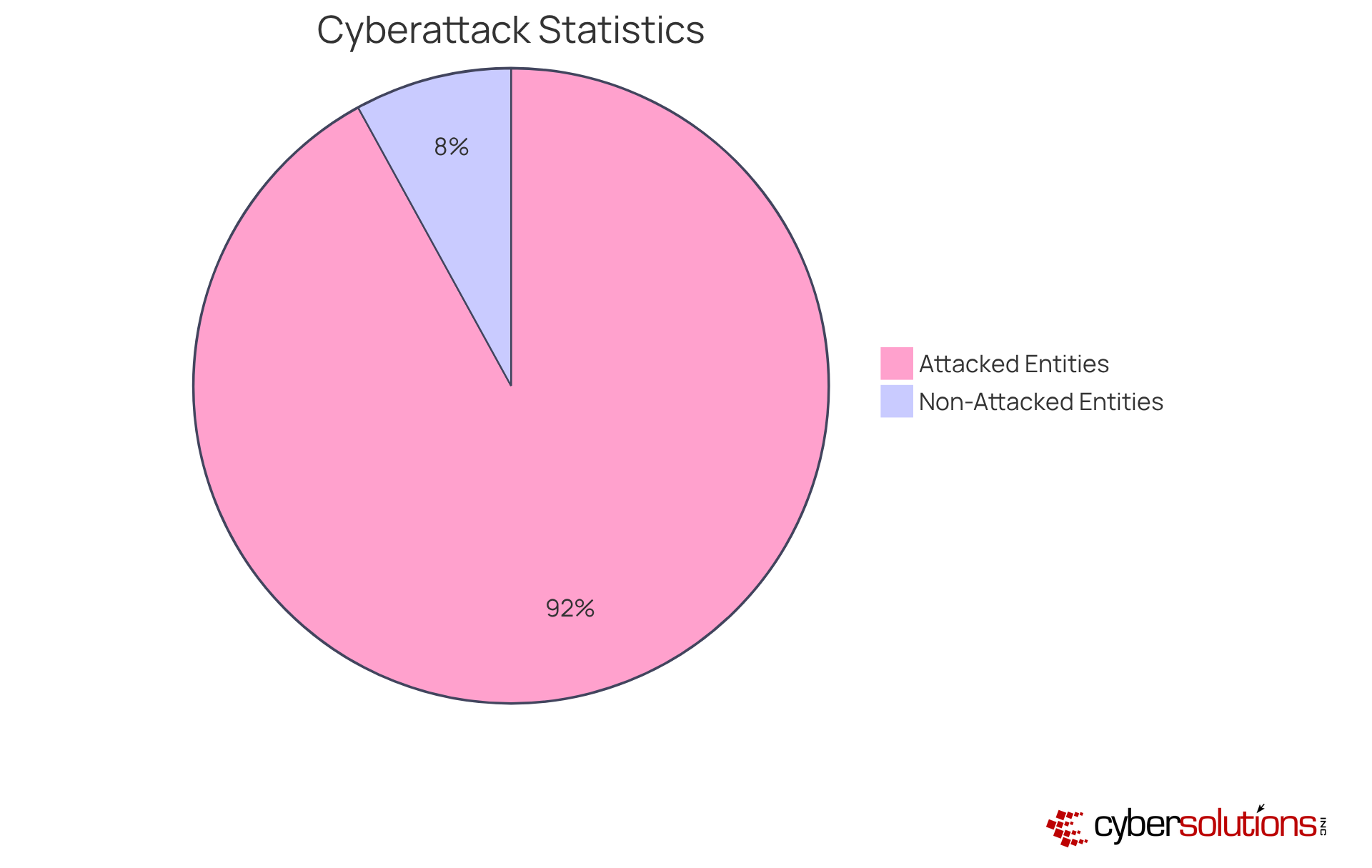
Endpoint protection stands as a cornerstone of a robust cybersecurity strategy, particularly within the medical sector. This vital aspect focuses on securing devices—like computers and mobile devices—that connect to the network, effectively shielding them from malware and unauthorized access. In 2025, medical organizations face alarming statistics, with 79% reporting ransomware attacks in the past year. This underscores the .
