
In today's rapidly evolving digital landscape, the stakes for C-suite leaders have never been higher. Ransomware attacks are not just common; they are becoming increasingly sophisticated. This reality makes it essential for executives to weave robust prevention strategies into their business frameworks.
As organizations confront the harsh truth of cyber extortion, the implications are profound. Are leaders truly prepared to defend their enterprises against the looming threat of ransomware? This article delves into essential best practices that can significantly bolster an organization's resilience against these cyber threats. It highlights the critical role of proactive measures and strategic alignment in safeguarding against potential attacks.
In a world where the cost of inaction can be devastating, understanding and addressing these challenges is imperative. Cyber Solutions can provide the necessary tools and strategies to navigate this complex landscape effectively.
To effectively combat ransomware threats, C-suite leaders must embed best practices to prevent ransomware within their overarching business strategy. This is not just a technical issue; it’s a critical component of operational resilience. By treating cybersecurity as a core element rather than a mere compliance requirement, organizations can significantly enhance their security posture.
Consider this: 97% of entities with encrypted data managed to recover it through various means. This statistic underscores the effectiveness of proactive measures. However, the financial impact is stark - 60% of ransomware victims reported revenue loss due to attacks. This highlights the necessity of integrating cybersecurity into business strategy, particularly for healthcare organizations, by adopting best practices to prevent ransomware to address their unique challenges.
Regular risk assessments are essential for identifying vulnerabilities and ensuring the implementation of best practices to prevent ransomware effectively. As companies increasingly acknowledge that 66% of them experienced cyber extortion attacks in the past year, the need for a strategic alignment becomes clear. This alignment not only strengthens defenses but also cultivates a culture of accountability and awareness among employees, empowering them to actively participate in the organization's defense against ransomware.
The experience of a healthcare provider illustrates the vital significance of prompt action and specialized knowledge in addressing cyber attack incidents. With Cyber Solutions' rapid response capabilities, including managed IT services and 24/7 threat monitoring, organizations can effectively contain threats and enhance their security measures. This ensures continuity of operations and compliance, safeguarding critical assets and ensuring long-term success.

C-suite leaders must recognize the critical importance of cybersecurity in healthcare, as misunderstandings about cyberattack prevention can severely hinder effective decision-making. A prevalent misconception is that traditional antivirus software suffices for defending against malicious software. However, as cyber threats evolve, relying solely on these solutions is no longer adequate. Research indicates that conventional antivirus programs often fail to detect many modern forms of malicious software, exposing organizations to significant vulnerabilities.
Moreover, there's a common belief that only large companies are at risk. In reality, small and medium-sized enterprises are equally susceptible, with a staggering 88% of small business incidents involving malicious software. This highlights the urgent need for C-suite leaders to adopt a proactive stance against these threats. One effective strategy is implementing application allowlisting, which prevents unauthorized software from executing, thereby reducing the attack surface and minimizing vulnerabilities.
This approach not only helps in thwarting malicious software attacks but also ensures compliance with regulations such as HIPAA, PCI-DSS, and GDPR. By dispelling these myths, leaders can appreciate the necessity of a comprehensive security strategy. This strategy should encompass:
All of which are best practices to prevent ransomware.
In conclusion, a multi-faceted approach is essential for effectively combating the ever-evolving landscape of extortion software threats. Are you prepared to fortify your organization against these challenges?

In today’s digital landscape, the importance of cybersecurity in healthcare cannot be overstated. C-suite leaders must understand the stages of a cyber attack, which typically unfold as:
In the initial infection phase, attackers often exploit vulnerabilities through phishing emails or malicious downloads. Alarmingly, 82.6% of phishing emails in 2025 are expected to contain AI-generated content, making vigilance essential.
Once attackers gain access, they navigate laterally within the network to reach critical data before encrypting it and demanding a ransom. This progression highlights the urgent need for targeted defenses. Implementing employee training programs empowers staff to recognize phishing attempts, while network segmentation can effectively limit lateral movement, containing potential breaches. Regular backups are crucial; organizations that had data encrypted were able to recover it in 97% of cases through backups or decryption tools, ensuring they do not succumb to ransom demands.
By comprehending these stages and implementing best practices to prevent ransomware, leaders can significantly enhance their organization's resilience against cyber threats. The time to act is now-strengthening cybersecurity measures is not just a necessity but a strategic imperative for healthcare organizations.

