
Navigating the complexities of cybersecurity compliance is no small feat, particularly for organizations striving to meet the stringent CMMC 2.0 Level 2 requirements. The stakes have never been higher; protecting Controlled Unclassified Information (CUI) is not merely a regulatory obligation - it’s a vital business imperative. This article outlines ten essential steps organizations can take to achieve compliance, bolster their cybersecurity posture, and ultimately secure lucrative government contracts.
But with so many moving parts, how can organizations ensure they are not only compliant but also effectively safeguarding their sensitive information against the ever-evolving landscape of cyber threats? The answer lies in a strategic approach that addresses both compliance and security, ensuring that organizations are well-equipped to face the challenges ahead.
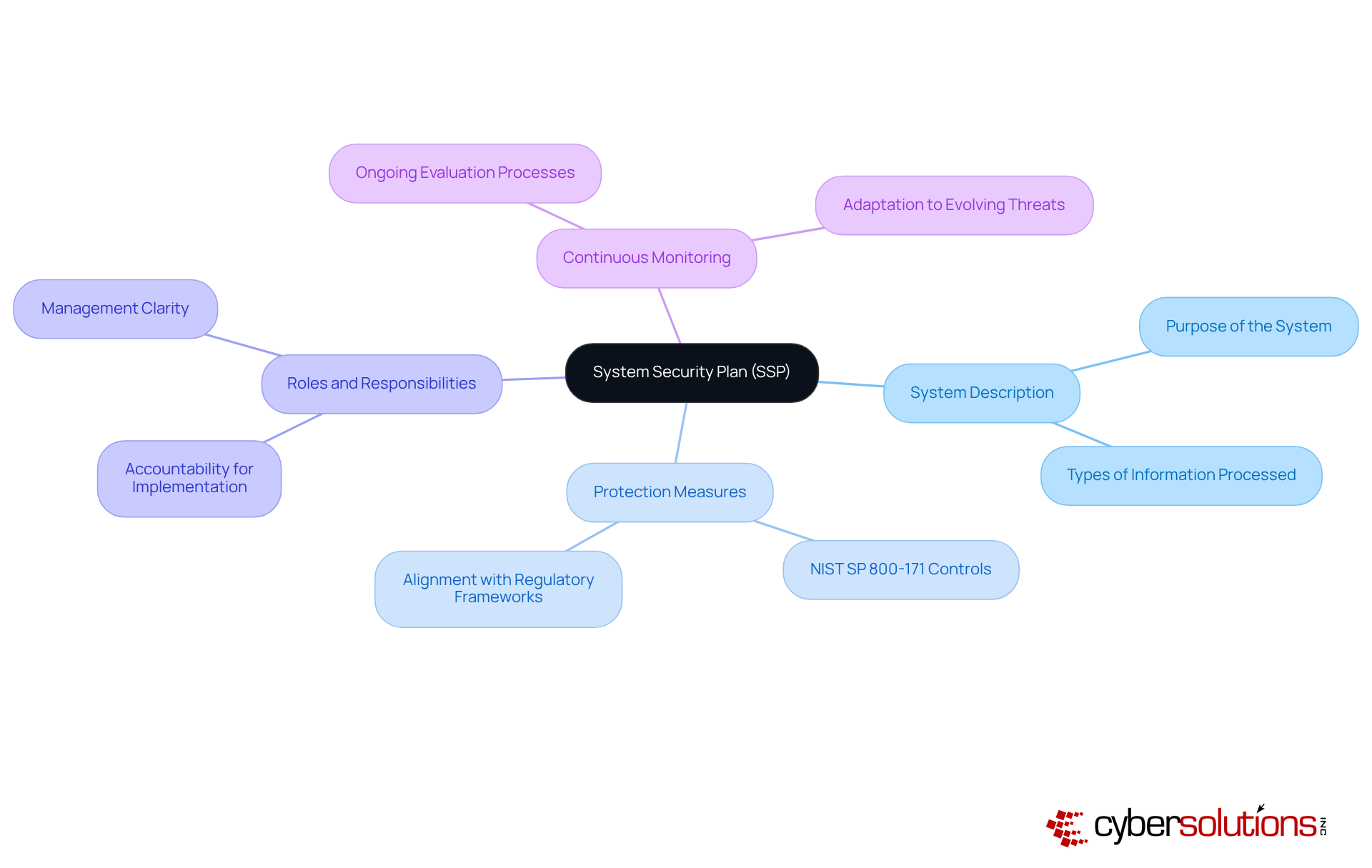
Creating a System Security Plan (SSP) is not just important; it’s essential for documenting the protective requirements and controls necessary to safeguard Controlled Unclassified Information (CUI) in accordance with CMMC 2.0 level 2 requirements. This adherence is vital for maintaining eligibility for government contracts and protecting sensitive federal data. A comprehensive SSP should encompass the following key elements:
System Description: Clearly outline the system's purpose and the types of information it processes, providing a foundational understanding of its operational context.