By deploying advanced endpoint protection solutions, including application allowlisting, medical providers can significantly mitigate the risk of data breaches while ensuring compliance with stringent regulations such as HIPAA. Application allowlisting proactively prevents unauthorized software from executing, thereby reducing the attack surface and minimizing vulnerabilities that could be exploited by attackers.
The financial ramifications of ransomware attacks in healthcare are staggering, with the typical cost amounting to $1.85 million per incident, emphasizing the dire consequences of inadequate endpoint security. This approach not only safeguards sensitive patient information but also fosters trust among patients and stakeholders.
Cybersecurity experts assert that layered defenses, regular updates, and employee awareness are essential for maintaining a secure environment. Successful endpoint protection strategies encompass:
Organizations investing in comprehensive endpoint security solutions from a managed IT solutions provider, including continuous monitoring and application allowlisting, can anticipate a reduction in the frequency and impact of cyber incidents.
As the medical landscape evolves, prioritizing endpoint protection is vital for safeguarding patient data and ensuring operational integrity. However, the shortage of cybersecurity experts in the medical field complicates the implementation of effective endpoint protection strategies, thereby increasing the risk of breaches. Healthcare entities experience an average downtime of 24 days following a ransomware attack, highlighting the operational consequences of cyber incidents.

In today's rapidly evolving healthcare landscape, backup and disaster recovery services have become indispensable for medical institutions. These services play a critical role in safeguarding vital data against loss from cyberattacks, natural disasters, or system failures. By facilitating swift data restoration, they significantly reduce downtime and ensure business continuity. Investing in robust backup solutions not only shields organizations from the financial repercussions of data loss—averaging an alarming $9.77 million per breach—but also aids in maintaining compliance with stringent regulatory mandates such as HIPAA.
The urgency for effective data protection strategies is underscored by recent statistics, which reveal that in 2023 alone, medical entities experienced an average of 364,571 records compromised each day. This staggering figure highlights the pressing need for healthcare organizations to adopt . As the medical field increasingly grapples with sophisticated cyber threats, implementing these solutions is paramount for mitigating risks and ensuring operational resilience.
In conclusion, the integration of comprehensive backup and disaster recovery services is not merely a precaution; it is a strategic imperative for healthcare institutions. By prioritizing these services, organizations can protect their most valuable asset—their data—while also fostering trust and compliance in an environment fraught with challenges.
In today's healthcare landscape, cybersecurity is not just a priority; it is a necessity. A managed IT solutions provider empowers medical providers to bolster their internal IT teams with specialized external expertise, effectively addressing the complex IT challenges they face while maintaining operational control. By collaborating with a managed IT solutions provider such as Cyber Solutions, CFOs can ensure that their teams harness cutting-edge technologies and industry best practices, including:
This strategic partnership enhances operational efficiency and significantly reduces costs associated with hiring and training in-house staff, with potential savings of up to 35%.
The integration of external IT knowledge facilitates proactive maintenance and rapid problem-solving—critical elements in medical environments where downtime can jeopardize patient care. Furthermore, Cyber Solutions offers predictable pricing models and scalable service plans, allowing medical institutions to manage their IT budgets effectively. The ongoing need for vigilant surveillance, extensive firewall solutions, advanced security intelligence, and customized access controls cannot be overstated, as these measures are essential in preserving quality patient care by preventing system failures and safeguarding against escalating cybersecurity threats.
Ultimately, a managed IT solutions provider offering fosters a more resilient IT infrastructure, enabling medical entities to focus on their primary mission: delivering quality patient care while enhancing their cybersecurity posture against increasing risks.
