
In today's rapidly evolving digital landscape, the significance of AI data security compliance cannot be overstated, particularly for CFOs. Understanding the fundamentals of AI data security is essential, as it lays the groundwork for navigating complex compliance requirements.
Effective risk management strategies must be implemented to safeguard organizational assets, while continuous monitoring and assessment practices are vital for adapting to emerging threats. These best practices are not merely recommendations; they are critical for mitigating risks, ensuring regulatory adherence, and enhancing organizational resilience against cyber threats.
Successful implementation examples across various sectors illustrate the tangible benefits of these strategies, prompting CFOs to take decisive action in fortifying their organizations against potential vulnerabilities.
As artificial intelligence continues to reshape the healthcare landscape, the imperative for robust data security practices becomes increasingly critical. Chief Financial Officers (CFOs) are at the forefront of navigating the complexities of AI data security compliance, ensuring that their organizations not only protect sensitive information but also meet stringent regulatory requirements. With evolving threats and compliance mandates, the question arises: how can CFOs effectively safeguard their organizations while optimizing resource allocation? This article explores four essential best practices that empower CFOs to enhance AI data security compliance and fortify their organizations against emerging risks.
Cybersecurity in healthcare is not just a necessity; it is a critical imperative. As AI systems increasingly handle sensitive information, the importance of robust AI data security practices cannot be overstated. CFOs must prioritize a comprehensive understanding of AI data security, particularly regarding how AI systems manage data, including the types of information they gather, process, and store. This knowledge is essential for identifying vulnerabilities and implementing effective protective measures. For example, employing encryption methods safeguards information integrity and confidentiality while significantly reducing the risk of breaches—a pressing concern in the healthcare sector. Moreover, access controls enhance security by ensuring that only authorized personnel can access sensitive information.
Additionally, application allowlisting is pivotal in fortifying cybersecurity defenses. By permitting only pre-approved applications to execute, organizations can proactively thwart malware, ransomware, and unauthorized software from infiltrating their systems. This strategy not only minimizes the attack surface but also aids healthcare organizations in meeting stringent , such as HIPAA, PCI-DSS, and GDPR, thereby protecting sensitive patient information.
