
Selecting the right managed cybersecurity services provider is crucial for CFOs aiming to safeguard sensitive financial information and ensure adherence to industry regulations. In today's landscape, where cybersecurity threats are increasingly prevalent, the stakes are higher than ever.
By choosing a provider that demonstrates:
CFOs can significantly reduce the financial risks associated with cyber threats. Statistics reveal that organizations employing such providers experience fewer incidents and improved incident response times, underscoring the importance of this decision.
Therefore, it is essential for CFOs to prioritize these factors when evaluating potential partners in cybersecurity.
In an era where cyber threats are increasingly sophisticated and prevalent, the role of managed cybersecurity services has never been more critical for organizations, particularly from a financial standpoint. CFOs are at the forefront of safeguarding sensitive data and ensuring compliance while navigating the complex landscape of digital security.
This article explores the essential criteria for selecting the right managed cybersecurity services provider, highlighting the significant benefits these services offer in mitigating risks and enhancing operational resilience.
As organizations confront the daunting challenge of protecting their financial integrity, the pressing question remains: how can CFOs effectively choose a provider that not only meets compliance standards but also fortifies their defenses against ever-evolving cyber threats?
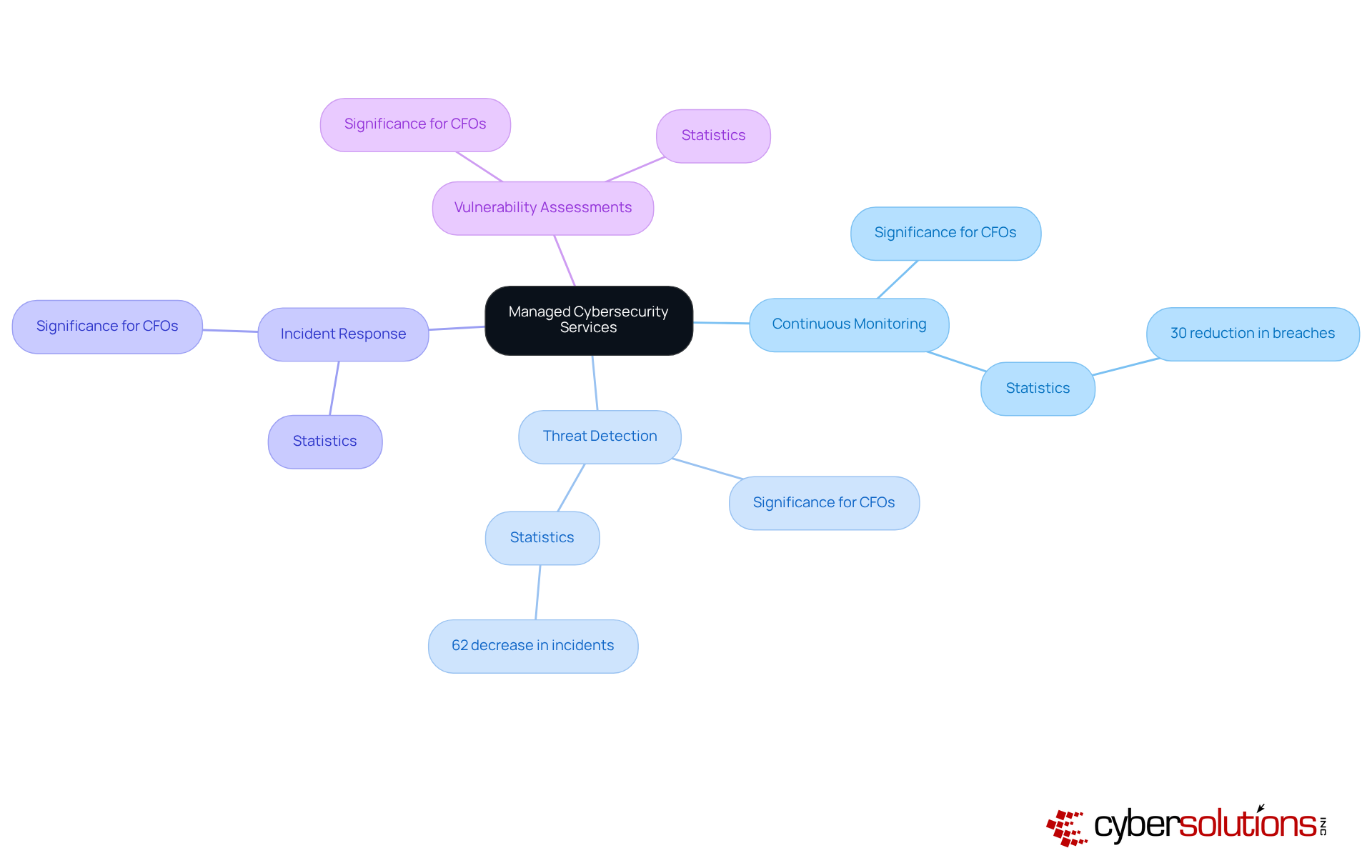
A managed cybersecurity services provider offers a comprehensive suite of solutions meticulously crafted to shield organizations from the ever-evolving landscape of cyber threats, all while ensuring compliance with industry standards. These offerings typically encompass:
For CFOs, the significance of these services cannot be overstated; they are crucial in safeguarding sensitive financial information and maintaining the company's reputation and operational integrity.