In today's healthcare landscape, cybersecurity is not just an option; it's a necessity. Managed security services provide medical facilities with essential proactive defense against cyber threats through ongoing monitoring, advanced threat detection, and efficient crisis response. By outsourcing these critical functions to specialized experts, organizations can significantly enhance their security posture and respond swiftly to potential breaches. This proactive approach not only safeguards sensitive patient information but also aids CFOs in navigating compliance with regulatory standards, ultimately reducing the financial repercussions associated with cyber incidents.
Consider this:
By investing in managed security services, CFOs in the medical sector can effectively mitigate risks and protect their organizations from an increasingly perilous threat environment. The time to act is now—secure your facility's future against cyber threats.
Proactive risk identification systems are essential for medical facilities, enabling them to detect potential security breaches before they escalate into significant incidents. By leveraging advanced technologies such as artificial intelligence (AI) and machine learning (ML), healthcare organizations can continuously monitor network activity for unusual patterns, facilitating rapid responses to emerging threats. This proactive approach not only safeguards sensitive patient information but also mitigates the associated with data breaches, which can exceed $10 million per occurrence in the healthcare sector.
Current trends reveal an increasing dependence on AI and ML in cybersecurity, with 45% of organizations already incorporating these technologies into their security frameworks. Experts highlight the critical nature of early breach detection, noting that AI-driven systems can decrease incident response times by as much as 70%. As one cybersecurity leader remarked, "The necessity of proactive risk detection in a breach-filled world cannot be overstated."