Consider a significant case: a healthcare organization that implemented robust information encryption, stringent access controls, and application allowlisting experienced a marked reduction in breaches. This outcome underscores the effectiveness of these essential practices in safeguarding sensitive information and highlights the necessity of proactive measures in enhancing an organization's overall safety posture. Furthermore, ongoing evaluations of information protection risks are vital for adapting to evolving threats and maintaining data integrity. By familiarizing themselves with these core principles, finance leaders can make informed decisions regarding resource allocation for cybersecurity initiatives, ultimately fortifying their organization's defenses against emerging threats.

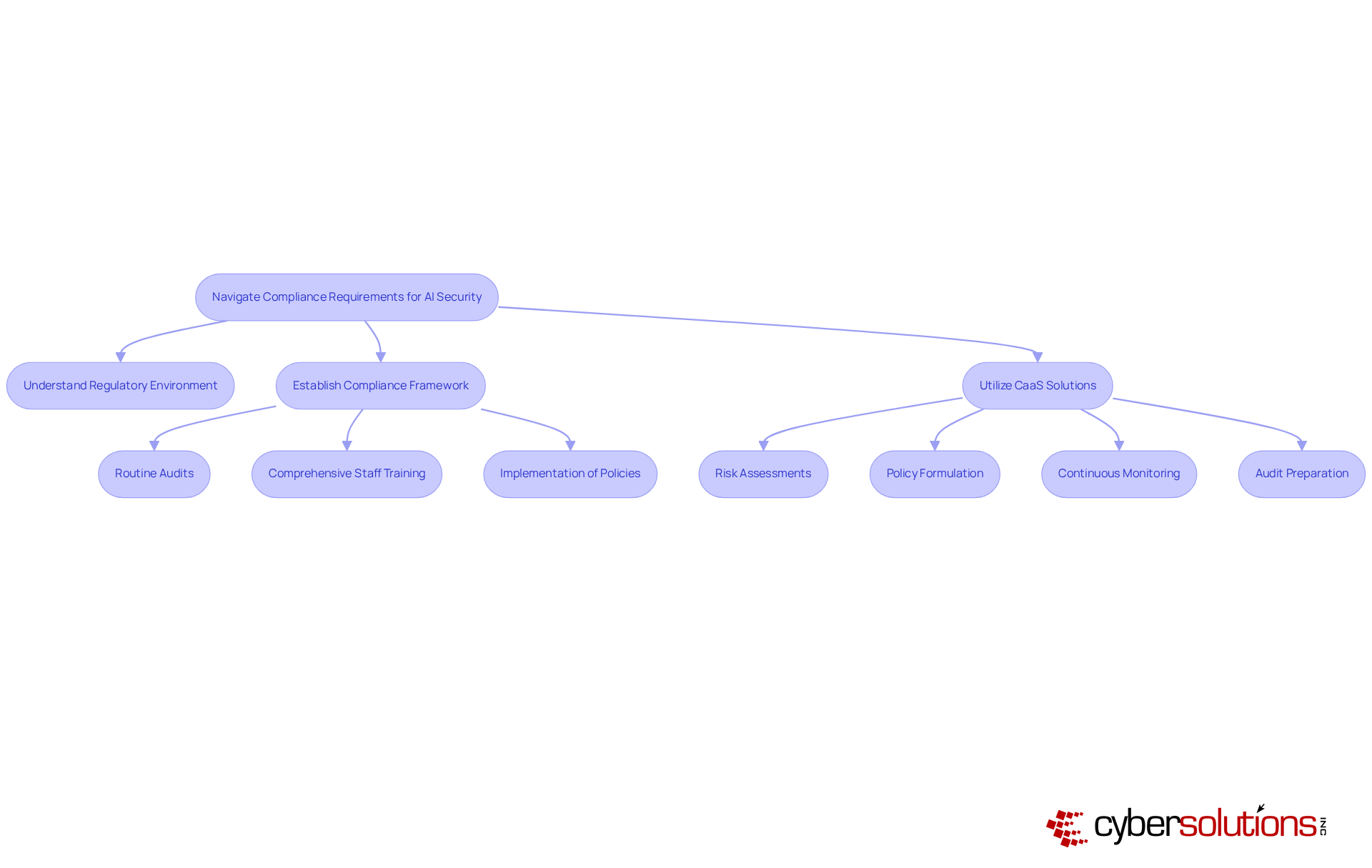
Chief financial officers must possess a deep understanding of the regulatory environment surrounding AI data security, which includes critical laws such as GDPR, HIPAA, and PCI-DSS. This knowledge is essential for mitigating risks associated with non-compliance, as violations can result in substantial fines and significant reputational damage. To ensure adherence, CFOs should establish a robust framework that integrates:
To navigate these complex requirements effectively, CFOs can utilize Compliance as a Service (CaaS) solutions, which offer comprehensive support for fulfilling regulatory obligations. CaaS streamlines the regulatory process by providing:
This proactive approach guarantees that organizations remain compliant with current regulations. Moreover, leveraging AI data security tools that automate oversight monitoring and reporting can help identify potential compliance gaps. For example, a financial organization that adopted AI-driven regulatory monitoring reported a remarkable 30% reduction in adherence-related incidents, highlighting the benefits of proactive regulatory management. Additionally, CaaS solutions deliver expert guidance for audits, simplifying the process for financial executives and ensuring successful audits while maintaining compliance in highly regulated environments.
CFOs must establish a robust risk management framework that systematically identifies, evaluates, and mitigates risks associated with AI data security. In today’s landscape, frequent risk evaluations are vital for assessing the effectiveness of existing protective measures and uncovering potential weaknesses. Strategies such as adopting multi-factor authentication significantly decrease the likelihood of unauthorized access, while conducting penetration testing proactively identifies system vulnerabilities. Additionally, creating strong [incident response plans](https://discovercybersolutions.com/cybersecurity-services/managed-security-service-provider) is essential for ensuring swift recovery from any breaches.