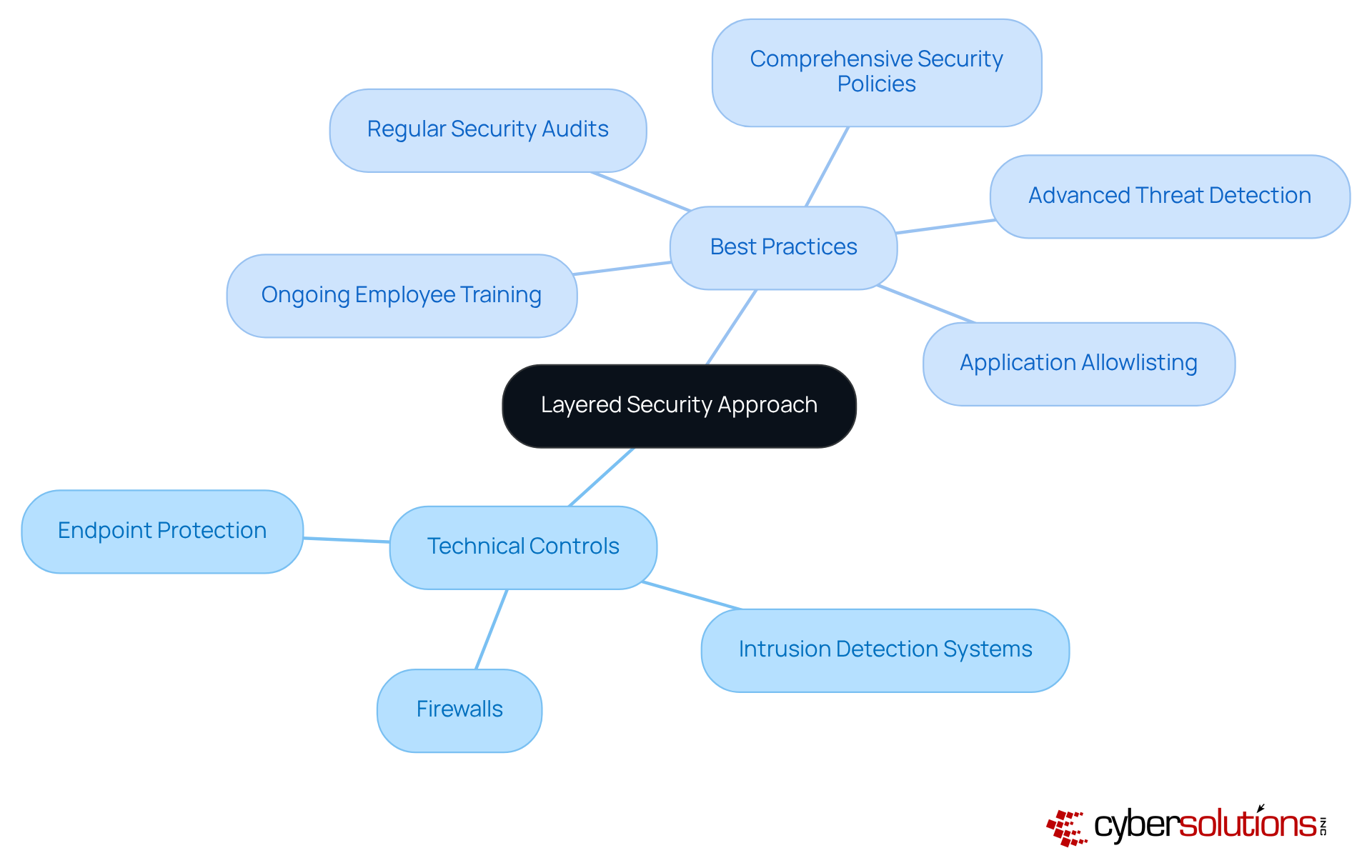
In today’s healthcare landscape, adopting best practices to prevent ransomware is not just important; it’s essential for safeguarding against malicious software incursions. C-suite leaders, particularly CFOs, face unique challenges in this arena. They must implement a blend of technical controls, such as:
Along with best practices to prevent ransomware, including:
One critical element of this strategy is application allowlisting. By actively preventing unauthorized software from running, organizations can significantly decrease their exposure and minimize vulnerabilities. Moreover, deploying advanced threat detection solutions that leverage machine learning can help identify anomalous behaviors, which is one of the best practices to prevent ransomware. Regular security audits and vulnerability assessments are considered best practices to prevent ransomware, as they help in pinpointing and remediating weaknesses in the security framework.
By adopting this layered approach, including application allowlisting, companies can create multiple obstacles for intruders, greatly reducing the likelihood of a successful malicious software breach. This proactive stance not only enhances security but also fosters a culture of awareness and preparedness among employees-vital in today’s evolving threat landscape.
Furthermore, adherence to compliance standards such as HIPAA, PCI-DSS, and GDPR is reinforced through these measures. This ensures that organizations not only meet regulatory requirements but also protect sensitive data effectively. Are you ready to bolster your organization’s cybersecurity posture? The time to act is now.