Successful implementations of AI-enhanced threat detection within the medical field have shown remarkable improvements in security posture. For instance, AI-driven solutions have achieved a 94% reduction in investigation durations and a 78% decrease in false positive notifications, allowing medical institutions to focus on critical vulnerabilities rather than being overwhelmed by alerts. These advancements not only enhance operational efficiency but also foster a culture of security awareness, ultimately protecting patient data and maintaining trust in medical services.

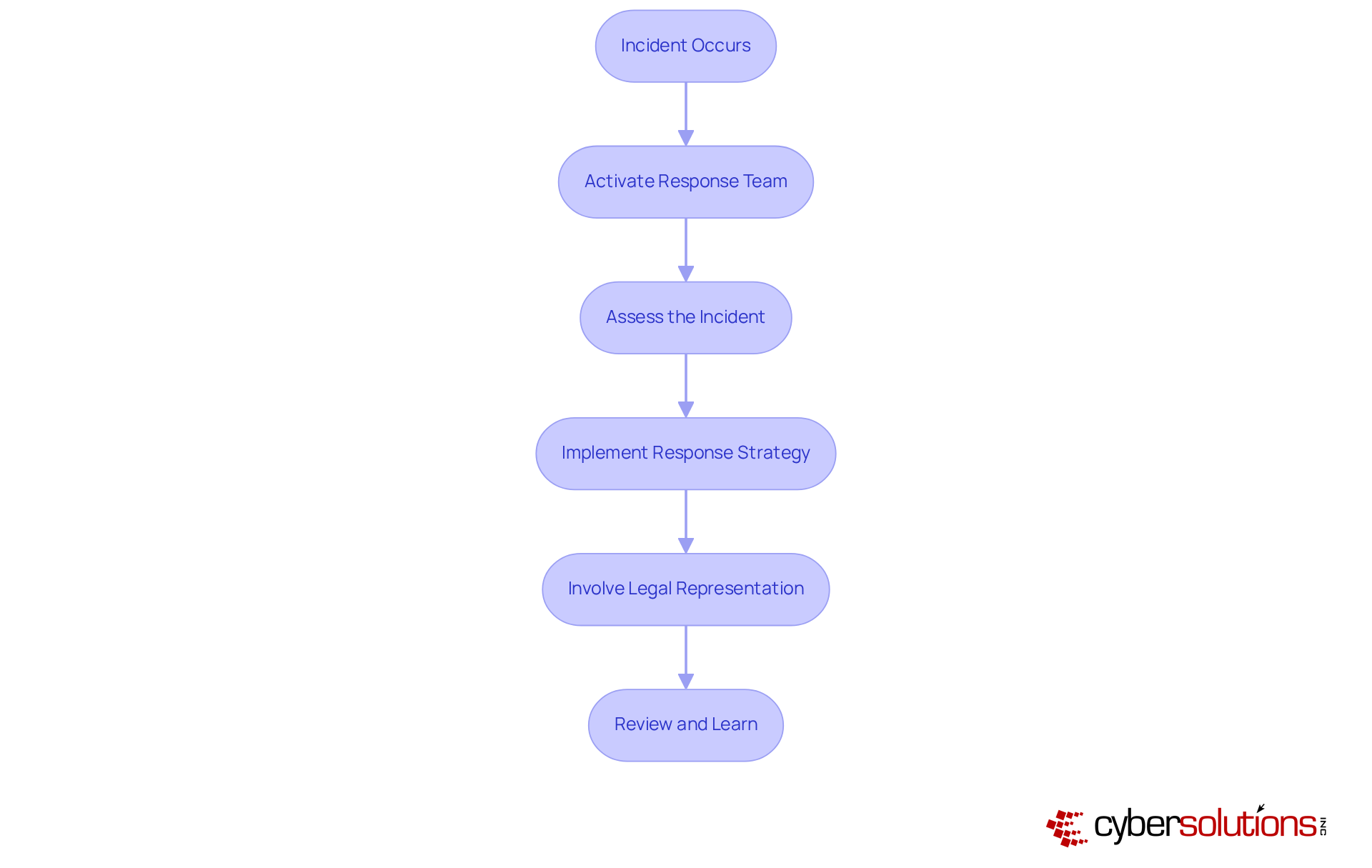
In today's rapidly evolving digital landscape, crisis response services are paramount for healthcare institutions, enabling them to swiftly address cyber events and significantly mitigate potential harm. A robust response strategy delineates critical actions to undertake during a breach, thereby empowering organizations to manage threats with efficiency and precision. Investing in these capabilities not only shields against the financial repercussions of cyber incidents but also ensures compliance with stringent regulatory requirements.
Recent case analyses reveal a striking statistic: entities equipped with well-rehearsed response strategies can detect breaches up to 54 days faster than those without such preparedness. This underscores the critical importance of readiness in the face of cyber threats. Furthermore, specialists emphasize that involving legal representation immediately following an incident is vital for navigating the complexities of compliance and minimizing associated risks.
