
The selection of appropriate Security-as-a-Service (SECaaS) providers is paramount in the healthcare sector, where safeguarding sensitive patient data and ensuring compliance with regulations such as HIPAA are non-negotiable.
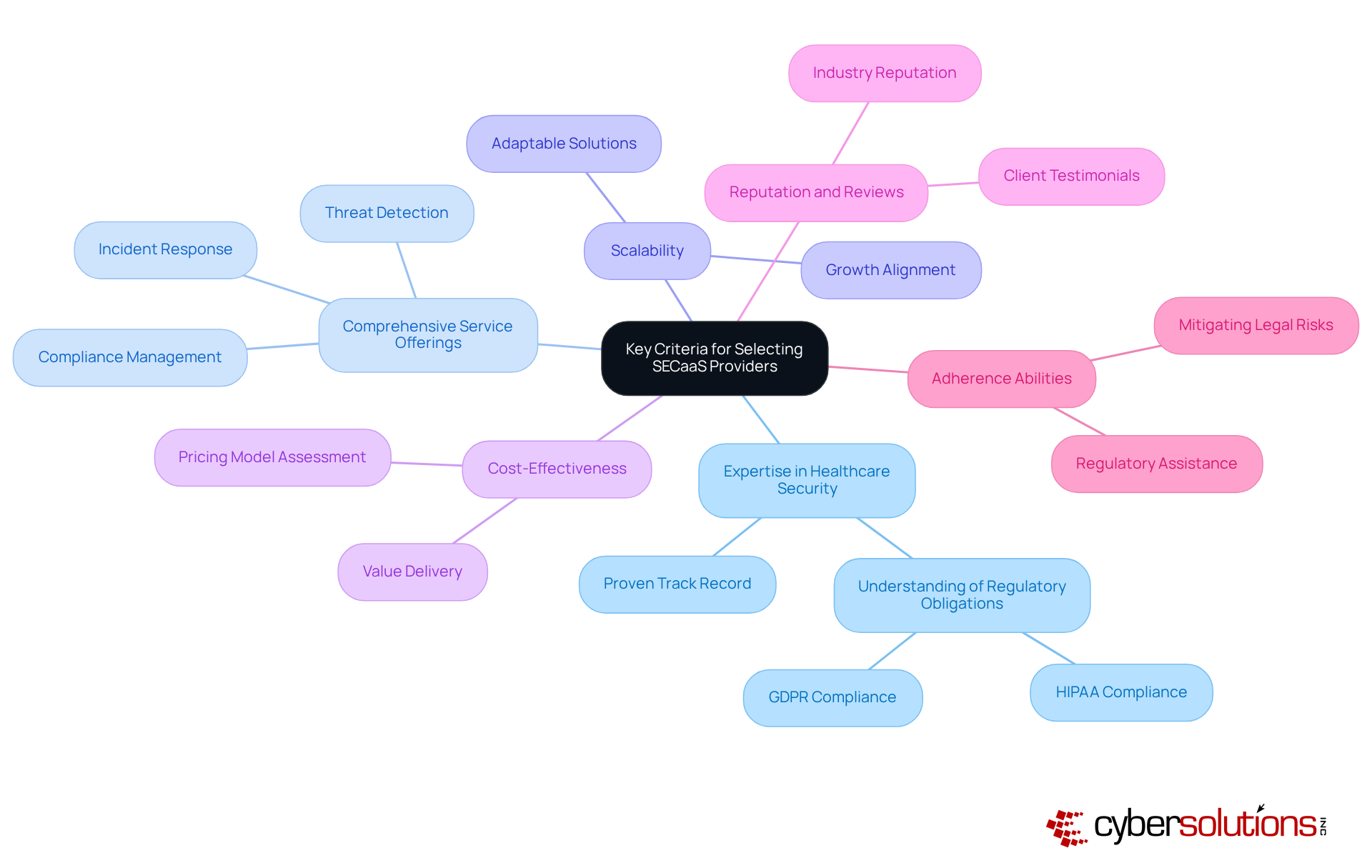
In a landscape rife with cybersecurity threats, healthcare organizations face unique challenges that demand vigilant attention. Evaluating SECaaS providers requires a thorough assessment of their expertise in healthcare security, the comprehensiveness of their service offerings, scalability, cost-effectiveness, and strict adherence to regulatory requirements.