C-suite executives must prioritize the creation and regular updating of a thorough response strategy, which aligns with the best practices to prevent ransomware attacks. In today’s evolving threat landscape, the stakes are higher than ever. This plan should clearly define roles and responsibilities, establish communication protocols, and outline recovery procedures. Carrying out tabletop exercises is crucial; they ensure that all team members are familiar with their roles during an incident.
Consider this: organizations that engage in regular testing of their incident response plans can reduce breach costs by an average of $1.49 million. By fostering relationships with cybersecurity experts and law enforcement, companies can facilitate a coordinated response, enhancing overall preparedness. Investing in these proactive measures aligns with the best practices to prevent ransomware, significantly minimizing the impact of a ransomware attack, ensuring a quicker recovery, and maintaining stakeholder trust. In fact, companies that implement organized response protocols prevent 21% more secondary breaches caused by mismanaged response efforts. This underscores the importance of preparation in the current threat environment.
Moreover, organizations should integrate actionable recommendations from user manuals to ensure compliance with HIPAA standards, which is crucial for safeguarding sensitive information. A predefined incident communication strategy can reduce response time by 30%. With the average downtime after a ransomware attack being 24 days, the urgency of having an effective incident response plan cannot be overstated. Additionally, organizations that implement changes based on past breaches reduce future incident rates by 50%, further emphasizing the need for continuous improvement in response strategies.
As highlighted by IBM, the portion of breaches caused by malicious software has increased by 41 percent, demonstrating the expanding threat landscape. The recent cyber event involving Sedgwick Government Solutions serves as a stark reminder of the consequences of inadequate response planning. Cyber Solutions emphasizes the importance of comprehensive risk assessments and gap analysis to identify vulnerabilities, ensuring compliance with HIPAA standards and enhancing overall cybersecurity posture. Their swift response abilities, showcased in restoring 4,500 endpoints following a cyber assault, highlight the essential role of specialized knowledge in ensuring continuity of care and adherence in healthcare environments.
Furthermore, 24/7 threat monitoring by Cyber Solutions provides proactive cybersecurity solutions that align with the best practices to prevent ransomware and phishing attacks, reinforcing the need for a robust incident response strategy.

Embedding ransomware prevention into the core business strategy is not just advisable; it’s essential for C-suite leaders who are serious about safeguarding their organizations against an ever-evolving threat landscape. Cybersecurity should be viewed as a critical aspect of operational resilience, influencing overall business success rather than merely a compliance obligation.
In this article, we’ve highlighted key practices for preventing ransomware. These include:
Such insights underscore the necessity for leaders to proactively engage in cybersecurity measures that protect sensitive data and ensure compliance with industry regulations.
The stakes are high. Executives bear the responsibility of fostering a culture of cybersecurity awareness within their organizations. By prioritizing these best practices and aligning them with business objectives, C-suite leaders can not only mitigate ransomware risks but also enhance their organization’s resilience and long-term success. The time to act is now. Taking decisive steps towards robust cybersecurity measures will ultimately safeguard critical assets and maintain stakeholder trust in an increasingly digital world.
Why is it important for C-suite leaders to integrate ransomware prevention into their business strategy?
Integrating ransomware prevention into business strategy is crucial because it enhances operational resilience and treats cybersecurity as a core element rather than just a compliance requirement. This approach significantly improves an organization's security posture.
What statistics highlight the effectiveness of proactive ransomware prevention measures?
Approximately 97% of entities with encrypted data managed to recover it through various means, demonstrating the effectiveness of proactive measures. Conversely, 60% of ransomware victims reported revenue loss due to attacks, emphasizing the need for integrated cybersecurity strategies.
How can regular risk assessments contribute to ransomware prevention?
Regular risk assessments help identify vulnerabilities and ensure the implementation of best practices to prevent ransomware effectively, strengthening defenses and fostering a culture of accountability and awareness among employees.
What is the significance of prompt action and specialized knowledge in addressing cyber attack incidents?
Prompt action and specialized knowledge are vital in addressing cyber attack incidents, as illustrated by a healthcare provider's experience. Rapid response capabilities, such as managed IT services and 24/7 threat monitoring, can effectively contain threats and enhance security measures.
What misconceptions do C-suite leaders have about ransomware prevention?
One misconception is that traditional antivirus software is sufficient for defending against cyber threats. However, as threats evolve, these solutions often fail to detect modern malicious software. Additionally, many believe that only large companies are at risk, while small and medium-sized enterprises are equally susceptible.
What strategies can C-suite leaders adopt to combat ransomware threats effectively?
C-suite leaders can implement strategies such as application allowlisting to prevent unauthorized software execution, conduct employee training, perform regular software updates, practice operational security like vulnerability scanning, and develop robust incident response plans.
What regulations can be ensured through effective ransomware prevention practices?
Implementing effective ransomware prevention practices can help organizations ensure compliance with regulations such as HIPAA, PCI-DSS, and GDPR.