As cyber threats continue to evolve, it is imperative for CFOs within the medical sector to prioritize incident response planning. This proactive approach is essential not only for but also for maintaining operational integrity in an increasingly perilous environment.
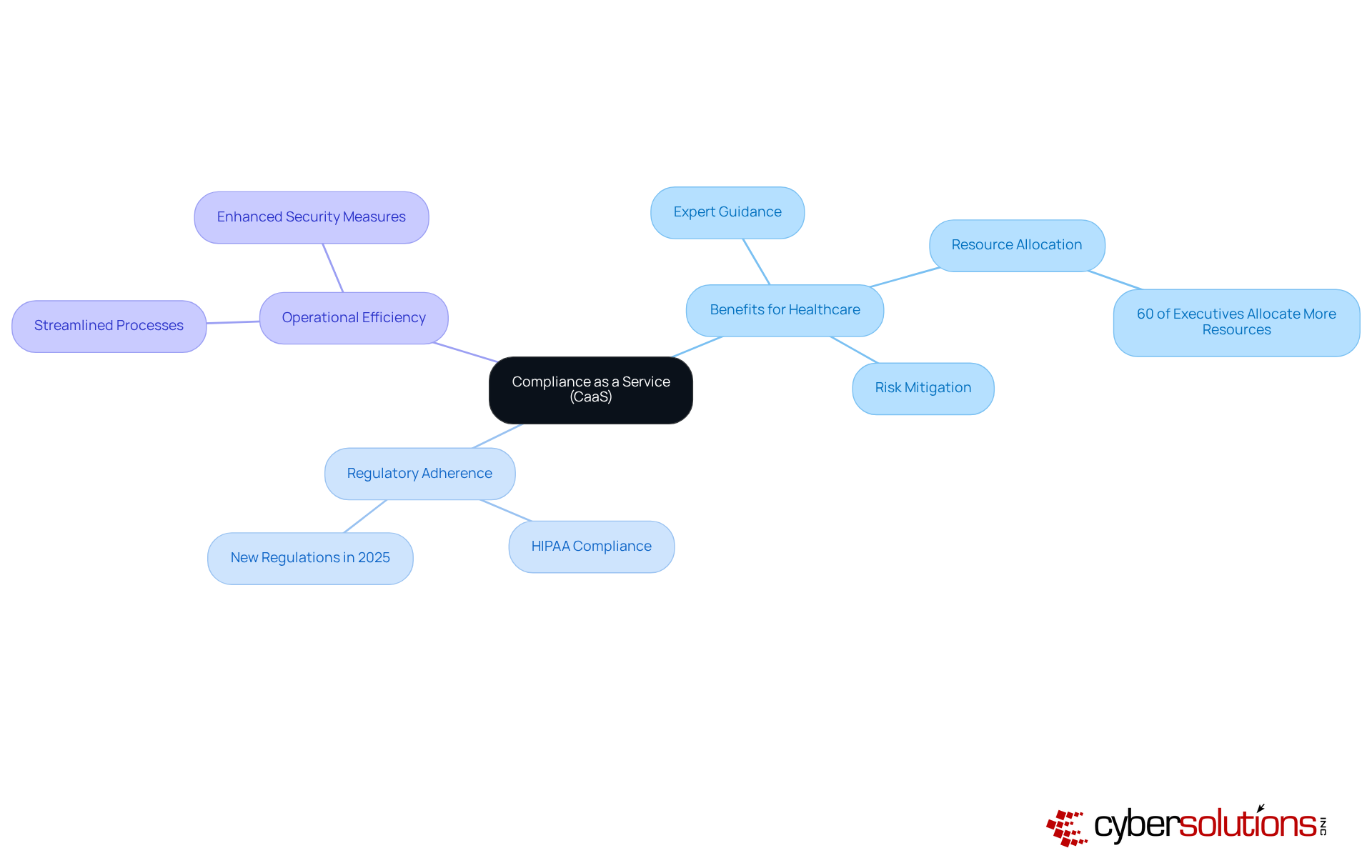
Compliance as a Service (CaaS) is essential for medical facilities navigating the intricate landscape of regulatory adherence. By outsourcing compliance functions, businesses can harness expert guidance and thorough assessments, ensuring alignment with critical regulations such as HIPAA. This strategic approach significantly mitigates the risk of , allowing CFOs to concentrate on high-level initiatives that foster organizational growth while upholding regulatory integrity.
The profound impact of CaaS on HIPAA compliance cannot be overstated; it not only streamlines adherence processes but also boosts operational efficiency. As healthcare entities face increasing scrutiny and evolving regulations, the ability to rely on specialized compliance services becomes indispensable. Notably, 60% of executives report allocating more resources to compliance, acknowledging its vital role in protecting patient data and ensuring operational continuity. This commitment is further reinforced by the comprehensive reporting and documentation tailored to HIPAA requirements that CaaS delivers.
Industry leaders underscore the necessity of simplifying regulatory adherence for effective healthcare operations. By embracing CaaS, organizations can foster a culture of compliance, ensuring that all staff members are well-informed and equipped to tackle regulatory challenges. This proactive strategy not only enhances compliance maturity but also positions entities to respond adeptly to the shifting regulatory landscape, ultimately strengthening patient trust and enhancing institutional reputation.