Protection Measures: Detail the specific protective measures to be implemented, referencing the 110 controls outlined in NIST SP 800-171. This ensures alignment with established regulatory frameworks and enhances the organization's protective stance, particularly for the CMMC 2.0 Level 2 requirements, which focus on safeguarding CUI.
Roles and Responsibilities: Define the individuals or teams accountable for implementing and maintaining these protective measures, fostering accountability and clarity in management.
Continuous Monitoring: Describe the processes for ongoing evaluation of the effectiveness of protective measures, ensuring they adapt to evolving threats and regulatory requirements.
A well-structured SSP not only aids adherence to the CMMC 2.0 level 2 requirements but also significantly enhances the overall security framework of the entity. According to a report by the U.S. Bureau of Labor Statistics, only 27% of entities have a documented SSP, highlighting a critical gap in cybersecurity preparedness. Cybersecurity experts emphasize that a robust SSP is foundational for compliance and can serve as a decisive factor during assessments. By effectively documenting protective measures, companies can demonstrate their commitment to safeguarding sensitive information and mitigating risks associated with cyber threats.
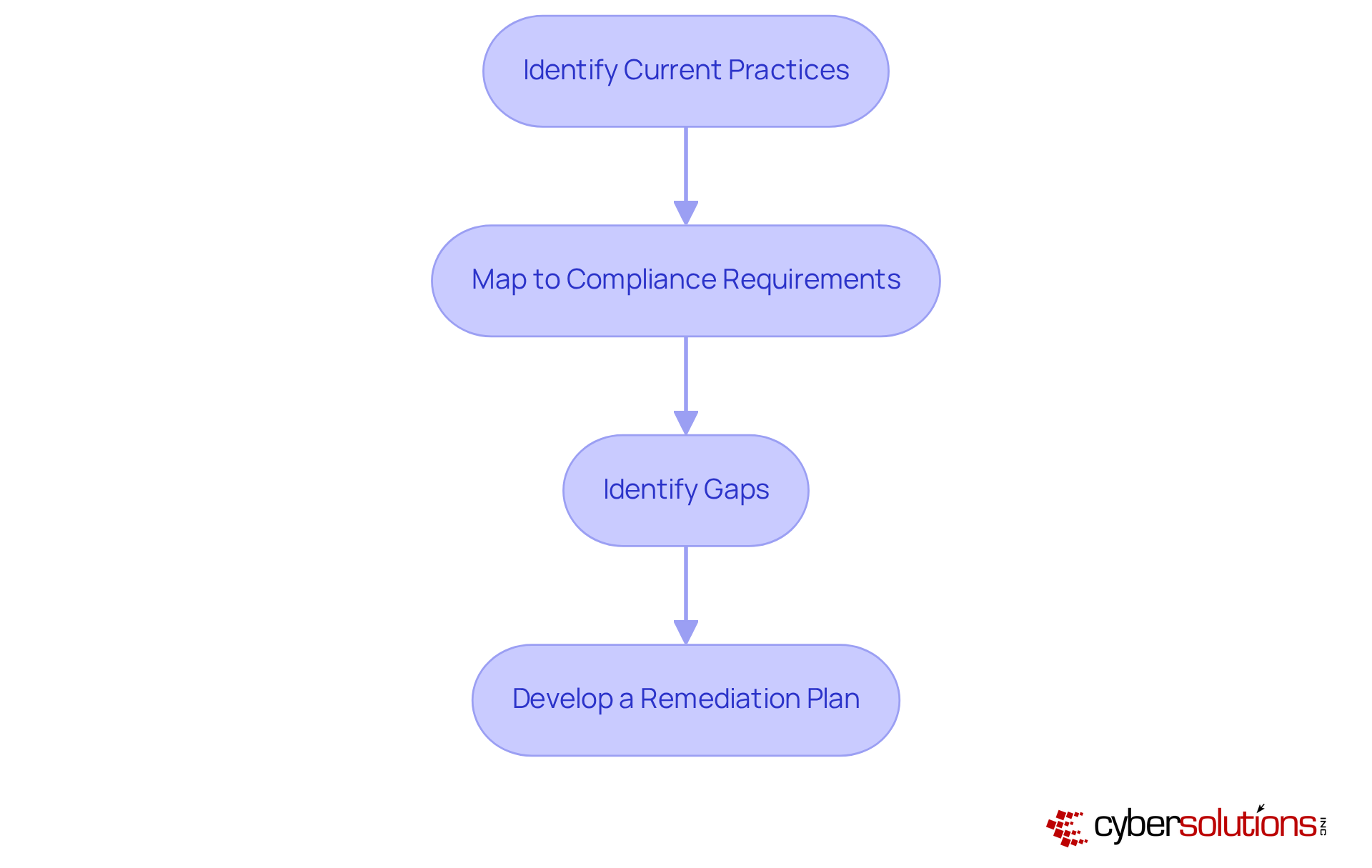
Conducting a Gap Analysis is crucial for organizations striving to meet CMMC 2.0 Level 2 requirements. In today’s landscape, where cybersecurity threats are increasingly sophisticated, this process involves a systematic evaluation of current protective practices against established standards.
Identify Current Practices: Start by documenting existing security measures and controls within your organization. This foundational step sets the stage for a thorough compliance assessment.