Investing in managed security services not only mitigates the risk of costly data breaches—where the average financial impact can reach approximately $5.9 million within the finance sector—but also helps avoid regulatory penalties that can average $14.82 million annually for non-compliance. This proactive approach fosters a more stable financial outlook, empowering organizations to allocate resources more strategically. By aligning digital security investments with overarching business objectives and risk management strategies, CFOs can bolster their firm's resilience against cyber threats while enhancing operational efficiency.
Real-world examples underscore the effectiveness of these offerings: organizations engaging in managed digital security and conducting regular assessments experience a remarkable 30% reduction in successful breaches. Furthermore, those implementing Managed Detection and Response (MDR) solutions report a 62% decrease in security incidents and a 50% reduction in the time required to identify and respond to threats. It is also noteworthy that 68% of data breaches stem from human error, highlighting the critical need for ongoing monitoring and training. Such statistics emphasize the importance of selecting the right managed cybersecurity services provider, as this choice directly influences the protection of vital financial data and the overall security posture of the organization.
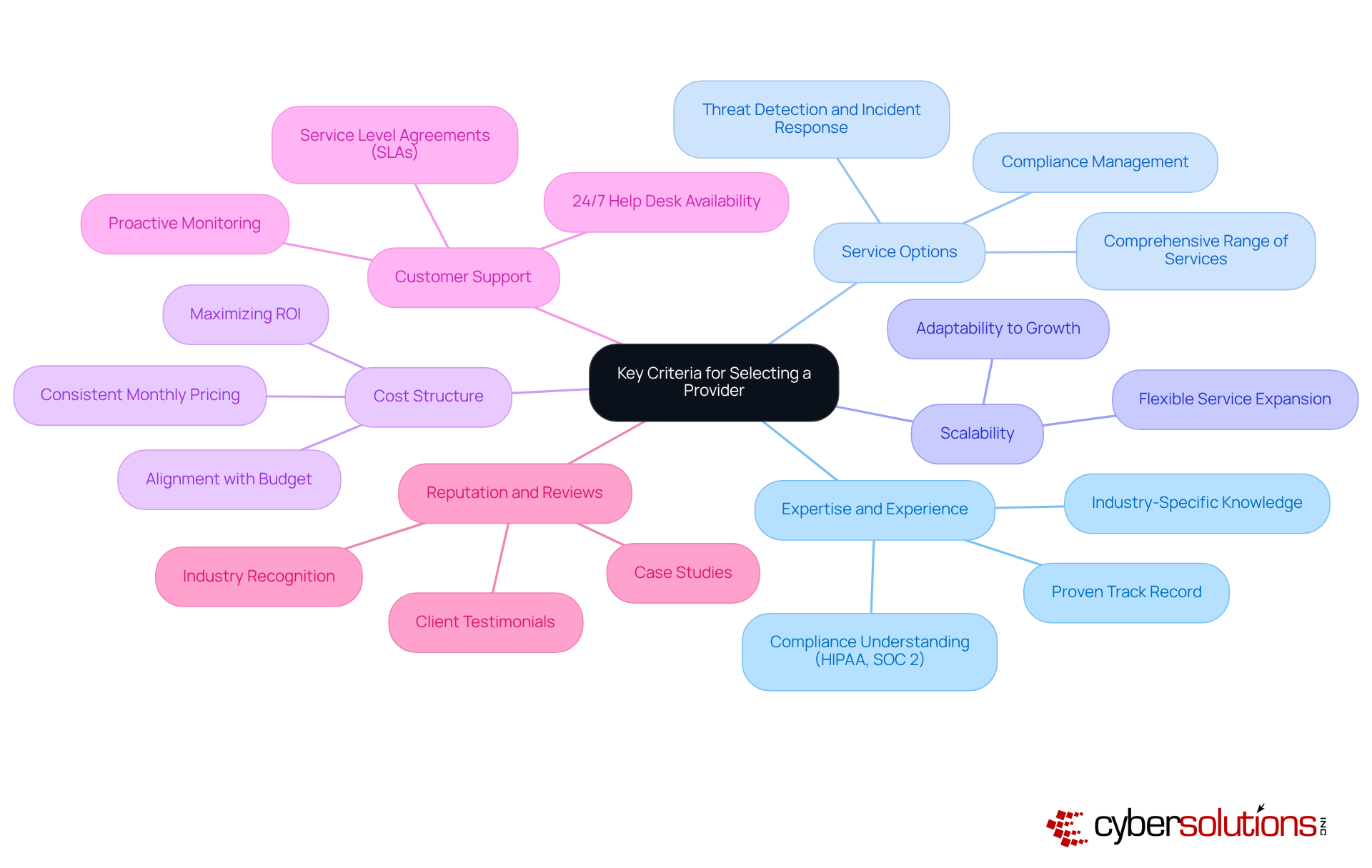
In today's rapidly evolving digital landscape, the importance of robust cybersecurity measures in healthcare cannot be overstated. CFOs must navigate a myriad of challenges, from compliance with regulations to the ever-present threat of cyberattacks. When selecting a managed cybersecurity services provider, several key criteria should be prioritized in the decision-making process.
Expertise and Experience: It is essential to prioritize providers with a proven track record in your industry, particularly those well-versed in compliance requirements such as HIPAA or SOC 2. This expertise is not just beneficial; it is crucial, as nearly 95% of cyberattacks are financially motivated. Industry-specific knowledge is vital for effective defense. Cyber Solutions offers customized IT solutions tailored to meet the distinct security and compliance needs of healthcare entities, ensuring that your provider understands the unique challenges you face.