These factors are not merely checkboxes; they are critical components that significantly influence the effectiveness of cybersecurity measures in an ever-evolving threat environment. As the stakes grow higher, the need for robust cybersecurity solutions becomes increasingly evident, prompting healthcare organizations to act decisively in their provider selection process.
In an era where healthcare organizations are increasingly targeted by cyberattacks, the necessity for robust cybersecurity measures has never been more pressing. Security-as-a-Service (SECaaS) provides a strategic solution, enabling these entities to outsource their security needs while leveraging advanced technologies and expert guidance.
However, with a multitude of providers available, how can healthcare organizations ensure they select the right partner to safeguard sensitive data and maintain compliance?
This article explores the essential criteria for choosing SECaaS providers, equipping healthcare leaders with the insights necessary to navigate this critical decision-making process.
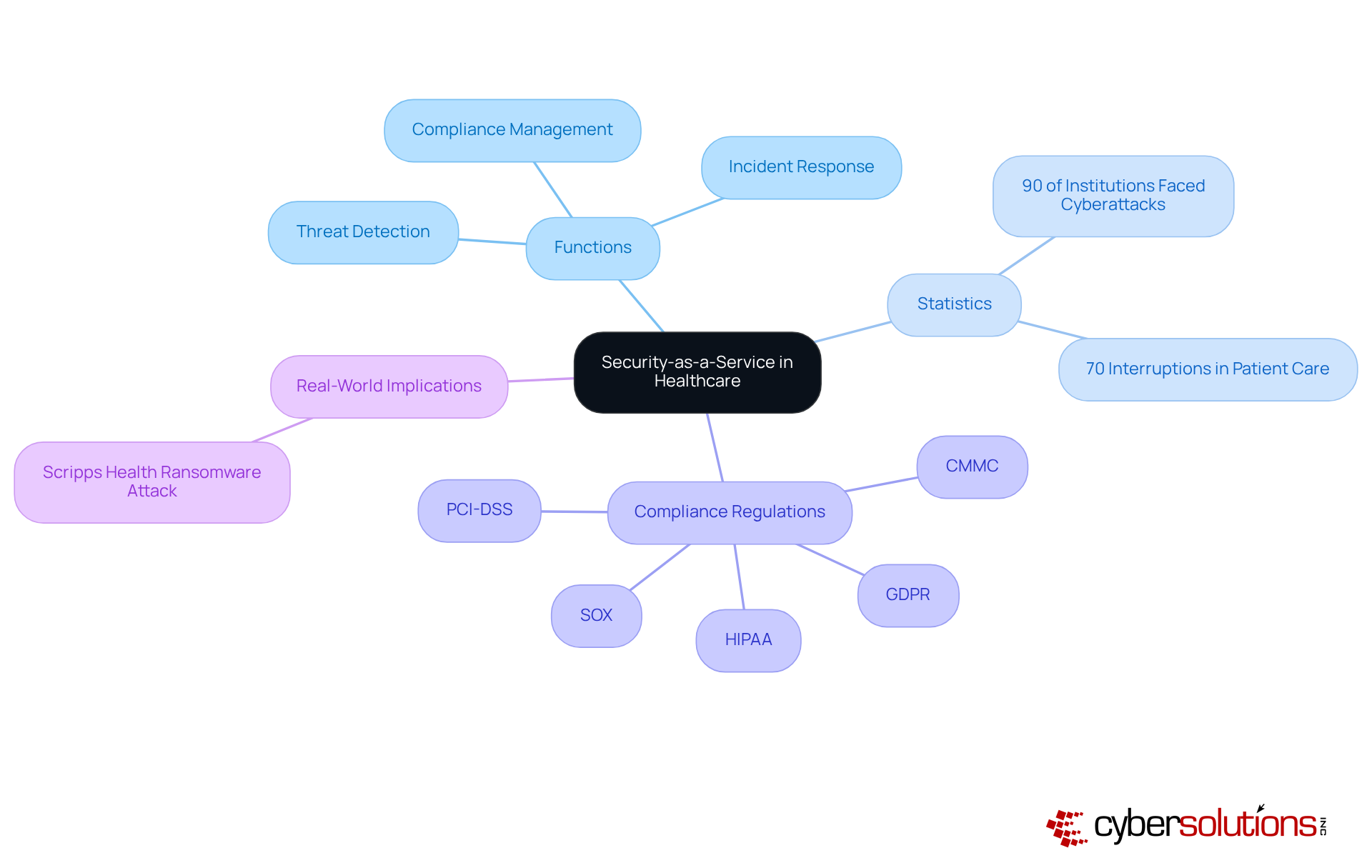
In today's digital age, cybersecurity is not just an option but a necessity for healthcare organizations. Security-as-a-Service (SECaaS) emerges as a vital cloud-based model, enabling healthcare entities to outsource their cybersecurity needs to security-as-a-service providers like Cyber Solutions. This comprehensive service encompasses critical protective functions, including:
These functions address the urgent need to safeguard sensitive patient data against escalating cyber threats.