Map to Compliance Requirements: Next, compare these practices with the 110 controls outlined in NIST SP 800-171. This ensures a comprehensive understanding of compliance expectations and highlights the unique challenges faced by many organizations.
Identify Gaps: It’s essential to pinpoint areas where current practices fall short of the CMMC 2.0 Level 2 requirements. Recent data reveals that a significant percentage of companies struggle with this aspect, often reporting vulnerabilities in their security frameworks. Are you among them?
Develop a Remediation Plan: Finally, formulate a strategic plan to address the identified gaps. Prioritize actions based on risk assessment and available resources to enhance your cybersecurity posture.
This structured approach not only clarifies your organization’s adherence status but also outlines a clear path for improving cybersecurity resilience. Engaging cybersecurity professionals in this process is vital; their insights can illuminate common pitfalls and effective remediation strategies. For instance, organizations that have successfully identified and addressed deficiencies in their cybersecurity measures report enhanced readiness for regulations and reduced risk exposure. This underscores the importance of proactive actions in today’s evolving threat environment.
In today’s digital landscape, ongoing monitoring and maintenance are not just important; they are essential for a robust cybersecurity strategy. Healthcare organizations face unique challenges, and understanding these is crucial for CFOs navigating this complex environment.
Regular Audits: Conducting periodic audits of security controls is vital to ensure they function as intended. These assessments not only help identify gaps but also reinforce compliance with the CMMC 2.0 level 2 requirements, supported by expert guidance during CMMC assessments. Are your current practices up to par?