Service Options: Ensure that the provider offers a comprehensive range of services, including threat detection, incident response, and compliance management. This holistic approach is vital, as entities utilizing Managed Detection and Response (MDR) solutions report a 62% reduction in security incidents. Cyber Solutions enhances its offerings with features such as 24/7 SOC monitoring and proactive threat response, which are essential for maintaining a strong security posture.
Scalability: It is important to select a provider capable of expanding their services as your organization grows. This flexibility ensures that security measures evolve alongside your business, which is a necessity as the global managed cybersecurity services provider market is projected to grow at a 15.4% CAGR until 2030. Cyber Solutions is designed to support small to medium enterprises, simplifying the process of adapting your security strategy as your needs change.
Cost Structure: Evaluate the pricing model to ensure alignment with your budget. Look for consistent monthly pricing that aids in effective budget planning, especially in light of the average cost of a data breach, which reached $4.45 million in 2023. Additionally, the average total cost of an insider threat event increased from $15.4 million in 2022 to $16.2 million in 2023, underscoring the financial ramifications of digital security. Cyber Solutions provides tailored pricing structures that help maximize ROI while ensuring comprehensive protection.
Customer Support: Assess the level of support provided, including 24/7 help desk availability and proactive monitoring. These components are critical for minimizing downtime and ensuring rapid incident response, which can significantly affect operational efficiency. Reviewing Service Level Agreements (SLAs) that outline success metrics, including response times and uptime benchmarks, is also essential. Cyber Solutions places a strong emphasis on customer support, ensuring that you have the assistance you need at all times.
Reputation and Reviews: Conduct thorough research on client testimonials and case studies to evaluate the provider's effectiveness and reliability. A strong reputation in the industry often correlates with high-quality service, as evidenced by organizations that have successfully navigated security challenges with the right partners. Checking references and reading reviews from recent customers is crucial for gauging the provider's dependability. Cyber Solutions boasts a proven history of delivering customized security solutions that enhance compliance and safety for healthcare entities.
By applying these criteria, CFOs can make informed decisions that not only bolster their organization's security posture but also ensure that their investments yield tangible returns.