The reality is stark: over 90% of healthcare institutions reported experiencing a cyberattack last year, with these incidents interrupting patient care in 70% of cases. By adopting security-as-a-service providers, healthcare organizations can utilize advanced protective technologies and expert knowledge, alleviating the burden of maintaining an in-house security team. This strategic move not only fortifies their security posture but also allows them to concentrate on core operations while ensuring compliance with essential regulations such as:
Recent trends indicate a growing reliance on security-as-a-service providers, driven by the increasing complexity of cyber threats and the pressing need for robust protective frameworks. Experts advocate for this model, underscoring its potential to enhance resilience and streamline operations, particularly as healthcare entities grapple with challenges like tech sprawl, where some depend on up to 76 different security tools, highlighting the need for security-as-a-service providers. The effectiveness of SECaaS is evident in real-world scenarios, such as the Scripps Health ransomware attack, which underscored the substantial operational disruptions caused by cyberattacks, leading to a 30% increase in recovery time.
With Cyber Solutions' , healthcare entities can swiftly identify, contain, and mitigate threats, ensuring business continuity. As the healthcare landscape continues to evolve, organizations striving to protect sensitive data and maintain operational efficiency will find the adoption of security-as-a-service providers crucial.
In today's digital landscape, selecting security-as-a-service providers is paramount for healthcare organizations seeking robust protection against cyber threats. The unique challenges faced by these organizations demand careful evaluation of several key criteria.
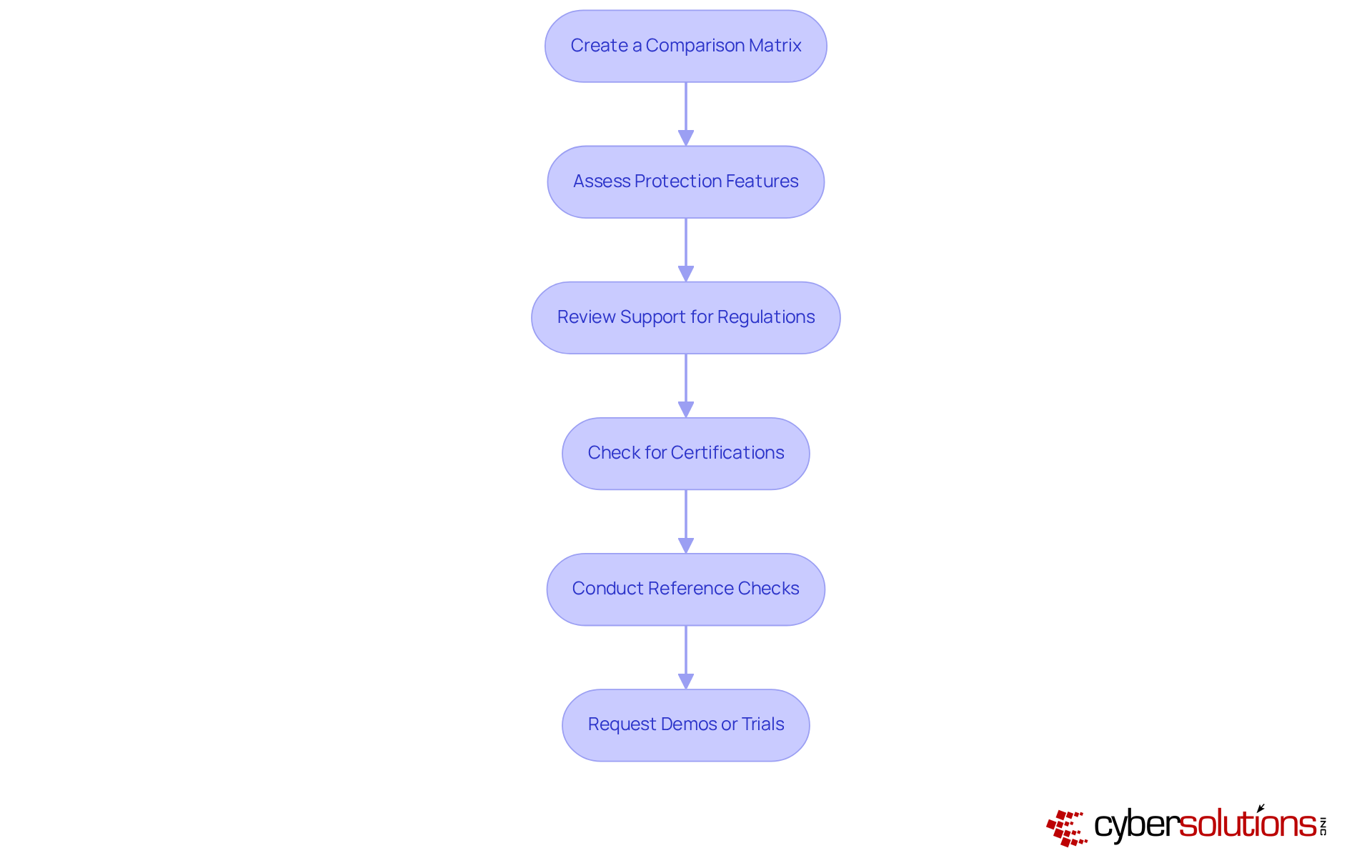
To effectively evaluate and compare , healthcare organizations must undertake essential steps to safeguard their operations against increasing cyber threats.