Automated Monitoring Tools: Implementing automated monitoring tools significantly enhances threat detection capabilities. These tools provide real-time notifications for suspicious activities, enabling organizations to react swiftly to potential threats. In fact, studies show that organizations using automated monitoring experience a 30% quicker detection rate of incidents compared to those relying solely on manual processes. Isn’t it time to upgrade your defenses?
Incident Response Drills: Regularly testing incident response plans through drills ensures that teams are prepared to act effectively in the event of a breach. These exercises not only enhance response strategies but also boost overall preparedness, aligning with advanced safety protocols necessary for higher levels of certification adherence. How ready is your team?
Updates and Patching: Keeping software and systems up to date is crucial for protecting against known vulnerabilities. Organizations that prioritize timely updates can reduce their risk of exploitation by up to 60%, ensuring eligibility for lucrative government contracts. Are you prioritizing updates in your strategy?
Promoting a culture of ongoing enhancement in security practices is vital for upholding regulations and protecting sensitive information. With expert audit guidance and management, navigating the complexities of certification becomes manageable. Take action now to fortify your cybersecurity posture.

Performing a NIST 800-171A Self-Assessment is essential for organizations seeking to meet CMMC 2.0 level 2 requirements and enhance their cybersecurity posture. This process involves several key steps:
Organizations that conduct self-evaluations not only prepare themselves for regulations but also strengthen their defenses against potential cyber threats. For instance, a manufacturing company reported a 60% reduction in accidental data leaks within six months of implementing a peer-led 'Security Champions' program. This demonstrates the effectiveness of proactive security measures. By prioritizing these steps, businesses can navigate the complexities of cybersecurity regulations and safeguard their critical assets.

Effective documentation is essential for organizations striving to secure lucrative federal contracts by meeting CMMC 2.0 Level 2 requirements. In today’s landscape, where cybersecurity threats are ever-present, having robust documentation can be a game-changer. Here are the key components that every entity should prioritize:
To maintain compliance and enhance security, organizations must routinely review and update their documentation. This ensures that it reflects changes in security practices, technology, and regulatory requirements. By adopting this proactive approach, entities can fortify their defenses and ensure they are prepared to respond effectively to incidents, ultimately supporting their ability to secure federal contracts.

Organizations must take decisive action to manage Controlled Unclassified Information (CUI) effectively. The importance of cybersecurity cannot be overstated, especially as organizations face increasing scrutiny under the new FAR CUI Rule. This begins with:
Understanding CUI is essential for achieving compliance and safeguarding sensitive information. As entities navigate the complexities of cybersecurity, it’s imperative to take these steps seriously. The implications of neglecting CUI management can be severe, making it essential for all government contractors to prioritize training and incident reporting obligations.

Conducting a comprehensive risk assessment is not just a best practice; it’s essential for organizations striving to meet CMMC 2.0 Level 3 requirements. In today’s landscape, where cybersecurity threats loom large, understanding and addressing these risks is paramount. This process should encompass the following key components:
Asset Identification: Start by cataloging all assets that process or store Controlled Unclassified Information (CUI). This crucial step ensures that all key elements are considered, allowing for focused protection strategies in line with advanced safety protocols.
Threat Analysis: Identify potential threats to these assets, which may include cyberattacks, insider threats, and natural disasters. Understanding the threat environment is vital; in fact, 32% of enterprise risk management experts cite information-related risks as their primary concern. Are you prepared to face these challenges?
Vulnerability Assessment: Evaluate existing protective measures to determine their effectiveness against the identified threats. Regular assessments are critical, as only 8% of organizations conduct cyber risk assessments monthly, while 40% do so annually. This gap underscores the urgent need for more proactive measures.
Risk Mitigation Strategies: Develop tailored strategies to address identified risks, which may involve implementing additional security controls or policies. Effective risk management not only safeguards sensitive data but also enhances operational resilience. Moreover, preparing detailed documentation is essential to demonstrate adherence during audits.