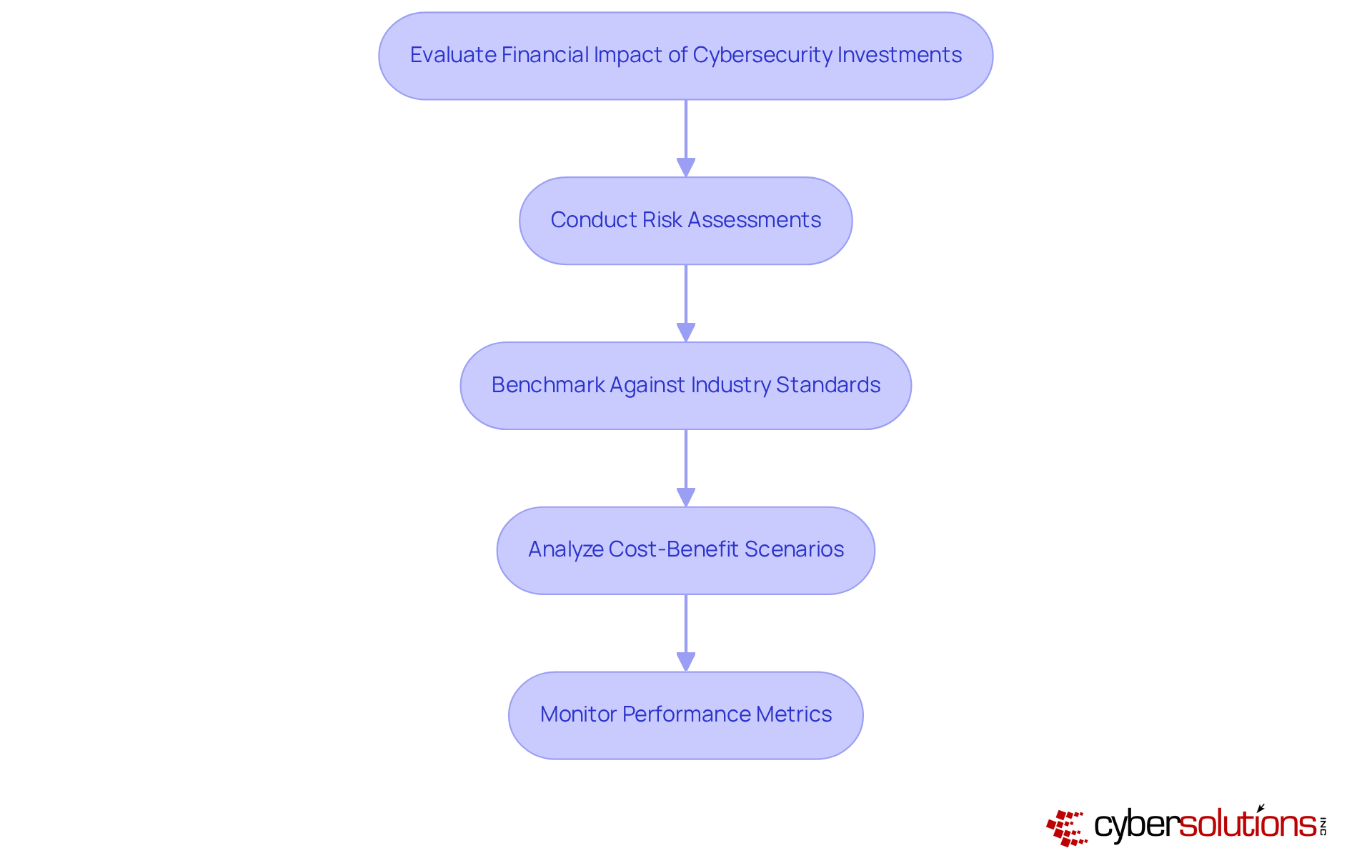
CFOs must evaluate the financial implications of security investments by considering both direct and indirect costs. Direct costs include the expenses related to acquiring security solutions and services, while indirect costs may encompass potential losses from data breaches, regulatory penalties, and reputational damage. To effectively measure ROI, CFOs should:
Conduct Risk Assessments: Regularly evaluate the organization's risk exposure to grasp the potential financial impact of cyber threats.
Benchmark Against Industry Standards: Compare security spending with industry benchmarks to ensure that investments remain competitive and effective.