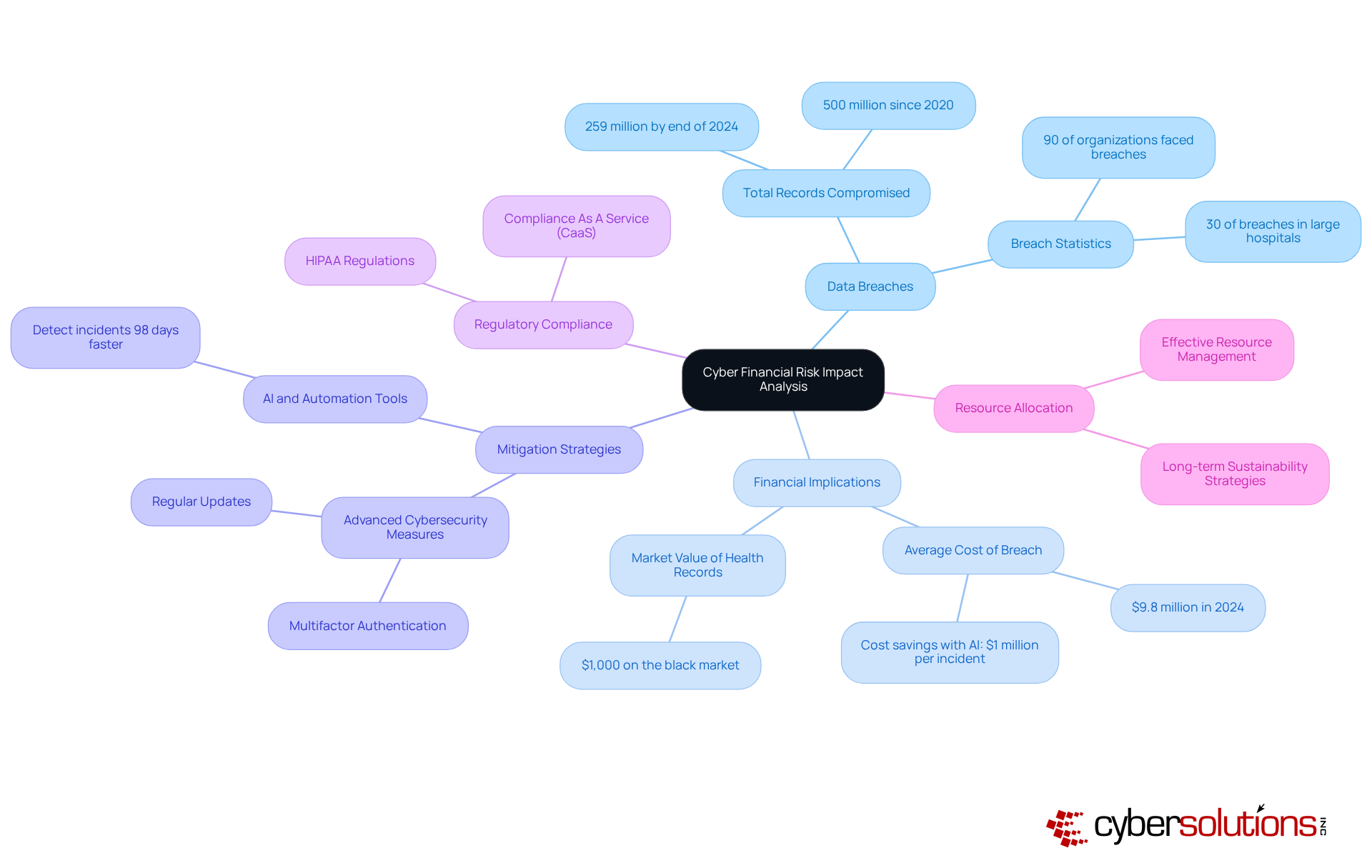
Cyber financial risk impact analysis is crucial for medical entities, offering vital insights into the potential financial ramifications of cyber threats. In a landscape where the healthcare sector has experienced a staggering increase in breaches—over 259 million health records compromised by the end of 2024—systematic risk assessments become indispensable. Organizations that evaluate the risks associated with data breaches and other cyber events can make informed decisions regarding their cybersecurity investments. With , robust financial risk evaluations are no longer optional; they are essential.