Moreover, fostering a culture of safety awareness within organizations is crucial. Continuous training and resources for employees can markedly enhance the organization's defense posture. For example, a manufacturing firm that implemented a rigorous risk management strategy, including regular training sessions, experienced a 40% reduction in safety incidents. This underscores the necessity of in safeguarding sensitive data and highlights the pivotal role financial leaders play in ensuring organizational resilience against evolving threats, especially concerning AI data security.

Ongoing monitoring and evaluation methods are crucial for ensuring the safety and AI data security of AI systems. CFOs must prioritize the deployment of automated monitoring tools that deliver real-time insights into system performance and vulnerabilities. These tools play a vital role in , unauthorized access attempts, and potential information breaches in the context of AI data security before they escalate into significant threats.
Regular evaluations are equally important to assess the effectiveness of protective measures and compliance with regulatory requirements for AI data security. For example, a government agency that implemented continuous monitoring reported an impressive 50% reduction in response times to security incidents, highlighting the value of proactive monitoring in safeguarding sensitive data. By cultivating a culture of continuous improvement, CFOs can bolster their organizations' resilience against the ever-evolving landscape of cyber threats.

The landscape of AI data security compliance poses a significant challenge for CFOs, who are pivotal in safeguarding sensitive information within their organizations. A comprehensive understanding of AI data security fundamentals, navigating complex compliance requirements, implementing effective risk management strategies, and establishing continuous monitoring practices are essential steps for financial leaders. These best practices not only bolster the organization’s defense against cyber threats but also ensure adherence to stringent regulations, ultimately protecting both the organization and its stakeholders.
Key arguments throughout the discussion underscore the necessity of robust cybersecurity measures such as:
Furthermore, understanding regulatory frameworks like GDPR, HIPAA, and PCI-DSS is crucial, alongside the advantages of utilizing Compliance as a Service (CaaS) solutions. The article emphasizes proactive risk management and continuous monitoring as vital for identifying vulnerabilities and ensuring swift incident responses.
In an era where cyber threats are continuously evolving, the responsibility of CFOs extends beyond financial oversight to encompass the strategic safeguarding of data. By adopting these best practices, CFOs can mitigate risks and foster a culture of security awareness within their organizations. This proactive approach is essential for maintaining compliance and protecting sensitive data, ultimately reinforcing the organization's resilience against emerging challenges in AI data security.
Why is AI data security important in healthcare?
AI data security is critical in healthcare because AI systems handle sensitive information, and robust security practices are necessary to protect this data from breaches and vulnerabilities.
What should CFOs prioritize regarding AI data security?
CFOs should prioritize a comprehensive understanding of how AI systems manage data, including the types of information they gather, process, and store, to identify vulnerabilities and implement protective measures.
What role does encryption play in AI data security?
Encryption safeguards information integrity and confidentiality, significantly reducing the risk of breaches, which is a pressing concern in the healthcare sector.
How do access controls enhance data security?
Access controls ensure that only authorized personnel can access sensitive information, thereby enhancing security and protecting against unauthorized access.
What is application allowlisting, and why is it important?
Application allowlisting is a security strategy that permits only pre-approved applications to execute, helping to thwart malware, ransomware, and unauthorized software, thus minimizing the attack surface.
How does application allowlisting assist in compliance?
By implementing application allowlisting, healthcare organizations can better meet compliance mandates such as HIPAA, PCI-DSS, and GDPR, which protect sensitive patient information.
Can you provide an example of successful AI data security implementation?
A healthcare organization that implemented robust information encryption, stringent access controls, and application allowlisting experienced a marked reduction in breaches, demonstrating the effectiveness of these practices.
Why are ongoing evaluations of information protection risks vital?
Ongoing evaluations are essential for adapting to evolving threats and maintaining data integrity, ensuring that organizations can respond effectively to new security challenges.
How can finance leaders use their understanding of AI data security?
By familiarizing themselves with core principles of AI data security, finance leaders can make informed decisions regarding resource allocation for cybersecurity initiatives, strengthening their organization's defenses against emerging threats.