Organizations must regularly update their risk assessments to reflect changes in the threat landscape and operational dynamics. This continuous vigilance is crucial for upholding regulations and protecting against emerging cyber threats. Are you ready to take action and fortify your defenses?

Access control measures are vital for protecting sensitive information and ensuring compliance with regulations. Here are the key components:
Role-Based Access Control (RBAC): This method assigns access rights based on user roles, effectively limiting exposure to sensitive information. Organizations implementing RBAC have reported improved security by ensuring that only authorized personnel can access critical data, which is essential for meeting Level 1 requirements for safeguarding Federal Contract Information (FCI).
Multi-Factor Authentication (MFA): The implementation of MFA significantly boosts security for systems managing Controlled Unclassified Information (CUI). Studies indicate that MFA can decrease the likelihood of account compromise by up to 99.9%. This layered defense requires users to provide multiple forms of verification, making unauthorized access considerably more difficult, aligning with the intermediate cybersecurity measures outlined in Level 2.
Regular Access Reviews: Periodic reviews of user access rights are crucial to ensure they match current job responsibilities. This practice helps organizations identify and eliminate unnecessary access, further mitigating risks associated with data breaches, which is essential for maintaining compliance and protecting sensitive federal information.
Audit Logs: Keeping detailed logs of access attempts is critical for monitoring unauthorized access and ensuring accountability. These logs provide valuable insights into user activity and can be instrumental in identifying potential risks, supporting the necessary documentation and reporting strategies required for compliance audits.
Implementing these measures not only fortifies the protection of sensitive information but also plays a crucial role in meeting compliance requirements, particularly the CMMC 2.0 Level 2 requirements. Furthermore, organizations can gain from expert guidance and support during the official CMMC assessment to secure their certification.

In today's digital age, cybersecurity is not just a necessity; it's a critical component of healthcare operations. An effective Incident Response Plan is essential for safeguarding sensitive information and maintaining trust. Here’s how to ensure your organization is prepared:
Incident Response Team: Designate a dedicated team responsible for managing security incidents. This team should be supported by Cyber Solutions' 24/7 Threat Monitoring, which detects suspicious activities before they escalate into serious threats.
Roles and Responsibilities: Clearly define the roles of each team member during an incident. This clarity ensures that everyone understands their part in the response process, fostering a coordinated effort.
Incident Handling Procedures: Outline the necessary steps during an incident, including detection, containment, eradication, and recovery. Leverage comprehensive firewall and network protection solutions to enhance your defense against ransomware and phishing attacks.
Post-Incident Review: Conduct thorough reviews after incidents to identify lessons learned and improve future response efforts. Ensure that documentation is meticulous and compliant with HIPAA standards through incident response tabletops.
Regularly testing and updating your incident response plan is crucial. This practice ensures its effectiveness and relevance in the face of evolving threats. Are you ready to fortify your organization against potential cyber threats?

Implementing effective training and awareness programs is essential for cultivating a robust protective culture within organizations. In today’s digital landscape, where cyber threats are increasingly sophisticated, the need for comprehensive cybersecurity measures has never been more critical.
Cybersecurity Awareness Training: Employees must be educated on identifying phishing attempts, social engineering tactics, and other prevalent threats. With human error accounting for over 90% of cyber breaches and 70-85% of breaches caused by human conduct, this training is vital for reducing vulnerabilities. How can organizations expect to defend against cyber threats if their first line of defense-employees-aren’t adequately prepared?
Role-Specific Training: Customizing training to particular job functions ensures that employees obtain pertinent practices that correspond with their duties. This targeted approach enhances engagement and effectiveness, as employees can relate the training to their daily tasks. Isn’t it more effective to equip staff with knowledge that directly applies to their roles?
Regular Updates: Training materials should be continuously refreshed to reflect the latest threats and protective practices. With cybercrime projected to cost the global economy $12.2 trillion annually by 2031 and the average cost of a data breach projected to exceed USD 5 million in 2025, staying current is crucial for maintaining resilience against evolving threats. Are organizations truly prepared to face these escalating costs without up-to-date training?