CFOs can leverage this analysis to allocate resources more effectively and develop strategies that mitigate financial risks, ensuring the long-term sustainability of their organizations. For example, implementing advanced cybersecurity measures—such as multifactor authentication and regular updates—can significantly diminish vulnerability to attacks. Moreover, healthcare entities that utilize AI and automation tools have demonstrated the ability to identify and manage incidents an impressive 98 days faster than average, leading to considerable cost savings, averaging nearly $1 million per case.
Understanding financial risks in cybersecurity transcends mere asset protection; it encompasses safeguarding the organization’s reputation and ensuring operational continuity. As illustrated in our case studies, swift incident response and specialized expertise can dramatically enhance recovery efforts and security protocols. As the medical industry faces increasing regulatory scrutiny and a shifting risk landscape, proactive financial risk management is paramount. By prioritizing cyber financial risk impact analysis and adopting Compliance As A Service (CaaS) solutions, healthcare CFOs can bolster their organizations' resilience against cyber threats while effectively preparing for audits and maintaining compliance with regulations such as HIPAA.
In the intricate and ever-evolving healthcare landscape, the significance of managed IT solutions is paramount. These services transcend mere enhancements; they are vital components that empower CFOs to navigate the complex challenges posed by cybersecurity threats, regulatory compliance, and operational efficiency. By leveraging comprehensive managed IT services, healthcare organizations can concentrate on their core mission—delivering exceptional patient care—while ensuring robust protection against cyber risks and operational disruptions.
Key services such as:
are critical for maintaining the integrity of healthcare operations. The integration of these services not only safeguards sensitive patient data but also enhances overall organizational resilience. Furthermore, the case for Compliance as a Service (CaaS) and cyber financial risk impact analysis underscores the necessity for healthcare CFOs to adopt proactive strategies that mitigate financial repercussions and uphold regulatory standards.
As the healthcare sector faces increasing scrutiny and sophisticated cyber threats, embracing managed IT solutions is no longer optional; it is a strategic imperative. Organizations that prioritize these services will not only protect their assets but also cultivate a culture of compliance and security awareness, ultimately enhancing patient trust and institutional reputation. It is essential for healthcare leaders to take decisive action now—investing in managed IT services today will pave the way for a more secure and efficient tomorrow in healthcare delivery.
What services does Cyber Solutions Inc. provide for healthcare organizations?
Cyber Solutions Inc. offers a range of managed IT services tailored for medical facilities, including 24/7 help desk support, endpoint protection, threat detection, and managed security services.
Why is cybersecurity essential for healthcare organizations?
Cybersecurity is crucial for healthcare organizations due to the increasing threats from cybercriminals, the need to protect patient data, and the requirement to comply with industry regulations such as HIPAA.
How does 24/7 help desk support benefit medical entities?
24/7 help desk support ensures rapid resolution of IT issues, minimizing disruptions in patient care and administrative functions, which allows medical personnel to focus on their primary responsibilities and enhances operational resilience.
What impact does effective IT support have on patient care?
Organizations with effective IT support experience higher patient satisfaction rates due to the timely resolution of issues, which directly correlates with superior care experiences and can prevent revenue losses tied to downtime.
What is endpoint protection and why is it important?
Endpoint protection secures devices that connect to the network, such as computers and mobile devices, shielding them from malware and unauthorized access. It is vital in the medical sector to mitigate the risk of data breaches and ensure compliance with regulations like HIPAA.
What are the financial consequences of ransomware attacks in healthcare?
The average cost of a ransomware attack in healthcare is approximately $1.85 million per incident, highlighting the severe financial impact of inadequate endpoint security.
What strategies are recommended for effective endpoint protection?
Effective endpoint protection strategies include implementing fine-grained network segmentation, utilizing centralized management for security devices, adopting Zero Trust principles, and maintaining regular updates and employee awareness.
What challenges do healthcare organizations face in implementing endpoint protection?
The shortage of cybersecurity experts in the medical field complicates the implementation of effective endpoint protection strategies, increasing the risk of breaches and leading to significant operational downtime after incidents.