In today's rapidly evolving landscape of cybersecurity threats, it is paramount for healthcare organizations to fortify their defenses and ensure compliance. To achieve continuous support and adaptability, organizations should implement the following strategic steps:
By adopting these strategies, healthcare organizations not only meet regulatory requirements but also establish a robust security posture that adapts to the dynamic landscape of cybersecurity threats.

In the evolving landscape of healthcare, the criticality of selecting the right security-as-a-service (SECaaS) provider is paramount. This strategic decision not only fortifies the security posture of healthcare organizations but also safeguards sensitive patient data against an ever-growing array of cyber threats. By outsourcing cybersecurity needs to specialized providers, healthcare entities can concentrate on their core missions while harnessing advanced technologies and expert knowledge.
The article underscores several essential factors to consider when choosing SECaaS providers, including:
Furthermore, effective evaluation methods—such as creating comparison matrices, assessing protection features, and conducting reference checks—are crucial for making informed decisions. Continuous support and adaptability in compliance are vital, as they enable organizations to stay aligned with evolving regulations and bolster overall resilience against cyber threats.
Ultimately, the proactive adoption of security-as-a-service solutions is indispensable for healthcare organizations striving to protect sensitive information and maintain operational efficiency. By prioritizing these considerations and nurturing a culture of security awareness, healthcare entities can not only mitigate risks but also position themselves as leaders in the battle against cybercrime. Embracing SECaaS transcends mere choice; it is a necessary step toward ensuring the safety and integrity of healthcare services in an increasingly digital world.
What is Security-as-a-Service (SECaaS) in healthcare?
Security-as-a-Service (SECaaS) is a cloud-based model that allows healthcare organizations to outsource their cybersecurity needs to specialized providers, enabling them to focus on core operations while ensuring the protection of sensitive patient data.
What critical functions does SECaaS provide?
SECaaS encompasses several critical protective functions, including threat detection, incident response, and compliance management.
Why is SECaaS important for healthcare organizations?
SECaaS is important because over 90% of healthcare institutions reported experiencing cyberattacks, which can disrupt patient care. By utilizing SECaaS, organizations can enhance their security posture and ensure compliance with essential regulations.
What regulations must healthcare organizations comply with when using SECaaS?
Healthcare organizations must comply with regulations such as HIPAA, GDPR, PCI-DSS, CMMC, and SOX when utilizing SECaaS.
What trends are driving the adoption of SECaaS in healthcare?
The increasing complexity of cyber threats and the need for robust protective frameworks are driving the growing reliance on SECaaS providers in healthcare.
How does SECaaS help with operational efficiency?
SECaaS helps streamline operations by alleviating the burden of maintaining an in-house security team and allowing healthcare organizations to focus on their primary functions.
Can you provide an example of the effectiveness of SECaaS?
The Scripps Health ransomware attack is an example where the operational disruptions caused by a cyberattack highlighted the need for SECaaS, leading to a significant increase in recovery time.
What services do providers like Cyber Solutions offer to healthcare entities?
Providers like Cyber Solutions offer incident response services that help healthcare entities swiftly identify, contain, and mitigate threats to ensure business continuity.