Testing and Drills: Conducting regular drills is necessary to evaluate employee preparedness in responding to incidents. Approximately 78% of entities experienced significant impacts from cybersecurity incidents in the past year, highlighting the need for preparedness. How can organizations ensure they are ready for the unexpected?
By integrating these elements into training programs, organizations can significantly enhance their cybersecurity posture and foster a proactive security environment. The time to act is now-don’t wait for a breach to realize the importance of robust training.

Achieving compliance with CMMC 2.0 Level 2 requirements is not just a regulatory obligation; it’s a strategic necessity for organizations handling Controlled Unclassified Information (CUI). In today’s landscape, where cyber threats are increasingly sophisticated, organizations must take decisive action. By following ten key steps, they can build a robust cybersecurity framework that not only meets compliance standards but also strengthens defenses against evolving cyber threats.
Critical actions include:
Each step is vital for identifying vulnerabilities, enhancing security measures, and ensuring preparedness for potential incidents. Moreover, fostering a culture of training and awareness among employees is essential for minimizing risks associated with human error, a significant factor in cybersecurity breaches.
Organizations cannot afford to be complacent. Proactive measures, continuous assessments, and a commitment to compliance are essential for safeguarding sensitive information and maintaining eligibility for government contracts. By prioritizing these steps, organizations not only enhance their cybersecurity posture but also position themselves as trustworthy partners in an increasingly digital world. Taking decisive action today will pave the way for a more secure and resilient future.
What is a System Security Plan (SSP) and why is it important?
A System Security Plan (SSP) is essential for documenting the protective requirements and controls necessary to safeguard Controlled Unclassified Information (CUI) in accordance with CMMC 2.0 level 2 requirements. It is crucial for maintaining eligibility for government contracts and protecting sensitive federal data.
What key elements should be included in a comprehensive SSP?
A comprehensive SSP should include the following key elements: 1. System Description: Outlining the system's purpose and the types of information it processes. 2. Protection Measures: Detailing specific protective measures aligned with the 110 controls in NIST SP 800-171. 3. Roles and Responsibilities: Defining individuals or teams accountable for implementing and maintaining protective measures. 4. Continuous Monitoring: Describing processes for ongoing evaluation of the effectiveness of protective measures.
What is the significance of conducting a Gap Analysis?
Conducting a Gap Analysis is crucial for organizations striving to meet CMMC 2.0 Level 2 requirements. It involves evaluating current protective practices against established standards to identify areas where practices fall short, ultimately leading to the development of a remediation plan to enhance cybersecurity posture.
What are the steps involved in performing a Gap Analysis?
The steps involved in performing a Gap Analysis include: 1. Identify Current Practices: Document existing security measures and controls. 2. Map to Compliance Requirements: Compare these practices with the 110 controls in NIST SP 800-171. 3. Identify Gaps: Pinpoint areas where current practices do not meet CMMC 2.0 Level 2 requirements. 4. Develop a Remediation Plan: Formulate a strategic plan to address identified gaps based on risk assessment.
Why is ongoing monitoring and maintenance essential for cybersecurity?
Ongoing monitoring and maintenance are essential for a robust cybersecurity strategy as they help ensure security controls function as intended, enhance threat detection capabilities, and prepare teams for effective incident response. This proactive approach is vital for compliance with CMMC 2.0 level 2 requirements and for protecting sensitive information.
What practices should organizations implement for ongoing monitoring and maintenance?
Organizations should implement the following practices for ongoing monitoring and maintenance: 1. Regular Audits: Conduct periodic audits of security controls. 2. Automated Monitoring Tools: Use automated tools for real-time threat detection. 3. Incident Response Drills: Regularly test incident response plans through drills. 4. Updates and Patching: Keep software and systems up to date to protect against vulnerabilities.