Analyze Cost-Benefit Scenarios: Develop scenarios that illustrate the possible expenses of a data breach in comparison to the costs associated with implementing robust security measures. With Cyber Solutions' flat-rate pricing model, organizations can streamline budgeting and improve operational efficiency by eliminating unforeseen IT expenses, thereby ensuring predictable monthly costs that positively impact overall economic health.
Monitor Performance Metrics: Track key performance indicators (KPIs) related to security effectiveness, such as incident response times and the number of breaches prevented, to showcase value. The significance of rapid incident response strategies is paramount; having an incident response team available within 24 hours can substantially mitigate damage and enable a quicker recovery, as evidenced by case studies demonstrating reduced downtime and lower recovery costs.
By systematically evaluating the financial impact of security investments, CFOs can make informed decisions that align with their organization's financial health and strategic objectives.
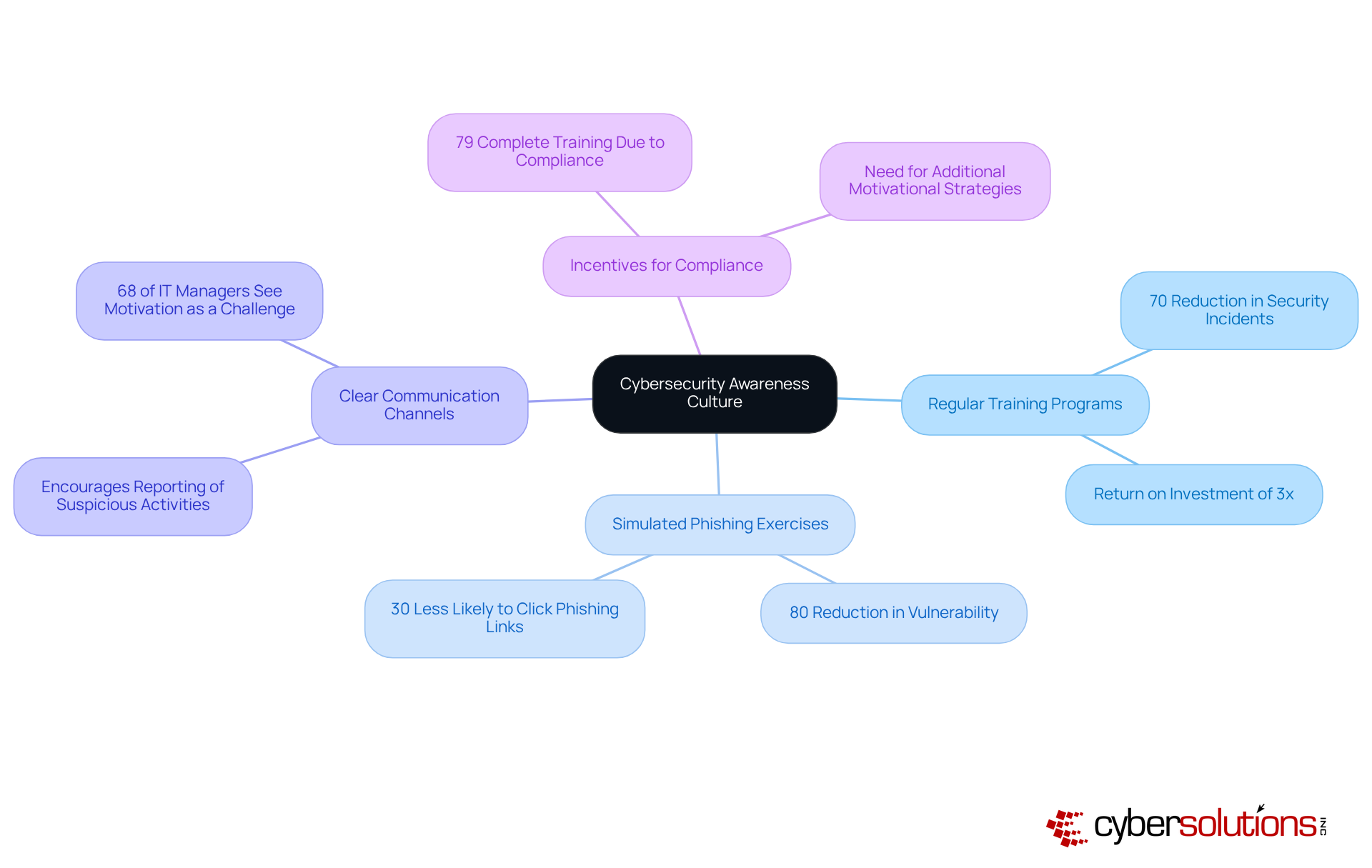
To effectively mitigate security risks, CFOs must prioritize the cultivation of a culture of awareness among employees. This can be achieved through:
Regular Training Programs: Implement ongoing training sessions that educate employees about the latest cyber threats and best practices for safeguarding sensitive information. Regular training enhances staff capability to identify potential cyber threats, leading to a 70% reduction in security incidents. Organizations can anticipate a return of over three times their investment in security awareness training, making it a financially prudent initiative.
Simulated Phishing Exercises: Conduct regular phishing simulations to test employees' awareness and response to potential threats. These exercises have demonstrated effectiveness, with entities reporting an 80% reduction in staff vulnerability to phishing attacks due to such training. Additionally, trained users are 30% less likely to click on a phishing link, further underscoring the effectiveness of these exercises in enhancing employee awareness.
Clear Communication Channels: Establish clear channels for reporting suspicious activities or potential security incidents. Encouraging employees to actively report concerns fosters a proactive security culture, where vigilance is part of daily operations. This is particularly important as 68% of IT managers see employee motivation as the biggest challenge in implementing security protocols.
Incentives for Compliance: Consider implementing incentive programs that reward employees for following security protocols and participating in training initiatives. Such programs can encourage employees to engage more deeply with security practices, emphasizing their significance in safeguarding the company. Notably, 79% of staff complete security training mainly due to required adherence, highlighting the necessity for companies to explore further motivational approaches beyond compliance.
By fostering a culture of cybersecurity awareness, organizations can significantly reduce the likelihood of breaches caused by human error, ultimately protecting their financial assets and reputation.
Selecting the right managed cybersecurity services provider is not merely important; it is essential for CFOs who seek to shield their organizations from the escalating threat of cyberattacks. Understanding the significance of these services enables CFOs to make informed decisions that not only protect sensitive financial information but also bolster overall operational integrity.
Key criteria for choosing a provider include:
The financial implications of investing in cybersecurity are profound; proactive measures can yield substantial cost savings and a strengthened security posture. Additionally, cultivating a culture of cybersecurity awareness among employees is vital, as human error remains a leading cause of breaches.
As the landscape of cyber threats continues to evolve, prioritizing managed cybersecurity services transcends strategic decision-making—it is a necessity. CFOs are urged to adopt a proactive approach in assessing their cybersecurity investments, ensuring alignment with organizational goals while fostering a secure environment for all stakeholders. By doing so, organizations can navigate the complexities of the digital age with confidence and resilience.
What are managed cybersecurity services?
Managed cybersecurity services are comprehensive solutions provided by a managed cybersecurity services provider to protect organizations from cyber threats while ensuring compliance with industry standards. These services typically include continuous monitoring, threat detection, incident response, and vulnerability assessments.
Why are managed cybersecurity services important for CFOs?
For CFOs, managed cybersecurity services are crucial for safeguarding sensitive financial information, maintaining the company's reputation, and ensuring operational integrity. They help mitigate the risk of costly data breaches and avoid regulatory penalties.
What is the financial impact of data breaches in the finance sector?
The average financial impact of data breaches in the finance sector can reach approximately $5.9 million.
What are the potential costs of non-compliance with cybersecurity regulations?
Non-compliance with cybersecurity regulations can lead to average penalties of about $14.82 million annually.
How do managed cybersecurity services affect an organization's financial outlook?
Investing in managed cybersecurity services fosters a more stable financial outlook by allowing organizations to allocate resources more strategically and align digital security investments with business objectives and risk management strategies.
What real-world benefits do organizations experience by using managed cybersecurity services?
Organizations that engage in managed digital security and conduct regular assessments experience a 30% reduction in successful breaches. Additionally, those implementing Managed Detection and Response (MDR) solutions report a 62% decrease in security incidents and a 50% reduction in the time required to identify and respond to threats.
What percentage of data breaches are caused by human error?
Approximately 68% of data breaches stem from human error, highlighting the need for ongoing monitoring and training.
How does the choice of a managed cybersecurity services provider impact an organization?
The choice of a managed cybersecurity services provider directly influences the protection of vital financial data and the overall security posture of the organization, making it critical to select the right provider.